200-901 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your 200-901 certification? Our 200-901 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an 200-901 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our 200-901 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
A company requires a new platform to store large volumes of log data that is generated in their assembly plant. The platform must be scalable, so the underlying technology must provide a path for fast deployment of new nodes for data and indexing? The data contains sensitive information, so specialist encryption tools must be used to secure the data. Which application deployment model meets the requirements?A. edge
B. private cloud
C. public cloud
D. hybrid cloud
Users cannot access a webserver and after the traffic is captured, the capture tool shows an ICMP packet that reports "time exceeded in-transit".
What is the cause of this webserver access issue?A. A router along the path has the wrong time.
B. A router along the path is misrouting the packets in a wrong direction.
C. The server is too loaded and the connection could not be handled in time.
D. The server is too far away and the packets require too much time to reach it.
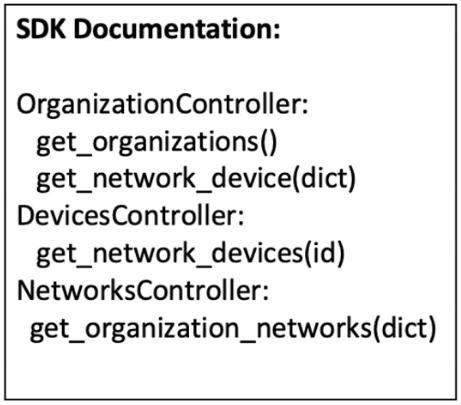
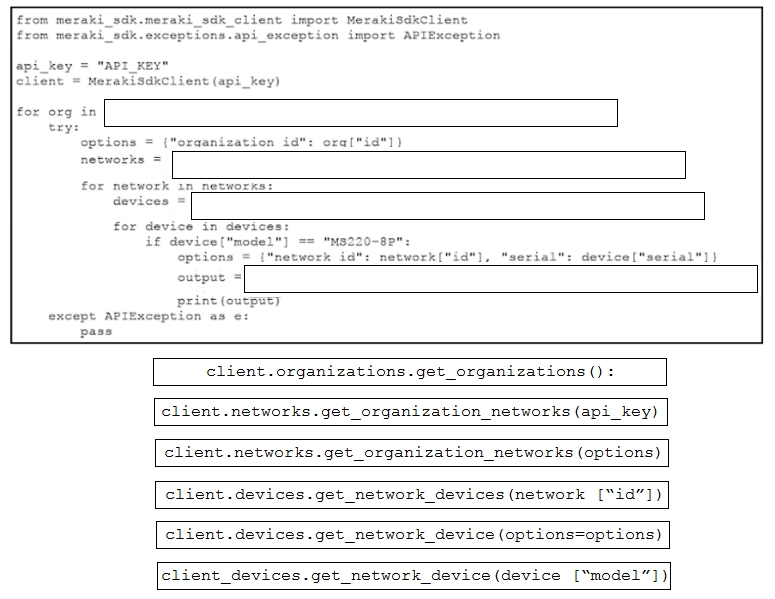
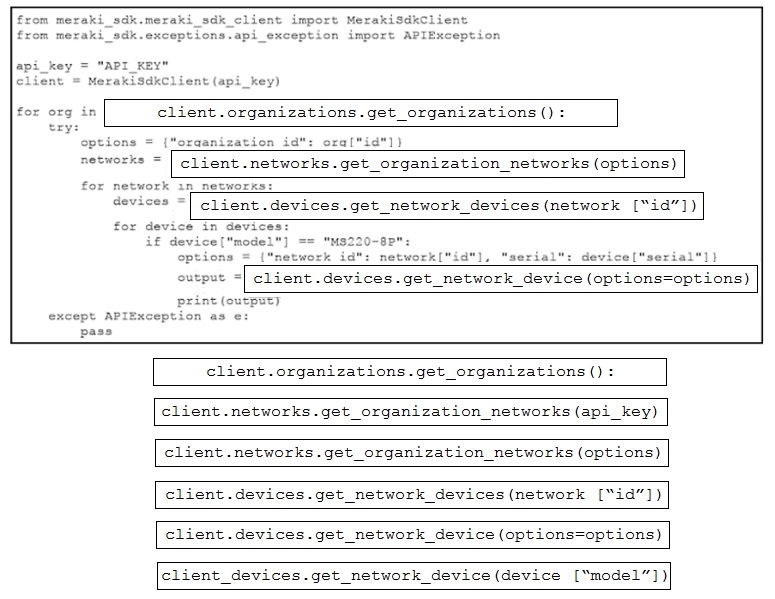
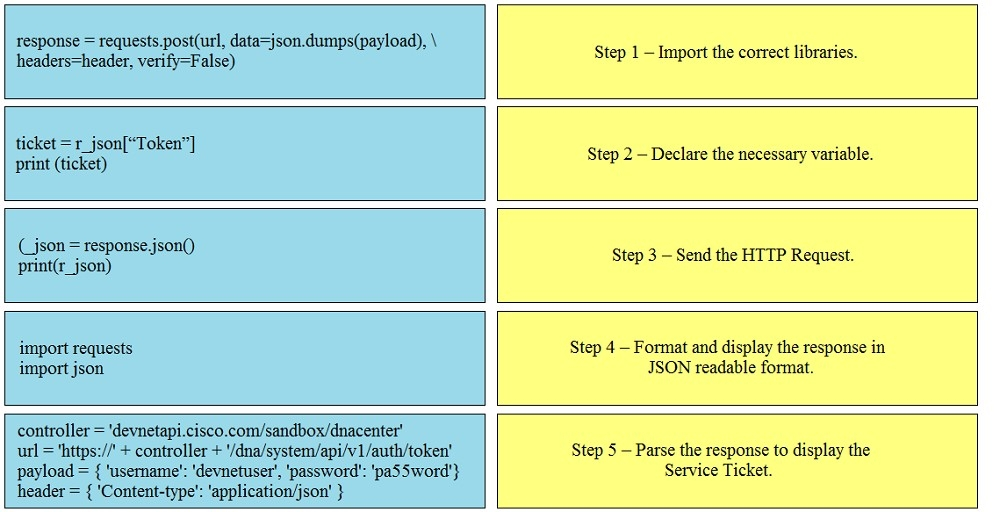
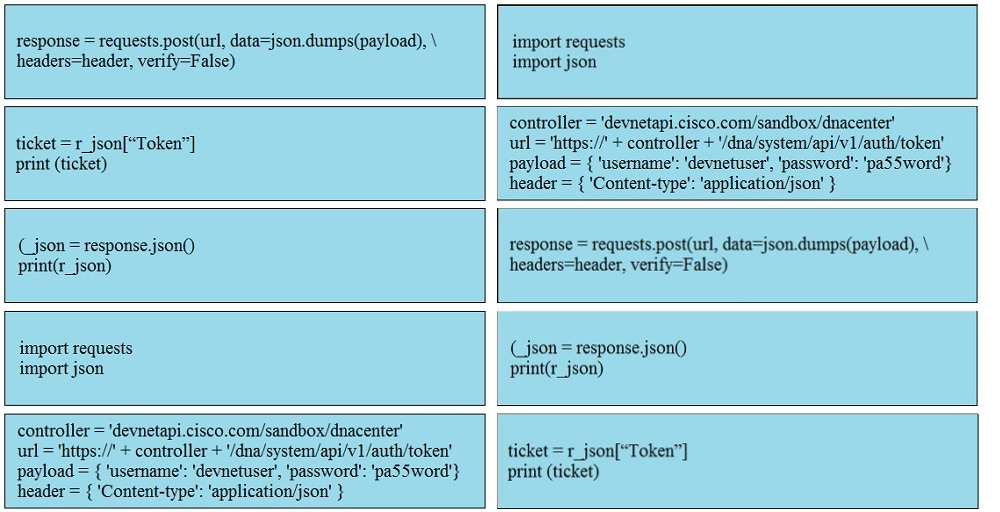
Refer to the exhibit. A script must output details of all the Cisco Meraki MS220-BP switches across all organizations and networks. Drag and drop the code snippets from the bottom onto the boxes in the code to complete the script. Not all options are used.Select and Place:
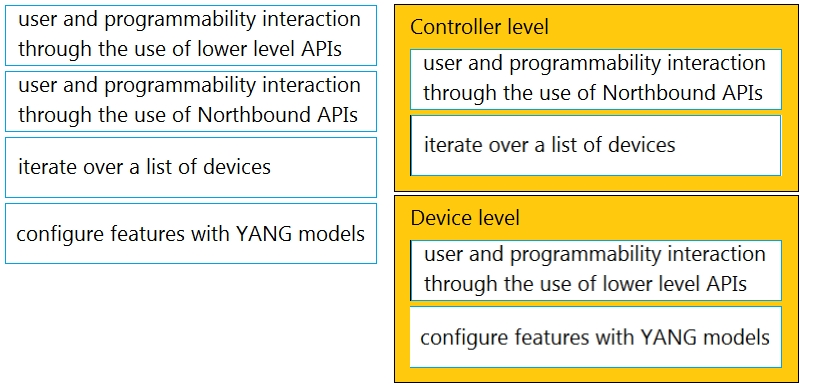
What is a difference between device-level and controller-level infrastructure management?A. Device-level management uses NETCONF, whereas controller-level management does not support NETCONF to automate the infrastructure.
B. Controller-level management uses APIs to simplify the developer experience, whereas device-level management uses traditional management protocols.
C. Controller-level management is more widely supported because it is standards-based, whereas device-level management is proprietary to each vendor.
D. Controller-level management exposes northbound, southbound, eastbound, and westbound APIs, easing integration with other technologies, whereas device-level management does not use a controller-based API.
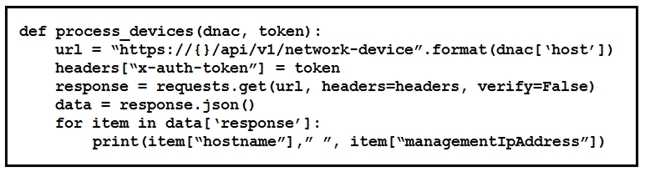
Refer to the exhibit.
What is the function of the Python script?A. Loop through the returned list of network devices and, for each device, print the device name and management IP address.
B. Count and print the total number of available devices.
C. For each device that is returned, display the device type and associated management IP address.
D. Iterate over a list of network devices and write all device names and management IP addresses to an output file.
A customer's cloud services must:
· Migrate services to another data center on demand.
· Save the operational state of the machine on demand.
· Support Windows and Linux GUIs.
· Maximize hardware utilization.
Which type of deployment meets these requirements?A. bare metal
B. container
C. virtual machine
D. Kubernetes
Refer to the exhibit.
A process running on the host wants to access the service running inside this Docker container. Which port or ports are used to make a connection?A. only outbound connections between 3000 and 5000 are possible
B. port 3000
C. any port between 3000 and 5000
D. port 5000
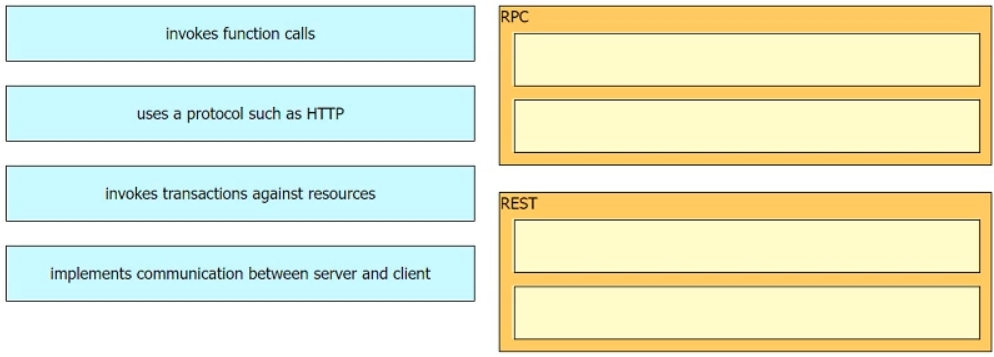
Drag and drop the API characteristics from the left onto the corresponding categories on the right.Select and Place:
Which type of threat occurs when an attacker can send hostile data to an interpreter within an application?A. sensitive data exposure
B. broken authentication
C. cross-site scripting
D. injection
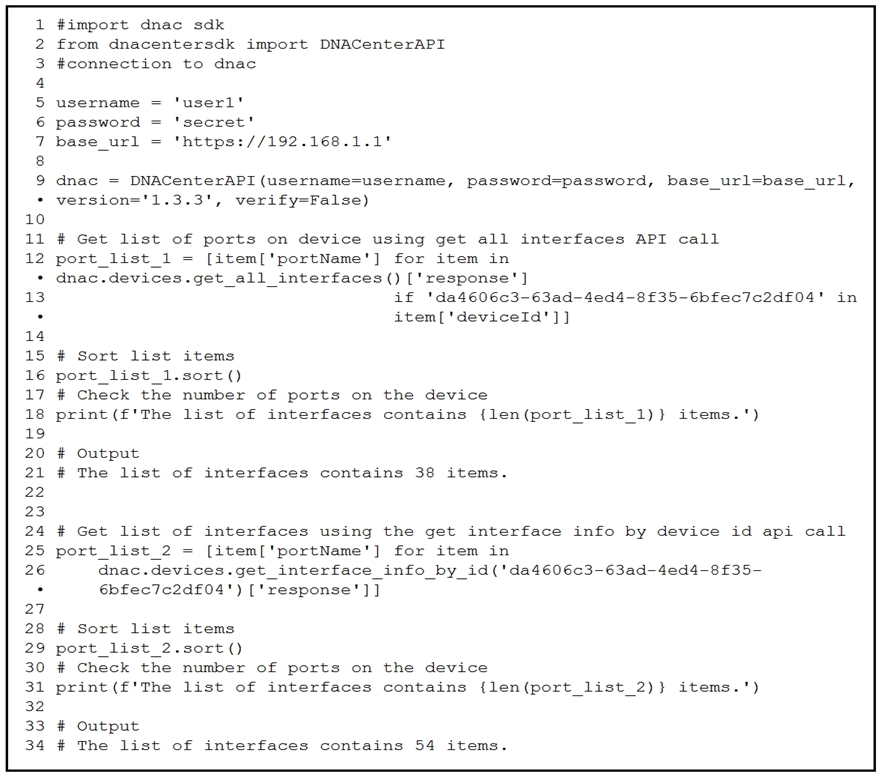
Refer to the exhibit. An engineer writes a Python script that uses two different API calls to query Cisco DNA Center for the number of interfaces on a device. The engineer notices that the two API calls produce different results. Why are fewer interfaces returned for the same device when the 'get_all_interfaces' API call is used?A. times out
B. rate limit
C. pagination
D. invalid password
Which protocol runs over TCP port 830?A. NETCONF
B. Telnet
C. RESTCONF
D. HTTP
What is an advantage of using network programmability?A. Manual configuration is faster.
B. No cloud abstraction occurs.
C. It removes CLI access for devices.
D. It provides for more scalable and replicable network provisioning.
Which tool simulates a network that runs Cisco equipment?A. Cisco Prime Infrastructure
B. VMware
C. Docker
D. CML
A new application is being developed with specific platform requirements. The platform and application deployment and the ongoing platform management must be fully automated. The application includes a large database component that has significant disk I/O requirements. Which application deployment type meets the requirements?A. Python virtual environment
B. virtual machine
C. bare metal
D. container
What is a benefit of using model-driven programmability on Cisco devices?A. deeper monitoring
B. better logging
C. automated configuration
D. increased security
Drag and drop the HTTP methods from the left onto their generally accepted corresponding create, read, update, and delete operations on the right.Select and Place:
What is a characteristic of Waterfall compared to Agile software development method?A. Waterfall focuses on continuous improvement, and Agile focuses on the design phase.
B. Waterfall separates the project development lifecycle into sprints, and Agile does not use cycles.
C. Waterfall speci es requirements before development begins, and Agile responds exibly to changes in requirements.
D. Waterfall uses reviews with step by step approach, and Agile uses a serially phased approach.
Refer to the exhibit. A developer needs to create a Docker image that listens on port 5000. Which code snippet must be placed onto the blank in the code?A. PORT 5000
B. LISTEN 5000
C. EXPOSE 5000
D. OPEN 5000
What is a difference between a synchronous API and an asynchronous API?A. Synchronous API calls require an authentication header to be sent while asynchronous calls do not require authentication.
B. Synchronous API calls are returned immediately while asynchronous calls do not guarantee an immediate response.
C. An asynchronous API can make offline calls while synchronous APIs do not have this capability.
D. An asynchronous API can make a larger number of calls in a speci ed time period than a synchronous API.
What is a rehose webhook?A. It collects data from third-party cloud APIs for custom applications.
B. It enables an application to receive real-time data from Cisco Webex.
C. It enables data to flow from the Cisco Webex API to a user's application.
D. It sends a notification of any event for commonly used resources.
What is the purpose of a firewall in application deployment?A. adds TLS support to an application that does not support it natively
B. limits traffic to only ports required by the application
C. provides translation for an application's hostname to its IP address
D. forwards traffic to a pool of instances of the application
Drag and drop the code snippets from the bottom into the Python script to write API output to a csv file. Not all options are used.Select and Place:
What is the impact on an application from having a large distance between a client device and a host server?A. latency
B. increased bandwidth
C. loss of connectivity
D. jitter
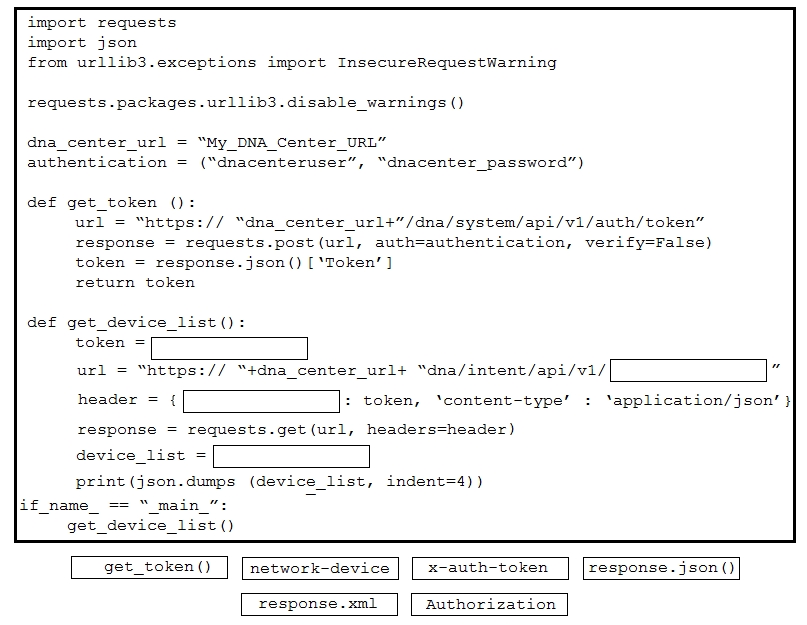
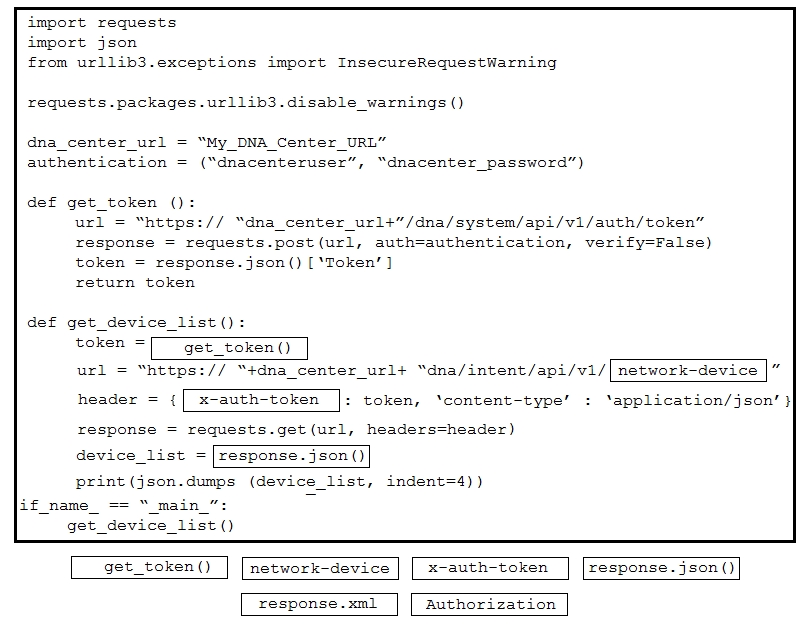
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the Python script to retrieve a list of network devices from Cisco DNA Center. Not all options are used.Select and Place:
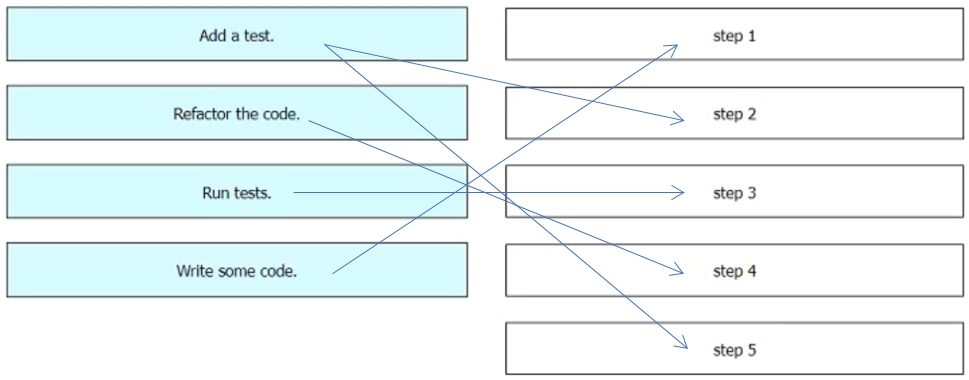
What is the purpose of running tests before writing code in test-driven development?A. to find unexpected failures in the tests
B. to demonstrate that the tests fail for expected reasons
C. to ensure that the tests pass
D. to provide proof of the work carried out
Which Python data type resembles JSON data structures?A. list
B. dictionary
C. string
D. tuple
What is a characteristic of Agile software development compared to the Waterfall method?A. Agile method values comprehensive documentation whereas Waterfall focuses on working software.
B. Agile delivers at the end of a linear process whereas in Waterfall each phase depends on the deliverables of the previous phase.
C. In Agile, development iterations last from one to four weeks whereas the Waterfall method does not utilize iterations.
D. In Agile, code is deployed to production immediately whereas in Waterfall deployment is processed gradually on each cycle.
A developer creates an application that must provide an encrypted connection or API keys. The keys will be used to communicate with a REST API. Which command must be used for the secure connection?A. curl X PUSH `http://username.app.com/endpoint/?api_key=12345abcdef'
B. curl v `ftp://username.app.com/endpoint/?api_key=12345abcdef'
C. curl X GET `https://username.app.com/endpoint/?api_key=12345abcdef'
D. curl X GET `http://username.app.com/endpoint/?api_key=12345abcdef'
Which two elements are foundational principles of DevOps? (Choose two.)A. organizing cross-functional teams over organizational silos
B. designing applications as microservices
C. encouraging containers for the deployment of applications
D. automating over documenting
E. optimizing the cost of infrastructures
Which status code is used by a REST API to indicate that the submitted payload is incorrect?A. 400
B. 403
C. 405
D. 429
What is a benefit of using Python classes?A. They improve code organization by keeping data members and methods together.
B. They remove the concept of inheritance to improve code readability and maintainability.
C. They allow a Python script to import code from various independent modules.
D. They simplify integration by testing the classes independently from other components.
What are two advantages of version control software? (Choose two.)A. It supports tracking and comparison of changes in binary format files.
B. It allows new team members to access the current code and history.
C. It supports comparisons between revisions of source code files.
D. It provides wiki collaboration software for documentation.
E. It allows old versions of packaged applications to be hosted on the Internet.
What is the purpose of a MAC address on a network device?A. unique network address that identifies the network interface of a device
B. unique network interlace address that is provided by the DHCP server
C. unique hardware address that identifies the network interface of a device
D. unique hardware interface address that is provided by the central switch
Refer to the exhibit. A developer is using cURL to test connectivity to a webpage. The request times out after 10 seconds. The developer tested connectivity by using Ping and can open a TCP socket to the remote server by using Telnet. Other users confirm that they can access the webpage from their device. The developer has SSH access to the remote server and runs commands to troubleshoot. What causes the issue?A. Connectivity from the remote server back to the client is down.
B. Firewall rules on the remote server block the client on port 443.
C. Application-layer security features on the remote server block the connection.
D. HTTPS proxy configured on the remote server blocks the connection.
Refer to the exhibit. An engineer is comparing two files by using the unified diff format. What is determined by the content in the le2.py file?A. Line 93 of file.py is `DEVICE-STATS'.
B. Line 92 of le2.py is `DEVICE-STATS'.
C. Line 16 of le2.py is auth=HTTPBasicAuth(USERNAME, PASSWORD).
D. Line 17 of le2.py is auth = HTTPBasicAuth(USERNAME, PASSWORD).
Drag and drop the Python code from the left onto the correct step on the right to call a REST API.Select and Place:
What is a principle of Infrastructure as Code?A. It requires manual resource provisioning.
B. It encourages overlaps in services.
C. It encourages repeatable processes.
D. It requires the use of large components.
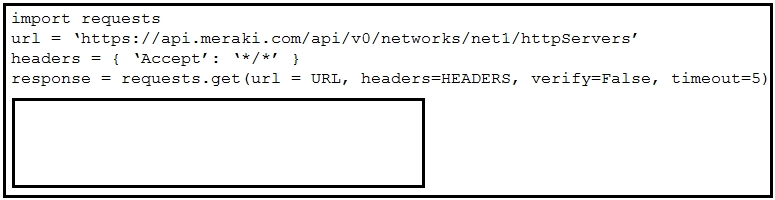
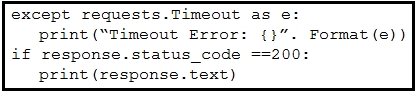
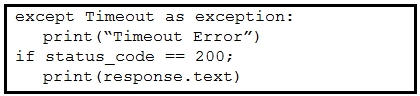
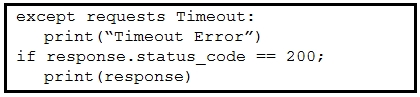
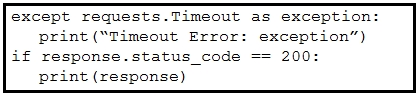
Refer to the exhibit. A developer created a Python script by using the Cisco Meraki API. The solution must:
· Obtain a list of HTTP servers for a network named "net1".
· Print the response body if the HTTP status code is 200.
· Handle the timeout requests as exceptions, and print Timeout Error next to the exception to stdout.
Which block of code completes the script?
A network engineer makes several API calls to Cisco Prime to retrieve a list of all devices. Each time a response is received, only a subset of the devices is returned. The engineer notices that HTTP code 429 is returned instead of 200 for some API calls. Why did the response exclude some of the devices?A. The API applied an offset that was indicated in the request.
B. The API failed to identify how many items to retrieve.
C. The API timed out the request.
D. The API rate limited the request.
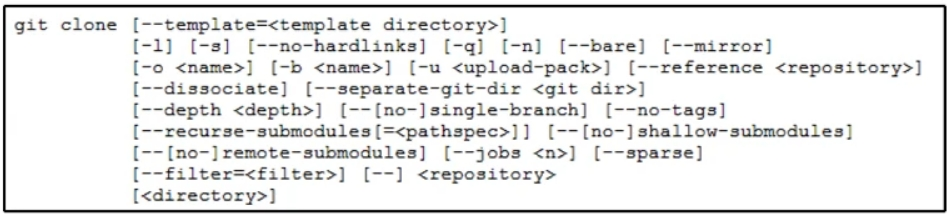
Refer to the exhibit. A network engineer must improve the fabric discovery process in a data center. The engineer wants to check current ACI scripts in the myproject repository and clone them to a folder named aci. The engineer will optimize the scripts from the new folder. Which command performs this task on the Git repository?

Which network device plane is responsible for handling QoS?A. management plane
B. data plane
C. configuration plane
D. control plane
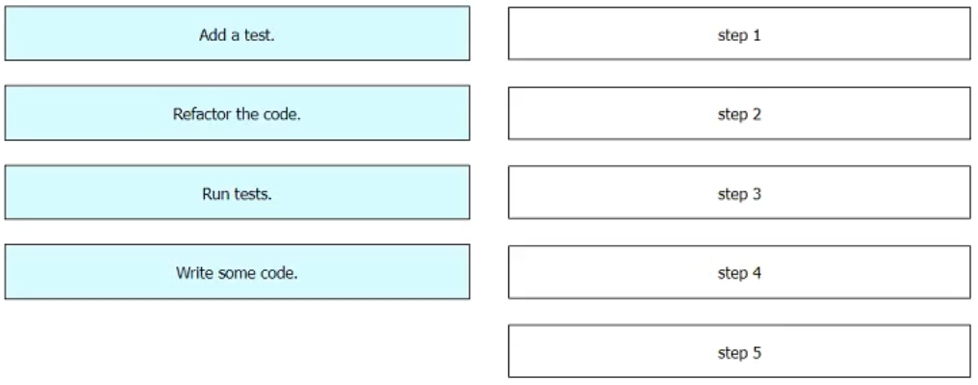
Drag and drop the steps from the left into the order on the right to create a testdriven development cycle. Some options are used more than once.Select and Place:
What are two functions of a routing table on a network device? (Choose two.)A. It lists the routes to drop traffic.
B. It lists the routes to a particular destination.
C. It lists the static and dynamic entries.
D. It lists hosts that are one hop away.
E. It lists entries more than two hops away.
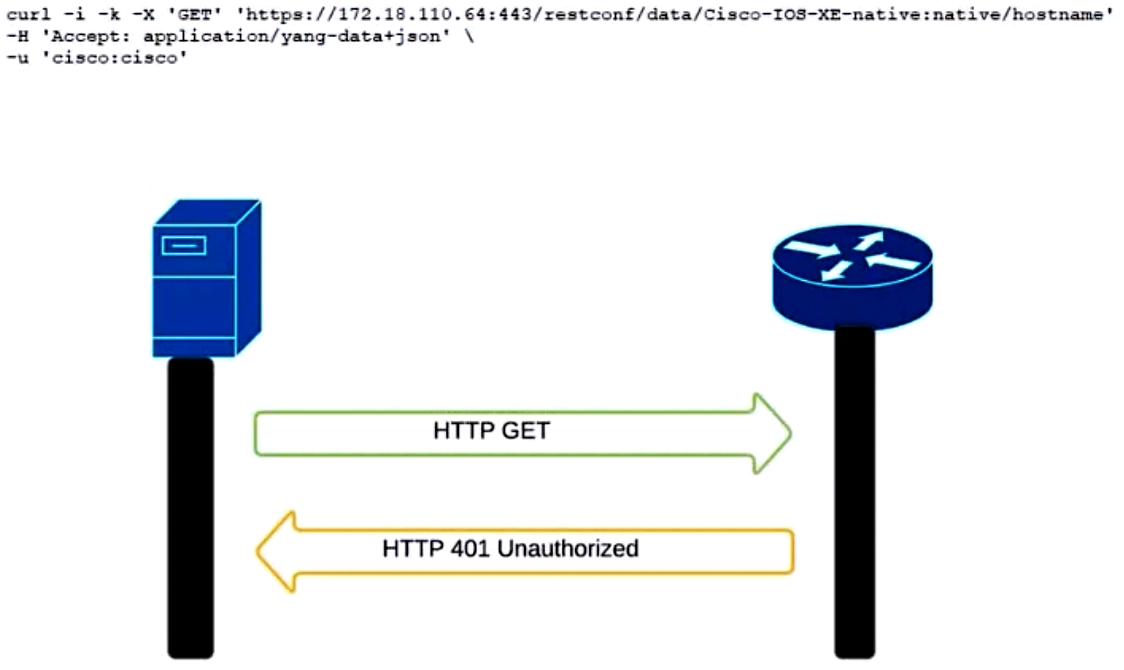
Refer to the exhibit. An administrator attempts to perform a GET operation by using the Cisco IOS XE RESTCONF API to return the hostname of a device. The sequence diagram in the exhibit illustrates the HTTP messages observed. Which change to the API request resolves the issue?A. Remove the -H 'Accept: application/yang-data+json' header.
B. Replace -u cisco:cisco parameter with -u `cisco:cisco'.
C. Change the request method from -X `GET' to -X `POST'.
D. Add the -H `Content-Type: application/yang-data+json' header.
Drag and drop the types of management from the left onto the levels at which they are performed on the right.Select and Place:
What is a benefit of using functions in the code for the development process?A. better user experience in the end product
B. improves code performance
C. easier to compile the code
D. faster code development
Which HTTP response code is returned from a successful REST API call to create a new resource?A. 201
B. 204
C. 302
D. 429
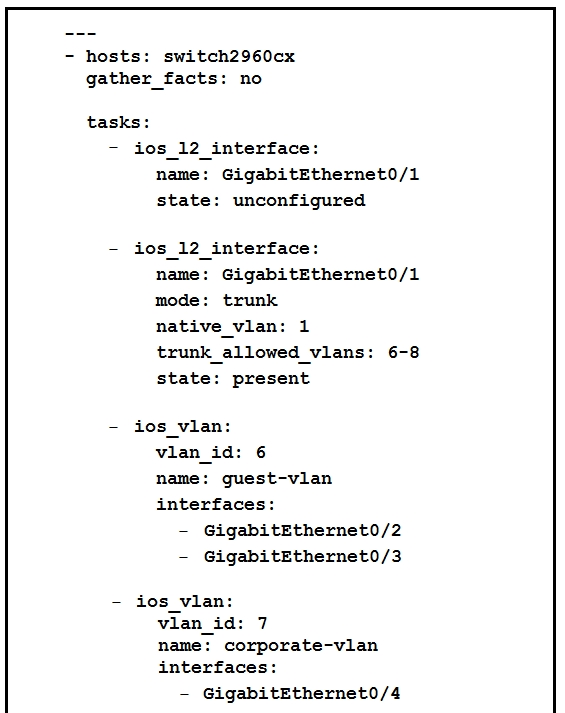
Refer to the exhibit.
Which two statements describe the configuration of the switch after the Ansible script is run? (Choose two.)A. traffic from ports 0/2 to 0/5 is able to flow on port 0/1 due to the trunk.
B. GigabitEthernet0/1 is left unconfigured.
C. GigabitEthernet0/2 and GigabitEthernet0/3 are access ports for VLAN 6.
D. traffic is able to flow between ports 0/2 to 0/5 due to the trunk on port 0/1.
E. traffic on ports 0/2 and 0/3 is connected to port 0/6.
Refer to the exhibit. An engineer must configure a load balancer server. The engineer prepares a script to automate work flow by using Bash. The script installs the nginx package, moves to the /opt/nginx directory, and reads the sites.txt file for further processing. Based on the script work flow, which process is being automated within the loop by using the information in sites.txt?A. creating a file per each line in sites.txt with the information in template.conf, creating a link for the previously created file, and then changing the ownership of the created files
B. using the content of the file to create the template.conf file, creating a link from the created file to the /etc/nginx/sites_enabled, and then changing the file execution permissions
C. creating a new file based on template.conf in the /etc/nginx/sites_enabled directory for each line in the sites.txt file, and then changing the file execution permissions
D. using the information in the file to create a set of empty files in the /etc/nginx/sites_enabled directory, and then assigning the owner of the file
An engineer must configure Cisco Nexus devices and wants to automate this work flow. The engineer will use an Ansible playbook to configure devices through Cisco NX REST API. Before the code is run, which resource must be used to verify that the REST API requests work as expected?A. Cisco Open NX-OS
B. Cisco NX-OS SDK
C. Cisco Learning Labs
D. Cisco Code Exchange for Nexus
Access Full 200-901 Dump Free
Looking for even more practice questions? Click here to access the complete 200-901 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our 200-901 dump free questions — and get one step closer to exam success!