200-301 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your 200-301 certification? Our 200-301 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an 200-301 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our 200-301 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
When deploying syslog, which severity level logs informational messages?
A. 0
B. 2
C. 4
D. 6
Refer to the exhibit. Traffic sourced from the loopback0 interface is trying to connect via ssh to the host at 10.0.1.15. What is the next hop to the destination address?
A. 192.168.0.7
B. 192.168.0.4
C. 192.168.0.40
D. 192.168.3.5
What are two facts that differentiate optical-fiber cabling from copper cabling? (Choose two.)
A. It is less expensive when purchasing patch cables.
B. It carries electrical current further distances for PoE devices.
C. It provides greater throughput options.
D. It has a greater sensitivity to changes in temperature and moisture.
E. It carries signals for longer distances.
Which concern is addressed with the use of private IPv4 addressing?
A. Lack of routing protocol support for CIDR and VLSM
B. Lack of security protocols at the network perimeter
C. Lack of available TCP/UDP ports per IPv5 address
D. Lack of available publicly routable unique IPv4 address
Which fact must the engineer consider when implementing syslog on a new network?
A. Syslog defines the software or hardware component that triggered the message.
B. There are 16 different logging levels (0-15).
C. The logging level defines the severity of a particular message.
D. By default, all message levels are sent to the syslog server.
Which Rapid PVST+ feature should be configured on a switch port to immediately send traffic to a connected server as soon as it is active?
A. portfast
B. uplinkfast
C. BPDU guard
D. loop guard
Which interface type enables an application running on a client to send data over an IP network to a server?
A. northbound interface
B. application programming interface
C. southbound interface
D. Representational State Transfer application programming interface
Which action must be taken when password protection is implemented?
A. Use less than eight characters in length when passwords are complex.
B. Include special characters and make passwords as long as allowed.
C. Share passwords with senior IT management to ensure proper oversight.
D. Store passwords as contacts on a mobile device with single-factor authentication.
Refer to the exhibit. An IPv6 address must be obtained automatically on the LAN interface on R1. Which command must be implemented to accomplish the task?
A. ipv6 address autocontig
B. ipv6 address dhcp
C. ipv6 address fe80::/10
D. ipv6 address 2001:db8:d8d2:1008:4332:45:0570::/64
Which switch concept is used to create separate broadcast domains?
A. STP
B. VTP
C. VLAN
D. CSMA/CD
In which situation is private IPv4 addressing appropriate for a new subnet on the network of an organization?
A. The network has multiple endpoint listeners, and it is desired to limit the number of broadcasts.
B. The ISP requires the new subnet to be advertised to the Internet for web services.
C. There is limited unique address space, and traffic on the new subnet will stay local within the organization.
D. Traffic on the subnet must traverse a site-to-site VPN to an outside organization.
A network administrator enters the following command on a router: logging trap 3. What are three message types that will be sent to the Syslog server? (Choose three.)
A. informational
B. emergency
C. warning
D. critical
E. debug
F. error
Refer to the exhibit. A packet sourced from 172.16.32.254 is destined for 172.16.32.8. What is the subnet mask of the preferred destination route?
A. 255.255.224.0
B. 255.255.255.0
C. 255.255.255.192
D. 255.255.255.252
DRAG DROP - Drag and drop the configuration management terms from the left onto the descriptions on the right. Not all terms are used.
What is the operating mode and role of a backup port on a shared LAN segment in Rapid PVST+?
A. learning mode and provides the shortest path toward the root bridge handling traffic away from the LAN
B. blocking mode and provides an alternate path toward the designated bridge
C. forwarding mode and provides the lowest-cost path to the root bridge for each VLAN
D. listening mode and provides an alternate path toward the root bridge
A network engineer is implementing a corporate SSID for WPA3-Personal security with a PSK. Which encryption cipher must be configured?
A. CCMP128
B. GCMP256
C. CCMP256
D. GCMP128
DRAG DROP - Drag and drop the characteristic from the left onto the cable type on the right.
When a switch receives a frame for a known destination MAC address, how is the frame handled?
A. flooded to all ports except the one from which it originated
B. forwarded to the first available port
C. sent to the port identified for the known MAC address
D. broadcast to all ports
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices: • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology tab to access the device console(s) and perform the tasks. • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window. • All necessary preconfigurations have been applied. • Do not change the enable password or hostname for any device. • Save your configurations to NVRAM before moving to the next item. • Click Next at the bottom of the screen to submit this lab and move to the next question. • When Next is clicked the lab closes and cannot be reopened. Topology -Tasks - Refer to the topology. All physical cabling is in place. Configure local users accounts, modify the Named ACL (NACL), and configure DHCP Snooping. The current contents of the NACL must remain intact. Task 1 - Configure a local account on Gw1 with telnet access only on virtual ports 0-4. Use the following information: • Username: wheel • Password: lock3path • Algorithm type: Scrypt • Privilege level: Exec mode Task 2 - Configure and apply a NACL on Gw1 to control network traffic from VLAN 10: • Name: CORP_ACL • Allow BOOTP and HTTPS • Restrict all other traffic and log the ingress interface, source MAC address, the packet’s source and destination IP addresses, and ports Task 3 - Configure Sw1: • Enable DNCP Snooping for VLAN 10 • Disable DHCP Option-82 data insertion • Enable DHCP Snooping MAC address verification • Enable trusted interfaces

Which command must you enter to guarantee that an HSRP router with higher priority becomes the HSRP primary router after it is reloaded?
A. standby 10 preempt
B. standby 10 version 1
C. standby 10 priority 150
D. standby 10 version 2
A network engineer must configure two new subnets using the address block 10.70.128.0/19 to meet these requirements: ✑ The first subnet must support 24 hosts. ✑ The second subnet must support 472 hosts. ✑ Both subnets must use the longest subnet mask possible from the address block. Which two configurations must be used to configure the new subnets and meet a requirement to use the first available address in each subnet for the router interfaces? (Choose two.)
A. interface vlan 1148 ip address 10.70.148.1 255.255.254.0
B. interface vlan 3002 ip address 10.70.147.17 255.255.255.224
C. interface vlan 4722 ip address 10.70.133.17 255.255.255.192
D. interface vlan 1234 ip address 10.70.159.1 255.255.254.0
E. interface vlan 155 ip address 10.70.155.65 255.255.255.224
Which two events occur automatically when a device is added to Cisco DNA Center? (Choose two.)
A. The device is placed into the Managed state.
B. The device is placed into the Unmanaged state.
C. The device is assigned to the Local site.
D. The device is assigned to the Global site.
E. The device is placed into the Provisioned state.
DRAG DROP - Drag and drop the characteristic from the left onto the IPv6 address type on the right.
Which function does an SNMP agent perform?
A. It sends information about MIB variables in response to requests from the NMS
B. It manages routing between Layer 3 devices in a network
C. It coordinates user authentication between a network device and a TACACS+ or RADIUS server
D. It requests information from remote network nodes about catastrophic system events
What are two purposes of HSRP? (Choose two.)
A. It provides a mechanism for diskless clients to autoconfigure their IP parameters during boot.
B. It improves network availability by providing redundant gateways.
C. It groups two or more routers to operate as one virtual router.
D. It passes configuration information to hosts in a TCP/IP network.
E. It helps hosts on the network to reach remote subnets without a default gateway.
Refer to the exhibit. The ntp server 192.168.0.3 command has been configured on router 1 to make it an NTP client of router 2. Which command must be configured on router 2 so that it operates in server-only mode and relies only on its internal clock?
A. Router2(config)#ntp server 172.17.0.1
B. Router2(config)#ntp server 192.168.0.2
C. Router2(config)#ntp passive
D. Router2(config)#ntp master 4
What are two protocols within the IPsec suite? (Choose two.)
A. 3DES
B. AES
C. ESP
D. TLS
E. AH
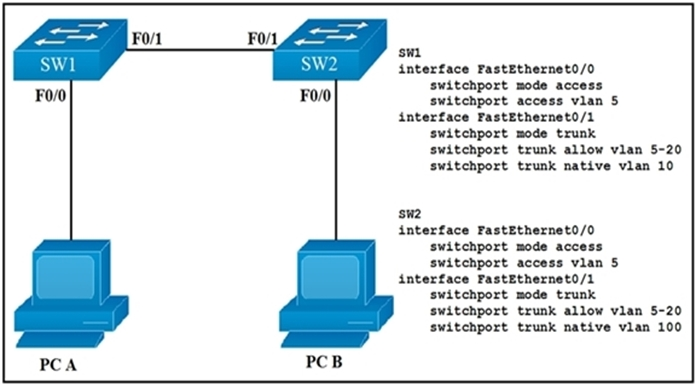
Refer to the exhibit. How will switch SW2 handle traffic from VLAN 10 on SW1?
A. It sends the traffic to VLAN 10.
B. It sends the traffic to VLAN 100.
C. It drops the traffic.
D. It sends the traffic to VLAN 1.
Which statement identifies the functionality of virtual machines?
A. Virtualized servers run most efficiently when they are physically connected to a switch that is separate from the hypervisor
B. The hypervisor can virtualize physical components including CPU, memory, and storage
C. Each hypervisor can support a single virtual machine and a single software switch
D. The hypervisor communicates on Layer 3 without the need for additional resources
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology tab to access the device console(s) and perform the tasks. • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window. • All necessary preconfigurations have been applied. • Do not change the enable password or hostname for any device. • Save your configurations to NVRAM before moving to the next item. • Click Next at the bottom of the screen to submit this lab and move to the next question. • When Next is clicked the lab closes and cannot be reopened. Topology -Tasks - Refer to the topology. All physical cabling is in place. Configure local users accounts, modify the Named ACL (NACL), and configure DHCP Snooping. The current contents of the NACL must remain intact. 1. Configure a local account on Sw103 with telnet access only on virtual ports 0-4. Use the following information: • Username: devnet • Password: access8cli • Algorithm type: SHA256 • Privilege level: Exec mode 2. Using the minimum number of ACEs, modify the existing NACL "INTERNET_ACL" to control network traffic destined for the Internet, and apply the ACL on R1: • Allow HTTPS from 172.16.0.0/16 • Allow Telnet only for VLAN 101 • Restrict all other traffic and log the ingress interface, source MAC address, the packet's source and destination IP addresses, and ports 3. Configure Sw101: • Enable DHCP Snooping for VLAN 101 • Disable DHCP Option-82 data insertion • Enable DHCP Snooping MAC address verification
Refer to the exhibit. A network engineer is verifying the settings on a new OSPF network. All OSPF configurations use the default values unless otherwise indicated. Which router does the engineer expect will be elected as the DR when all devices boot up simultaneously?
A. R1
B. R2
C. R3
D. R4
Which two protocols are used by an administrator for authentication and configuration on access points? (Choose two.)
A. 802.1Q
B. RADIUS
C. Kerberos
D. TACACS+
E. 802.1x
Which type of security program is violated when a group of employees enters a building using the ID badge of only one person?
A. intrusion detection
B. network authorization
C. physical access control
D. user awareness
How do TCP and UDP fit into a query-responsible model?
A. TCP avoids using sequencing and UDP avoids using acknowledgments
B. TCP establishes a connection prior to sending data, and UDP sends immediately
C. TCP encourages out-of-order packet delivery, and UDP prevents re-ordering
D. TCP uses error detection for packets, and UDP uses error recovery.
Refer to the exhibit. How does router R1 handle traffic to 192.168.10.16?
A. It selects the IS-IS route because it has the shortest prefix inclusive of the destination address
B. It selects the RIP route because it has the longest prefix inclusive of the destination address
C. It selects the OSPF route because it has the lowest cost
D. It selects the EIGRP route because it has the lowest administrative distance
DRAG DROP - Drag and drop the characteristic from the left onto the IPv6 address type on the right.
Which two pieces of information can you learn by viewing the routing table? (Choose two.)
A. whether an ACL was applied inbound or outbound to an interface
B. the EIGRP or BGP autonomous system
C. whether the administrative distance was manually or dynamically configured
D. which neighbor adjacencies are established
E. the length of time that a route has been known
On workstations running Microsoft Windows, which protocol provides the default gateway for the device?
A. STP
B. DHCP
C. SNMP
D. DNS
When a floating static route is configured, which action ensures that the backup route is used when the primary route fails?
A. The administrative distance must be higher on the primary route so that the backup route becomes secondary.
B. The default-information originate command must be configured for the route to be installed into the routing table.
C. The floating static route must have a lower administrative distance than the primary route so it is used as a backup.
D. The floating static route must have a higher administrative distance than the primary route so it is used as a backup
What is the function of a server?
A. It transmits packets between hosts in the same broadcast domain.
B. It provides shared applications to end users.
C. It routes traffic between Layer 3 devices.
D. It ׁreates security zones between trusted and untrusted networks.
DRAG DROP - Drag and drop the statements about device management from the left onto the corresponding device-management types on the right.
The clients and DHCP server reside on different subnets. Which command must be used to forward requests and replies between clients on the 10.10.0.1/24 subnet and the DHCP server at 192.168.10.1?
A. ip route 192.168.10.1
B. ip dhcp address 192.168.10.1
C. ip default-gateway 192.168.10.1
D. ip helper-address 192.168.10.1
Refer to the exhibit. According to the output, which parameter set is validated using the routing table of R7?
A. R7 is missing a gateway of last resort.R7 is receiving routes that were redistributed in EIGRP.R7 will forward traffic destined to 10.90.8.0/24.
B. R7 has a gateway of last resort available.R7 is receiving routes that were redistributed from BGP.R7 will drop traffic destined to 10.90.8.0/24.
C. R7 is missing a gateway of last resort.R7 is receiving routes that were redistributed from BGP.R7 will forward traffic destined to 10.90.8.0/24.
D. R7 has a gateway of last resort available.R7 is receiving routes that were redistributed in EIGRP.R7 will drop traffic destined to 10.90.8.0/24.
What is a functionality of the control plane in the network?
A. It looks up an egress interface in the forwarding information base.
B. It forwards traffic to the next hop.
C. It exchanges topology information with other routers.
D. It provides CLI access to the network device.
When configuring IPv6 on an interface, which two IPv6 multicast groups are joined? (Choose two.)
A. 2000::/3
B. 2002::5
C. FC00::/7
D. FF02::1
E. FF02::2
Which 802.11 management frame type is sent when a client roams between access points on the same SSID?
A. Reassociation Request
B. Authentication Request
C. Association Request
D. Probe Request
Refer to the exhibit. To which device does Router1 send packets that are destined to host 10.10.13.165?
A. Router2
B. Router3
C. Router4
D. Router5
A user configured OSPF and advertised the Gigabit Ethernet interface in OSPF. By default, to which type of OSPF network does this interface belong?
A. point-to-multipoint
B. point-to-point
C. broadcast
D. nonbroadcast
Refer to the exhibit. Which action must be taken to ensure that router A is elected as the DR for OSPF area 0?
A. Configure the router A interfaces with the highest OSPF priority value within the area
B. Configure router B and router C as OSPF neighbors of router A
C. Configure the OSPF priority on router A with the lowest value between the three routers.
D. Configure router A with a fixed OSPF router ID
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology tab to access the device console(s) and perform the tasks • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window • All necessary preconfigurations have been applied • Do not change the enable password or hostname for any device • Save your configurations to NVRAM before moving to the next item • Click Next at the bottom of the screen to submit this lab and move to the next question • When Next is clicked the lab closes and cannot be reopened Topology -Tasks - All physical cabling is in place. A company plans to deploy 16 new sites. The sites will utilize both IPv4 and IPv6 networks. 1. Subnet 172.16.0.0/16 to meet the subnet requirements and maximize the number of hosts • Using the second subnet - Assign the first usable IP address to e0/0 on Sw101 - Assign the last usable IP address to e0/0 on Sw102 2. Subnet 2001:DB8::/50 to meet the subnet requirements and maximize the number of hosts • Using the second subnet - Assign an IPv6 GUA using a unique 64-Bit interface identifier on e0/0 on Sw101 - Assign an IPv6 GUA using a unique 64-Bit interface identifier on e0/0 on Sw102
Access Full 200-301 Dump Free
Looking for even more practice questions? Click here to access the complete 200-301 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our 200-301 dump free questions — and get one step closer to exam success!