200-901 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 200-901 certification exam? Start your preparation the smart way with our 200-901 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 200-901 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 200-901 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
Which Cisco compute management platform enables the management of Cisco UCS, Cisco HyperFlex, Pure Storage, and Cisco Network Insights from a single platform?
A. Cisco UCS Manager
B. Cisco Intersight
C. Cisco HyperFlex
D. Cisco UCS Director
Refer to the exhibit. An engineer must add new users and set privileges for executing a few Python scripts. The engineer prepares a Bash script to automate this task. The script adds a user and a group from the command-line arguments, creates a directory, and copies the Python scripts to it. The script then changes to the directory and lists the scripts. Based on the script work flow, which process is being automated within the loop by using the list of Python scripts?
A. assigning execution privileges to the owner, setting the user and group owner to the scripts that were initially created, and storing the script names in a file.
B. creating a file with the content of all the files, assigning execution permissions to each script, and then changing ownership to the initially created user and group.
C. removing the files that are not Python, listing the Python files, and assigning execution privileges to the initially created user and group.
D. assigning execution privileges to everyone and changing the ownership to the initially created user and group.
Refer to the exhibit. A network engineer works on a Cisco DevNet application that is available for download on the Cisco DevNet website. The engineer prepares a bash script to automate operations that relate to the application. Which work flow is being automated in the bash script?
A. compilation and configuration of the Cisco DevNet application so that it must be started manually
B. compilation, installation, and configuration of the Cisco DevNet application so that it starts automatically
C. compilation and installation of the Cisco DevNet application for an autonomous deployment model
D. installation and configuration of the Cisco DevNet application so that it starts manually
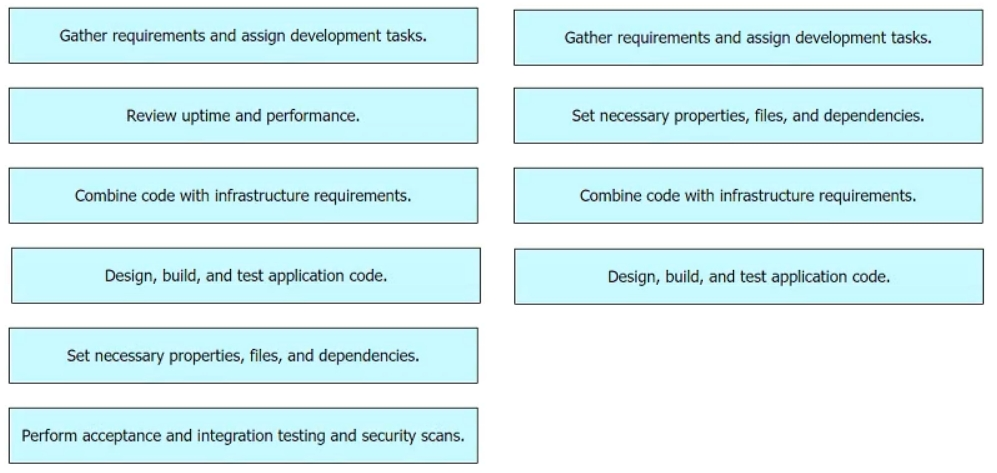
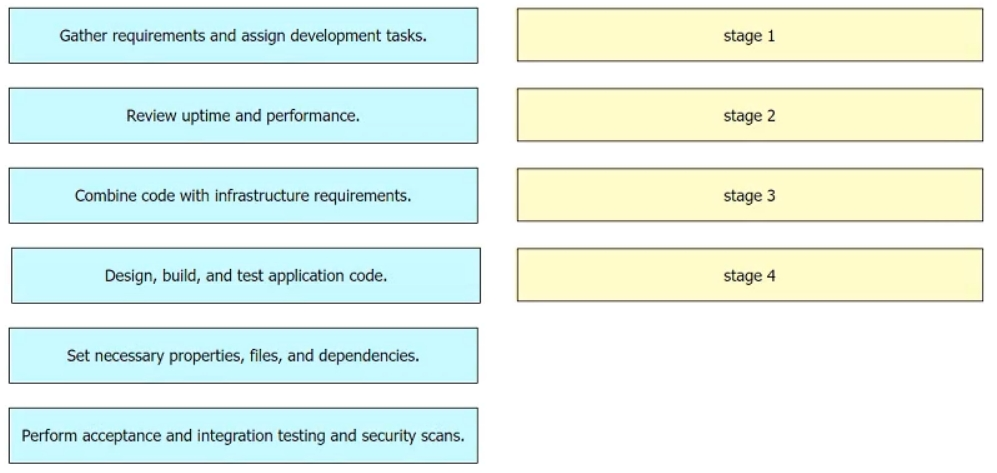
Drag and drop the first four stages of a DevOps toolchain from the left into the order on the right to create a new complex product. Not all options are used.
Select and Place:
Refer to the exhibit.A REST API returns this JSON output for a GET HTTP request, which has been assigned to a variable called `vegetables`. Using Python, which output is the result of this command? print( filter(lambda 1: 1['type'] == 'fruit', vegetables) [0]['items'][0]['items'][0])
A. {‘color’: ‘green’, ‘items’: [‘kiwi’, ‘grape’]}
B. [‘kiwi’, ‘grape’]
C. lettuce
D. kiwi
Which unique identifier allows network traffic to be routed to a host?
A. hostname
B. network prefix
C. IP address
D. subnet mask
Which two statements about JSON and XML are true? (Choose two.)
A. The syntax of JSON contains tags, elements, and attributes.
B. XML objects are collections of key-value pairs.
C. JSON objects are collections of key-value pairs.
D. JSON arrays are an unordered set of key-value pairs.
E. The syntax of XML contains tags, elements, and attributes.
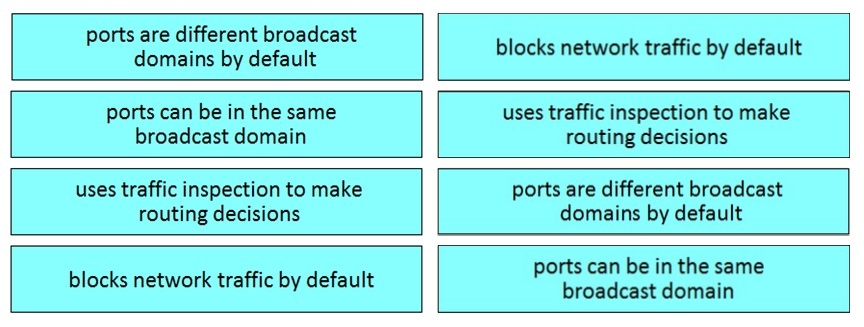
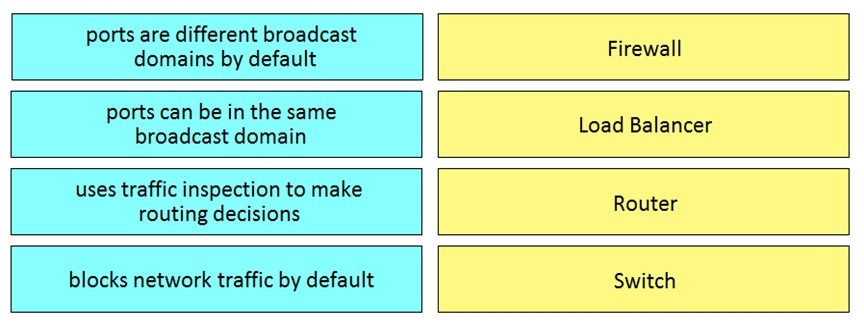
Drag and drop the functionalities from the left onto the correct networking devices on the right.
Select and Place:
An engineer must configure Cisco Nexus devices and wants to automate this work flow. The engineer will use an Ansible playbook to configure devices through Cisco NX REST API. Before the code is run, which resource must be used to verify that the REST API requests work as expected?
A. Cisco Open NX-OS
B. Cisco NX-OS SDK
C. Cisco Learning Labs
D. Cisco Code Exchange for Nexus
Refer to the exhibit. A network engineer wants to automate the port enable/disable process on specific Cisco switches. The engineer creates a script to send a request through RESTCONF and uses ietf as the YANG model and JSON as payload. Which command enables an interface named Loopback1?
A. enable_function(Loopback1, true, ‘iana-if-type:softwareLoopback’)
B. enable_function(‘iana-if-type:softwareLoopback’, Loopback1, true,)
C. def enable_function(‘iana-if-type:softwareLoopback’, Loopback1, false,)
D. def enable_function(Loopback1, true, ‘iana-if-type:softwareLoopback’)
Which Cisco platform provides organization-wide automation, security, policy enforcement, and agility across wired and wireless networks?
A. Cisco SD-WAN
B. Cisco DNA Center
C. Cisco ACI
D. Cisco Umbrella
What are two advantages of version control software? (Choose two.)
A. It supports tracking and comparison of changes in binary format files.
B. It allows new team members to access the current code and history.
C. It supports comparisons between revisions of source code files.
D. It provides wiki collaboration software for documentation.
E. It allows old versions of packaged applications to be hosted on the Internet.
Drag and drop the Git commands from the left onto the right that add modified local files to a remote repository. Not all options are used.
Select and Place:

What are the two benefits of edge computing architecture? (Choose two.)
A. run applications
B. centralized implementation
C. event logging
D. node distribution
E. complex event processing
Refer to the exhibit. An engineer must create a local user on Cisco ASA and prepares a script to send the request through ASA REST API. The engineer gets a response of 400 Bad Request. Which HTTP request produces a response code of 201?
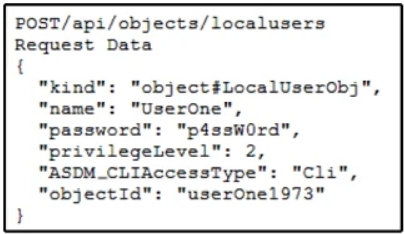

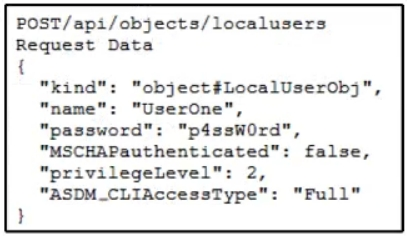
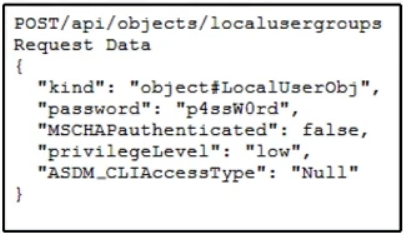
A developer checks the performance of a web application. The application is in the local data center and used a REST-based API. Based on the API logs, it is discovered that many users abandon API requests. Also, the response is taking too long to get back. What is the reason for this issue?
A. Token-based authentication is disabled.
B. Pagination is not implemented.
C. Rate limiting is not implemented.
D. Token-based authentication is enabled.
Which status code is used by a REST API to indicate that the submitted payload is incorrect?
A. 400
B. 403
C. 405
D. 429
Which advantage does the agile process offer compared to waterfall software development?
A. to add or update features with incremental delivery
B. to view the full scope of end-to-end work
C. to have each phase end before the next begins
D. to fix any issues at the end of the development cycle
A company wants to optimize the use of its existing compute resources by running multiple operating systems on a single Cisco UCS server. The company also wants to minimize new purchases for physical resources such as hard drives. The network connectivity between virtual hosts and the physical host needs to be bridged. Which deployment model type must be used?
A. bare metal
B. Docker
C. container
D. virtual machine
Which two NETCONF operations cover the RESTCONF GET operation? (Choose two.)
A. <get>
B. <get-config>
C. <get-update>
D. <modify-config>
E. <edit>
What are two benefits of model-driven programmability? (Choose two.)
A. easier to design, deploy, and manage APIs
B. single choice of transport, protocol, and encoding
C. models decoupled from transport, protocol, and encoding
D. model-based, structured, and human friendly
E. model-driven APIs for abstraction and simpli cation
A resource named /item is protected by oAuth2 authentication. An endpoint named /login must request authentication. Which method must be used to access the resource by using the REST API?
A. Make a GET call to /login that includes the username and password, and retrieve a token to insert into the /item call.
B. Make a POST call to /login including the user credentials in the message, and retrieve a token to insert into the authorization header of the /item call.
C. Make a GET call to /item, then make a call to /login that includes the username and password in the body of the message, and wait for the authorization code.
D. Make a POST call to /item that includes the username and password in the body of the request message, and submit it to request access.
A company wants to automate the orders processed on its website using API. The network device that supports the solution must: · support XML encoding · support distributed transactions · support YANG data models · be support software redundancy Which requirement prevents the use of RESTCONF for the solution?
A. software redundancy
B. YANG data models
C. distributed transactions
D. XML encoding
What is a requirement when authenticating a RESTCONF API session with a router that runs Cisco IOS XE Software?
A. No authentication is required.
B. OAuth must be used.
C. A token must be retrieved and the associated string must be embedded in the X-Auth-Token header.
D. Basic authentication must be used.
What is a feature of a MAC address?
A. It consists of 38 bits.
B. It consists of 12 hexadecimal numbers.
C. It consists of 6 hexadecimal numbers.
D. It consists of 24 bits.
Access to the management interface of devices must be restricted by using SSH and HTTPS. Which two ports must be included in the ACLs for the protocols to work? (Choose two.)
A. 22
B. 23
C. 80
D. 443
E. 880
What is a benefit of a distributed version control system?
A. encourages users to commit small places of work to the system more frequently
B. ensures that all code meets minimum standards before being committed to the system
C. allows users to work on the codebase even when not connected to the Internet
D. ensures that all code is tested before being committed to the system
Refer to the exhibit. A developer is creating a Python script to obtain a list of HTTP servers on a network named office_east by using the Cisco Meraki API. The request has these requirements: * Must time out if the response is not received within 2 seconds. * Must utilize client certificates and SSL certificate verification. * Must utilize basic authentication that uses a username of admin and a password of cisco. * Must save the response to an object named response. Drag and drop the code snippets from the bottom onto the blanks in the code to meet the requirements. Not all options are used.
Select and Place:
Which tool simulates a network that runs Cisco equipment?
A. Cisco Prime Infrastructure
B. VMware
C. Docker
D. CML
A developer improves the code repository to clean a bug on the custom network monitoring application. The developer adds the changes to the staging area and then commits on the local branch. Which command pushes commits that are made on a local branch to the remote repository?
A. push origin master
B. git push all
C. push all
D. git push origin master
Refer to the exhibit. Which RESTCONF request results in this response?
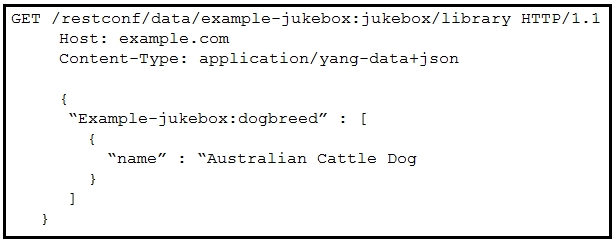
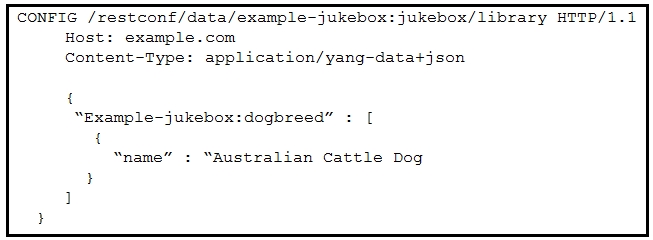

A. D
Calling a REST API returns a 404 error. What does this code represent?
A. A query parameter is missing.
B. The URI being requested is incorrect.
C. A header is missing.
D. The payload is formatted incorrectly.
Refer to the exhibit. The Cisco Meraki API manages two organizations. In each organization, two independent networks are defined. How many calls to the / organizations/{orgId}/networks endpoint will be run parallel by the GetAllNetworks function of the API client?
A. 0
B. 1
C. 2
D. 4
What are two benefits of organizing code into classes, methods, functions, and modules? (Choose two.)
A. improves readability
B. improves reusability
C. improves parallelism
D. improves performance
E. decreases complexity
Refer to the exhibit. The sequence diagram shows a RESTful API call. Which step and response will represent the behavior of the REST API call to be synchronous?
A. POST/discovery/ when there is a slot available and get the response from the POST call with the discovery details.
B. GET/discovery/ when the discovery is nished and get the response from the GET call with the discovery requirements.
C. POST/discovery?discoveryid= when the discovery is created and get the response from the POST call with the discovery details.
D. PUT/discovery/ when the discovery is created and get the response of the discovery when it is updated.
Which protocol runs over TCP port 23?
A. SSH
B. NETCONF
C. HTTP
D. Telnet
What are two benefits of managing network configuration via APIs? (Choose two.)
A. more security due to locking out manual device configuration
B. configuration on devices becomes less complex
C. eliminates the need of legacy management protocols like SNMP
D. reduction in network changes performed manually
E. increased scalability and consistency of network changes
Which benefit does CI/CD provide to the infrastructure?
A. supports connectivity between network resources and external platforms
B. supports the integration of network devices with external databases
C. provides version control during application development
D. enables frequent and reliable code deployments
Refer to the exhibit. A network engineer makes a RESTCONF API call to Cisco IOS XE to retrieve information. Which HTTP method and URL does the engineer use to make the API call?
A. GET https://devnetlab.local/restconf/api/running/native/GigabitEthernet
B. GET https://devnetlab.local/restconf/api/running/native/interface/GigabitEthernet
C. GET https://devnetlab.local/restconf/api/running/native/interface/GigabitEthernet/2/
D. GET https://devnetlab.local/restconf/api/running/ios/native/interface/GigabitEthernet/1/
What is a capability of the NETCONF protocol?
A. allows Python scripts to be executed externally from a network device
B. uses JSON to encode data in its content layer
C. allows XML messages to be exchanged via the SSH protocol
D. exposes a web-based interface
Refer to the exhibit. An engineer is managing the network of an enterprise. The network is using a distributed deployment model. The enterprise uses database to store logs. The current policy requires logs to be stored if changes are made to the infrastructure in any of the devices on the data centers. Which work flow is being automated by the Bash script?
A. returning backup files that are older than 30 days
B. deleting backup files that are older than 30 days
C. configuring the directory to delete files automatically
D. automating deletion of all backup files every 30 days
Refer to the exhibit. A developer must integrate a bot with an internal communication app. The developer wants to replace the webexbot package with the teamsbot package by using Ansible and prepares a playbook. In the first two tasks, the playbook stops the webexbot and verifies that the teamsbot is installed. What is accomplished in the last task of the work flow when the developer runs the Ansible playbook?
A. uninstalls the webexbot package and removes its configuration files
B. installs the webexbot and retains the configuration files
C. stops the webexbot service and uninstall it and retains its configuration files
D. searches whether the purge package is available in the repository and uninstalls the webexbot package
What is a principle of test-driven development?
A. write and run tests before writing new code
B. write tests after adding new blocks of code
C. run tests after writing new code
D. write documentation for tests
Refer to the exhibit. A developer wants to create a room named cisco through Webex API. The developer prepares the request by putting an API token inside the authorization header; however, the given HTTP call returns error code 400. How must the call parameters be changed to ensure a valid response?
A. Replace the team body parameter with the name body parameter.
B. Replace cisco with a valid name for a team.
C. Change the token in the header with the authorization token.
D. Change the HTTP method of the call to PUT.
A developer is developing a web application that uses username and password to authenticate to the next service. The user credentials must be available at any time in the application. The developer must choose and implement a secure method of storing the authentication credentials that are used in the automation code. Which password handling method must be used to minimize the security risk?
A. Store the username and password in a separate configuration file.
B. Store the username and password in a vault.
C. Store the passwords in a dictionary.
D. Store the username and password in code.
A developer prepares a Python application to monitor network performance on specific applications. The developer tests the code on a test environment but requires more use cases and wants the scripts to be improved for different networks. Which resource must be used to take advantage of open-source communities and contributors for the application?
A. code exchange
B. sandbox
C. packet tracer
D. learning labs
A new application is being developed with specific platform requirements. The platform and application deployment and the ongoing platform management must be fully automated. The application includes a large database component that has significant disk I/O requirements. Which application deployment type meets the requirements?
A. Python virtual environment
B. virtual machine
C. bare metal
D. container
What are two benefits of edge architecture? (Choose two.)
A. device authentication
B. secure access
C. service deployment
D. offline support
E. data management
Refer to the exhibit. An engineer wants to create a Bash script to automate a workflow that is related to a machine learning-based application. The engineer wants to use the application as a container and use an image from the open-source public repository. What is accomplished by the script?
A. Create a new software package
B. Install and remove files.
C. Update an existing software package.
D. Install a software package.
A retail store is launching an online presence through their new application. The amount of end-user traffic on the application is expected to fluctuate depending on whether there are sales on or not. The application developer has decided to adopt an application-deployment model that allows them to leverage cloud bursting. Which deployment approach would allow cloud bursting?
A. local infrastructure
B. edge computing
C. on-premises
D. hybrid
Access Full 200-901 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 200-901 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 200-901 mock test free today—and take a major step toward exam success!