200-901 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the 200-901 certification? Take your preparation to the next level with our 200-901 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a 200-901 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic 200-901 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
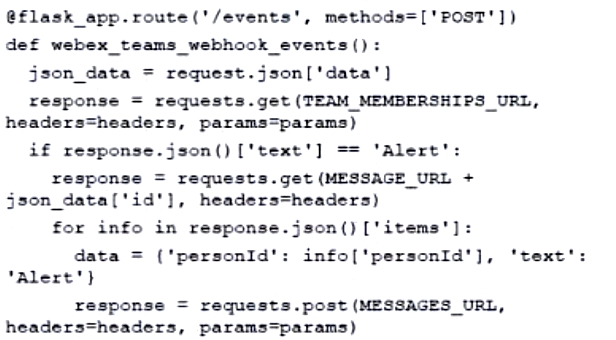
Refer to the exhibit. Which code snippet represents the sequence.
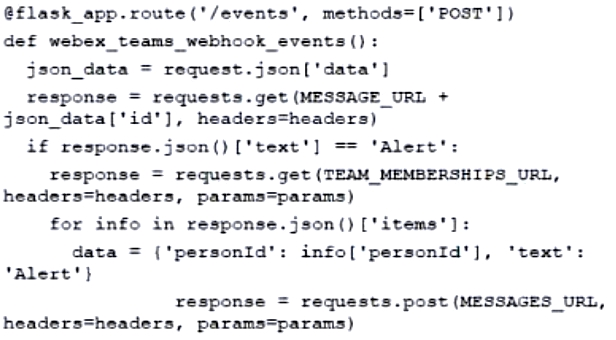
A.
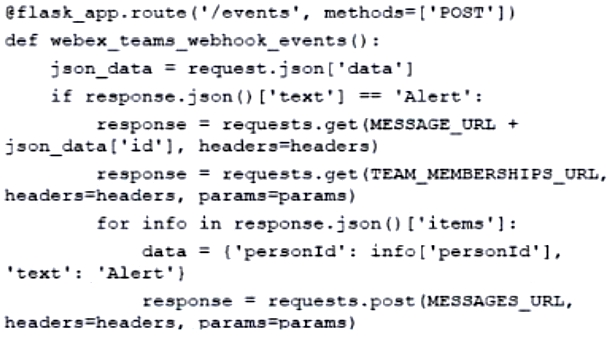
Refer to the exhibit. Which command, including arguments, is executed when the container starts?
A. /bin/sh -c “/bin/sleep 30 && nginx -g ‘daemon off;'”
B. /bin/sh -c “/bin/sleep 10 && nginx -g ‘daemon off;'”
C. /bin/bash -c “/bin/sleep 30 && nginx -g ‘daemon off;'”
D. /bin/sh -c “/bin/sleep 30” && nginx -g ‘daemon off;’
Refer to the exhibit. A network engineer executes the bash script shown. Which two things are achieved by running the script? (Choose two.)
A. A directory called PRODUCTION is created.
B. The engineer changes to the parent directory.
C. A YAML file is created.
D. A YAML file is removed.
E. A directory called state.yml is created.
Which OWASP threat occurs when untrusted data is supplied as input to an interpreter as part of a command or query?
A. broken authentication
B. data exposure
C. injection
D. cross-site scripting
What is a benefit of a distributed version control system?
A. encourages users to commit small places of work to the system more frequently
B. ensures that all code meets minimum standards before being committed to the system
C. allows users to work on the codebase even when not connected to the Internet
D. ensures that all code is tested before being committed to the system
What is the benefit of organizing data into functions?
A. supports using same variable in different modules
B. supports altering the state of an object
C. organize code in a reusable way
D. stores data values of different types
A developer improves the code repository to clean a bug on the custom network monitoring application. The developer adds the changes to the staging area and then commits on the local branch. Which command pushes commits that are made on a local branch to the remote repository?
A. push origin master
B. git push all
C. push all
D. git push origin master
Refer to the exhibit. A software engineer needs to collect data about devices that are registered in Cisco DNA Center using the API. Before collecting the data, the engineer must obtain a token and authenticate with the API. To automate the procedure, a Python script is used. Which code snippet must be placed onto the blank in the code?
A. get(uri,headers = headers,data={}, verify-True)
B. post(uri,headers=headers,data={}, verify=False)
C. get(uri,headers= headers,data={}, verify=False)
D. post(uri,headers=headers,data={“Basic”}, verify=False)
What is a benefit of using model-driven programmability on Cisco devices?
A. deeper monitoring
B. better logging
C. automated configuration
D. increased security
A distributed application is under development and the interaction between the application and an API is being tested using the URL and port: devasc468262987.com port 443 The requests that were sent to the server could not execute because the application was blocked by the firewall. Which protocol must be allowed by the firewall to fix the issue?
A. SSH
B. HTTP
C. HTTPS
D. FTP
What are two advantages of model-driven programmability as compared to traditional network management? (Choose two.)
A. standardized transport protocol
B. better performance
C. better visibility and control
D. device abstraction
E. access to more routing features
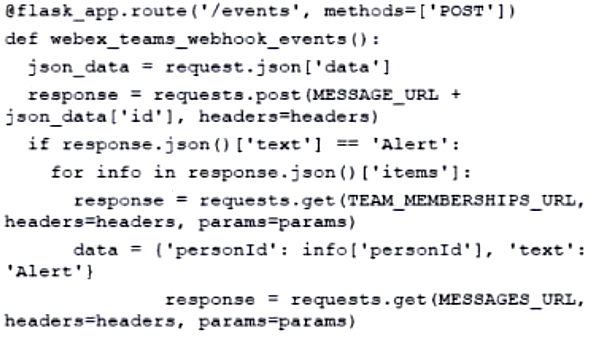
Refer to the exhibit. What is the result of running the Docker file?
A. Copy the directory /app from the ubuntu:18.04 image, build it with make, and execute the application with the Python command.
B. Copy the directory app from the current directory of the Docker client, execute the application with make, and after it runs, execute an additional application.
C. Copy the directory app from the current directory of the Docker client, build it with make, and execute the application with the Python command.
D. Copy the /app directory from the ubuntu:18.04 image, execute the application with make, and after it runs, execute an additional application.
What is a feature of a MAC address?
A. It consists of 38 bits.
B. It consists of 12 hexadecimal numbers.
C. It consists of 6 hexadecimal numbers.
D. It consists of 24 bits.
Refer to the exhibit.Which OWASP threat does this example demonstrate?
A. broken access control
B. cross-site scripting
C. SQL injection
D. man-in-the-middle
Which port does HTTPS use by default?
A. 433
B. 443
C. 803
D. 883
What is a benefit of using Python classes?
A. They improve code organization by keeping data members and methods together.
B. They remove the concept of inheritance to improve code readability and maintainability.
C. They allow a Python script to import code from various independent modules.
D. They simplify integration by testing the classes independently from other components.
Refer to the exhibit. The sequence diagram shows a RESTful API call. Which step and response will represent the behavior of the REST API call to be synchronous?
A. POST/discovery/ when there is a slot available and get the response from the POST call with the discovery details.
B. GET/discovery/ when the discovery is nished and get the response from the GET call with the discovery requirements.
C. POST/discovery?discoveryid= when the discovery is created and get the response from the POST call with the discovery details.
D. PUT/discovery/ when the discovery is created and get the response of the discovery when it is updated.
A small company has 5 servers and 50 clients. What are two reasons an engineer should split this network into separate client and server subnets? (Choose two.)
A. Subnets will split domains to limit failures.
B. A router will limit the traffic types between the clients and servers.
C. Subnets provide more IP address space for clients and servers.
D. A router will bridge the traffic between clients and servers.
E. Internet access to the servers will be denied on the router.
What is the benefit of edge computing?
A. It reduces network latency by moving processing closer to the data source.
B. It reduces data velocity from devices or other data sources.
C. It simpli es security as devices and processing are brought closer together.
D. It removes the need for centralized data processing.
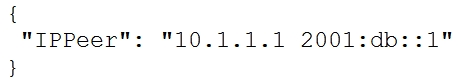
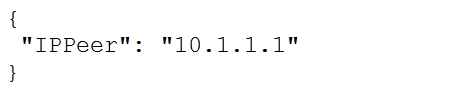
Refer to the exhibit.What is the value of the node defined by this YANG structure?

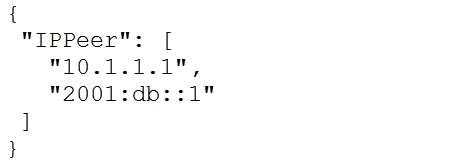
A developer is trying to retrieve data over a REST API. The API server responds with an HTTP client error response code. After investigating the response, the developer realizes the response has a Retry-After header. What is the root cause of this error?
A. An appliance limited the rate of requests to the transport layer.
B. The REST service is unreachable at the time of the REST request.
C. Too many requests were sent to the REST service in a given amount of time.
D. An appliance limited the rate of requests to the application layer.
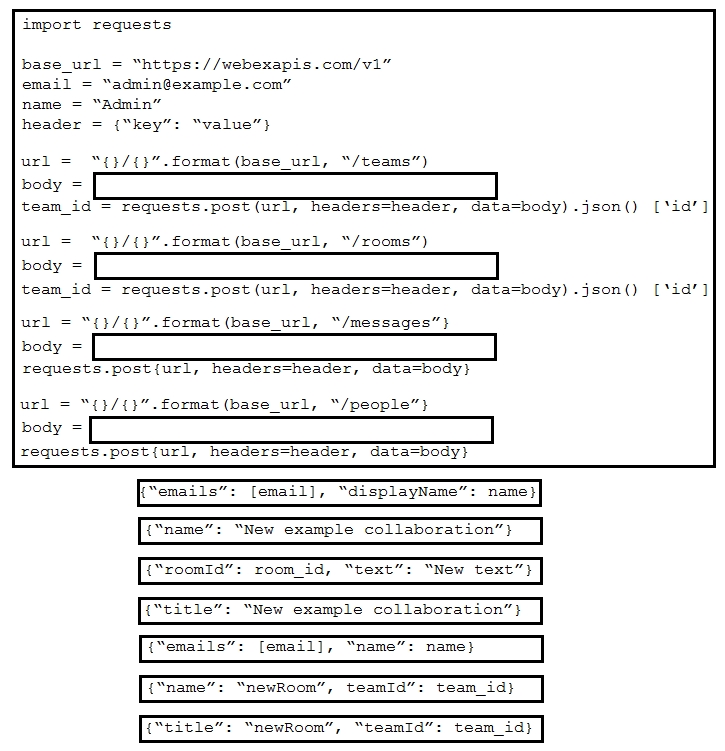
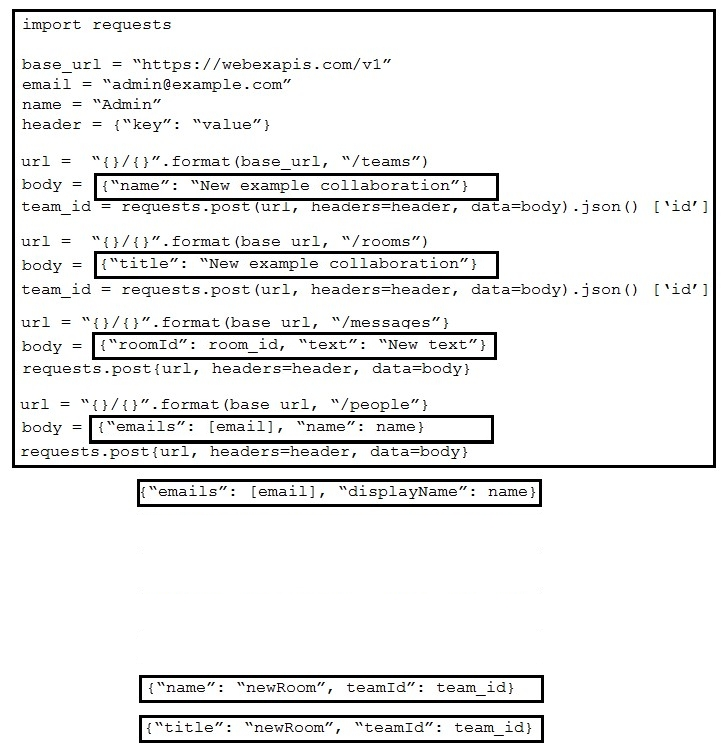
Refer to the exhibit. A script must create a new team, create a new space, send a message, and create a participant. Drag and drop the code snippets from the bottom onto the boxes in the code to complete the script. Not all options are used.
Select and Place:
What are two use cases where webhooks are effective? (Choose two.)
A. Filter out information from a response to an API call.
B. Close a session with a web server after a specific amount of time.
C. Inform a previously defined chat channel after a deployment fails.
D. Send an email to a customer of an online store after payment is complete.
E. Change the response format or content type of an API call.
Which solution reduces costs from MPLS, improves application performance, and simpli es operations?
A. Cisco NSO
B. Cisco SD-WAN
C. Cisco ACI
D. Cisco DNA Center
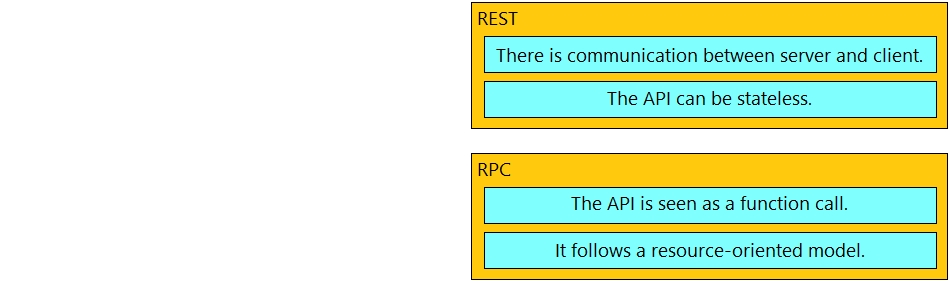
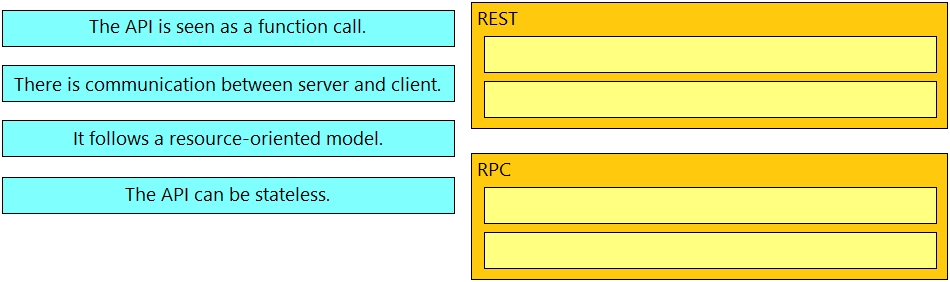
Drag and drop the API characteristics from the left onto the categories on the right.
Select and Place:
Access to the management interface of devices must be restricted by using SSH and HTTPS. Which two ports must be included in the ACLs for the protocols to work? (Choose two.)
A. 22
B. 23
C. 80
D. 443
E. 880
Refer to the exhibit. An engineer wants to create a Bash script to automate a workflow that is related to a machine learning-based application. The engineer wants to use the application as a container and use an image from the open-source public repository. What is accomplished by the script?
A. Create a new software package
B. Install and remove files.
C. Update an existing software package.
D. Install a software package.
Which method should be used to safely store the API keys?
A. in an environment variable unique to the system database
B. encrypted in a configuration file that is separate from the code
C. plain text in the code as a constant
D. encrypted in the code in a function
Refer to the exhibit.What is represented in this YANG module?
A. interface management
B. BGP
C. OpenFlow
D. topology
What is the first development task in test-driven development?
A. Write code that implements a desired function.
B. Write a failing test case for a desired function.
C. Reverse engineer the code for a desired function.
D. Write a passing test case for existing code.
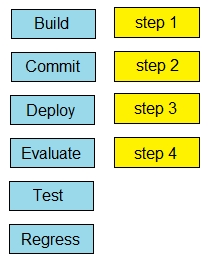
Drag and drop the steps from the left into order on the right to create a common CI/CD pipeline process. Not all options are used.
Select and Place:
Which Cisco compute management platform controls server, network, storage, and virtual resources with policy-driven management for up to 10000 physical Cisco servers?
A. UCS Central
B. Cisco Intersight
C. Cisco DNA Center
D. Cisco HyperFlex
What is impacted by the network bandwidth on an application?
A. time taken for a data packet to travel between two endpoints
B. number of data packets dropped during transmission
C. consistency in the arrival of data packets between two endpoints
D. rate of data transferred between two endpoints
A developer has created a three-tier web application for network device control and management. The application consists of multiple objects assigned for different functionalities. The architecture of the application is based on the Observer pattern. Which advantage does this pattern provide for the application design and architecture?
A. Independent observers are updated automatically.
B. It updates the state of dependent subjects directly.
C. One observer can query the state of other subjects
D. It decouples the subjects from the observers.
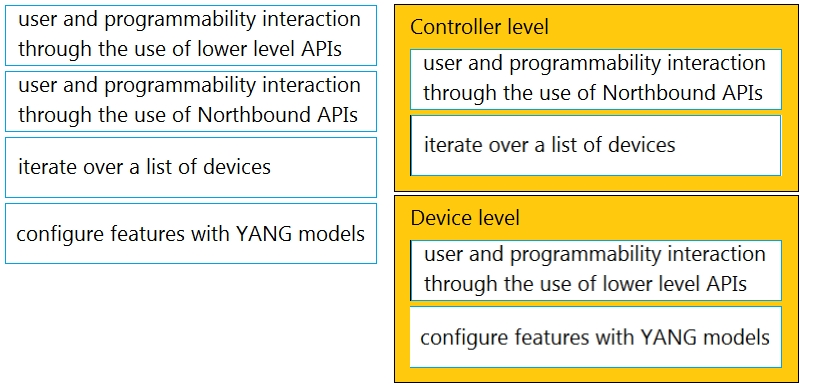
Drag and drop the capability on the left onto the Cisco compute management platform that supports the capability on the right.
Select and Place:

What are two key capabilities of Cisco Finesse? (Choose two.)
A. Agents access Finesse from a browser without needing to install or configure anything on the client machine.
B. An OpenDNS utility is preconfigured and ready to use on Finesse.
C. Gadget containers provide a seamless experience in a single user interface.
D. Finesse automatically collects telemetry data.
E. Finesse includes an RPC API that enables the development of custom gadgets.
Refer to the exhibit. Which HTTP code is returned after the RESTCONF query is executed?
A. 201
B. 204
C. 302
D. 304
An application developer deploys several applications on the same server. The environment runs on a single operating system and allows the developer to bind dependencies with the application code. Which environment has the code been developed in?
A. bare metal server
B. virtual machine
C. container
D. Linux server
Which Cisco compute management platform enables the management of Cisco UCS, Cisco HyperFlex, Pure Storage, and Cisco Network Insights from a single platform?
A. Cisco UCS Manager
B. Cisco Intersight
C. Cisco HyperFlex
D. Cisco UCS Director
A business needs to create a simulated environment that mimics a production infrastructure to make changes to the OSPF process and analyze the impact. What should be used?
A. Cisco VIRL / Cisco CML
B. Cisco DevNet Sandbox labs
C. pyATS
D. Puppet
Which RFC 1918 address space includes a subnet of 172.16.0.0 that uses a mask of 255.255.0.0?
A. class A
B. class B
C. class C
D. class D
Refer to the exhibit. A developer must use a token to collect data from Cisco DNA Center API and prepares a Python script to send requests. Which line of codefineeds to be placed on the snippet where the code is missing to obtain a token from the Cisco DNA Center API?
A. token=BasicAuth(`user’,`password’))
B. auth=BasicAuth(`user’,`password’))
C. auth=HTTPBasicAuth(user,password))
D. token=HTTPBasicAuth(user,password))
Where is an IP packet routed if the packet does not match any routes in the routing table?
A. firewall
B. load balancer
C. central switch
D. default gateway
Which Python function is used to parse a string that contains JSON data into a Python dictionary?
A. json.dumps()
B. json.to_json()
C. json.parse()
D. json.loads()
Which automation tool uses NEDs to abstract southbound interfaces?
A. Chef
B. Puppet
C. Ansible
D. Cisco NSO
Refer to the exhibit. What is the result of the API sequence diagram?
A. export of the authenticated user on the device
B. text file that contains the authentication token
C. export of the Cisco IOS XE configuration file
D. text file that contains the string IOS-XE 16.6.3
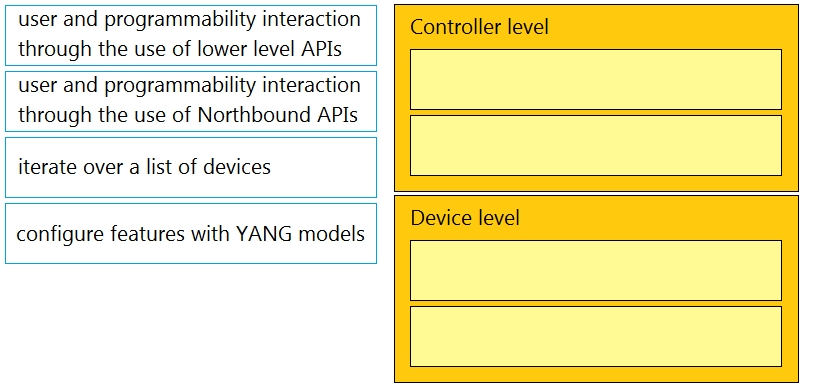
Drag and drop the types of management from the left onto the levels at which they are performed on the right.
Select and Place:
Which description of a default gateway is true?
A. It is a security feature that denies certain traffic.
B. It is a device that receives IP packets that have no explicit next-hop in the routing table.
C. It is a feature that translates between public and private addresses.
D. It is a device that receives Layer 2 frames with an unknown destination address.
Which advantage does the agile process offer compared to waterfall software development?
A. to add or update features with incremental delivery
B. to view the full scope of end-to-end work
C. to have each phase end before the next begins
D. to fix any issues at the end of the development cycle
Which two items are Cisco DevNet resources? (Choose two.)
A. TAC Support
B. Software Research
C. API Documentation
D. Bitbucket
E. Sandbox
Free Access Full 200-901 Practice Exam Free
Looking for additional practice? Click here to access a full set of 200-901 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your 200-901 certification journey!