200-301 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the 200-301 certification? Our 200-301 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective 200-301 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic 200-301 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
Which value is the unique identifier that an access point uses to establish and maintain wireless connectivity to wireless network devices?
A. VLAN ID
B. SSID
C. RFID
D. WLAN ID
Which wireless security protocol relies on Perfect Forward Secrecy?
A. WEP
B. WPA2
C. WPA
D. WPA3
What is the difference in data transmission delivery and reliability between TCP and UDP?
A. TCP transmits data at a higher rate and ensures packet delivery. UDP retransmits lost data to ensure applications receive the data on the remote end.
B. TCP requires the connection to be established before transmitting data. UDP transmits data at a higher rate without ensuring packet delivery.
C. UDP sets up a connection between both devices before transmitting data. TCP uses the three-way handshake to transmit data with a reliable connection.
D. UDP is used for multicast and broadcast communication. TCP is used for unicast communication and transmits data at a higher rate with error checking.
DRAG DROP - Drag and drop the RF terms from the left onto the corresponding statements on the right.
Which interface enables communication between a program on the controller and a program on the networking device?
A. software virtual interface
B. tunnel interface
C. northbound interface
D. southbound interface
Refer to the exhibit. Only four switches are participating in the VLAN spanning-tree process. Branch-1: priority 614440 - Branch-2: priority 39391170 - Branch-3: priority 0 - Branch-4: root primary - Which switch becomes the permanent root bridge for VLAN 5?
A. Branch-1
B. Branch-2
C. Branch-3
D. Branch-4
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology tab to access the device console(s) and perform the tasks. • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window. • All necessary preconfigurations have been applied. • Do not change the enable password or hostname for any device. • Save your configurations to NVRAM before moving to the next item. • Click Next at the bottom of the screen to submit this lab and move to the next question. • When Next is clicked the lab closes and cannot be reopened. Topology -Tasks - IP connectivity and OSPF are preconfigured on all devices where necessary. Do not make any changes to the IP addressing or OSPF. The company policy uses connected interfaces and next hops when configuring static routes except for load balancing or redundancy without floating static. Connectivity must be established between subnet 172.20.20.128/25 on the Internet and the LAN at 192.168.0.0/24 connected to SW1: 1. Configure reachability to the switch SW1 LAN subnet in router R2. 2. Configure default reachability to the Internet subnet in router R1. 3. Configure a single static route in router R2 to reach to the Internet subnet considering both redundant links between routers R1 and R2. A default route is NOT allowed in router R2. 4. Configure a static route in router R1 toward the switch SW1 LAN subnet where the primary link must be through Ethernet0/1, and the backup link must be through Ethernet0/2 using a floating route. Use the minimal administrative distance value when required.
DRAG DROP - Drag and drop the DNS commands from the left onto their effects on the right.
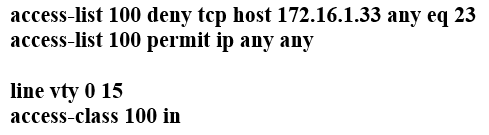
Refer to the exhibit. Which two commands must be configured on router R1 to enable the router to accept secure remote-access connections? (Choose two.)
A. ip ssh pubkey-chain
B. username cisco password 0 cisco
C. crypto key generate rsa
D. transport input telnet
E. login console
Refer to the exhibit. PC A is communicating with another device at IP address 10.225.34.225. Through which router does router Y route the traffic?
A. router A
B. router B
C. router C
D. router D
What is a function of a remote access VPN?
A. establishes a secure tunnel between two branch sites
B. uses cryptographic tunneling to protect the privacy of data for multiple users simultaneously
C. used exclusively when a user is connected to a company’s internal network
D. allows the users to access company internal network resources through a secure tunnel
Which network action occurs within the data plane?
A. reply to an incoming ICMP echo request
B. make a configuration change from an incoming NETCONF RPC
C. run routing protocols (OSPF, EIGRP, RIP, BGP)
D. compare the destination IP address to the IP routing table
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology tab to access the device console(s) and perform the tasks. • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window. • All necessary pre-configurations have been applied. • Do not change the enable password or hostname for any device. • Save your configurations to NVRAM before moving to the next item. • Click Next at the bottom of the screen to submit this lab and move to the next question. • When Next is clicked, the lab closes and cannot be reopened. Topology -Tasks - Refer to the topology. All physical cabling is in place. Configure local user account, configure a Named ACL (NACL), and Dynamic Arp Inspection. 1. Configure a local account on Sw3 with telnet access only on virtual ports 0-4. Use the following information: o Username: tech12 o Password: load1key o Algorithm type: md5 o Privilege level: Exec mode 2. Configure and apply a NACL on R1 to control network traffic towards ISP: o Name: ISP_ACL o Restrict RFC 1918 class A and B addresses o Allow all other addresses 3. A DHCP IP Pool is preconfigured on R1 for VLAN 5, and DHCP Snooping is configured on Sw2. Configure on Sw2: o Dynamic Arp Inspection for VLAN 5 o Enable validation of the ARP packet destination MAC address o Enable validation of the ARP packet source MAC address o Enable validation of the ARP Packet IP address
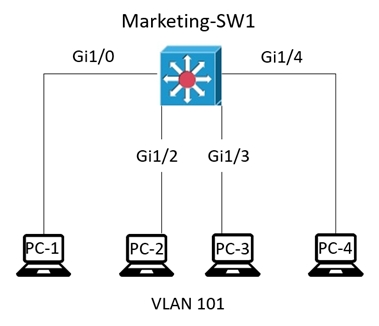
Refer to the exhibit. The entire Marketing-SW1 MAC address table is shown here: What does the switch do when PC-4 sends a frame to PC-1?
A. It performs a lookup in the MAC address table and discards the frame due to a missing entry.
B. It maps the Layer 2 MAC address to the Layer 3 IP address and forwards the frame.
C. It inserts the source MAC address and port into the table and forwards the frame to PC-1.
D. It floods the frame out of all ports except on the port where PC-1 is connected.
What is a characteristic of private IPv4 addressing?
A. is used when the ISP requires the new subnet to be advertised to the internet for web services
B. provides unlimited address ranges
C. is used when the network has multiple endpoint listeners
D. alleviates the shortage of IPv4 addresses
Which type of security program is violated when a group of employees enters a building using the ID badge of only one person?
A. intrusion detection
B. network authorization
C. physical access control
D. user awareness
Refer to the exhibit. A network engineer must update the configuration on Switch2 so that it sends LLDP packets every minute and the information sent via LLDP is refreshed every 3 minutes. Which configuration must the engineer apply?
A. Switch2(config)#lldp timer 60 Switch2(config)#lldp tlv-select 180
B. Switch2(config)#lldp timer 60 Switch2(config)#lldp holdtime 180
C. Switch2(config)#lldp timer 1 Switch2(config)#lldp holdtime 3
D. Switch2(config)#lldp timer 1 Switch2(config)#lldp tlv-select 3
After you deploy a new WLAN controller on your network, which two additional tasks should you consider? (Choose two.)
A. deploy load balancers
B. configure additional vlans
C. configure multiple VRRP groups
D. deploy POE switches
E. configure additional security policies
Refer to the exhibit. An engineer must configure router R2 so it is elected as the DR on the WAN subnet. Which command sequence must be configured?
A. interface gigabitethernet0/0 ip address 10.0.0.34 255.255.255.248 ip ospf priority 0
B. interface gigabitethernet0/0 ip address 10.0.0.34 255.255.255.224 ip ospf priority 100
C. interface gigabitethernet0/0 ip address 10.0.1.1 255.255.255.0 ip ospf priority 255
D. interface gigabitethernet0/0 ip address 10.0.1.1 255.255.255.224 ip ospf priority 98
On a corporate network, hosts on the same VLAN can communicate with each other, but they are unable to communicate with hosts on different VLANs. What is needed to allow communication between the VLANs?
A. a router with subinterfaces configured on the physical interface that is connected to the switch
B. a router with an IP address on the physical interface connected to the switch
C. a switch with an access link that is configured between the switches
D. a switch with a trunk link that is configured between the switches
What is the difference between an IPv6 link-local address and a unique local address?
A. The scope of an IPv6 link-local address is limited to a directly attached interface, but an IPv6 unique local address is used throughout a company site or network.
B. The scope of an IPv6 link-local address is global, but the scope of an IPv6 unique local address is limited to a loopback address.
C. The scope of an IPv6 link-local address can be used throughout a company site or network, but an IPv6 unique local address is limited to a loopback address.
D. The scope of an IPv6 link-local address is limited to a loopback address, and an IPv6 unique local address is limited to a directly attached interface.
When a client and server are not on the same physical network, which device is used to forward requests and replies between client and server for DHCP?
A. DHCPOFFER
B. DHCP relay agent
C. DHCP server
D. DHCPDISCOVER
Which two features introduced in SNMPv2 provide the ability to retrieve large amounts of data in one request and acknowledge a trap using PDUs? (Choose two.)
A. Get
B. GetNext
C. Set
D. GetBulk
E. Inform
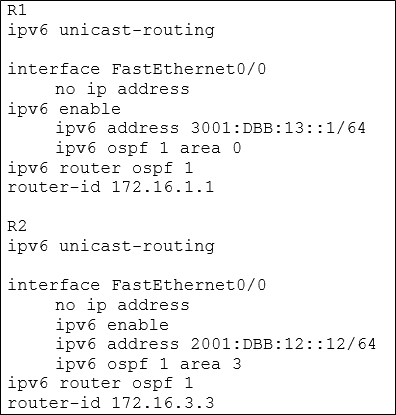
Refer to the exhibit. After you apply the given configurations to R1 and R2 you notice that OSPFv3 fails to start.
A. The area numbers on R1 and R2 are mismatched
B. The IPv6 network addresses on R1 and R2 are mismatched
C. The autonomous system numbers on R1 and R2 are mismatched
D. The router ids on R1 and R2 are mismatched
What are two benefits for using private IPv4 addressing? (Choose two.)
A. They allow for Internet access from IoT devices.
B. They alleviate the shortage of public IPv4 addresses.
C. They provide a layer of security from internet threats.
D. They supply redundancy in the case of failure.
E. They offer Internet connectivity to endpoints on private networks.
Which command is used to verify the DHCP relay agent address that has been set up on your Cisco IOS router?
A. show ip interface brief
B. show ip dhcp bindings
C. show ip route
D. show ip interface
E. show interface
F. show ip dhcp pool
When a site-to-site VPN is configured which IPsec mode provides encapsulation and encryption of the entire original IP packet?
A. IPsec transport mode with AH
B. IPsec tunnel mode with AH
C. IPsec transport mode with ESP
D. IPsec tunnel mode with ESP
Refer to the exhibit. A router received these five routes from different routing information sources. Which two routes does the router install in its routing table? (Choose two.)
A. OSPF route 10.0.0.0/30
B. IBGP route 10.0.0.0/30
C. OSPF route 10.0.0.0/16
D. EIGRP route 10.0.0.1/32
E. RIP route 10.0.0.0/30
How does MAC learning function?
A. enabled by default on all VLANs and interfaces
B. increases security on the management VLAN
C. sends frames with unknown destinations to a multicast group
D. inspects and drops frames from unknown destinations
A network administrator enters the following command on a router: logging trap 3. What are three message types that will be sent to the Syslog server? (Choose three.)
A. informational
B. emergency
C. warning
D. critical
E. debug
F. error
Which command is used to display the collection of OSPF link states?
A. show ip ospf link-state
B. show ip ospf lsa database
C. show ip ospf neighbors
D. show ip ospf database
What must be considered before deploying virtual machines?
A. resource limitations, such as the number of CPU cores and the amount of memory
B. support for physical peripherals, such as monitors, keyboards, and mice
C. whether to leverage VSM to map multiple virtual processors to two or more virtual machines
D. location of the virtual machines within the data center environment
Refer to the exhibit. Which type of route does R1 use to reach host 10.10.13.10/32?
A. default route
B. network route
C. host route
D. floating static route
Which concern is addressed with the use of private IPv4 addressing?
A. Lack of routing protocol support for CIDR and VLSM
B. Lack of security protocols at the network perimeter
C. Lack of available TCP/UDP ports per IPv5 address
D. Lack of available publicly routable unique IPv4 address
Which 802.11 frame type is indicated by a probe response after a client sends a probe request?
A. data
B. management
C. control
D. action
Refer to the exhibit. Which configuration for RTR-1 denies SSH access from PC-1 to any RTR-1 interface and allows all other traffic?A.
B.
C.
D.
What is a characteristic of private IPv4 addressing?
A. reduces network complexity
B. is used on hosts that communicate only with other internal hosts
C. simplifies the addressing in the network
D. reduces network maintenance costs
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices. • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology tab to access the device console(s) and perform the tasks. • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window. • All necessary preconfigurations have been applied. • Do not change the enable password or hostname for any device. • Save your configurations to NVRAM before moving to the next item. • Click Next at the bottom of the screen to submit this lab and move to the next question. • When Next is clicked, the lab doses and cannot be reopened. Topology -Tasks - SW-3 and SW-4 are preconfigured with all necessary commands. All physical cabling is in place and verified. All connectivity must be operational. 1. Configure both SW-1 and SW-2 switch ports e0/0 and e0/1 for 802.1q trunking with only VLANS 1, 12, and 22 permitted. 2. Configure SW-1 port e0/2 for 802.1q trunking and include only VLANS 12 and 22. 3. Configure both SW-1 and SW-2 switch ports e0/0 and e0/1 for link aggregation using the industry standard protocol. All ports must be configured so that they immediately negotiate the link.
What is the function of a server?
A. It transmits packets between hosts in the same broadcast domain.
B. It provides shared applications to end users.
C. It routes traffic between Layer 3 devices.
D. It ׁreates security zones between trusted and untrusted networks.
Which type of address is the public IP address of a NAT device?
A. outside global
B. outside local
C. inside global
D. inside local
E. outside public
F. inside public
What is the benefit of configuring PortFast on an interface?
A. The frames entering the interface are marked with the higher priority and then processed faster by a switch.
B. After the cable is connected, the interface is available faster to send and receive user data.
C. Real-time voice and video frames entering the interface are processed faster.
D. After the cable is connected, the interface uses the fastest speed setting available for that cable type.
What is a characteristic of private IPv4 addressing?
A. is used when the ISP requires the new subnet to be advertised to the internet for web services
B. allows multiple companies to use the same addresses without conflict
C. is used on the external interface of a firewall
D. allows endpoints to communicate across public network boundaries
Refer to the exhibit. Router R14 is in the process of being configured. Which configuration must be used to establish a host route to a PC 10?
A. ip route 10.80.65.10 255.255.255.254 10.80.65.1
B. ip route 10.80.65.10 255.255.255.255 10.73.65.66
C. ip route 10.73.65.66 0.0.0.255 10.80.65.10
D. ip route 10.73.65.66 255.0.0.0 10.80.65.10
Which PoE mode enables powered-devices detection and guarantees power when the device detected?
A. auto
B. static
C. dynamic
D. active
DRAG DROP - Drag and drop the statements about AAA services from the left to the corresponding AAA services on the right. Not all options are used.
Refer to the exhibit. An engineer configured NAT translations and has verified that the configuration is correct. Which IP address is the source IP after the NAT has taken place?
A. 10.4.4.4
B. 10.4.4.5
C. 172.23.103.10
D. 172.23.104.4
Which statement about VLAN configuration is true?
A. The switch must be in VTP server or transparent mode before you can configure a VLAN
B. The switch must be in config-vlan mode before you configure an extended VLAN
C. Dynamic inter-VLAN routing is supported on VLAN2 through VLAN 4064
D. A switch in VTP transparent mode save the VLAN databases to the running configuration only
Refer to the exhibit. All routers in the network are configured correctly, and the expected routes are being exchanged among the routers. Which set of routes are learned from neighbors and installed on router 2?
A. 10.129.9.0/2310.139.2.0/3010.2.191.0/3010.129.9.0/25
B. 10.129.9.0/2310.40.1.0/3010.2.191.0/3010.129.9.0/25
C. 10.40.1.0/3010.139.2.0/3010.2.191.0/3010.129.9.0/25
D. 10.129.9.0/2310.139.2.0/3010.129.9.0/2510.22.1.0/24
What is a function of MAC learning on a switch?
A. MAC address learning is disabled by default on all VLANs.
B. Frames received for a destination MAC address not listed in the address table are dropped.
C. The MAC address table is used to populate the ARP table.
D. A static MAC address is manually added to the MAC table.
Which 802.11 frame type is Association Response?
A. management
B. protected frame
C. action
D. control
Access Full 200-301 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of 200-301 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your 200-301 certification journey!