220-1002 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 220-1002 certification exam? Start your preparation the smart way with our 220-1002 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 220-1002 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 220-1002 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
A user reports that an application has been closing unexpectedly for the past two days when posting transactions. When an administrator attempts to access the application, it generates an error stating a data library is missing. Which of the following should a technician attempt FIRST?
A. Uninstall and reinstall the application using the Windows Control Panel.
B. Reinstall the application using the Windows Control Panel
C. Repair the application using the Windows Control Panel.
D. Locate the missing data library and copy it to the Windows program folder.
A Mac user's operating system became corrupted, and files were deleted after malware was downloaded. The user needs to access the data that was previously stored on the MAC. Which of the following built-in utilities should be used?
A. Time Machine
B. Snapshot
C. System Restore
D. Boot Camp
A technician is alerted to a virus on a PC. The technician isolates the PC from the network. After verifying there are no other infected PCs on the network, which of the following is the SAFEST method for the technician to use to clean the infected PC?
A. Download and apply the security patch that addresses the vulnerability that was exploited
B. Use System Restore to bring the PC back to a previous restore point
C. Reimage the computer and update it with all the latest patches
D. Download another antivirus software that will quarantine the virus
Which of the following would MOST likely be connected to a computer to provide electricity in case of a blackout?
A. Battery backup
B. Surge suppressor
C. Portable generator
D. Power inverter
A user installed a new company-approved application on a Windows PC. The installation required a reboot. After the reboot and logon, the system froze. A technician has been called to fix the problem. Which of the following should the technician do FIRST?
A. Contact the application vendor support staff for more information
B. Boot into safe mode, and then load the ERD and restore the most recent files
C. Boot the PC, run msconfig, check the safe boot box under the Boot tab, and then restart
D. Log in as an administrative user and determine if the problem persists
A user's desktop will not run an accounting program. The program's splash screen pops up, and then the software freezes. Which of the following actions should a technician take FIRST to help resolve the issue?
A. Uninstall, reinstall, and restart the application.
B. Reseat the memory.
C. Ensure the PC meets the minimum requirements.
D. Reset the PC display settings.
A technician is working on a user's workstation and notices a lot of unknown processes running in the background. The user informs the technician that an application was recently downloaded from the Internet. Which of the following types of infection does the user MOST likely have?
A. Rootkit
B. Keylogger
C. Trojan
D. Ransomware
A user recently downloaded a JPEG attachment from an email. When the user clicks on the attachment, instead of opening a picture, a small command prompt window appears for several seconds and then disappears. A technician views the file and sees the following:Which of the following Windows Control Panel utilities should the technician use to resolve this issue?
A. Folder Options
B. Display Settings
C. Device Manager
D. Internet Options
Following a recent password change, a user can log on successfully to an Apple computer but cannot access a web-based service. An error message displays each time the user attempts to authenticate to the service. Prior to changing the password, the computer had no communication issues. Which of the following should a technician use to continue troubleshooting the issue?
A. passwd
B. FileVault
C. Keychain
D. Gatekeeper
After a virus has been spread unknowingly via USB removable hard drives, a technician is tasked with limiting removable hard drive access to certain network users. USB ports are used for many devices, including scanners, printers, and signature pads, so a policy is created to deny access to removable hard drives only. When testing the policy, a removable drive is plugged in but can still be accessed. Which of the following command-line tools should the technician use to apply the new policy?
A. grupdate
B. diskpart
C. gpresult
D. net use
A user believes there is a virus on a laptop. The user installs additional real-time protection antivirus software but is now experiencing extremely slow performance on the laptop. Which of the following should a technician do to resolve the issue and avoid recurrence?
A. Activate real-time protection on both antivirus software programs
B. Uninstall one antivirus software program and install a different one
C. Run OS updates
D. Enable the quarantine feature on both antivirus software programs
E. Remove the user-installed antivirus software
A user has reported that a computer is running extremely slow when opening applications. A technician checks the computer and needs to verify memory utilization. Which of the following tools should the technician use to begin troubleshooting the issue?
A. Task Scheduler
B. Device Manager
C. Drive Status
D. Performance
Joe, a user, reports that several of his colleagues have received a suspicious email from his account that he did not send. A technician asks one of the colleagues to forward the email for inspection. After ruling out spoofing, the technician verifies the email originated from the corporate email server. Which of the following is the FIRST step the technician should take to correct this issue?
A. See if Joe’s email address has been blacklisted
B. Change the password on Joe’s email account
C. Update the antivirus and perform a full scan on the PC
D. Isolate Joe’s computer from the network
Which of the following is considered government-regulated data?
A. PHI
B. End-user license agreement
C. Digital Millennium Copyright Act
D. DRM
Which of the following is the MOST secure wireless security protocol?
A. AES
B. WPA
C. WPA2
D. WEP
Ann, a user, has purchased a new Android phone and is attempting to access a public hotspot. When she opens a browser, she gets a message indicating the page cannot be displayed. She notices there is a `?` in the radio icon in the toolbar. She has verified Bluetooth is active, airplane mode is off, and tethering is turned on. She uses the cell phone to call a technician for assistance. Which of the following is the MOST likely issue Ann is experiencing?
A. There is unauthenticated wireless connectivity
B. She has exceeded the data allowance
C. The phone is only 3G capable
D. It is an unrooted phone
E. The SIM card was not activated
F. A data plan was not purchased
Joe, an employee, took a company-issued Windows laptop home, but is having trouble connecting to any of the shares hosted on his home media server. Joe has verified he is connected to the Internet. Which of the following would explain why Joe cannot access his personal shares?
A. An IP conflict is present
B. A corporate VPN is enabled
C. A firewall exception must be set
D. HomeGroup must be enabled
A Mac user needs to configure a network device using a serial connection to enable a remote network connection. Which of the following utilities would MOST likely be used to make the necessary changes?
A. Terminal
B. Disk maintenance
C. iCloud
D. Image recovery
Which of the following extensions identify files that are typically implemented as scripts? (Choose two.)
A. .vbs
B. .txt
C. .exe
D. .zip
E. .bat
F. .xlsx
A manager requests remote access to a server after hours and on weekends to check data. The manager insists on using the server. Before granting the access, which of the following is the MOST important step a technician can take to protect against possible infection?
A. Create a policy to remove Internet access from the server during off hours
B. Set the local antivirus software on the server to update and scan daily
C. Ensure the server is patched with the latest security updates
D. Educate the manager on safe Internet browsing practices
A user is attempting to create a Windows fileshare on a Windows 10 workstation in a small peer-to-peer environment. The user is logged in with a Microsoft account. Which of the following would be the MOST secure way to allow other users to access the share?
A. Create a new local user for peer-to-peer share access.
B. Provide other users with the Microsoft account information.
C. Set the share permissions to Everyone/Full Control.
D. Enable the local guest account access.
An executive has contacted you through the help-desk chat support about an issue with a mobile device. Assist the executive to help resolve the issue. INSTRUCTIONS - Select the MOST appropriate statement for each response. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.Let's take a look at your phone settings.
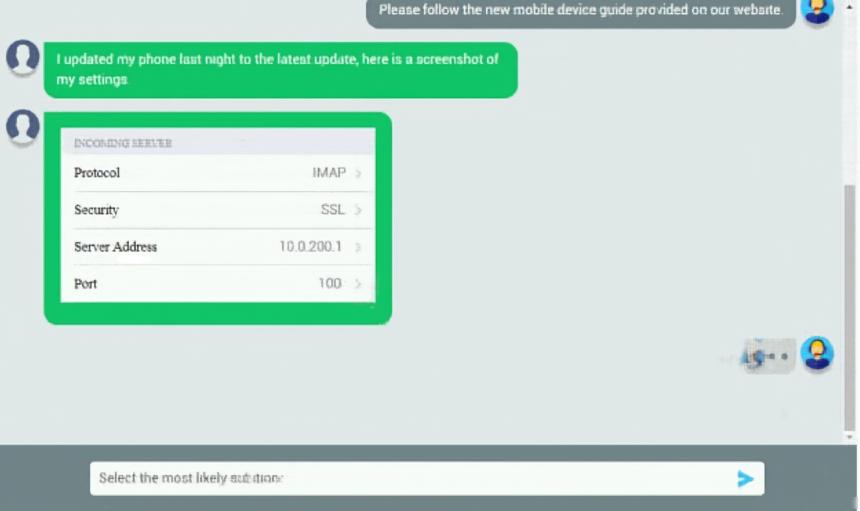
Please change the port number on your mail settings to 993. Which of the following should be done NEXT?
A. Close the ticket out
B. Educate the user on the solution that was performed
C. Tell the user to take time to fix it themselves next time
D. Send an email to Telecom to inform them of the issue and prevent reoccurrence
Which of the following are typically too dangerous to be disassembled by an in-house technician? (Choose two.)
A. LCD monitor
B. Power supply
C. Laptop screen
D. CRT monitor
E. Motherboard
F. Tablet
A technician is in the process of removing a recently discovered Trojan horse application from a user's laptop. Which of the following should the technician complete to prevent reinfection of the same machine?
A. Reenable Windows System Restore after rebooting the device.
B. Research the symptoms to identify the threat.
C. Update the operating system and anti-malware signatures.
D. Isolate the infected machine from all networks.
A technician is working on a desktop computer that is not performing as expected. Program windows sometimes open and close without user intervention. Windows cannot check for OS updates, and some websites are not accessible. Which of the following tasks should the technician perform FIRST?
A. Roll back recent driver updates.
B. Replace the defective keyboard.
C. Reset all the settings in the Internet Options.
D. Unplug the Ethernet cable.
A technician repaired a laptop for a customer. The customer then complained the repair took too long and questioned the steps the technician took to fix the problem. Which of the following should the technician do NEXT?
A. Provide documentation of the repair to the customer
B. Allow the customer to voice concerns and post the story to social media later
C. Inform the customer the job is done and return to the office
D. Defend each step and why it was necessary
A technician is removing malware from a workstation. The malware was installed via a phishing attack, which was initiated from a link that was included in an email. Which of the following should the technician do to address this issue? (Choose two.)
A. Ensure the anti-rootkit utility is up to date and run it to remove the threat.
B. Update the host firewall to block port 80 on the workstation.
C. Restore the system using the last known-good configuration from the recovery console.
D. Ensure antivirus is up to date and install the latest patches.
E. Educate the user on verifying email links by hovering over them before clicking.
F. Ensure endpoint protection is up to date and run the utility to remove the threat.
Which of the following is a reason to use WEP over WPA?
A. Device compatibility
B. Increased security
C. TACACS
D. Multifactor authentication
Which of the following operating systems has versions for servers, workstations, and phones?
A. Android
B. iOS
C. Chrome OS
D. Windows
A customer is having issues with an Android-based smartphone after a recent application update. The application becomes unresponsive immediately after attempting to open it. Auto-sync is not enabled, and no recent backups exist for the smartphone. Without losing any critical information, which of the following should be performed NEXT to further troubleshoot the issue? (Choose two.)
A. Reboot into safe mode
B. Clear the application data
C. Contact the application’s developer
D. Reinstall the application
E. Do a force stop
F. Clear the application cache
A user receives an error message when trying to upgrade an application on a work computer. Which of the following is the MOST likely reason the user cannot complete this task?
A. The computer does not meet the application’s minimum requirements.
B. The program is being deployed via optical media.
C. The user account lacks administrative rights.
D. A 32-bit application cannot be installed on a 64-bit system.
A technician responds to a report that a user's desktop is operating much slower after upgrading the Windows OS to the latest version. The technician notices responsiveness is erratic, and the symptoms are similar to a failing hard drive. The technician runs a full hardware diagnostic, and all systems pass. The technician checks the properties for each device in Device Manager and the hard disk and the standard AHCI 1.0 serial ATA controller both indicate the following message: This device is working properly. Which of the following should the technician attempt that will MOST likely resolve the performance issue?
A. Roll back the OS upgrade. Continue using the older version of Windows
B. Reset the PC to its factory conditions. Perform the OS upgrade again
C. Update the SATA controller driver from the manufacturer’s website
D. Perform a full backup and replace the hard drive
A user is trying to install a very large .dmg file on a Windows computer but is receiving an error message. Which of the following is causing the error?
A. Small hard drive
B. Insufficient RAM
C. OS compatibility
D. Folder permissions
A company recently experienced a security incident in which an unauthorized user was able to insert a USB flash drive into a kiosk, launch a non-native OS, and deliver malicious payloads across the network. Which of the following security measures would have been BEST to prevent the attack from being executed in the first place? (Choose two.)
A. Using a host-based antivirus with real-time scanning
B. Implementing automatic screen locks after 60 seconds of inactivity
C. Creating a strong BIOS/UEFI password
D. Disabling AutoRun for USB devices
E. Enabling the Secure Boot option
F. Changing the default administrator credentials
A technician needs to connect to a server using a secure terminal application. The technician must be able to reboot the server quickly and restart all the daemons with this application. Which of the following methods will the technician MOST likely use? (Choose two.)
A. SSH
B. Telnet
C. Putty
D. HTTPS
E. Remote Assistance
F. RDP
Which of the following variable types should be used to store the data `Chicago` within a script or code?
A. Integer
B. String
C. Boolean
D. Float
A technician is troubleshooting a network connectivity issue on a Linux workstation. Which of the following commands would help the technician gain information about the network settings on the machine?
A. chmod
B. grep
C. ifconfig
D. sudo
A user wants to see the workstations present on the LAN in a workgroup environment. Which of the following settings must be enabled to make this possible?
A. Turn off public folder sharing
B. Turn on network discovery
C. Use 128-bit encryption
D. Turn on file and folder sharing
After connecting to the corporate VPN, a user's workstation is no longer to browse Internet websites. A technician discovers launching a different web browser on the same computer reaches the websites correctly. Which of the following should the technician do NEXT?
A. Verify the browser’s proxy configuration settings
B. Instruct the user to use the alternate web browser instead
C. Flush the workstation’s DNS cache
D. Scan the user’s workstation for malware
E. Disconnect and reconnect from the corporate VPN
Which of the following is a device that stores a copy of a certificate that is used for authentication?
A. Biometric scanner
B. Soft token
C. Smart card
D. OTP token
A junior Linux systems administrator needs to update system software. Which of the following shell commands would allow the administrator to gain the necessary permissions to update the software?
A. sudo
B. chmod
C. grep
D. pwd
Which of the following would a technician use to store memory chips from a laptop safely after an upgrade?
A. Mylar bags
B. Cardboard boxes
C. Antistatic containers
D. Paper envelopes
A technician is troubleshooting a PC and identifies the issue as malware. To remediate the PC, the technician attempts to download a malware removal tool but finds the PC cannot connect to the Internet. Which of the following MOST likely explains why the PC cannot access the Internet?
A. The PC is quarantined.
B. System Restore is disabled.
C. The PC is currently running antivirus.
D. Malware corrupted the NIC drivers.
A technician is repairing a computer's motherboard in a clean environment. The technician needs to ensure all necessary safety procedures are taken prior to performing the replacement. Which of the following should the technician employ during this process to ensure safety? (Choose two.)
A. CPU paste
B. Safety goggles
C. Self-grounding
D. ESD straps
E. Antistatic bag
F. Air filter mask
A technician is installing a private PC in a public workspace. Which of the following password practices should the technician implement on the PC to secure network access?
A. Remove the guest account from the administrators group
B. Disable single sign-on
C. Issue a default strong password for all users
D. Require authentication on wake-up
Which of the following best practices should a technician observe to reduce the risk of electrical shock?
A. Keep components in an anti-static bag.
B. Remove metallic jewelry.
C. Utilize proper cable management.
D. Wear an ESD wrist strap.
A computer's power light is on, but the screen is completely black. The user is unable to wake the computer and then contacts a technician. The technician asks the user to inspect the display cable, but it is securely connected at each end. Which of the following steps should the technician ask the user to take NEXT?
A. Roll back the Windows updates
B. Perform a startup recovery
C. Perform a hard restart
D. Boot from the last known-good configuration
A sales representative regularly modifies confidential files on a laptop and needs them to be available all the time. The sales representative will be on a six-month business trip in two weeks. A technician has been asked to assist the sales representative with saving files. Which of the following is the BEST method to implement to prevent any data loss for the sales representative?
A. Give the sales representative a USB security lock.
B. Encrypt the laptop’s image on the server.
C. Create a redundant cloud storage drive.
D. Give the sales representative an external hard drive.
Which of the following allows for per-command authentication and authorization?
A. TKIP
B. RADIUS
C. AES
D. TACACS
A Windows user logs on to a network domain computer after recently being switched to a roaming profile. The user reports extremely long startup times. Which of the following should a technician check to address this issue?
A. The amount of data on the user’s desktop.
B. The total quantity of RAM installed on the computer.
C. The free space available on the network share.
D. The size of the Windows swap file.
Access Full 220-1002 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 220-1002 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 220-1002 mock test free today—and take a major step toward exam success!

