220-1002 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the 220-1002 certification? Take your preparation to the next level with our 220-1002 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a 220-1002 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic 220-1002 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
A Windows user reports that clicking on links when browsing the Internet results in unexpected destination pages with advertisements or virus infection warnings. The user reboots the computer, but the issue persists. Which of the following should a technician perform to identify and resolve the issue? (Choose two.)
A. Run a virus scan with updated signature files
B. Uninstall any unknown browser extensions or add-ons
C. Install the latest version of the Internet browser
D. Enable SSL 3.0 in the browser settings
E. Delete all unknown registry keys and reboot
After installing an application on a smartphone, a user starts receiving pop-up ads for recently visited physical stores. The user also receives prompts to install other applications. Which of the following permissions should be revoked to disable the unwanted notifications?
A. Account access
B. Mobile data
C. Location access
D. Contacts access
A technician needs to format a 64GB flash drive. Which of the following formats will the technician MOST likely use?
A. FAT
B. ExFAT
C. FAT32
D. CDFS
A user who is running Windows XP calls a technician to upgrade the computer to a newer Windows OS. The user states the computer has only 1GB of RAM and 16GB of hard drive space with a 1.7GHz processor. Which of the following OSs should the technician recommended to ensure the BEST performance on this computer?
A. Windows 7
B. Windows 8
C. Windows 8.1
D. Windows 10
An administrator is creating a new user account and wants to grant access to only the resources required to perform the user's assigned job duties. Which of the following will the administrator MOST likely use?
A. Access control lists
B. Multifactor authentication
C. Directory permissions
D. Principle of least privilege
A user's mobile social media application is sending emails on behalf of the user. However, the user has not authorized any new permissions for the social media application. The user only has this application installed on their smart phone and no other devices. Which of the following should a technician perform to resolve the issue?
A. Run a malware scan on the device.
B. Instruct the user to change the device’s password.
C. Disable access to the user’s contacts.
D. Deny access to text messages.
Which of the following uses a remote access server to forward a user's logon password to an authentication server, allowing or denying access to a system?
A. WPA2-PSK
B. AES
C. TACACS
D. TKIP
A technician is adding a folder to a structure that is several levels down from the top level. The technician wants to make sure the new folder will have the same permissions as the top level. Which of the following should the technician configure?
A. Attributes
B. Shares
C. Inheritance
D. Replication
Which of the following threats uses personalized information in an attempt at obtaining information?
A. Whaling
B. Impersonation
C. Spoofing
D. Spear phishing
Joe, a technician, has his daily plans forwarded to him by his supervisor. Upon arrival to the second support call of the day, Joe realizes the issue will require much more time than initially scheduled, and several support calls will not be completed. Which of the following would be the appropriate action for Joe?
A. Contact his supervisor so the supervisor can make scheduling changes.
B. Move the appointments to the next business day.
C. Reach out to a colleague to assist in completing the jobs.
D. Continue to work on the current call, and get to the other as soon as possible.
A customer is having trouble opening several files on a computer. The customer renames one of the files, but then the correct program will no longer open it. Which of the following settings is a solution to the issue?
A. Set the view options to detail
B. Hide the extensions
C. Utilize Credential Manager
D. View the system files
A technician is removing a virus from a user's Windows workstation. The virus was installed by the user while downloading pirated software from the Internet. Which of the following should the technician do to address this issue?
A. End the current explorer.exe task. Update and run an antivirus scanning utility to remove the threat. Relaunch explorer.exe using Task Manager.
B. End the current explorer.exe task using the command line. Update and run an antivirus scanning utility to remove the threat.
C. Launch explorer.exe using Task Manager. Update and run an antivirus scanning utility to remove the threat.
D. Update and run an antivirus scanning utility to remove the threat. Launch explorer.exe using Task Manager.
A technician has enabled port security on a switchport. Which of the following BEST describes the effect this will have?
A. Devices must match a list of allowed MAC addresses before accessing the network.
B. Devices need to conform to the policies set forth by the MDM software.
C. Data loss prevention software will be monitoring for data exfiltration on the port.
D. A firewall is actively monitoring the network traffic using heuristic analysis.
SIMULATION - Welcome to your first day as a Fictional Company, LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue. INSTRUCTIONS - Click on individual tickets to see the ticket details. View attachments to determine the problem. Select the appropriate issue from the 'Issue' drop-down menu. Then, select the MOST efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper command or verification to remediate or confirm your fix of the issue form he 'Verify/Resolve' drop-down menu. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.[1]
[1]
[1]
A technician determines a newly installed service is keeping a device from functioning in Windows. Which of the following tools should the technician use to keep the service from being loaded on the PC reboot?
A. Task Scheduler
B. MSINFO32
C. System Restore
D. MSConfig
Joe, an employee, took a company-issued Windows laptop home, but is having trouble connecting to any of the shares hosted on his home media server. Joe has verified he is connected to the Internet. Which of the following would explain why Joe cannot access his personal shares?
A. An IP conflict is present
B. A corporate VPN is enabled
C. A firewall exception must be set
D. HomeGroup must be enabled
After a virus has been spread unknowingly via USB removable hard drives, a technician is tasked with limiting removable hard drive access to certain network users. USB ports are used for many devices, including scanners, printers, and signature pads, so a policy is created to deny access to removable hard drives only. When testing the policy, a removable drive is plugged in but can still be accessed. Which of the following command-line tools should the technician use to apply the new policy?
A. grupdate
B. diskpart
C. gpresult
D. net use
A technician has completed troubleshooting and repairing a newly found bug on a user's workstation. The technician wants to share the repair steps with the rest of the team. Which of the following methods will the technician MOST likely use?
A. Knowledge-base entry
B. Team chat message
C. Email to the team leader
D. Incident documentation
Which of the following application installation methods requires the use of a valid IP address?
A. USB
B. Network-based
C. Script-based
D. CD-ROM
A technician is working on an infected computer that is currently turned off. The technician is concerned the boot sector is affected. Which of the following is the BEST method for the technician to use to scan the boot sector?
A. Mount the drive using a forensic platform.
B. Boot into safe mode.
C. Boot to last known good configuration.
D. Boot the drive in another computer.
Which of the following is a reason to use WEP over WPA?
A. Device compatibility
B. Increased security
C. TACACS
D. Multifactor authentication
An executive has contacted you through the help-desk chat support about an issue with a mobile device. Assist the executive to help resolve the issue. INSTRUCTIONS - Select the MOST appropriate statement for each response. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.Let's take a look at your phone settings.
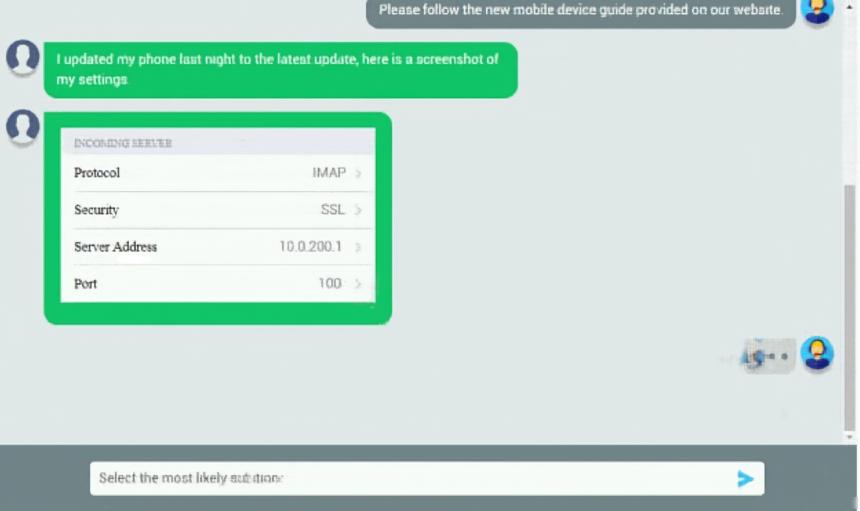
Please change the port number on your mail settings to 993. Which of the following should be done NEXT?
A. Close the ticket out
B. Educate the user on the solution that was performed
C. Tell the user to take time to fix it themselves next time
D. Send an email to Telecom to inform them of the issue and prevent reoccurrence
A technician is running Windows on a company's Mac workstations without incurring an additional expense to the company. The Windows licenses were purchased in the past. Users are required to run both Windows and Mac operating systems on their machines, but never at the same time. Which of the following would be the BEST way to accomplish this?
A. Perform a PXE boot on the workstations.
B. Install virtualization software.
C. Utilize Mission Control on the Mac workstations.
D. Install Boot Camp on the workstations.
A recent outbreak of a virus has uncovered that a company must put a security template in place to mitigate future virus outbreaks. Which of the following best practices would a technician MOST likely implement as part of the security template? (Choose two.)
A. Failed attempts lockout policy
B. Restricting user permissions
C. Login time restrictions
D. Setting strong passwords
E. Patch/update management
Which of the following provide the BEST security for a server room? (Choose two.)
A. Badge reader
B. Bollard
C. Biometric lock
D. Cable lock
E. USB token
F. Privacy window shades
Ann, an employee, has been trying to use a company-issued mobile device to access an internal fileshare while traveling abroad. She restarted the device due to a mobile OS update, but she is now unable to access company information. Ann calls the help desk for assistance, and a technician verifies she can make calls and access websites. Which of the following should the technician suggest NEXT to try to fix the issue?
A. Navigate to the VPN profile in the device settings, delete the pre-shared key, and restart the device
B. Instruct Ann to open the company’s MDM application to ensure proper functionality
C. Navigate to the corporate intranet page and use hyperlinks to access the fileshare
D. Instruct Ann to disable TLS 1.0 in the device settings
A user received a brand new mobile device about six months ago. The device is now running very slowly and is hotter than normal, and certain applications crash when they are started. Which of the following are the BEST options for troubleshooting this phone? (Choose two.)
A. Check for any applications that are running and stop them.
B. Check the device’s battery and replace it.
C. Check the smartphone’s screen and replace it.
D. Check the smartphone’s charging cable to ensure it is working properly.
E. Check for any unnecessary applications and uninstall them.
F. Check for any OS updates and install them.
Joe, a systems administrator, is setting up a risk management plan for the IT department. Part of the plan is to take daily backups of all servers. The server backups will be saved locally to NAS. Which of the following can Joe do to ensure the backups will work if needed?
A. Frequently restore the servers from backup files and test them
B. Configure the backups to restore to virtual machines for quick recovery
C. Set up scripts that automatically rerun failed backup jobs
D. Set up alerts to let administrators know when backups fail
E. Store copies of the backups off-side in a secure datacenter
Which of the following security permissions takes precedence over the other?
A. File permissions over share permissions
B. Share permissions over inherited permissions
C. Share permissions over file permissions
D. File permissions over user permissions
A systems administrator needs to add security to the server room. Which of the following would provide the BEST security for the room? (Choose two.)
A. Universal serial bus locks
B. Personal identity verification cards
C. Privacy screen
D. Entry control roster
E. Door locks
F. Privacy window
After a security audit, a technician is tasked with implementing new measures to help secure company workstations. The new policy states that all workstations must be signed off at night, a password is necessary to boot the computer, and encryption must be enabled. Which of the following features should the technician implement to BEST meet these requirements? (Choose three.)
A. Screen locks
B. Screensaver passwords
C. UEFI passwords
D. Login time restrictions
E. Strong passwords
F. Multifactor authentication
G. BitLocker
H. Credential Manager
A company needs to destroy several SSDs that contain sensitive information. Which of the following methods is BEST suited for the total destruction of the SSDs?
A. Overwriting
B. Formatting
C. Incinerating
D. Degaussing
Ann, a user, calls the help desk regarding an issue on her laptop. While working remotely, she appears to be connecting to WiFi but is unable to retrieve her corporate email. The wireless name is listed as `ConnectMe` and appears as unsecure. Which of the following should the help desk perform to fix the issue?
A. Remote into Ann’s system and restart the wireless adapter
B. Ask Ann to open a browser and watch for a redirect page
C. Advice Ann to plug an Ethernet cable into her laptop
D. Direct Ann to run an antivirus program on her laptop
A technician is running updates on a Windows PC. Some of the updates install properly, while others appear as failed. While troubleshooting, the technician restarts the PC and attempts to install the failed updates again. The updates continue to fail. Which of the following is the FIRST option to check?
A. Visit the Microsoft Update website to see if there is an issue with a specific update
B. Look up the error number associated with the failed update
C. Look at the system Event Viewer to find more information on the failure
D. Download the failed update to install manually
A technician needs to install Windows 10 on a 4TB hard drive. Which of the following should the technician perform to accomplish this task?
A. Format the drive to use exFAT.
B. Configure the drive to use the GPT.
C. Configure the drive to use an MBR.
D. Format the drive to use CDFS.
Which of the following extensions identify files that are typically implemented as scripts? (Choose two.)
A. .vbs
B. .txt
C. .exe
D. .zip
E. .bat
F. .xlsx
Which of the following operating systems has versions for servers, workstations, and phones?
A. Android
B. iOS
C. Chrome OS
D. Windows
A company is creating a disaster recovery plan. Which of the following should be implemented to BEST ensure the company's data can be successfully restored in the event of a disaster?
A. File-level backups
B. Backups for critical applications
C. Regular backup testing
D. Backups to cloud storage
E. Redundant backups on site
A user's computer is displaying a black screen. The technician restarts the computer, but the OS still does not load. The technician discovers the OS was patched the previous evening. Which of the following should the technician attempt NEXT?
A. Reboot into safe mode and roll back the updates
B. Repair the Windows Registry
C. Configure boot options in the BIOS
D. Disable Windows services and applications
Which of the following must be enabled to configure 20 new machines to be booted over a network?
A. Multi-boot
B. Dynamic
C. PXE
D. GPT
Joe, a mobile device user, reached his monthly quota of data about halfway through the current billing cycle. Joe contacts a technician to identify potential issues with the mobile device, as his usage patterns have not changed over the past month. Which of the following is MOST likely causing this issue?
A. There are unintended WiFi connections.
B. Location tracking has been enabled.
C. Applications are causing high resource utilization.
D. Malware is causing excessive data transmission.
An office location regularly experiences brownouts. Which of the following would be the MOST appropriate solution to protect the office computers?
A. Uninterruptible power supply
B. Voltage regulator
C. Surge suppressor
D. Generator
An office building lost power, and the generator started up. Users on several floors have reported their machines will not start, even though the generator is running. A technician works to divert power from other floors until all users are able to work. Which of the following is the BEST solution for the technician to recommend?
A. Add more redundancy to the power cabling
B. Purchase more battery backups for individual users
C. Implement desktop virtualization
D. Increase the capacity of the backup generator
The Chief Executive Offer (CEO) of a company receives an email from a local bank. It states the company's account has several suspicious transactions and instructs the CEO to log in immediately to validate the transactions; otherwise, the account will be frozen. Which of the following BEST describes this email?
A. Spear phishing
B. Impersonation
C. Dumpster diving
D. Whaling
A technician submitted a change control request to upgrade the firmware on all company switches at the same time, during off hours, and through automation. Which of the following change management documents is MOST important to create to ensure the upgrade will not adversely affect the business?
A. Plan for the change
B. Scope of the change
C. Risk analysis of the change
D. Documentation of the change
Which of the following NTFS security settings overrides all other settings?
A. Deny
B. Modify
C. Read
D. Write
A Mac user's operating system became corrupted, and files were deleted after malware was downloaded. The user needs to access the data that was previously stored on the MAC. Which of the following built-in utilities should be used?
A. Time Machine
B. Snapshot
C. System Restore
D. Boot Camp
A corporate fileshare holds files for multiple departments. Individual users in each department create reports that are meant to be read by the rest of the company. Recently, a user ran a malicious executable that encrypted all of the documents on the fileshare. The software asked for money to be transferred via cryptocurrency in order to decrypt the files; however, the files were not decrypted after the company paid the ransom. Which of the following would MOST likely minimize the damage to a fileshare in this type of situation?
A. Enable System Restore on the file server and make frequent restore points.
B. Disable full disk encryption on the file server.
C. Install a next-generation firewall at the network edge.
D. Use a host-based intrusion detection system and continuously monitor filesystem changes.
E. Use granular file permissions on the share and follow the principle of least privilege.
During a network server outage, the administrator's computer received an IP address of 169.254.0.10 and had no access to internal or external resources. Which of the following should be configured to ensure the administrator's computer retains network access?
A. Alternative IP address
B. Wake-on-LAN
C. APIPA
D. Proxy setting
A technician is helping a remote user who has a Windows issue. The user is working from a shared office space and is not on the corporate network. Which of the following remote access methods is MOST likely to be successful in this case?
A. Telnet
B. Remote desktop
C. Third-party screen sharing
D. Secure shell
Free Access Full 220-1002 Practice Exam Free
Looking for additional practice? Click here to access a full set of 220-1002 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your 220-1002 certification journey!