200-201 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 200-201 certification exam? Kickstart your success with our 200-201 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 200-201 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 200-201 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
What is the impact of encryption on data visibility?
A. TLS 1.3 traffic cannot be decrypted and monitored.
B. Traffic decryption causes high CPU load on monitoring systems.
C. Traffic decryption is needed for deep inspection of SSL traffic via NGFW.
D. IPsec encryption of traffic is vulnerable to man-in-the-middle attacks.
Refer to exhibit. An analyst performs the analysis of the pcap file to detect the suspicious activity. What challenges did the analyst face in terms of data visibility?
A. data encapsulation
B. code obfuscation
C. data encryption
D. IP fragmentation
An engineer is investigating a case of the unauthorized usage of the `Tcpdump` tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface. What type of information did the malicious insider attempt to obtain?
A. tagged protocols being used on the network
B. all firewall alerts and resulting mitigations
C. tagged ports being used on the network
D. all information and data within the datagram
Which system monitors local system operation and local network access for violations of a security policy?
A. host-based data loss prevention
B. host-based intrusion detection
C. antivirus
D. sandbox
Which of these describes volatile evidence?
A. logs
B. registers and cache
C. disk and removable drives
D. usernames
Which two components reduce the attack surface on an endpoint? (Choose two.)
A. secure boot
B. load balancing
C. increased audit log levels
D. restricting USB ports
E. full packet captures at the endpoint
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
A. Firepower
B. Email Security Appliance
C. Web Security Appliance
D. Stealthwatch
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
A. The RST flag confirms the beginning of the TCP connection, and the ACK flag responds when the data for the payload is complete
B. The ACK flag confirms the beginning of the TCP connection, and the RST flag responds when the data for the payload is complete
C. The RST flag confirms the receipt of the prior segment, and the ACK flag allows for the spontaneous termination of a connection
D. The ACK flag confirms the receipt of the prior segment, and the RST flag allows for the spontaneous termination of a connection
An investigator is examining a copy of an ISO file that is stored in CDFS format. What type of evidence is this file?
A. data from a CD copied using Mac-based system
B. data from a CD copied using Linux system
C. data from a DVD copied using Windows system
D. data from a CD copied using Windows
A user received a malicious email attachment named "DS045-report1122345.exe" and executed it. In which step of the Cyber Kill Chain is this event?
A. reconnaissance
B. delivery
C. weaponization
D. installation
An engineer configured regular expression ".*.([Dd][Oo][Cc]|[Xx][LI][Ss]|[Pp][Pp][Tt]) HTTP/1.[01]" on Cisco ASA firewall. What does this regular expression do?
A. It captures .doc, .xls, and .pdf files in HTTP v1.0 and v1.1.
B. It captures documents in an HTTP network session.
C. It captures Word, Excel, and PowerPoint files in HTTP v1.0 and v1.1.
D. It captures .doc, .xls, and .ppt files extensions in HTTP v1.0.
Which evasion method involves performing actions slower than normal to prevent detection?
A. timing attack
B. traffic fragmentation
C. resource exhaustion
D. tunneling
What are two social engineering techniques? (Choose two.)
A. privilege escalation
B. DDoS attack
C. phishing
D. man-in-the-middle
E. pharming
A user received an email attachment named `Hr402-report3662-empl621.exe` but did not run it. Which category of the cyber kill chain should be assigned to this type of event?
A. delivery
B. reconnaissance
C. weaponization
D. installation
Refer to the exhibit. Which component is identifiable in this exhibit?
A. Windows Registry hive
B. Trusted Root Certificate store on the local machine
C. Windows PowerShell verb
D. local service in the Windows Services Manager
Which category relates to improper use or disclosure of PII data?
A. legal
B. compliance
C. regulated
D. contractual
Which technique is a low-bandwidth attack?
A. evasion
B. phishing
C. session hijacking
D. social engineering
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
A. The computer has a HIPS installed on it.
B. The computer has a NIPS installed on it.
C. The computer has a HIDS installed on it.
D. The computer has a NIDS installed on it.
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group. What is the initial event called in the NIST SP800-61?
A. online assault
B. precursor
C. trigger
D. instigator
What is the difference between a threat and an exploit?
A. An exploit is an attack path, and a threat represents a potential vulnerability.
B. An exploit is an attack vector, and a threat is a potential path the attack must go through.
C. A threat is a potential attack on an asset, and an exploit takes advantage of the vulnerability of the asset.
D. A threat is a result of utilizing flow in a system, and an exploit is a result of gaining control over the system.
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
A. context
B. session
C. laptop
D. firewall logs
E. threat actor
What is the functionality of an IDS?
A. forensic tool used to perform an in-depth analysis and debugging
B. software or device which monitors and identifies malicious network activity
C. device or software that detects and blocks suspicious files
D. endpoint protection software that prevents viruses and malware
How does an attack surface differ from an attack vector?
A. An attack vector recognizes the potential outcomes of an attack, and the attack surface is choosing a method of an attack.
B. An attack vector matches components that can be exploited, and an attack surface classifies the potential path for exploitation.
C. An attack surface mitigates external vulnerabilities, and an attack vector identifies mitigation techniques and possible workarounds.
D. An attack surface identifies vulnerable parts for an attack, and an attack vector specifies which attacks are feasible to those parts.
Refer to the exhibit. An attacker scanned the server using Nmap. What did the attacker obtain from this scan?
A. Identified a firewall device preventing the port state from being returned.
B. Identified open SMB ports on the server.
C. Gathered information on processes running on the server.
D. Gathered a list of Active Directory users.
Which technology on a host is used to isolate a running application from other application?
A. application allow list
B. application block list
C. host-based firewall
D. sandbox
An engineer needs to discover alive hosts within the 192.168.1.0/24 range without triggering intrusive portscan alerts on the IDS device using Nmap. Which command will accomplish this goal?
A. nmap –top-ports 192.168.1.0/24
B. nmap ג€”sP 192.168.1.0/24
C. nmap -sL 192.168.1.0/24
D. nmap -sV 192.168.1.0/24
What is the impact of false positive alerts on business compared to true positive?
A. True positives affect security as no alarm is raised when an attack has taken place, while false positives are alerts raised appropriately to detect and further mitigate them.
B. True-positive alerts are blocked by mistake as potential attacks, while False-positives are actual attacks identified as harmless.
C. False positives alerts are manually ignored signatures to avoid warnings that are already acknowledged, while true positives are warnings that are not yet acknowledged.
D. False-positive alerts are detected by confusion as potential attacks, while true positives are attack attempts identified appropriately.
What is a description of "phishing" as a social engineering attack?
A. Fake Social Security Administration personnel contact random individuals, inform them that there has been a computer problem on their end, and ask that those individuals confirm their Social Security Number, all for the purpose of committing identity theft.
B. A hacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message. The recipient is then tricked into clicking a malicious link.
C. The attacker focuses on creating a good pretext, or a fabricated scenario, that is used to try and steal victims’ personal information.
D. Someone without the proper authentication follows an authenticated employee into a restricted area. The attacker might impersonate a delivery driver and wait outside a building to get things started.
What is an incident response plan?
A. an organizational approach to events that could lead to asset loss or disruption of operations
B. an organizational approach to security management to ensure a service lifecycle and continuous improvements
C. an organizational approach to disaster recovery and timely restoration of operational services
D. an organizational approach to system backup and data archiving aligned to regulations
An engineer received a flood of phishing emails from HR with the source address HRjacobrn@company.com . What is the threat actor in this scenario?
A. sender
B. phishing email
C. receiver
D. HR
What causes events on a Windows system to show Event Code 4625 in the log messages?
A. The system detected an XSS attack
B. Someone is trying a brute force attack on the network
C. Another device is gaining root access to the system
D. A privileged user successfully logged into the system
Refer to the exhibit. Which kind of attack method is depicted in this string?
A. cross-site scripting
B. man-in-the-middle
C. SQL injection
D. denial of service
An organization's security team has detected network spikes coming from the internal network. An investigation has concluded that the spike in traffic was from intensive network scanning. How should the analyst collect the traffic to isolate the suspicious host?
A. based on the most used applications
B. by most active source IP
C. by most used ports
D. based on the protocols used
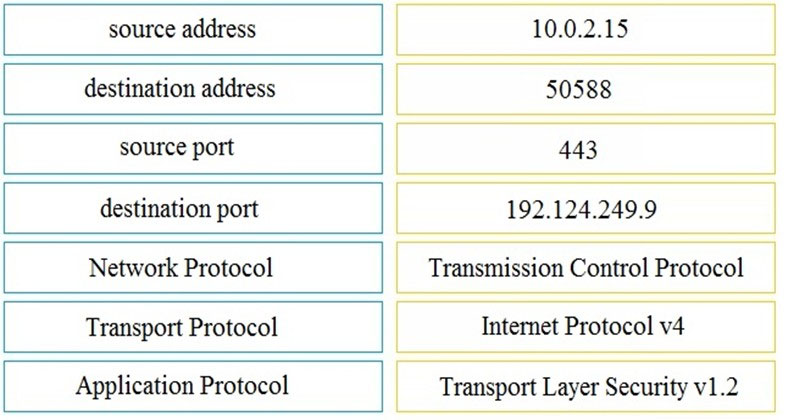
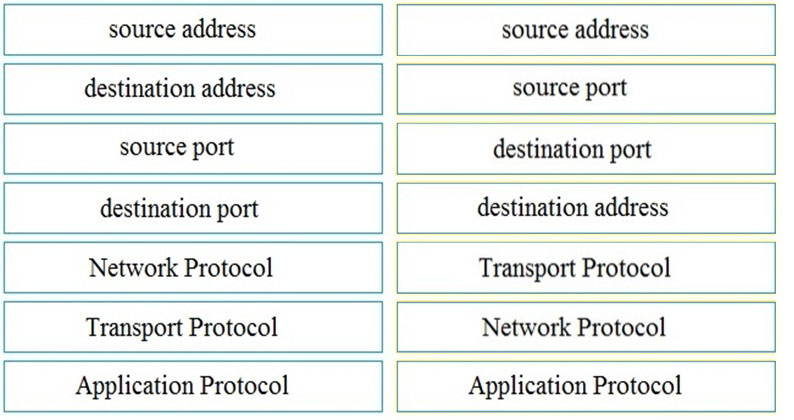
DRAG DROP -Refer to the exhibit. Drag and drop the element name from the left onto the appropriate piece of the PCAP file on the right. Select and Place:
Refer to the exhibit. What does this Cuckoo sandbox report indicate?
A. The file is ransomware.
B. The file is spyware.
C. The file will open unsecure ports when executed.
D. The file will open a command interpreter when executed.
A company's cyber security team performed a phishing simulation campaign for employees and performed security awareness trainings to affected personal. According to NIST.SP800-61, at which phase of incident response is this action?
A. post-incident activity phase
B. detection and analyze phase
C. preparation phase
D. eradication and recovery phase
Which tool gives the ability to see session data in real time?
A. tcpdstat
B. trafdump
C. trafshow
D. tcptrace
An analyst is using the SIEM platform and must extract a custom property from a Cisco device and capture the phrase, `File: Clean.` Which regex must the analyst import?
A. File: Clean (.*)
B. ^Parent File: Clean$
C. File: Clean
D. ^File: Clean$
Why is HTTPS traffic difficult to screen?
A. HTTPS is used internally and screening traffic for external parties is hard due to isolation.
B. Digital certificates secure the session, and the data is sent at random intervals.
C. Traffic Is tunneled to a specific destination and is inaccessible to others except for the receiver.
D. The communication is encrypted and the data in transit is secured.
What is the difference between an attack vector and an attack surface?
A. An attack surface identifies vulnerabilities that require user input or validation; and an attack vector identifies vulnerabilities that are independent of user actions.
B. An attack vector identifies components that can be exploited; and an attack surface identifies the potential path an attack can take to penetrate the network.
C. An attack surface recognizes which network parts are vulnerable to an attack; and an attack vector identifies which attacks are possible with these vulnerabilities.
D. An attack vector identifies the potential outcomes of an attack; and an attack surface launches an attack using several methods against the identified vulnerabilities.
In a SOC environment, what is a vulnerability management metric?
A. code signing enforcement
B. full assets scan
C. internet exposed devices
D. single factor authentication
What is session data used for in network security?
A. It contains the set of parameters used for fetching logs.
B. It tracks cookies within each session initiated from user.
C. It is the transaction log between monitoring software.
D. It is the summary of the transmission between two network devices.
What is the difference between inline traffic interrogation and traffic mirroring?
A. Inline replicates the traffic to preserve integrity rather than modifying packets before sending them to other analysis tools.
B. Traffic mirroring results in faster traffic analysis and inline is considerably slower due to latency.
C. Inline interrogation is less complex as traffic mirroring applies additional tags to data.
D. Traffic mirroring copies the traffic rather than forwarding it directly to the analysis tools.
A security analyst notices a sudden surge of incoming traffic and detects unknown packets from unknown senders. After further investigation, the analyst learns that customers claim that they cannot access company servers. According to NIST SP800-61, in which phase of the incident response process is the analyst?
A. preparation
B. post-incident activity
C. containment, eradication, and recovery
D. detection and analysis
According to the NIST SP 800-86, which two types of data are considered volatile? (Choose two.)
A. temporary files
B. login sessions
C. swap files
D. dump files
E. free space
An employee reports that someone has logged into their system and made unapproved changes, files are out of order, and several documents have been placed in the recycle bin. The security specialist reviewed the system logs, found nothing suspicious, and was not able to determine what occurred. The software is up to date; there are no alerts from antivirus and no failed login attempts. What is causing the lack of data visibility needed to detect the attack?
A. The threat actor used a dictionary-based password attack to obtain credentials.
B. The threat actor gained access to the system by known credentials.
C. The threat actor used the teardrop technique to confuse and crash login services.
D. The threat actor used an unknown vulnerability of the operating system that went undetected.
Refer to the exhibit. A network administrator is investigating suspicious network activity by analyzing captured traffic. An engineer notices abnormal behavior and discovers that the default user agent is present in the headers of requests and data being transmitted. What is occurring?
A. indicators of denial-of-service attack: due to the frequency of requests
B. indicators of data exfiltration: HTTP requests must be plain text
C. cache bypassing attack: attacker is sending requests for noncacheable content
D. garbage flood attack: attacker is sending garbage binary data to open ports
Refer to the exhibit. Which frame numbers contain a file that is extractable via TCP stream within Wireshark?
A. 7 to 21
B. 7 and 21
C. 7, 14, and 21
D. 14, 16, 18, and 19
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
A. management and reporting
B. traffic filtering
C. adaptive AVC
D. metrics collection and exporting
E. application recognition
What is a difference between signature-based and behavior-based detection?
A. Signature-based identifies behaviors that may be linked to attacks, while behavior-based has a predefined set of rules to match before an alert.
B. Behavior-based identifies behaviors that may be linked to attacks, while signature-based has a predefined set of rules to match before an alert.
C. Behavior-based uses a known vulnerability database, while signature-based intelligently summarizes existing data.
D. Signature-based uses a known vulnerability database, while behavior-based intelligently summarizes existing data.
Free Access Full 200-201 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 200-201 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 200-201 certification journey!