212-89 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 212-89 certification exam? Start your preparation the smart way with our 212-89 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 212-89 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 212-89 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
A security policy will take the form of a document or a collection of documents, depending on the situation or usage. It can become a point of reference in case a violation occurs that results in dismissal or other penalty. Which of the following is NOT true for a good security policy?
A. It must be enforceable with security tools where appropriate and with sanctions where actual prevention is not technically feasible
B. It must be approved by court of law after verifications of the stated terms and facts
C. It must be implemented through system administration procedures, publishing of acceptable use guide lines or other appropriate methods
D. It must clearly define the areas of responsibilities of the users, administrators and management
An estimation of the expected losses after an incident helps organization in prioritizing and formulating their incident response. The cost of an incident can be categorized as a tangible and intangible cost. Identify the tangible cost associated with virus outbreak?
A. Loss of goodwill
B. Damage to corporate reputation
C. Psychological damage
D. Lost productivity damage
Based on the some statistics; what is the typical number one top incident?
A. Phishing
B. Policy violation
C. Un-authorized access
D. Malware
In a qualitative risk analysis, risk is calculated in terms of:
A. (Attack Success + Criticality ) “”(Countermeasures)
B. Asset criticality assessment “” (Risks and Associated Risk Levels)
C. Probability of Loss X Loss
D. (Countermeasures + Magnitude of Impact) “” (Reports from prior risk assessments)
Incidents such as DDoS that should be handled immediately may be considered as:
A. Level One incident
B. Level Two incident
C. Level Three incident
D. Level Four incident
A computer Risk Policy is a set of ideas to be implemented to overcome the risk associated with computer security incidents. Identify the procedure that is NOT part of the computer risk policy?
A. Procedure to identify security funds to hedge risk
B. Procedure to monitor the efficiency of security controls
C. Procedure for the ongoing training of employees authorized to access the system
D. Provisions for continuing support if there is an interruption in the system or if the system crashes
The role that applies appropriate technology and tries to eradicate and recover from the incident is known as:
A. Incident Manager
B. Incident Analyst
C. Incident Handler
D. Incident coordinator
The Malicious code that is installed on the computer without user's knowledge to acquire information from the user's machine and send it to the attacker who can access it remotely is called:
A. Spyware
B. Logic Bomb
C. Trojan
D. Worm
Which of the following is an appropriate flow of the incident recovery steps?
A. System Operation-System Restoration-System Validation-System Monitoring
B. System Validation-System Operation-System Restoration-System Monitoring
C. System Restoration-System Monitoring-System Validation-System Operations
D. System Restoration-System Validation-System Operations-System Monitoring
The largest number of cyber-attacks are conducted by:
A. Insiders
B. Outsiders
C. Business partners
D. Suppliers
Risk is defined as the probability of the occurrence of an incident. Risk formulation generally begins with the likeliness of an event's occurrence, the harm it may cause and is usually denoted as Risk = ∑(events)X(Probability of occurrence)X?
A. Magnitude
B. Probability
C. Consequences
D. Significance
A payroll system has a vulnerability that cannot be exploited by current technology. Which of the following is correct about this scenario:
A. The risk must be urgently mitigated
B. The risk must be transferred immediately
C. The risk is not present at this time
D. The risk is accepted
An assault on system security that is derived from an intelligent threat is called:
A. Threat Agent
B. Vulnerability
C. Attack
D. Risk
The Linux command used to make binary copies of computer media and as a disk imaging tool if given a raw disk device as its input is:
A. “dd” command
B. “netstat” command
C. “nslookup” command
D. “find” command
Computer forensics is methodical series of techniques and procedures for gathering evidence from computing equipment, various storage devices and or digital media that can be presented in a course of law in a coherent and meaningful format. Which one of the following is an appropriate flow of steps in the computer forensics process:
A. Examination> Analysis > Preparation > Collection > Reporting
B. Preparation > Analysis > Collection > Examination > Reporting
C. Analysis > Preparation > Collection > Reporting > Examination
D. Preparation > Collection > Examination > Analysis > Reporting
Which of the following incident recovery testing methods works by creating a mock disaster, like fire to identify the reaction of the procedures that are implemented to handle such situations?
A. Scenario testing
B. Facility testing
C. Live walk-through testing
D. Procedure testing
Which of the following is an incident tracking, reporting and handling tool:
A. CRAMM
B. RTIR
C. NETSTAT
D. EAR/ Pilar
Insider threats can be detected by observing concerning behaviors exhibited by insiders, such as conflicts with supervisors and coworkers, decline in performance, tardiness or unexplained absenteeism. Select the technique that helps in detecting insider threats:
A. Correlating known patterns of suspicious and malicious behavior
B. Protecting computer systems by implementing proper controls
C. Making is compulsory for employees to sign a none disclosure agreement
D. Categorizing information according to its sensitivity and access rights
Which of the following incidents are reported under CAT -5 federal agency category?
A. Exercise/ Network Defense Testing
B. Malicious code
C. Scans/ probes/ Attempted Access
D. Denial of Service DoS
A distributed Denial of Service (DDoS) attack is a more common type of DoS Attack, where a single system is targeted by a large number of infected machines over the Internet. In a DDoS attack, attackers first infect multiple systems which are known as:
A. Trojans
B. Zombies
C. Spyware
D. Worms
An audit trail policy collects all audit trails such as series of records of computer events, about an operating system, application or user activities. Which of the following statements is NOT true for an audit trail policy:
A. It helps calculating intangible losses to the organization due to incident
B. It helps tracking individual actions and allows users to be personally accountable for their actions
C. It helps in compliance to various regulatory laws, rules,and guidelines
D. It helps in reconstructing the events after a problem has occurred
ADAM, an employee from a multinational company, uses his company's accounts to send e-mails to a third party with their spoofed mail address. How can you categorize this type of account?
A. Inappropriate usage incident
B. Unauthorized access incident
C. Network intrusion incident
D. Denial of Service incident
Bit stream image copy of the digital evidence must be performed in order to:
A. Prevent alteration to the original disk
B. Copy the FAT table
C. Copy all disk sectors including slack space
D. All the above
A risk mitigation strategy determines the circumstances under which an action has to be taken to minimize and overcome risks. Identify the risk mitigation strategy that focuses on minimizing the probability of risk and losses by searching for vulnerabilities in the system and appropriate controls:
A. Risk Assumption
B. Research and acknowledgment
C. Risk limitation
D. Risk absorption
Identify the network security incident where intended authorized users are prevented from using system, network, or applications by flooding the network with high volume of traffic that consumes all existing network resources.
A. URL Manipulation
B. XSS Attack
C. SQL Injection
D. Denial of Service Attack
The left over risk after implementing a control is called:
A. Residual risk
B. Unaccepted risk
C. Low risk
D. Critical risk
Incident management team provides support to all users in the organization that are affected by the threat or attack. The organization's internal auditor is part of the incident response team. Identify one of the responsibilities of the internal auditor as part of the incident response team:
A. Configure information security controls
B. Perform necessary action to block the network traffic from suspected intruder
C. Identify and report security loopholes to the management for necessary actions
D. Coordinate incident containment activities with the information security officer
One of the main objectives of incident management is to prevent incidents and attacks by tightening the physical security of the system or infrastructure. According to CERT's incident management process, which stage focuses on implementing infrastructure improvements resulting from postmortem reviews or other process improvement mechanisms?
A. Protection
B. Preparation
C. Detection
D. Triage
Which one of the following is the correct sequence of flow of the stages in an incident response:
A. Containment – Identification – Preparation – Recovery – Follow-up – Eradication
B. Preparation – Identification – Containment – Eradication – Recovery – Follow-up
C. Eradication – Containment – Identification – Preparation – Recovery – Follow-up
D. Identification – Preparation – Containment – Recovery – Follow-up – Eradication
Which of the following terms may be defined as "a measure of possible inability to achieve a goal, objective, or target within a defined security, cost plan and technical limitations that adversely affects the organization's operation and revenues?
A. Risk
B. Vulnerability
C. Threat
D. Incident Response
A malware code that infects computer files, corrupts or deletes the data in them and requires a host file to propagate is called:
A. Trojan
B. Worm
C. Virus
D. RootKit
The ability of an agency to continue to function even after a disastrous event, accomplished through the deployment of redundant hardware and software, the use of fault tolerant systems, as well as a solid backup and recovery strategy is known as:
A. Business Continuity Plan
B. Business Continuity
C. Disaster Planning
D. Contingency Planning
Adam calculated the total cost of a control to protect 10,000 $ worth of data as 20,000 $. What do you advise Adam to do?
A. Apply the control
B. Not to apply the control
C. Use qualitative risk assessment
D. Use semi-qualitative risk assessment instead
A Malicious code attack using emails is considered as:
A. Malware based attack
B. Email attack
C. Inappropriate usage incident
D. Multiple component attack
Organizations or incident response teams need to protect the evidence for any future legal actions that may be taken against perpetrators that intentionally attacked the computer system. EVIDENCE PROTECTION is also required to meet legal compliance issues. Which of the following documents helps in protecting evidence from physical or logical damage:
A. Network and host log records
B. Chain-of-Custody
C. Forensic analysis report
D. Chain-of-Precedence
An adversary attacks the information resources to gain undue advantage is called:
A. Defensive Information Warfare
B. Offensive Information Warfare
C. Electronic Warfare
D. Conventional Warfare
A threat source does not present a risk if NO vulnerability that can be exercised for a particular threat source. Identify the step in which different threat sources are defined:
A. Identification Vulnerabilities
B. Control analysis
C. Threat identification
D. System characterization
The correct sequence of Incident Response and Handling is:
A. Incident Identification, recording, initial response, communication and containment
B. Incident Identification, initial response, communication, recording and containment
C. Incident Identification, communication, recording, initial response and containment
D. Incident Identification, recording, initial response, containment and communication
An access control policy authorized a group of users to perform a set of actions on a set of resources. Access to resources is based on necessity and if a particular job role requires the use of those resources. Which of the following is NOT a fundamental element of access control policy
A. Action group: group of actions performed by the users on resources
B. Development group: group of persons who develop the policy
C. Resource group: resources controlled by the policy
D. Access group: group of users to which the policy applies
A computer virus hoax is a message warning the recipient of non-existent computer virus. The message is usually a chain e-mail that tells the recipient to forward it to every one they know. Which of the following is NOT a symptom of virus hoax message?
A. The message prompts the end user to forward it to his / her e-mail contact list and gain monetary benefits in doing so
B. The message from a known email id is caught by SPAM filters due to change of filter settings
C. The message warns to delete certain files if the user does not take appropriate action
D. The message prompts the user to install Anti-Virus
What command does a Digital Forensic Examiner use to display the list of all IP addresses and their associated MAC addresses on a victim computer to identify the machines that were communicating with it:
A. “arp” command
B. “netstat “”an” command
C. “dd” command
D. “ifconfig” command
The service organization that provides 24x7 computer security incident response services to any user, company, government agency, or organization is known as:
A. Computer Security Incident Response Team CSIRT
B. Security Operations Center SOC
C. Digital Forensics Examiner
D. Vulnerability Assessor
What is correct about Quantitative Risk Analysis:
A. It is Subjective but faster than Qualitative Risk Analysis
B. Easily automated
C. Better than Qualitative Risk Analysis
D. Uses levels and descriptive expressions
Computer viruses are malicious software programs that infect computers and corrupt or delete the data on them. Identify the virus type that specifically infects Microsoft Word files?
A. Micro Virus
B. File Infector
C. Macro Virus
D. Boot Sector virus
Incident handling and response steps help you to detect, identify, respond and manage an incident. Which of the following steps focus on limiting the scope and extent of an incident?
A. Eradication
B. Containment
C. Identification
D. Data collection
A US Federal agency network was the target of a DoS attack that prevented and impaired the normal authorized functionality of the networks. According to agency's reporting timeframe guidelines, this incident should be reported within two (2) HOURS of discovery/detection if the successful attack is still ongoing and the agency is unable to successfully mitigate the activity. Which incident category of the US Federal Agency does this incident belong to?
A. CAT 5
B. CAT 1
C. CAT 2
D. CAT 6
Which of the following service(s) is provided by the CSIRT:
A. Vulnerability handling
B. Technology watch
C. Development of security tools
D. All the above
Which policy recommends controls for securing and tracking organizational resources:
A. Access control policy
B. Administrative security policy
C. Acceptable use policy
D. Asset control policy
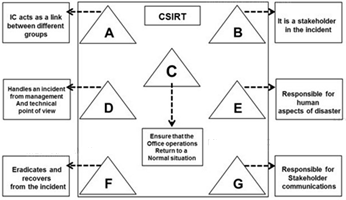
The flow chart gives a view of different roles played by the different personnel of CSIRT. Identify the incident response personnel denoted by A, B, C, D, E, F and G.
A. A-Incident Analyst, B- Incident Coordinator, C- Public Relations, D-Administrator, E- Human Resource, F-Constituency, G-Incident Manager
B. A- Incident Coordinator, B-Incident Analyst, C- Public Relations, D-Administrator, E- Human Resource, F-Constituency, G-Incident Manager
C. A- Incident Coordinator, B- Constituency, C-Administrator, D-Incident Manager, E- Human Resource, F-Incident Analyst, G-Public relations
D. A- Incident Manager, B-Incident Analyst, C- Public Relations, D-Administrator, E- Human Resource, F-Constituency, G-Incident Coordinator
Except for some common roles, the roles in an IRT are distinct for every organization. Which among the following is the role played by the Incident Coordinator of an IRT?
A. Links the appropriate technology to the incident to ensure that the foundation’s offices are returned to normal operations as quickly as possible
B. Links the groups that are affected by the incidents, such as legal, human resources, different business areas and management
C. Applies the appropriate technology and tries to eradicate and recover from the incident
D. Focuses on the incident and handles it from management and technical point of view
Access Full 212-89 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 212-89 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 212-89 mock test free today—and take a major step toward exam success!