200-301 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 200-301 certification exam? Kickstart your success with our 200-301 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 200-301 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 200-301 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
Refer to the exhibit. What is missing from this output for it to be executed?
A. double quotes (” “) around the “Cisco Devices” string
B. exclamation point (!) at the beginning of each line
C. square bracket ( [ ) at the beginning
D. curly braket ( } ) at the end
Refer to the exhibit. An engineer is asked to configure router R1 so that it forms an OSPF single-area neighbor relationship with R2. Which command sequence must be implemented to configure the router?
A. router ospf 100 network 10.0.0.0 0.0.0.252 area0 network 10.0.1.0 0.0.0.255 area0
B. router ospf 100 network 10.0.0.0 0.0.0.3 area0 network 10.0.2.0 255.255.255.0 area0
C. router ospf 10 network 10.0.0.0 0.0.0.3 area0 network 10.0.1.0 0.0.0.255 area0
D. router ospf 10 network 10.0.0.0 0.0.0.3 area0 network 10.0.2.0 0.0.0.255 area0
Refer to the exhibit. What are the two steps an engineer must take to provide the highest encryption and authentication using domain credentials from LDAP? (Choose two.)
A. Select PSK under Authentication Key Management.
B. Select Static-WEP + 802.1X on Layer 2 Security.
C. Select WPA+WPA2 on Layer 2 Security.
D. Select 802.1X from under Authentication Key Management.
E. Select WPA Policy with TKIP Encryption.
Which cipher is supported for wireless encryption only with the WPA2 standard?
A. RC4
B. AES
C. SHA
D. AES256
What benefit does controller-based networking provide versus traditional networking?
A. allows configuration and monitoring of the network from one centralized point
B. provides an added layer of security to protect from DDoS attacks
C. combines control and data plane functionality on a single device to minimize latency
D. moves from a two-tier to a three-tier network architecture to provide maximum redundancy
Refer to the exhibit. Which next-hop IP address has the least desirable metric when sourced from R1?
A. 10.10.10.4
B. 10.10.10.5
C. 10.10.10.3
D. 10.10.10.2
DRAG DROP - Drag and drop the characteristic from the left onto the cable type on the right.
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology tab to access the device console(s) and perform the tasks. • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window. • All necessary preconfigurations have been applied. • Do not change the enable password or hostname for any device. • Save your configurations to NVRAM before moving to the next item. • Click Next at the bottom of the screen to submit this lab and move to the next question. • When Next is clicked the lab closes and cannot be reopened. Topology -Tasks - All physical cabling is in place and verified. Connectivity between all four switches must be established and operational. All ports are pre-configured as 802.1q trunks. 1. Configure both SW-1 and SW-2 ports e0/1 and e0/2 to permit only the allowed VLANs 2. Configure both SW-3 and SW-4 ports e0/2 to permit only the allowed VLANs 3. Configure both SW-1 and SW-2 e0/1 ports to send and receive untagged traffic over VLAN 99 4. Configure both SW-3 and SW-4 ports e0/0 and e0/1 for link aggregation using the industry standard protocol. All ports must immediately negotiate the link aggregation 5. Permit only the allowed VLANs on the new link
After you deploy a new WLAN controller on your network, which two additional tasks should you consider? (Choose two.)
A. deploy load balancers
B. configure additional vlans
C. configure multiple VRRP groups
D. deploy POE switches
E. configure additional security policies
How does a hub handle a frame traveling to a known destination MAC address differently than a switch?
A. The hub forwards the frame to all ports, and a switch forwards the frame to the known destination.
B. The hub forwards the frame to all ports in the FIB table, and a switch forwards the frame the destination MAC is known.
C. The hub forwards the frame using the information in the MAC table, and a switch uses data in its routing table.
D. The hub forwards the frame only to the port connected to the known MAC address, and a switch forwards the frame to all ports.
What is a characteristic of encryption in wireless networks?
A. provides increased protection against spyware
B. prompts a user for a login ID
C. uses ciphers to detect and prevent zero-day network attacks
D. prevents the interception of data as it transits a network
What are two features of PortFast? (Choose two.)
A. Convergence is fast after a link failure.
B. STP loops are mitigated for uplinks to other switches.
C. Ports transition directly from the blocking state to the forwarding state.
D. Ports operate normally without receiving BPDUs.
E. Ports that connect to the backbone automatically detect indirect link failures.
Which interface is used to send traffic to the destination network?
A. G0/9
B. G0/20
C. G0/16
D. G0/11
What is represented by the word "switch" within this JSON schema?
A. key
B. object
C. array
D. value
Refer to the exhibit A new VLAN and switch are added to the network. A remote engineer configures OldSwitch and must ensure that the configuration meets these requirements: • accommodates current configured VLANs • expands the range to include VLAN 20 • allows for IEEE standard support for virtual LANs Which configuration on the NewSwitch side of the link meets these requirements?
A. switch port mode dynamicchannel group 1 mode activeswitchport trunk allowed vlan 5,10,15, 20
B. no switchport mode trunkswitchport trunk encapsulation islswitchport mode access vlan 20
C. switchport nonegotiateno switchport trunk allowed vlan 5,10switchport trunk allowed vlan 5,10,15,20
D. no switchport trunk encapsulation islswitchport trunk encapsulation dot1qswitchport trunk allowed vlan add 20
What is an expected outcome when network management automation is deployed?
A. A distributed management plane must be used.
B. Complexity increases when new device configurations are added.
C. Custom applications are needed to configure network devices.
D. Software upgrades are performed from a central controller.
DRAG DROP - Drag and drop the statements about device management from the left onto the corresponding device-management types on the right.
With REST API, which standard HTTP header tells a server which media type is expected by the client?
A. Accept-Encoding: gzip. deflate
B. Accept-Patch: text/example; charset=utf-8
C. Content-Type: application/json; charset=utf-8
D. Accept: application/json
What is the difference between an IPv6 link-local address and a unique local address?
A. The scope of an IPv6 link-local address is limited to a directly attached interface, but an IPv6 unique local address is used throughout a company site or network.
B. The scope of an IPv6 link-local address is global, but the scope of an IPv6 unique local address is limited to a loopback address.
C. The scope of an IPv6 link-local address can be used throughout a company site or network, but an IPv6 unique local address is limited to a loopback address.
D. The scope of an IPv6 link-local address is limited to a loopback address, and an IPv6 unique local address is limited to a directly attached interface.
What does a switch do when it receives a frame whose destination MAC address is missing from the MAC address table?
A. It changes the checksum of the frame to a value that indicates an invalid frame.
B. It updates the CAM table with the destination MAC address of the frame.
C. It appends the table with a static entry for the MAC and shuts down the port.
D. It floods the frame unchanged across all remaining ports in the incoming VLAN.
Which interface on the WLC is limited to one when LAG is in use?
A. service
B. virtual
C. trunk
D. AP-manager
Refer to the exhibit. If OSPF is running on this network, how does Router2 handle traffic from Site B to 10.10.13.128/25 at Site A?
A. It sends packets out of interface Fa0/1 only.
B. It sends packets out of interface Fa0/2 only.
C. It load-balances traffic out of Fa0/1 and Fa0/2.
D. It cannot send packets to 10.10.13.128/25.
DRAG DROP - Drag and drop the characteristic from the left onto the IPv6 address type on the right.
Refer to the exhibit. Host A switch interface is configured in VLAN 2. Host D sends a unicast packet destined for the IP address of host A.
What does the switch do when it receives the frame from host D?
A. It floods the frame out of every ports except the source port.
B. It creates a broadcast storm.
C. It shuts down the source port and places it in err-disable mode.
D. It drops the frame from the MAC table of the switch.
What is a feature of WPA?
A. TKIP/MIC encryption
B. small Wi-Fi application
C. preshared key
D. 802.1x authentication
What is the collapsed layer in collapsed core architectures?
A. Core and distribution
B. access and WAN
C. distribution and access
D. core and WAN
Refer to the exhibit. The IPv6 address for the LAN segment on router R1 must be configured using the EUI-64 format. When configured which ipv6 address is produced by the router?
A. 2001:db8:1a44:41a4:C081:BFFF:FE4A:1
B. 2001:db8:1a44:41a4:C801:BEFF:FE4A:1
C. 2001:db8:1a44:41a4:4660:592F:FE65:1
D. 2001:db8:1a44:41a4:C800:BAFE:FF00:1
What does a switch search for in the CAM table when forwarding a frame?
A. source MAC address and aging time
B. destination MAC address and flush time
C. source MAC address and source port
D. destination MAC address and destination port
Refer to the exhibit. A network engineer started to configure port security on a new switch. These requirements must be met: • MAC addresses must be learned dynamically. • Log messages must be generated without disabling the interface when unwanted traffic is seen. Which two commands must be configured to complete this task? (Choose two.)
A. SW(config-if)#switchport port-security violation restrict
B. SW(config-if)#switchport port-security mac-address 0010.7B84.45E6
C. SW(config-if)#switchport port-security maximum 2
D. SW(config-if)#switchport port-security violation shutdown
E. SW(config-if)#switchport port-security mac-address sticky
What occurs to frames during the process of frame flooding?
A. Frames are sent to all ports, including those that are assigned to other VLANs.
B. Frames are sent to every port on the switch that has a matching entry in MAC address table.
C. Frames are sent to every port on the switch in the same VLAN except from the originating port.
D. Frames are sent to every port on the switch in the same VLAN.
What are two reasons to deploy private addressing on a network? (Choose two.)
A. to subnet addresses in an organized hierarchy
B. to reduce network maintenance costs
C. to segment local IP addresses from the global routing table
D. to hide sensitive data from access users within an enterprise
E. to route protected data securely via an Internet service provider
An engineering team asks an implementer to configure syslog for warning conditions and error conditions. Which command does the implementer configure to achieve the desired result?
A. logging trap 5
B. logging trap 2
C. logging trap 3
D. logging trap 4
Which JSON data type is an unordered set of attribute-value pairs?
A. string
B. array
C. Boolean
D. object
A network administrator wants the syslog server to filter incoming messages into different files based on their importance. Which filtering criteria must be used?
A. message body
B. level
C. facility
D. process ID
What is the benefit of configuring PortFast on an interface?
A. The frames entering the interface are marked with the higher priority and then processed faster by a switch.
B. After the cable is connected, the interface is available faster to send and receive user data.
C. Real-time voice and video frames entering the interface are processed faster.
D. After the cable is connected, the interface uses the fastest speed setting available for that cable type.
Refer to the exhibit. Which configuration enables SW2 to establish an LACP EtherChannel?
A.

B.

C.

D.

DRAG DROP - Drag and drop the SNMP components from the left onto the descriptions on the right.
Refer to the exhibit. A newly configured PC fails to connect to the internet by using TCP port 80 to www.cisco.com. Which setting must be modified for the connection to work?
A. Subnet Mask
B. DNS Servers
C. Default Gateway
D. DHCP Servers
Which device separates networks by security domains?
A. intrusion protection system
B. firewall
C. wireless controller
D. access point
Refer to the exhibit. How many arrays are present in the JSON data?
A. one
B. three
C. six
D. nine
Which type of hypervisor operates without an underlying OS to host virtual machines?
A. Type 1
B. Type 2
C. Type 3
D. Type 12
Refer to the exhibit. A network engineer configures the CCNA WLAN so that clients must reauthenticate hourly and to limit the number of simultaneous connections to the WLAN to 10. Which two actions complete this configuration? (Choose two.)
A. Enable the Wi-Fi Direct Clients Policy option
B. Enable the Enable Session Timeout option and set the value to 3600.
C. Enable the Client Exclusion option and set the value to 3600.
D. Set the Maximum Allowed Clients value to 10.
E. Set the Maximum Allowed Clients Per AP Radio value to 10.
What are network endpoints?
A. support inter-VLAN connectivity
B. a threat to the network if they are compromised
C. act as routers to connect a user to the service provider network
D. enforce policies for campus-wide traffic going to the Internet
Which option about JSON is true -
A. uses predefined tags or angle brackets () to delimit markup text
B. used to describe structured data that includes arrays
C. used for storing information
D. similar to HTML, it is more verbose than XML
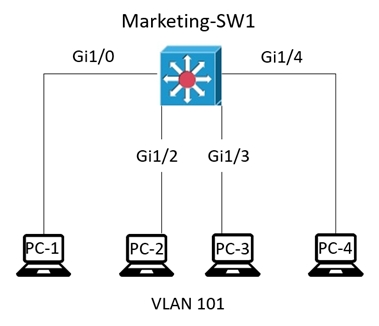
Refer to the exhibit. The entire Marketing-SW1 MAC address table is shown here: What does the switch do when PC-4 sends a frame to PC-1?
A. It performs a lookup in the MAC address table and discards the frame due to a missing entry.
B. It maps the Layer 2 MAC address to the Layer 3 IP address and forwards the frame.
C. It inserts the source MAC address and port into the table and forwards the frame to PC-1.
D. It floods the frame out of all ports except on the port where PC-1 is connected.
Which statement compares traditional networks and controller-based networks?
A. Only controller-based networks decouple the control plane and the data plane.
B. Traditional and controller-based networks abstract policies from device configurations.
C. Only traditional networks natively support centralized management.
D. Only traditional networks offer a centralized control plane.
What is represented by the word "LB13" within this JSON schema?
A. array
B. value
C. object
D. key
What are two reasons that cause late collisions to increment on an Ethernet interface? (Choose two.)
A. when Carrier Sense Multiple Access/Collision Detection is used
B. when one side of the connection is configured for half-duplex
C. when the sending device waits 15 seconds before sending the frame again
D. when a collision occurs after the 32nd byte of a frame has been transmitted
E. when the cable length limits are exceeded
Which plane is centralized in software-defined networking?
A. application
B. services
C. data
D. control
Refer to the exhibit. Which network prefix was learned via EIGRP?
A. 172.160.0/16
B. 207.165.200.0/24
C. 192.168.1.0/24
D. 192.168.2.0/24
Free Access Full 200-301 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 200-301 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 200-301 certification journey!













