200-301 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 200-301 certification exam? Start your preparation the smart way with our 200-301 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 200-301 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 200-301 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
Which global command encrypts all passwords in the running configuration?
A. service password-encryption
B. enable password-encryption
C. enable secret
D. password-encrypt
Refer to the exhibit. According to the output, which parameter set is validated using the routing table of R7?
A. R7 is missing a gateway of last resort.R7 is receiving routes that were redistributed in EIGRP.R7 will forward traffic destined to 10.90.8.0/24.
B. R7 has a gateway of last resort available.R7 is receiving routes that were redistributed from BGP.R7 will drop traffic destined to 10.90.8.0/24.
C. R7 is missing a gateway of last resort.R7 is receiving routes that were redistributed from BGP.R7 will forward traffic destined to 10.90.8.0/24.
D. R7 has a gateway of last resort available.R7 is receiving routes that were redistributed in EIGRP.R7 will drop traffic destined to 10.90.8.0/24.
What is the collapsed layer in collapsed core architectures?
A. Core and distribution
B. access and WAN
C. distribution and access
D. core and WAN
Which output displays a JSON data representation? A.B.
C.
D.
Which two wireless security standards use counter mode cipher block chaining Message Authentication Code Protocol for encryption and data integrity? (Choose two.)
A. Wi-Fi 6
B. WPA3
C. WEP
D. WPA2
E. WPA
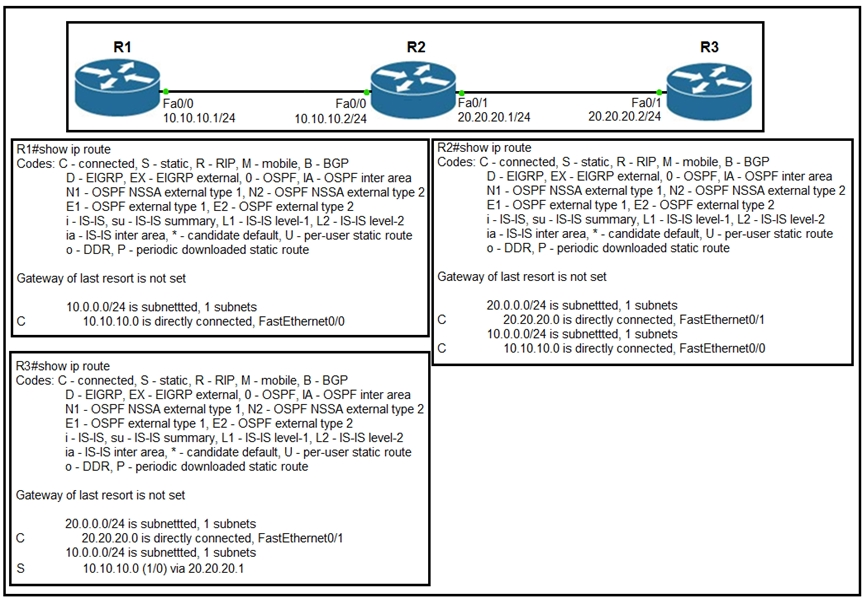
Refer to the exhibit. Router R1 Fa0/0 cannot ping router R3 Fa0/1. Which action must be taken in router R1 to help resolve the configuration issue?
A. set the default gateway as 20.20.20.2
B. configure a static route with Fa0/1 as the egress interface to reach the 20.20.2.0/24 network
C. configure a static route with 10.10.10.2 as the next hop to reach the 20.20.20.0/24 network
D. set the default network as 20.20.20.0/24
Refer to the exhibit. Which prefix does Router1 use for traffic to Host A?
A. 10.10.10.0/28
B. 10.10.13.0/25
C. 10.10.13.144/28
D. 10.10.13.208/29
Refer to the exhibit. An engineer configures interface fa0/1 on SW1 and SW2 to pass traffic from two different VLANs. For security reasons, company policy requires the native VLAN to be set to a nondefault value. Which configuration meets this requirement?
A. Switch(config-if)#switchport mode trunkSwitch(config-if)#switchport trunk encapsulation dot1qSwitch(config-if)#switchport trunk allowed vlan 100,105Switch(config-if)#switchport trunk native vlan 3
B. Switch(config-if)#switchport mode trunkSwitch(config-if)#switchport trunk encapsulation islSwitch(config-if)#switchport trunk allowed vlan 100,105Switch(config-if)#switchport trunk native vlan 1
C. Switch(config-if)#switchport mode dynamicSwitch(config-if)#switchport access vlan 100,105Switch(config-if)#switchport trunk native vlan 1
D. Switch(config-if)#switchport mode accessSwitch(config-if)#switchport trunk encapsulation dot1qSwitch(config-if)#switchport access vlan 100,105Switch(config-if)#switchport trunk native vlan 3
Refer to the exhibit. Switch AccSw1 has just been added to the network along with PC2. All VLANs have been implemented on AccSw2. How must the ports on AccSw2 be configured to establish Layer 2 connectivity between PC1 and PC2?
A. interface GigabitEthernet1/2 switchport mode access switchport access vlan 2 ! interface GigabitEthernet1/24 switchport mode trunk
B. interface GigabitEthernet1/1 switchport mode access switchport access vlan 11 ! interface GigabitEthernet1/24 switchport mode trunk
C. interface GigabitEthernet1/24 switchport mode trunk switchport trunk allowed vlan 11, 12 ! interface GigabitEthernet1/1 switchport access vlan 11
D. interface GigabitEthernet1/2 switchport mode access switchport access vlan 12 ! interface GigabitEthernet1/24 switchport mode trunk switchport trunk allowed vlan 11, 12
Refer to the exhibit. The network engineer is configuring router R2 as a replacement router on the network. After the initial configuration is applied, it is determined that R2 failed to show R1 as a neighbor. Which configuration must be applied to R2 to complete the OSPF configuration and enable it to establish the neighbor relationship with R1?
A. R2(config)#router ospf 1 R2(config-router)#network 192.168.1.0 255.255.255.0 area 2
B. R2(config)#interface g0/0/0 R2(config-if)#ip ospf hello-interval 10
C. R2(config)#interface g0/0/0 R2(config-if)#ip ospf dead-interval 40
D. R2(config)#router ospf 1 R2(config-router)#router-id 192.168.1.2
Refer to the exhibit. IPv6 is being implemented within the enterprise. The command ipv6 unicast-routing is configured. Interface Gig0/0 on R1 must be configured to provide a dynamic assignment using the assigned IPv6 block. Which command accomplishes this task?
A. ipv6 address 2001:DB8:FFFF:FCF3::64 link-local
B. ipv6 address 2001:DB8:FFFF:FCF3::1/64
C. ipv6 address 2001:DB8:FFFF:FCF3::64 eui-64
D. ipv6 address autoconfig 2001:DB8:FFFF:FCF2::/64
Refer to the exhibit. What is the next hop for traffic entering R1 with a destination of 10.1.2.126?
A. 10.165.20.126
B. 10.165.20.146
C. 10.165.20.166
D. 10.165.20.226
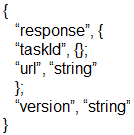
Refer to the exhibit. Which type of JSON data is represented?
A. number
B. array
C. object
D. string
What is a characteristic of private IPv4 addressing?
A. composed of up to 65,536 available addresses
B. issued by IANA in conjunction with an autonomous system number
C. used without tracking or registration
D. traverse the Internet when an outbound ACL is applied
DRAG DROP - Drag and drop the characteristic from the left onto the cable type on the right.
hostname CPE service password-encryption ip domain name ccna.cisco.com ip name-server 198.51.100.210 crypto key generate rsa modulus 1024 username admin privilege 15 secret s0m3s3cr3t line vty 0 4 transport input ssh login local Refer to the exhibit. An engineer executed the script and added commands that were not necessary for SSH and now must remove the commands. Which two commands must be executed to correct the configuration? (Choose two.)
A. no ip name-serveer 198.51.100.210
B. no login local
C. no service password-encryption
D. no ip domain mame ccna.cisco.com
E. no hostname CPE
Refer to the exhibit. Configurations for the switch and PCs are complete. Which configuration must be applied so that VLANs 2 and 3 communicate back and forth?
A. interface GigabitEthernet0/0 ip address 10.10.2.10 255.255.252.0
B. interface GigabitEthernet0/0.10 encapsulation dot1Q 3 ip address 10.10.2.10 255.255.254.0
C. interface GigabitEthernet0/0.3 encapsulation dot1Q 3 native ip address 10.10.2.10 255.255.252.0
D. interface GigabitEthernet0/0.3 encapsulation dot1Q 10 ip address 10.10.2.10 255.255.255.252
R1 has learned route 192.168.12.0/24 via IS-IS, OSPF, RIP, and Internal EIGRP. Under normal operating conditions, which routing protocol is installed in the routing table?
A. IS-IS
B. Internal EIGRP
C. RIP
D. OSPF
What is a characteristic of encryption in wireless networks?
A. intercepts data threats before they attack a network
B. uses policies to prevent unauthorized users
C. must include a combination of letters and numbers
D. encodes and decodes data for authorized users
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices. • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology tab to access the device console(s) and perform the tasks. • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window. • All necessary preconfigurations have been applied. • Do not change the enable password or hostname for any device. • Save your configurations to NVRAM before moving to the next item. • Click Next at the bottom of the screen to submit this lab and move to the next question. • When Next is clicked, the lab doses and cannot be reopened. Topology -Tasks - R1 has been pre-configured with all the necessary commands. All physical cabling is in place and verified. Connectivity for PC1 and PC2 must be established to the switches, and each port must only allow one VLAN. 1. Configure SW-1 with VLAN 35 and label it exactly as SALES 2. Configure SW-2 with VLAN 39 and label it exactly as MARKETING 3. Configure the switch port connecting to PC1 4. Configure the switch port connecting to PC2 5. Configure SW-1 and SW-2 for universal neighbor discovery using the industry standard protocol and disable it on the interface connecting to PC1
Refer to the exhibit. A network engineer is configuring a wireless LAN with Web Passthrough Layer 3 Web Policy. Which action must the engineer take to complete the configuration?
A. Set the Layer 2 Security to 802.1X.
B. Enable TKIP and CCMP256 WPA2 Encryption.
C. Enable the WPA Policy.
D. Set the Layer 2 Security to None.
An implementer is preparing hardware for virtualization to create virtual machines on a host. What is needed to provide communication between hardware and virtual machines?
A. router
B. hypervisor
C. switch
D. straight cable
Refer to the exhibit. A public IPv6 address must be configured for internet access. Which command must be configured on the R2 WAN interface to the service provider?
A. ipv6 address fe80::/10
B. ipv6 address 2001:db8:433:37:7710:ffff:ffff:ffff/64 anycast
C. ipv6 address 2001:db8:123:45::4/64
D. ipv6 address fe80::260:3EFF:FE11:6770 link-local
Refer to the exhibit. A network engineer started to configure port security on a new switch. These requirements must be met: • MAC addresses must be learned dynamically. • Log messages must be generated without disabling the interface when unwanted traffic is seen. Which two commands must be configured to complete this task? (Choose two.)
A. SW(config-if)#switchport port-security violation restrict
B. SW(config-if)#switchport port-security mac-address 0010.7B84.45E6
C. SW(config-if)#switchport port-security maximum 2
D. SW(config-if)#switchport port-security violation shutdown
E. SW(config-if)#switchport port-security mac-address sticky
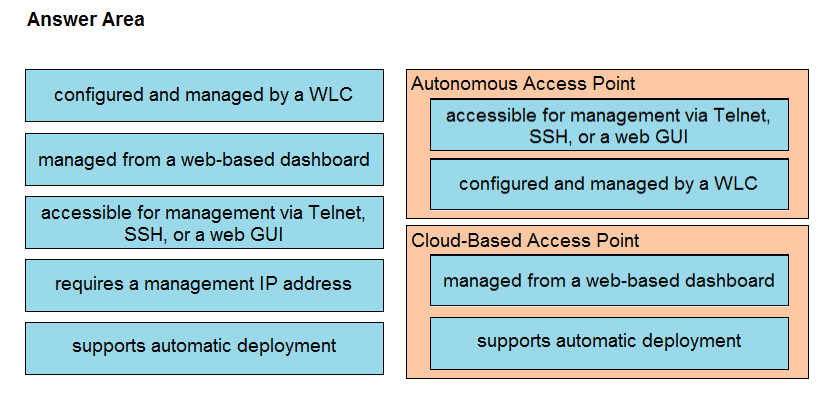
DRAG DROP - Drag and drop the facts about wireless architectures from the left onto the types of access point on the right. Not all options are used. Select and Place:
DRAG DROP - Drag and drop the Qos features from the left onto the corresponding statements on the right.
When configuring an EtherChannel bundle, which mode enables LACP only if a LACP device is detected?
A. Passive
B. Desirable
C. On
D. Auto
E. Active
Refer to the exhibit. Which switch becomes the root of the spanning tree?Switch 1 - BID: 32778 0018.184e.3c00 - Switch 2 - BID: 24586 001a.e3ff.a680 - Switch 3 - BID: 28682 0022.55cf.cc00 - Switch 4 - BID: 64000 4e15.8403.08f -
A. Switch 1
B. Switch 2
C. Switch 3
D. Switch 4
Refer to the exhibit. The ntp server 192.168.0.3 command has been configured on router 1 to make it an NTP client of router 2. Which command must be configured on router 2 so that it operates in server-only mode and relies only on its internal clock?
A. Router2(config)#ntp server 172.17.0.1
B. Router2(config)#ntp server 192.168.0.2
C. Router2(config)#ntp passive
D. Router2(config)#ntp master 4
Refer to the exhibit. What is missing from this output for it to be executed?
A. double quotes (” “) around the “Cisco Devices” string
B. exclamation point (!) at the beginning of each line
C. square bracket ( [ ) at the beginning
D. curly braket ( } ) at the end
Refer to the exhibit. Which switch in this configuration will be elected as the root bridge?
A. SW1: 0C:4A:82.:65:62:72
B. SW2: 0C:0A:A8:1A:3C:9D
C. SW3: 0C:0A:18:81:B3:19
D. SW4: 0C:0A:05:22:05:97
Refer to the exhibit. Shortly after SiteA was connected to SiteB over a new single-mode fiber path, users at SiteA report intermittent connectivity issues with applications hosted at SiteB. What is the cause of the intermittent connectivity issue?
A. Interface errors are incrementing.
B. High usage is causing high latency.
C. An incorrect SFP media type was used at SiteA.
D. The sites were connected with the wrong cable type.
Refer to the exhibit. What are two conclusions about this configuration? (Choose two.)
A. The spanning-tree mode is Rapid PVST+
B. This tea root bridge
C. The spanning-tree mode is PVST+
D. The designated port is FastEthernet 2/1
E. The root port is FastEthernet 2/1
An engineer must configure an OSPF neighbor relationship between router R1 and R3. The authentication configuration has been configured and the connecting interfaces are in the same 192.168.1.0/30 subnet. What are the next two steps to complete the configuration? (Choose two.)
A. configure the interfaces as OSPF active on both sides
B. configure both interfaces with the same area ID
C. configure the hello and dead timers to match on both sides
D. configure the same process ID for the router OSPF process
E. configure the same router ID on both routing processes
Refer to the exhibit. The engineer configured the VLANs on the new AccSw2 switch. A router-on-a-stick is connected to both switches. How must the ports be configured on AccSw2 to establish full connectivity between the two switches and for Server1?
A. interface GigabitEthernet1/1switchport access vlan 11!interface GigabitEthernet1/24switchport mode trunkswitchport trunk allowed vlan 10,11
B. interface GigabitEthernet1/3switchport mode accessswitchport access vlan 10!interface GigabitEthernet1/24switchport mode trunkswitchport trunk allowed vlan 2,10
C. interface GigabitEthernet1/3switchport mode accessswitchport access vlan 10!interface GigabitEthernet1/24switchport mode trunk
D. interface GigabitEthernet1/1switchport mode accessswitchport access vlan 11!interface GigabitEthernet1/24switchport mode trunk
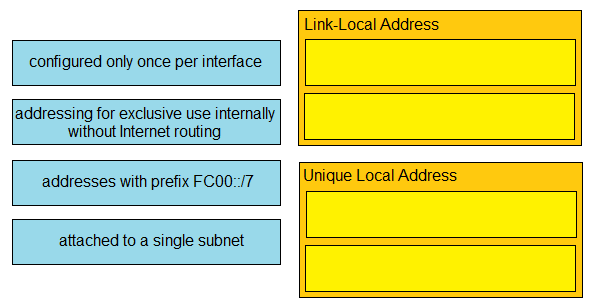
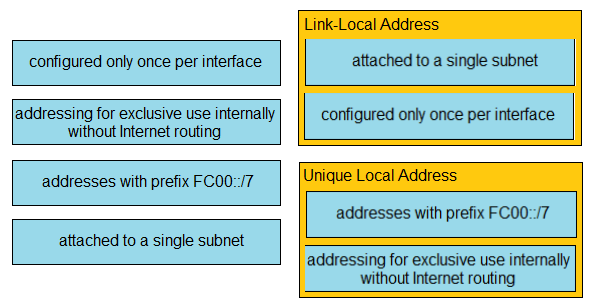
DRAG DROP - Drag and drop the IPv6 address type characteristics from the left to the right. Select and Place:
What is a characteristic of private IPv4 addressing?
A. used on the external interface of a firewall
B. used by ISP’s when only one IP is needed to connect to the internet
C. reduces the forwarding table on network routers
D. address space which is isolated from the internet
An organization has decided to start using cloud-provided services. Which cloud service allows the organization to install its own operating system on a virtual machine?
A. platform-as-a-service
B. network-as-a-service
C. software-as-a-service
D. infrastructure-as-a-service
Which function is performed by the collapsed core layer in a two-tier architecture?
A. enforcing routing policies
B. marking interesting traffic for data policies
C. applying security policies
D. attaching users to the edge of the network
Refer to the exhibit. When router R1 receives a packet with destination IP address 10.56.0.62, through which interface does it route the packet?
A. Vlan58
B. Null0
C. Vlan59
D. Vlan60
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology tab to access the device console(s) and perform the tasks • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window • All necessary preconfigurations have been applied • Do not change the enable password or hostname for any device • Save your configurations to NVRAM before moving to the next item • Click Next at the bottom of the screen to submit this lab and move to the next question • When Next is clicked the lab closes and cannot be reopened Topology -Tasks - Physical connectivity is implemented between the two Layer 2 switches, and the network connectivity between them must be configured. 1. Configure an LACP EtherChannel and number it as 44; configure it between switches SW1 and SW2 using interfaces Ethemet0/0 and Ethernet0/1 on both sides. The LACP mode must match on both ends. 2. Configure the EtherChannel as a trunk link. 3. Configure the trunk link with 802.1q tags. 4. Configure VLAN 'MONITORING' as the untagged VLAN of the EtherChannel.
Which command can you enter to allow Telnet to be supported in addition to SSH?
A. transport input telnet ssh
B. transport input telnet
C. no transport input telnet
D. privilege level 15
What is a characteristic of private IPv4 addressing?
A. is used when the ISP requires the new subnet to be advertised to the internet for web services
B. allows multiple companies to use the same addresses without conflict
C. is used on the external interface of a firewall
D. allows endpoints to communicate across public network boundaries
Refer to the exhibit. How does the router manage traffic to 192.168.12.16?
A. It chooses the EIGRP route because it has the lowest administrative distance.
B. It load-balances traffic between all three routes.
C. It chooses the OSPF route because it has the longest prefix inclusive of the destination address.
D. It selects the RIP route because it has the longest prefix inclusive of the destination address.
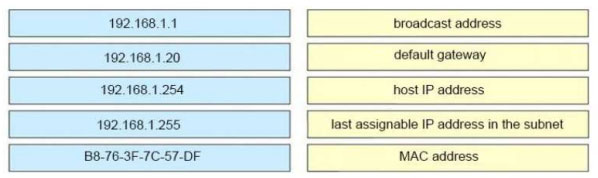
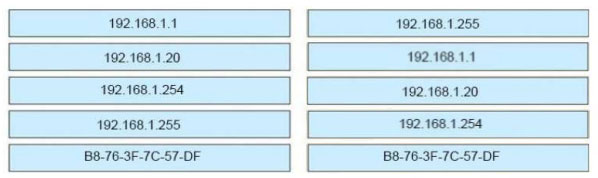
DRAG DROP - Refer to the exhibit.An engineer is tasked with verifying network configuration parameters on a client workstation to report back to the team lead. Drag and drop the node identifiers from the left onto the network parameters on the right. Select and Place:
Refer to the exhibit. An extended ACL has been configured and applied to router R2. The configuration failed to work as intended. Which two changes stop outbound traffic on TCP ports 25 and 80 to 10.0.20.0/26 from the 10.0.10.0/26 subnet while still allowing all other traffic? (Choose two.)
A. Add a ג€permit ip any anyג€ statement at the end of ACL 101 for allowed traffic.
B. Add a ג€permit ip any anyג€ statement to the beginning of ACL 101 for allowed traffic.
C. The ACL must be moved to the Gi0/1 interface outbound on R2.
D. The source and destination IPs must be swapped in ACL 101.
E. The ACL must be configured the Gi0/2 interface inbound on R1.
DRAG DROP - Drag and drop the VLAN port modes from the left onto the descriptions on the right.
If a switch port receives a new frame while it is actively transmitting a previous frame, how does it process the frames?
A. The new frame is delivered first, the previous frame is dropped, and a retransmission request is sent
B. The previous frame is delivered, the new frame is dropped, and a retransmission request is sent
C. The new frame is placed in a queue for transmission after the previous frame
D. The two frames are processed and delivered at the same time
Which channel-group mode must be configured when multiple distribution interfaces connected to a WLC are bundled?
A. Channel-group mode passive.
B. Channel-group mode on.
C. Channel-group mode desirable.
D. Channel-group mode active.
Which two command sequences must be configured on a switch to establish a Layer 3 EtherChannel with an open-standard protocol? (Choose two.)
A. interface GigabitEthernet0/0/1 channel-group 10 mode auto
B. interface GigabitEthernet0/0/1 channel-group 10 mode on
C. interface port-channel 10 no switchport ip address 172.16.0.1 255.255.255.0
D. interface GigabitEthernet0/0/1 channel-group 10 mode active
E. interface port-channel 10 switchport switchport mode trunk
Access Full 200-301 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 200-301 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 200-301 mock test free today—and take a major step toward exam success!