220-1102 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 220-1102 certification exam? Kickstart your success with our 220-1102 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 220-1102 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 220-1102 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
As part of a CYOD policy, a systems administrator needs to configure each user's Windows device to require a password when resuming from a period of sleep or inactivity. Which of the following paths will lead the administrator to the correct settings?
A. Use Settings to access Screensaver settings.
B. Use Settings to access Screen Timeout settings.
C. Use Settings to access General.
D. Use Settings to access Display.
A technician is setting up a SOHO router in a user's home. The user wants the router to be configured to prevent access to malicious content and apply internet access protection. Which of the following settings should the technician configure?
A. Port forwarding
B. Content filtering
C. Firmware updates
D. DHCP reservations
A technician downloaded software from the Internet that required the technician to scroll through a text box and at the end of the text box, click a button labeled Accept. Which of the following agreements is MOST likely in use?
A. DRM
B. NDA
C. EULA
D. MOU
A user reports that antivirus software indicates a computer is infected with viruses. The user thinks this happened while browsing the internet. The technician does not recognize the interface with which the antivirus message is presented. Which of the following is the NEXT step the technician should take?
A. Shut down the infected computer and swap it with another computer.
B. Investigate what the interface is and what triggered it to pop up.
C. Proceed with initiating a full scan and removal of the viruses using the presented interface.
D. Call the phone number displayed in the interface of the antivirus removal tool.
A user calls the help desk and reports a workstation is infected with malicious software. Which of the following tools should the help desk technician use to remove the malicious software? (Choose two.)
A. Local Network Connection
B. User Account Control
C. Windows Backup and Restore
D. Windows Firewall
E. Windows Defender
F. Network Packet Analyzer
Which of the following items require special e-waste recycling? (Choose two.)
A. Solid-state drive
B. A/C adapter
C. Surge protector
D. Laptop battery
E. CRT monitor
F. Power supply
Which of the following file extensions should a technician use for a PowerShell script?
A. .ps1
B. .py
C. .sh
D. .bat
E. .cmd
A company wants to remove information from past users' hard drives in order to reuse the hard drives. Which of the following is the MOST secure method?
A. Reinstalling Windows
B. Performing a quick format
C. Using disk-wiping software
D. Deleting all files from command-line interface:
A technician has verified a computer is infected with malware. The technician isolates the system and updates the anti-malware software. Which of the following should the technician do next?
A. Run one scan and schedule future scans.
B. Back up the uninfected files and reimage the computer.
C. Restore the clean backup copies of the infected files.
D. Run repeated remediation scans until the malware is removed.
A manager reports that staff members often forget the passwords to their mobile devices and applications. Which of the following should the systems administrator do to reduce the number of help desk tickets submitted?
A. Enable multifactor authentication.
B. Increase the failed log-in threshold.
C. Remove complex password requirements.
D. Implement a single sign-on with biometrics.
A company is retiring old workstations and needs a certificate of destruction for all hard drives. Which of the following would be BEST to perform on the hard drives to ensure the data is unrecoverable? (Choose two.)
A. Standard formatting
B. Drilling
C. Erasing
D. Recycling
E. Incinerating
F. Low-level formatting
A user reports that a PC seems to be running more slowly than usual. A technician checks system resources, but disk, CPU, and memory usage seem to be ne. The technician sees that GPU temperature is extremely high. Which of the following types of malware is MOST likely to blame?
A. Spyware
B. Cryptominer
C. Ransomware
D. Boot sector virus
A remote user is having issues accessing an online share. Which of the following tools would MOST likely be used to troubleshoot the issue?
A. Screen-sharing software
B. Secure shell
C. Virtual private network
D. File transfer software
After clicking on a link in an email, a Chief Financial officer (CFO) received the following error:The CFO then reported the incident to a technician. The link is purportedly to the organization's bank. Which of the following should the technician perform FIRST?
A. Update the browser’s CRLs.
B. File a trouble ticket with the bank.
C. Contact the ISP to report the CFO’s concern.
D. Instruct the CFO to exit the browser.
Which of the following Linux commands would be used to install an application?
A. yum
B. grep
C. ls
D. sudo
A user connected a smartphone to a coffee shop's public Wi-Fi and noticed the smartphone started sending unusual SMS messages and registering strange network activity. A technician thinks a virus or other malware has infected the device. Which of the following should the technician suggest the user do to best address these security and privacy concerns? (Choose two.)
A. Disable Wi-Fi autoconnect.
B. Stay offline when in public places.
C. Uninstall all recently installed applications.
D. Schedule an antivirus scan.
E. Reboot the device.
F. Update the OS.
A technician installed an application on a user's desktop and received an error message. Which of the following tools can the technician use to research the error?
A. Resource Monitor > CPU > Services
B. Task Manager > Processes > Apps
C. Event Viewer > Windows Logs > Application
D. Device Manager > Computer
A user turns on a new laptop and attempts to log in to specialized software, but receives a message stating that the address is already in use. The user logs on to the old desktop and receives the same message. A technician checks the account and sees a comment that the user requires a specifically allocated address before connecting to the software. Which of the following should the technician do to MOST likely resolve the issue?
A. Bridge the LAN connection between the laptop and the desktop.
B. Set the laptop configuration to DHCP to prevent conflicts.
C. Remove the static IP configuration from the desktop.
D. Replace the network card in the laptop, as it may be defective.
A user's corporate laptop with proprietary work information was stolen from a coffee shop. The user logged in to the laptop with a simple password, and no other security mechanisms were in place. Which of the following would MOST likely prevent the stored data from being recovered?
A. Biometrics
B. Full disk encryption
C. Enforced strong system password
D. Two-factor authentication
A police officer often leaves a workstation for several minutes at a time. Which of the following is the BEST way the officer can secure the workstation quickly when walking away?
A. Use a key combination to lock the computer when leaving.
B. Ensure no unauthorized personnel are in the area.
C. configure a screensaver to lock the computer automatically after approximately 30 minutes of inactivity.
D. Turn off the monitor to prevent unauthorized visibility of information.
A macOS user needs to create another virtual desktop space. Which of the following applications will allow the user to accomplish this task?
A. Dock
B. Spotlight
C. Mission Control
D. Launchpad
During an enterprise rollout of a new application, a technician needs to validate compliance with an application's EULA while also reducing the number of licenses to manage. Which of the following licenses would best accomplish this goal?
A. Personal use license
B. Corporate use license
C. Open-source license
D. Non-expiring license
A technician is tasked with configuring a computer for a visually impaired user. Which of the following utilities should the technician use?
A. Device Manager
B. System
C. Ease of Access Center
D. Programs and Features
A user calls the help desk to report potential malware on a computer. The anomalous activity began after the user clicked a link to a free gift card in a recent email. The technician asks the user to describe any unusual activity, such as slow performance, excessive pop-ups, and browser redirections. Which of the following should the technician do NEXT?
A. Advise the user to run a complete system scan using the OS anti-malware application.
B. Guide the user to reboot the machine into safe mode and verify whether the anomalous activities are still present.
C. Have the user check for recently installed applications and outline those installed since the link in the email was clicked.
D. Instruct the user to disconnect the Ethernet connection to the corporate network.
Antivirus software indicates that a workstation is infected with ransomware that cannot be quarantined. Which of the following should be performed FIRST to prevent further damage to the host and other systems?
A. Power off the machine.
B. Run a full antivirus scan.
C. Remove the LAN card.
D. Install a different endpoint solution.
A help desk technician runs the following script: Inventory.py. The technician receives the following error message: How do you want to open this file? Which of the following is the MOST likely reason this script is unable to run?
A. Scripts are not permitted to run.
B. The script was not built for Windows.
C. The script requires administrator privileges.
D. The runtime environment is not installed.
A user contacts a technician about an issue with a laptop. The user states applications open without being launched and the browser redirects when trying to go tofficertain websites. Which of the following is MOST likely the cause of the user's issue?
A. Keylogger
B. Cryptominers
C. Virus
D. Malware
A help desk technician is troubleshooting a workstation in a SOHO environment that is running above normal system baselines. The technician discovers an unknown executable with a random string name running on the system. The technician terminates the process, and the system returns to normal operation. The technician thinks the issue was an infected file, but the antivirus is not detecting a threat. The technician is concerned other machines may be infected with this unknown virus. Which of the following is the MOST effective way to check other machines on the network for this unknown threat?
A. Run a startup script that removes files by name.
B. Provide a sample to the antivirus vendor.
C. Manually check each machine.
D. Monitor outbound network traffic.
A user is receiving repeated pop-up advertising messages while browsing the internet. A malware scan is unable to locate the source of an infection. Which of the following should the technician check NEXT?
A. Windows updates
B. DNS settings
C. certificate store
D. Browser plug-ins
A help desk technician needs to remotely access and control a customer's Windows PC by using a secure session that allows the technician the same control as the customer. Which of the following tools provides this type of access?
A. FTP
B. RDP
C. SSH
D. VNC
The courts determined that a cybercrimes case could no longer be prosecuted due to the agency's handling of evidence. Which of the following was MOST likely violated during the investigation?
A. Open-source software
B. EULA
C. Chain of custody
D. AUP
A company is creating an access control system that uses something you have and something you are. Which of the following will be required for user authentication? (Choose two.)
A. Password manager
B. Encryption keys
C. Biometric scanner
D. Smartcard reader
E. Host-based IDS
F. PIN code
Which of the following would cause a corporate-owned iOS device to have an Activation Lock issue?
A. A forgotten keychain password
B. An employee’s Apple ID used on the device
C. An operating system that has been jailbroken
D. An expired screen unlock code
A user receives a call from someone who claims to be from the user's bank and requests information to ensure the user's account is safe. Which of the following social-engineering attacks is the user experiencing?
A. Phishing
B. Smishing
C. Whaling
D. Vishing
A user requires a drive to be mapped through a Windows command line. Which of the following command-line tools can be utilized to map the drive?
A. gpupdate
B. net use
C. hostname
D. dir
In an organization with a standardized set of installed software, a developer submits a request to have new software installed. The company does not currently have a license for this software, but the developer already downloaded the installation file and is requesting that the technician install it. The developer states that the management team approved the business use of this software. Which of the following is the best action for the technician to take?
A. Contact the software vendor to obtain the license for the user, and assist the user with installation once the license is purchased.
B. Run a scan on the downloaded installation file to confirm that it is free of malicious software, install the software, and document the software installation process.
C. Indicate to the developer that formal approval is needed; then, the IT team should investigate the software and the impact it will have on the organization before installing the software.
D. Install the software and run a full system scan with antivirus software to confirm that the operating system is free of malicious software.
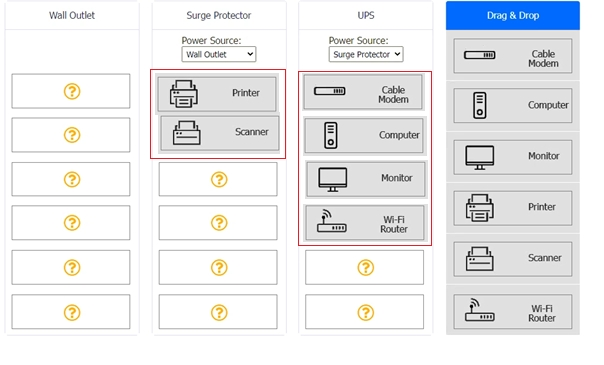
DRAG DROP A customer recently experienced a power outage at a SOHO. The customer does not think the components are connected properly. A print job continued running for several minutes after the power failed, but the customer was not able to interact with the computer. Once the UPS stopped beeping, all functioning devices also turned off. In case of a future power failure, the customer wants to have the most time available to save cloud documents and shut down the computer without losing any data. INSTRUCTIONS Based on the customer's requirements, connect the customer's devices to the proper outlets. Select the power source for the Surge Protector and UPS. This may require reselecting dropdowns or removing tokens. Each token may only be used once. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.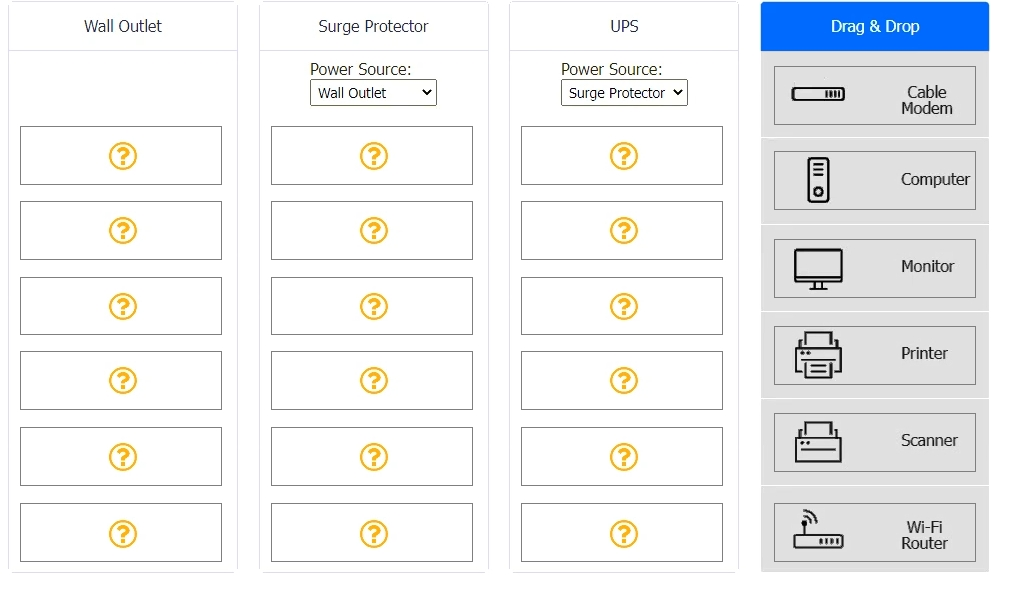
Which of the following social engineering tactics is best avoided by shredding sensitive documents?
A. Dumpster diving
B. Phishing
C. Whaling
D. Shoulder sur ng
Sensitive data was leaked from a user's smartphone. A technician discovered an unapproved application was installed, and the user has full access to the device's command shell. Which of the following is the NEXT step the technician should take to find the cause of the leaked data?
A. Restore the device to factory settings.
B. Uninstall the unapproved application.
C. Disable the ability to install applications from unknown sources.
D. Ensure the device is connected to the corporate WiFi network.
A user who is unable to connect to the network submits a help desk ticket. The assigned help desk technician inquires about whether any recent changes have been made. The user reports there is construction activity in the surrounding offices. The help desk technician proceeds to ping the user's desktop, which does not respond. Which of the following is the MOST likely cause of this issue?
A. A duplicate IP address has been issued to the user’s desktop.
B. The HDD of the OS is failing.
C. The network cable has become disconnected.
D. Malware has infected the system.
A user is unable to use any internet-related functions on a smartphone when it is not connected to Wi-Fi. When the smartphone is connected to Wi-Fi, the user can browse the internet and send and receive email. The user is also able to send and receive text messages and phone calls when the smartphone is not connected to Wi-Fi. Which of the following is the MOST likely reason the user is unable to use the internet on the smartphone when it is not connected to Wi-Fi?
A. The smartphone’s line was not provisioned with a data plan
B. The smartphone’s SIM card has failed.
C. The smartphone’s Bluetooth radio is disabled
D. The smartphone has too many applications open
A junior administrator is responsible for deploying software to a large group of computers in an organization. The administrator finds a script on a popular coding website to automate this distribution but does not understand the scripting language. Which of the following BEST describes the risks in running this script?
A. The instructions from the software company are not being followed.
B. Security controls will treat automated deployments as malware.
C. The deployment script is performing unknown actions.
D. Copying scripts off the internet is considered plagiarism.
Which of the following is most likely used to run .vbs files on Windows devices?
A. winmgmt.exe
B. powershell.exe
C. cscript.exe
D. explorer.exe
A user's laptop has been performing slowly and redirecting to unfamiliar websites. The user has also noticed random pop-up windows. Which of the following is the first step a technician should take to resolve the issue?
A. Scan for malware and ransomware.
B. Perform a system restore.
C. Check the network utilization.
D. Update the antivirus software.
Which of the following commands can a technician use to get the MAC address of a Linux distribution?
A. net use
B. ifconfig
C. netstat
D. ping
A user has been unable to access a website and has submitted a help desk ticket. The website has been verified to be online. Which of the following troubleshooting steps will MOST likely resolve the issue?
A. Deleting the browser history
B. Clearing the cache
C. Enabling private mode browsing
D. Enabling ad blocking
All the desktop icons on a user's newly issued PC are very large. The user reports that the PC was working ne until a recent software patch was deployed. Which of the following would BEST resolve the issue?
A. Rolling back video card drivers
B. Restoring the PC to factory settings
C. Repairing the Windows profile
D. Reinstalling the Windows OS
A technician is troubleshooting a mobile device that was dropped. The technician finds that the screen fails to rotate, even though the settings are correctly applied. Which of the following pieces of hardware should the technician replace to resolve the issue?
A. LCD
B. Battery
C. Accelerometer
D. Digitizer
A call center technician receives a call from a user asking how to update Windows. Which of the following describes what the technician should do?
A. Have the user consider using an iPad if the user is unable to complete updates.
B. Have the user text the user’s password to the technician.
C. Ask the user to click in the Search field, type Check for Updates, and then press the Enter key.
D. Advise the user to wait for an upcoming, automatic patch.
An internet café has several computers available for public use. Recently, users have reported the computers are much slower than they were the previous week. A technician finds the CPU is at 100% utilization, and antivirus scans report no current infection. Which of the following is MOST likely causing the issue?
A. Spyware is redirecting browser searches.
B. A cryptominer is verifying transactions.
C. Files were damaged from a cleaned virus infection.
D. A keylogger is capturing user passwords.
Free Access Full 220-1102 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 220-1102 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 220-1102 certification journey!

