200-201 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the 200-201 certification? Take your preparation to the next level with our 200-201 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a 200-201 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic 200-201 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
What is the difference between deep packet inspection and stateful inspection?
A. Stateful inspection is more secure due to its complex signatures, and deep packet inspection requires less human intervention.
B. Deep packet inspection is more secure due to its complex signatures, and stateful inspection requires less human intervention.
C. Deep packet inspection gives insights up to Layer 7, and stateful inspection gives insights only up to Layer 4.
D. Stateful inspection verifies data at the transport layer, and deep packet inspection verifies data at the application layer.
Refer to the exhibit. A company's user HTTP connection to a malicious site was blocked according to configured policy. What is the source technology used for this measure?
A. network application control
B. firewall
C. IPS
D. web proxy
Refer to the exhibit. An engineer received a ticket to analyze unusual network traffic. What is occurring?
A. data exfiltration
B. regular network traffic; no suspicious activity
C. denial-of-service attack
D. cookie poisoning
How does an attacker observe network traffic exchanged between two users?
A. port scanning
B. man-in-the-middle
C. command injection
D. denial of service
Which filter allows an engineer to filter traffic in Wireshark to further analyze the PCAP file by only showing the traffic for LAN 10.11.x.x, between workstations and servers without the Internet?
A. src=10.11.0.0/16 and dst=10.11.0.0/16
B. ip.src==10.11.0.0/16 and ip.dst==10.11.0.0/16
C. ip.src=10.11.0.0/16 and ip.dst=10.11.0.0/16
D. src==10.11.0.0/16 and dst==10.11.0.0/16
Refer to the exhibit. A workstation downloads a malicious .docx file from the Internet and a copy is sent to FTDv. The FTDv sends the file hash to FMC and the file event is recorded. What would have occurred with stronger data visibility?
A. An extra level of security would have been in place.
B. Malicious traffic would have been blocked on multiple devices.
C. The traffic would have been monitored at any segment in the network.
D. Detailed information about the data in real time would have been provided.
A SOC analyst observed Ursnif malware at the SIEM dashboard. The analyst opened the PCAP file to search the certificate issue data. Where must the analyst navigate?
A. under the rdnSequence line
B. under the validity line
C. under the subject
D. under the signed certificate
What is an attack surface as compared to a vulnerability?
A. any potential danger to an asset
B. the sum of all paths for data into and out of the environment
C. an exploitable weakness in a system or its design
D. the individuals who perform an attack
An analyst received a ticket regarding a degraded processing capability for one of the HR department's servers. On the same day an engineer noticed a disabled antivirus software and was not able to determine when or why it occurred. According to the NIST Incident Handling Guide, what is the next phase of this investigation?
A. Analysis
B. Eradication
C. Detection
D. Recovery
Which two protocols are used for DDoS amplification attacks? (Choose two.)
A. HTTP
B. DNS
C. TCP
D. ICMPv6
E. NTP
A user received a targeted spear-phishing email and identified it as suspicious before opening the content. To which category of the Cyber Kill Chain model does to this type of event belong?
A. exploitation
B. weaponization
C. reconnaissance
D. delivery
What does an attacker use to determine which network ports are listening on a potential target device?
A. man-in-the-middle
B. port scanning
C. SQL injection
D. ping sweep
Which two components reduce the attack surface on an endpoint? (Choose two.)
A. secure boot
B. load balancing
C. increased audit log levels
D. restricting USB ports
E. full packet captures at the endpoint
Which principle is being followed when an analyst gathers information relevant to a security incident to determine the appropriate course of action?
A. decision making
B. rapid response
C. data mining
D. due diligence
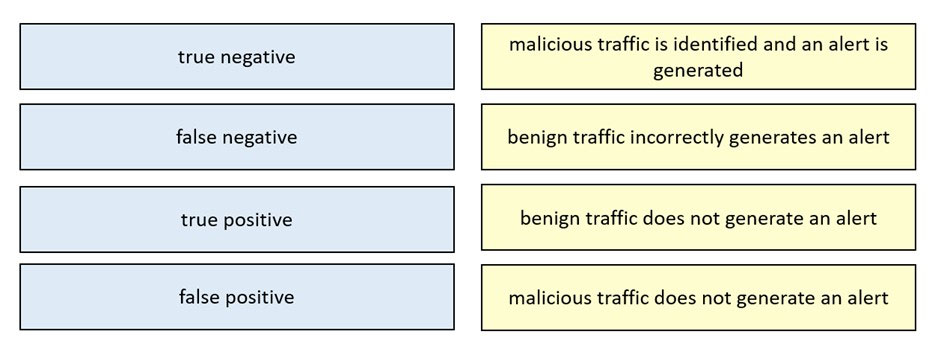
Which signature impacts network traffic by causing legitimate traffic to be blocked?
A. false negative
B. true positive
C. true negative
D. false positive
Which attack represents the evasion technique of resource exhaustion?
A. SQL injection
B. bluesnarfing
C. denial-of-service
D. man-in-the-middle
What is the function of a command and control server?
A. It enumerates open ports on a network device
B. It drops secondary payload into malware
C. It is used to regain control of the network after a compromise
D. It sends instruction to a compromised system
Which option describes indicators of attack?
A. blocked phishing attempt on a company
B. spam emails on an employee workstation
C. virus detection by the AV software
D. malware reinfection within a few minutes of removal
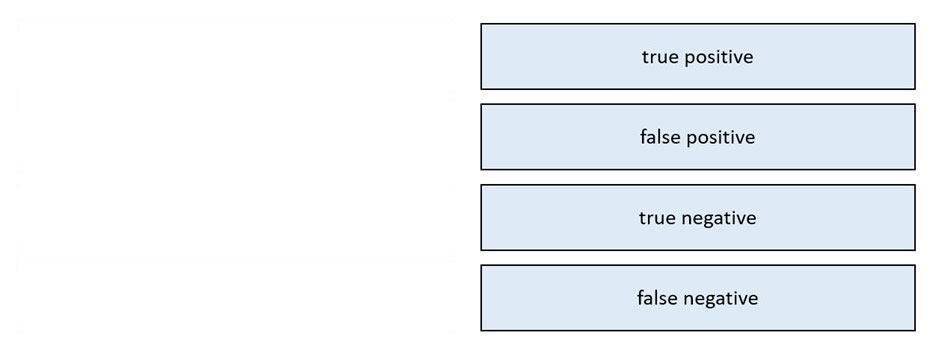
DRAG DROP - Drag and drop the event term from the left onto the description on the right. Select and Place:
According to the NIST SP 800-86, which two types of data are considered volatile? (Choose two.)
A. temporary files
B. login sessions
C. swap files
D. dump files
E. free space
Which regular expression is needed to capture the IP address 192.168.20.232?
A. ^(?:[0-9]{1,3}.){3}[0-9]{1,3}
B. ^(?:[0-9]{1,3}.)*
C. ^)?:[0-9]{1,3}.){1,4}
D. ^([0-9].{3})
An engineer must investigate suspicious connections. Data has been gathered using a tcpdump command on a Linux device and saved as sandboxmalware2022-12-22.pcaps file. The engineer is trying to open the tcpdump in the Wireshark tool. What is the expected result?
A. The file is opened.
B. The tool does not support Linux.
C. The file does not support the “-“ character.
D. The file has an incorrect extension.
A cyberattacker notices a security flaw in a software that a company is using. They decide to tailor a specific worm to exploit this flaw and extract saved passwords from the software. To which category of the Cyber Kill Chain model does this event belong?
A. weaponization
B. reconnaissance
C. delivery
D. exploitation
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
A. The computer has a HIPS installed on it.
B. The computer has a NIPS installed on it.
C. The computer has a HIDS installed on it.
D. The computer has a NIDS installed on it.
Which technology should be used to implement a solution that makes routing decisions based on HTTP header, uniform resource identifier, and SSL session ID attributes?
A. AWS
B. IIS
C. Load balancer
D. Proxy server
What is the difference between vulnerability and risk?
A. A vulnerability represents a flaw in a security that can be exploited, and the risk is the potential damage it might cause.
B. A risk is potential threat that adversaries use to infiltrate the network, and a vulnerability is an exploit.
C. A risk is a potential threat that an exploit applies to, and a vulnerability represents the threat itself.
D. A vulnerability is a sum of possible malicious entry points, and a risk represents the possibility of the unauthorized entry itself.
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
A. The RST flag confirms the beginning of the TCP connection, and the ACK flag responds when the data for the payload is complete
B. The ACK flag confirms the beginning of the TCP connection, and the RST flag responds when the data for the payload is complete
C. The RST flag confirms the receipt of the prior segment, and the ACK flag allows for the spontaneous termination of a connection
D. The ACK flag confirms the receipt of the prior segment, and the RST flag allows for the spontaneous termination of a connection
What is a sandbox interprocess communication service?
A. A collection of rules within the sandbox that prevent the communication between sandboxes.
B. A collection of network services that are activated on an interface, allowing for inter-port communication.
C. A collection of interfaces that allow for coordination of activities among processes.
D. A collection of host services that allow for communication between sandboxes.
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?
A. Hypertext Transfer Protocol
B. SSL Certificate
C. Tunneling
D. VPN
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
A. application identification number
B. active process identification number
C. runtime identification number
D. process identification number
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?
A. integrity
B. confidentiality
C. availability
D. scope
What is obtained using NetFlow?
A. full packet capture
B. session data
C. application logs
D. network downtime report
Which type of data collection requires the largest amount of storage space?
A. alert data
B. transaction data
C. session data
D. full packet capture
Refer to the exhibit. An analyst was given a PCAP file, which is associated with a recent intrusion event in the company FTP server. Which display filters should the analyst use to filter the FTP traffic?
A. dst.port = 21
B. tcp.port == 21
C. dstport == FTP
D. tcpport = FTP
Which security monitoring data type requires the largest storage space?
A. transaction data
B. statistical data
C. session data
D. full packet capture
An engineer runs a suspicious file in a sandbox analysis tool to see the outcome. The analysis report shows that outbound callouts were made post infection. Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
A. signatures
B. host IP addresses
C. file size
D. dropped files
E. domain names
What are two denial of service attacks? (Choose two.)
A. MITM
B. TCP connections
C. ping of death
D. UDP flooding
E. code red
What is an example of social engineering attacks?
A. receiving an unexpected email from an unknown person with an attachment from someone in the same company
B. receiving an email from human resources requesting a visit to their secure website to update contact information
C. sending a verbal request to an administrator who knows how to change an account password
D. receiving an invitation to the department’s weekly WebEx meeting
Which attack method is being used when an attacker tries to compromise a network with an authentication system that uses only 4-digit numeric passwords and no username?
A. replay
B. SQL injection
C. dictionary
D. cross-site scripting
How is attacking a vulnerability categorized?
A. action on objectives
B. delivery
C. exploitation
D. installation
What describes the impact of false-positive alerts compared to false-negative alerts?
A. A false negative is alerting for an XSS attack. An engineer investigates the alert and discovers that an XSS attack happened. A false positive is when an XSS attack happens and no alert is raised.
B. A false positive is an event altering for an SQL injection attack. An engineer investigates the alert and discovers that an attack attempt was blocked by IPS. A false negative is when the attack gets detected but succeeds and results in a breach.
C. A false positive is an event altering for a brute-force attack. An engineer investigates the alert and discovers that a legitimate user entered the wrong credential several times. A false negative is when a threat actor tries to brute-force attack a system and no alert is raised.
D. A false negative is a legitimate attack triggering a brute-force alert. An engineer investigates the alert and finds out someone intended to break into the system. A false positive is when no alert and no attack is occurring.
What is a difference between SIEM and SOAR?
A. SIEM predicts and prevents security alerts, while SOAR checks attack patterns and applies the mitigation.
B. SIEM’s primary function is to collect and detect anomalies, while SOAR is more focused on security operations automation and response.
C. SOAR’s primary function is to collect and detect anomalies, while SIEM is more focused on security operations automation and response.
D. SOAR predicts and prevents security alerts, while SIEM checks attack patterns and applies the mitigation.
An engineer is working with the compliance teams to identify the data passing through the network. During analysis, the engineer informs the compliance team that external perimeter data flows contain records, writings, and artwork. Internal segregated network flows contain the customer choices by gender, addresses, and product preferences by age? The engineer must identify protected data. Which two types of data must be identified? (Choose two.)
A. SOX
B. PII
C. PCI
D. PHI
E. copyright
How does an SSL certificate impact security between the client and the server?
A. by enabling an authenticated channel between the client and the server
B. by creating an integrated channel between the client and the server
C. by enabling an authorized channel between the client and the server
D. by creating an encrypted channel between the client and the server
What is a difference between signature-based and behavior-based detection?
A. Signature-based identifies behaviors that may be linked to attacks, while behavior-based has a predefined set of rules to match before an alert.
B. Behavior-based identifies behaviors that may be linked to attacks, while signature-based has a predefined set of rules to match before an alert.
C. Behavior-based uses a known vulnerability database, while signature-based intelligently summarizes existing data.
D. Signature-based uses a known vulnerability database, while behavior-based intelligently summarizes existing data.
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
A. ransomware communicating after infection
B. users downloading copyrighted content
C. data exfiltration
D. user circumvention of the firewall
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor. Which type of evidence is this?
A. best evidence
B. prima facie evidence
C. indirect evidence
D. physical evidence
An offline audit log contains the source IP address of a session suspected to have exploited a vulnerability resulting in system compromise. Which kind of evidence is this IP address?
A. best evidence
B. corroborative evidence
C. indirect evidence
D. forensic evidence
Refer to the exhibit. This request was sent to a web application server driven by a database. Which type of web server attack is represented?
A. parameter manipulation
B. heap memory corruption
C. command injection
D. blind SQL injection
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header. Which technology makes this behavior possible?
A. encapsulation
B. TOR
C. tunneling
D. NAT
Free Access Full 200-201 Practice Exam Free
Looking for additional practice? Click here to access a full set of 200-201 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your 200-201 certification journey!