200-201 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the 200-201 exam? Start with our 200-201 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a 200-201 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free 200-201 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
What are two denial of service attacks? (Choose two.)A. MITM
B. TCP connections
C. ping of death
D. UDP flooding
E. code red
What describes the concept of data consistently and readily being accessible for legitimate users?A. accessibility
B. availability
C. integrity
D. confidentiality
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?A. application whitelisting/blacklisting
B. network NGFW
C. host-based IDS
D. antivirus/antispyware software
Which evasion method involves performing actions slower than normal to prevent detection?A. timing attack
B. traffic fragmentation
C. resource exhaustion
D. tunneling
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?A. integrity
B. confidentiality
C. availability
D. scope
What is the difference between the ACK flag and the RST flag in the NetFlow log session?A. The RST flag confirms the beginning of the TCP connection, and the ACK flag responds when the data for the payload is complete
B. The ACK flag confirms the beginning of the TCP connection, and the RST flag responds when the data for the payload is complete
C. The RST flag confirms the receipt of the prior segment, and the ACK flag allows for the spontaneous termination of a connection
D. The ACK flag confirms the receipt of the prior segment, and the RST flag allows for the spontaneous termination of a connection
What is a difference between signature-based and behavior-based detection?A. Signature-based identifies behaviors that may be linked to attacks, while behavior-based has a predefined set of rules to match before an alert.
B. Behavior-based identifies behaviors that may be linked to attacks, while signature-based has a predefined set of rules to match before an alert.
C. Behavior-based uses a known vulnerability database, while signature-based intelligently summarizes existing data.
D. Signature-based uses a known vulnerability database, while behavior-based intelligently summarizes existing data.
A user received a malicious email attachment named "DS045-report1122345.exe" and executed it. In which step of the Cyber Kill Chain is this event?A. reconnaissance
B. delivery
C. weaponization
D. installation
Why is HTTPS traffic difficult to screen?A. HTTPS is used internally and screening traffic for external parties is hard due to isolation.
B. Digital certificates secure the session, and the data is sent at random intervals.
C. Traffic Is tunneled to a specific destination and is inaccessible to others except for the receiver.
D. The communication is encrypted and the data in transit is secured.
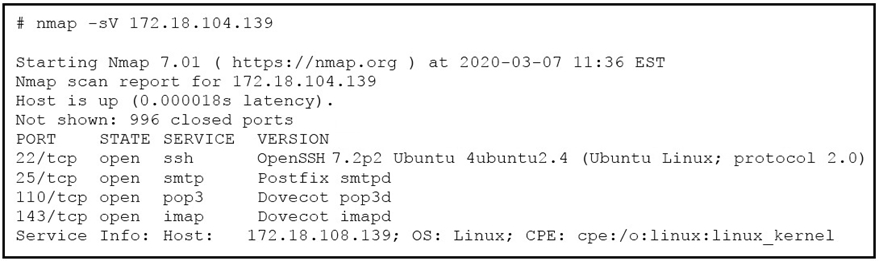
Refer to the exhibit. What does the output indicate about the server with the IP address 172.18.104.139?A. open ports of a web server
B. open port of an FTP server
C. open ports of an email server
D. running processes of the server
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?A. forgery attack
B. plaintext-only attack
C. ciphertext-only attack
D. meet-in-the-middle attack
Refer to the exhibit. What is depicted in the exhibit?A. Windows Event logs
B. Apache logs
C. IIS logs
D. UNIX-based syslog
What are the two characteristics of the full packet captures? (Choose two.)A. Identifying network loops and collision domains.
B. Troubleshooting the cause of security and performance issues.
C. Reassembling fragmented traffic from raw data.
D. Detecting common hardware faults and identify faulty assets.
E. Providing a historical record of a network transaction.
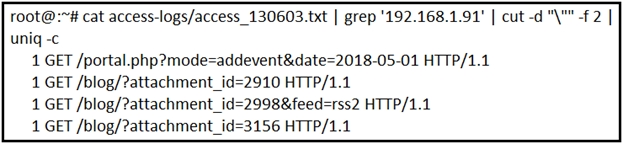
Which event artifact is used to identify HTTP GET requests for a specific file?A. destination IP address
B. TCP ACK
C. HTTP status code
D. URI
An engineer needs to configure network systems to detect command and control communications by decrypting ingress and egress perimeter traffic and allowing network security devices to detect malicious outbound communications Which technology should be used to accomplish the task?A. static IP addresses
B. cipher suite
C. digital certificates
D. signatures
Which type of data consists of connection level, application-specific records generated from network traffic?A. transaction data
B. location data
C. statistical data
D. alert data
What specific type of analysis is assigning values to the scenario to see expected outcomes?A. deterministic
B. exploratory
C. probabilistic
D. descriptive
Which type of access control depends on the job function of the user?A. role-based access control
B. rule-based access control
C. nondiscretionary access control
D. discretionary access control
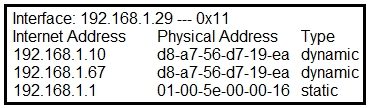
Refer to the exhibit. What is occurring in this network?A. ARP cache poisoning
B. DNS cache poisoning
C. MAC address table overflow
D. MAC flooding attack
What makes HTTPS traffic difficult to monitor?A. SSL interception
B. packet header size
C. signature detection time
D. encryption
Which action prevents buffer overflow attacks?A. variable randomization
B. using web based applications
C. input validation
D. using a Linux operating system
Which type of verification consists of using tools to compute the message digest of the original and copied data, then comparing the similarity of the digests?A. evidence collection order
B. volatile data collection
C. data integrity
D. data preservation
Which technology on a host is used to isolate a running application from other application?A. application allow list
B. application block list
C. host-based firewall
D. sandbox
An engineer must investigate suspicious connections. Data has been gathered using a tcpdump command on a Linux device and saved as sandboxmalware2022-12-22.pcaps file. The engineer is trying to open the tcpdump in the Wireshark tool. What is the expected result?A. The file is opened.
B. The tool does not support Linux.
C. The file does not support the “-“ character.
D. The file has an incorrect extension.
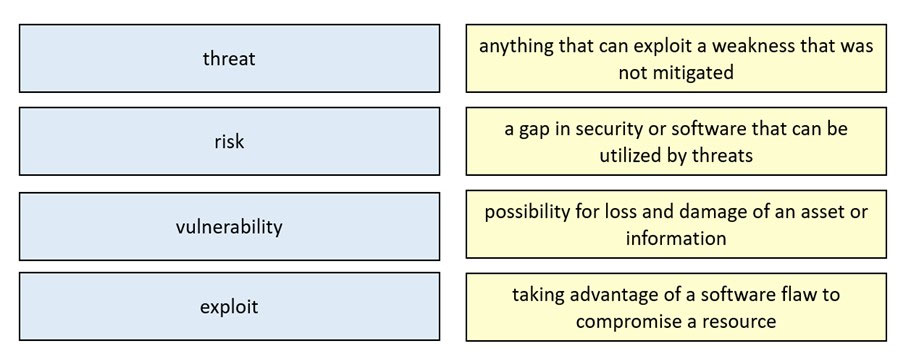
DRAG DROP -
Drag and drop the security concept from the left onto the example of that concept on the right.
Select and Place:
What is a difference between data obtained from Tap and SPAN ports?A. SPAN passively splits traffic between a network device and the network without altering it, while Tap alters response times.
B. Tap mirrors existing traffic from specified ports, while SPAN presents more structured data for deeper analysis.
C. SPAN improves the detection of media errors, while Tap provides direct access to traffic with lowered data visibility.
D. Tap sends traffic from physical layers to the monitoring device, while SPAN provides a copy of network traffic from switch to destination.
In a SOC environment, what is a vulnerability management metric?A. code signing enforcement
B. full assets scan
C. internet exposed devices
D. single factor authentication
Refer to the exhibit. Which technology generates this log?A. NetFlow
B. IDS
C. web proxy
D. firewall
Refer to the exhibit. What does this Cuckoo sandbox report indicate?A. The file is ransomware.
B. The file is spyware.
C. The file will open unsecure ports when executed.
D. The file will open a command interpreter when executed.
The SOC team has confirmed a potential indicator of compromise on an endpoint. The team has narrowed the executable file's type to a new trojan family.
According to the NIST Computer Security Incident Handling Guide, what is the next step in handling this event?A. Perform forensics analysis on the infected endpoint
B. Isolate the infected endpoint from the network
C. Prioritize incident handling based on the impact
D. Collect public information on the malware behavior
An engineer is investigating a case of the unauthorized usage of the `Tcpdump` tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface. What type of information did the malicious insider attempt to obtain?A. tagged protocols being used on the network
B. all firewall alerts and resulting mitigations
C. tagged ports being used on the network
D. all information and data within the datagram
An organization is cooperating with several third-party companies. Data exchange is on an unsecured channel using port 80. Internal employees use the FTP service to upload and download sensitive data. An engineer must ensure confidentiality while preserving the integrity of the communication. Which technology must the engineer implement in this scenario?A. RADIUS server
B. web application firewall
C. X.509 certificates
D. CA server
What describes the impact of false-positive alerts compared to false-negative alerts?A. A false negative is alerting for an XSS attack. An engineer investigates the alert and discovers that an XSS attack happened. A false positive is when an XSS attack happens and no alert is raised.
B. A false positive is an event altering for an SQL injection attack. An engineer investigates the alert and discovers that an attack attempt was blocked by IPS. A false negative is when the attack gets detected but succeeds and results in a breach.
C. A false positive is an event altering for a brute-force attack. An engineer investigates the alert and discovers that a legitimate user entered the wrong credential several times. A false negative is when a threat actor tries to brute-force attack a system and no alert is raised.
D. A false negative is a legitimate attack triggering a brute-force alert. An engineer investigates the alert and finds out someone intended to break into the system. A false positive is when no alert and no attack is occurring.
A user received a targeted spear-phishing email and identified it as suspicious before opening the content. To which category of the Cyber Kill Chain model does to this type of event belong?A. exploitation
B. weaponization
C. reconnaissance
D. delivery
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?A. MAC is controlled by the discretion of the owner and DAC is controlled by an administrator
B. MAC is the strictest of all levels of control and DAC is object-based access
C. DAC is controlled by the operating system and MAC is controlled by an administrator
D. DAC is the strictest of all levels of control and MAC is object-based access
What are two types of cross site scripting attacks? (Choose two.)A. directed
B. encoded
C. reflected
D. stored
E. cascaded
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?A. least privilege
B. need to know
C. integrity validation
D. due diligence
Which security technology allows only a set of pre-approved applications to run on a system?A. application-level blacklisting
B. host-based IPS
C. application-level whitelisting
D. antivirus
An organization that develops high-end technology is going through an internal audit. The organization uses two databases. The main database stores patent information and a secondary database stores employee names and contact information. A compliance team is asked to analyze the infrastructure and identify protected data. Which two types of protected data should be identified? (Choose two.)A. Payment Card Industry (PCI)
B. Sarbanes-Oxley (SOX)
C. Intellectual Property (IP)
D. Protected Health Information (PHI)
E. Personally Identifiable Information (PII)
Refer to the exhibit. Which attack is being attempted against a web application?A. command injection
B. man-in-the-middle
C. denial of service
D. SQL injection
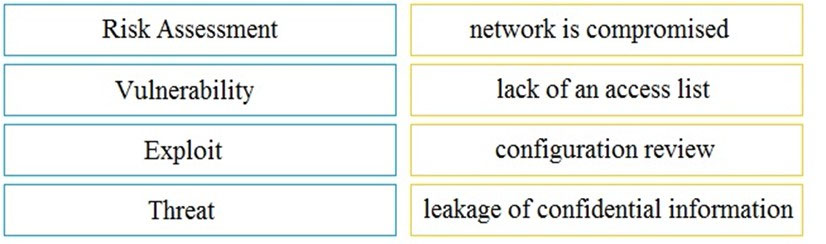
DRAG DROP -
Drag and drop the security concept on the left onto the example of that concept on the right.
Select and Place:
Refer to the exhibit. An analyst received this alert from the Cisco ASA device, and numerous activity logs were produced. How should this type of evidence be categorized?A. indirect
B. circumstantial
C. corroborative
D. best
What is email greylisting by the mail transfer agent?A. denying any email from a sender it does not recognize
B. returning emails that are potential phishing attempts
C. allowing emails from unknown senders temporarily
D. quarantining emails sent from outside of the organization
DRAG DROP
-
Cisco’s Zero Trust Architecture simplifies the Zero Trust journey into three critical areas. Drag the definitions onto the graphic to describe Zero Trust from the Cisco perspective

How does an attacker observe network traffic exchanged between two users?A. port scanning
B. man-in-the-middle
C. command injection
D. denial of service
What is the practice of giving an employee access to only the resources needed to accomplish their job?A. principle of least privilege
B. organizational separation
C. separation of duties
D. need to know principle
What is the functionality of an IDS?A. forensic tool used to perform an in-depth analysis and debugging
B. software or device which monitors and identifies malicious network activity
C. device or software that detects and blocks suspicious files
D. endpoint protection software that prevents viruses and malware
An engineer discovered a breach, identified the threat's entry point, and removed access. The engineer was able to identify the host, the IP address of the threat actor, and the application the threat actor targeted. What is the next step the engineer should take according to the NIST SP 800-61 Incident handling guide?A. Recover from the threat.
B. Analyze the threat.
C. Identify lessons learned from the threat.
D. Reduce the probability of similar threats.
An engineer is addressing a connectivity issue between two servers where the remote server is unable to establish a successful session. Initial checks show that the remote server is not receiving a SYN-ACK while establishing a session by sending the first SYN. What is causing this issue?A. incorrect TCP handshake
B. incorrect UDP handshake
C. incorrect OSI configuration
D. incorrect snaplen configuration
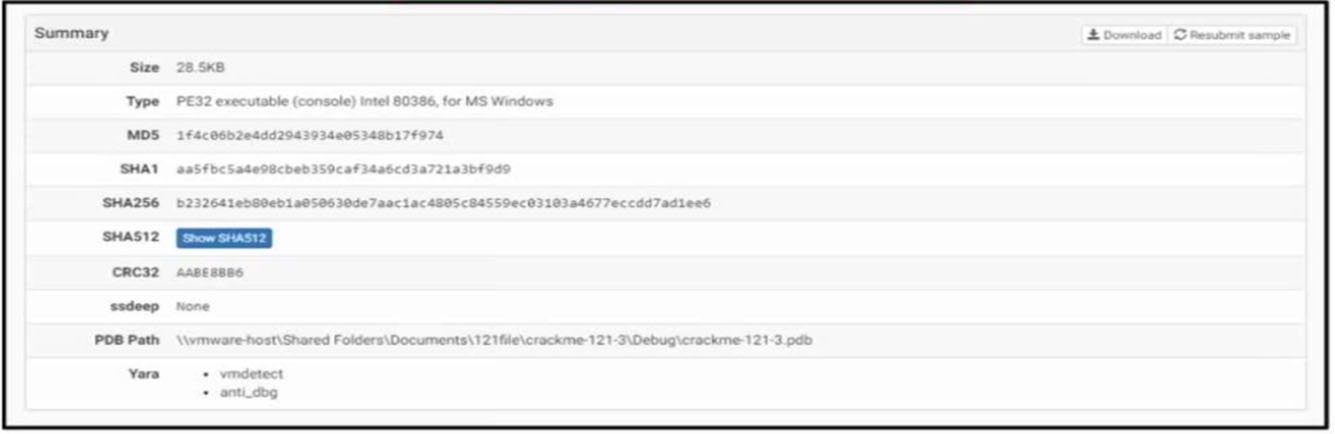
Refer to the exhibit. An engineer is reviewing a Cuckoo report of a file. What must the engineer interpret from the report?A. The file will monitor user activity and send the information to an outside source.
B. The file will Insert itself into an application and execute when the application is run.
C. The file will appear legitimate by evading signature-based detection.
D. The file will not execute its behavior in a sandbox environment to avoid detection.
Free Access Full 200-201 Practice Test Free Questions
If you're looking for more 200-201 practice test free questions, click here to access the full 200-201 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 200-201 certification journey!