200-201 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 200-201 certification exam? Start your preparation the smart way with our 200-201 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 200-201 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 200-201 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
Refer to the exhibit. A workstation downloads a malicious .docx file from the Internet and a copy is sent to FTDv. The FTDv sends the file hash to FMC and the file event is recorded. What would have occurred with stronger data visibility?
A. An extra level of security would have been in place.
B. Malicious traffic would have been blocked on multiple devices.
C. The traffic would have been monitored at any segment in the network.
D. Detailed information about the data in real time would have been provided.
What makes HTTPS traffic difficult to monitor?
A. SSL interception
B. packet header size
C. signature detection time
D. encryption
What is a description of "phishing" as a social engineering attack?
A. Fake Social Security Administration personnel contact random individuals, inform them that there has been a computer problem on their end, and ask that those individuals confirm their Social Security Number, all for the purpose of committing identity theft.
B. A hacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message. The recipient is then tricked into clicking a malicious link.
C. The attacker focuses on creating a good pretext, or a fabricated scenario, that is used to try and steal victims’ personal information.
D. Someone without the proper authentication follows an authenticated employee into a restricted area. The attacker might impersonate a delivery driver and wait outside a building to get things started.
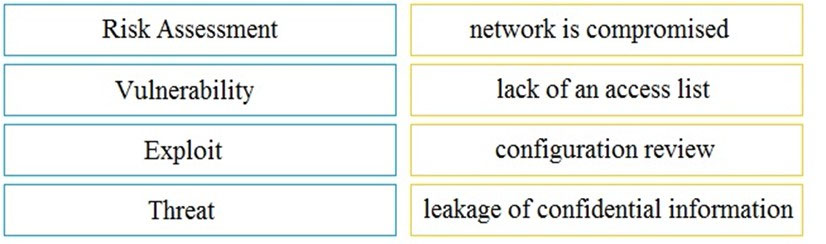
What is the difference between vulnerability and risk?
A. A vulnerability represents a flaw in a security that can be exploited, and the risk is the potential damage it might cause.
B. A risk is potential threat that adversaries use to infiltrate the network, and a vulnerability is an exploit.
C. A risk is a potential threat that an exploit applies to, and a vulnerability represents the threat itself.
D. A vulnerability is a sum of possible malicious entry points, and a risk represents the possibility of the unauthorized entry itself.
Refer to the exhibit. An engineer is analyzing a PCAP file after a recent breach. An engineer identified that the attacker used an aggressive ARP scan to scan the hosts and found web and SSH servers. Further analysis showed several SSH Server Banner and Key Exchange Initiations. The engineer cannot see the exact data being transmitted over an encrypted channel and cannot identify how the attacker gained access. How did the attacker gain access?
A. by using an SSH Tectia Server vulnerability to enable host-based authentication
B. by using brute force on the SSH service to gain access
C. by using the buffer overflow in the URL catcher feature for SSH
D. by using an SSH vulnerability to silently redirect connections to the local host
An engineer received a flood of phishing emails from HR with the source address HRjacobrn@company.com . What is the threat actor in this scenario?
A. sender
B. phishing email
C. receiver
D. HR
An analyst is exploring the functionality of different operating systems. What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
A. queries Linux devices that have Microsoft Services for Linux installed
B. deploys Windows Operating Systems in an automated fashion
C. is an efficient tool for working with Active Directory
D. has a Common Information Model, which describes installed hardware and software
What is the impact of encryption?
A. Data is unaltered and its integrity is preserved.
B. Data is accessible and available to permitted individuals.
C. Confidentiality of the data is kept secure and permissions are validated.
D. Data is secure and unreadable without decrypting it.
Refer to the exhibit. What must be interpreted from this packet capture?
A. IP address 192.168.88.12 is communicating with 192.168.88.149 with a source port 49098 to destination port 80 using TCP protocol.
B. IP address 192.168.88.149 is communicating with 192.168.88.12 with a source port 49098 to destination port 80 using TCP protocol.
C. IP address 192.168.88.149 is communicating with 192.168.88.12 with a source port 80 to destination port 49098 using TCP protocol.
D. IP address 192.168.88.12 is communicating with 192.168.88.149 with a source port 74 to destination port 49098 using TCP protocol.
Which artifact is used to uniquely identify a detected file?
A. file timestamp
B. file extension
C. file size
D. file hash
Refer to the exhibit. Which stakeholders must be involved when a company workstation is compromised?
A. Employee 1, Employee 2, Employee 3, Employee 4, Employee 5, Employee 7
B. Employee 4, Employee 6, Employee 7
C. Employee 1, Employee 2, Employee 4, Employee 5
D. Employee 2, Employee 3, Employee 4, Employee 5
Which action prevents buffer overflow attacks?
A. variable randomization
B. using web based applications
C. input validation
D. using a Linux operating system
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IP phones?
A. known-plaintext
B. replay
C. dictionary
D. man-in-the-middle
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs. Which technology should be used to accomplish this task?
A. application whitelisting/blacklisting
B. network NGFW
C. host-based IDS
D. antivirus/antispyware software
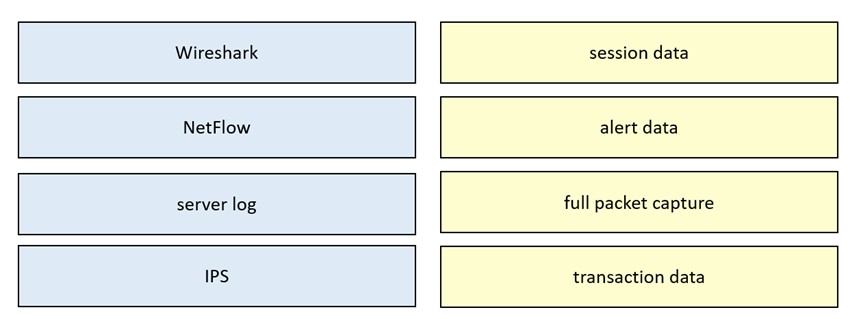
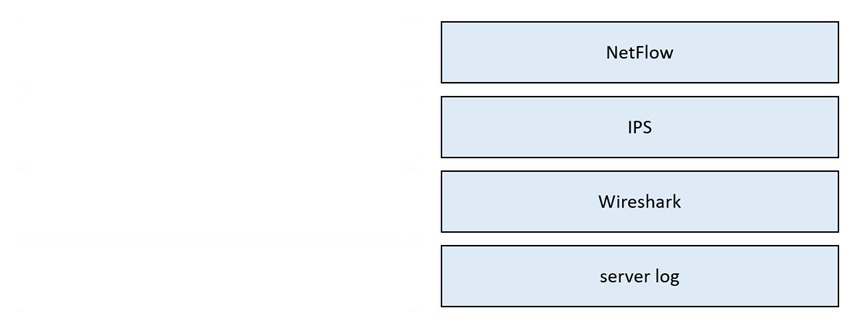
What is session data used for in network security?
A. It contains the set of parameters used for fetching logs.
B. It tracks cookies within each session initiated from user.
C. It is the transaction log between monitoring software.
D. It is the summary of the transmission between two network devices.
Which tool gives the ability to see session data in real time?
A. tcpdstat
B. trafdump
C. trafshow
D. tcptrace
An engineer is investigating a case of the unauthorized usage of the `Tcpdump` tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface. What type of information did the malicious insider attempt to obtain?
A. tagged protocols being used on the network
B. all firewall alerts and resulting mitigations
C. tagged ports being used on the network
D. all information and data within the datagram
Refer to the exhibit. Which kind of attack method is depicted in this string?
A. cross-site scripting
B. man-in-the-middle
C. SQL injection
D. denial of service
According to CVSS, which metric group does user interaction belong to?
A. temporal
B. temporary
C. base
D. environmental
What is the difference between a threat and a risk?
A. Threat represents a potential danger that could take advantage of a weakness, while the risk is the likelihood of a compromise or damage of an asset.
B. Risk represents the known and identified loss or danger in the system, while threat is a non-identified impact of possible risks.
C. Risk is the unintentional possibility of damages or harm to infrastructure, while the threats are certain and intentional.
D. Threat is a state of being exposed to an attack or a compromise, while risk is the calculation of damage or potential loss affecting the organization from an exposure.
Which technology on a host is used to isolate a running application from other application?
A. application allow list
B. application block list
C. host-based firewall
D. sandbox
Refer to the exhibit. Which frame numbers contain a file that is extractable from Wireshark PCAP?
A. Frames No. 20064 and 20066
B. Frame No. 20064
C. Frame No. 20086
D. All Frames from No. 20061 to 20064
What is a difference between SOAR and SIEM?
A. SOAR platforms are used for threat and vulnerability management, but SIEM applications are not
B. SIEM applications are used for threat and vulnerability management, but SOAR platforms are not
C. SOAR receives information from a single platform and delivers it to a SIEM
D. SIEM receives information from a single platform and delivers it to a SOAR
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?
A. MAC is controlled by the discretion of the owner and DAC is controlled by an administrator
B. MAC is the strictest of all levels of control and DAC is object-based access
C. DAC is controlled by the operating system and MAC is controlled by an administrator
D. DAC is the strictest of all levels of control and MAC is object-based access
Which tool provides a full packet capture from network traffic?
A. Nagios
B. CAINE
C. Hydra
D. Wireshark
What does the Zero Trust security model signify?
A. Zero Trust security means that no one is trusted by default from inside or outside the network.
B. Zero Trust addresses access control and states that an individual should have only the minimum access privileges necessary to perform specific tasks.
C. Zero Trust states that no users should be given enough privileges to misuse the system on their own.
D. Zero Trust states that unless a subject is given explicit access to an object, it should be denied access to that object.
An engineer needs to discover alive hosts within the 192.168.1.0/24 range without triggering intrusive portscan alerts on the IDS device using Nmap. Which command will accomplish this goal?
A. nmap –top-ports 192.168.1.0/24
B. nmap ג€”sP 192.168.1.0/24
C. nmap -sL 192.168.1.0/24
D. nmap -sV 192.168.1.0/24
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?
A. NetScout
B. tcpdump
C. SolarWinds
D. netsh
What specific type of analysis is assigning values to the scenario to see expected outcomes?
A. deterministic
B. exploratory
C. probabilistic
D. descriptive
Which attack method is being used when an attacker tries to compromise a network with an authentication system that uses only 4-digit numeric passwords and no username?
A. replay
B. SQL injection
C. dictionary
D. cross-site scripting
What is personally identifiable information that must be safeguarded from unauthorized access?
A. date of birth
B. driver’s license number
C. gender
D. zip code
What are two types of cross site scripting attacks? (Choose two.)
A. directed
B. encoded
C. reflected
D. stored
E. cascaded
The SOC team has confirmed a potential indicator of compromise on an isolated endpoint. The team has narrowed the potential malware type to a new trojan family. According to the NIST Computer Security Incident Handling Guide, what is the next step in handling the event?
A. Perform an AV scan on the infected endpoint.
B. Isolate the infected endpoint from the network.
C. Prioritize incident handling based on the impact.
D. Analyze the malware behavior.
What is a difference between data obtained from Tap and SPAN ports?
A. SPAN passively splits traffic between a network device and the network without altering it, while Tap alters response times.
B. Tap mirrors existing traffic from specified ports, while SPAN presents more structured data for deeper analysis.
C. SPAN improves the detection of media errors, while Tap provides direct access to traffic with lowered data visibility.
D. Tap sends traffic from physical layers to the monitoring device, while SPAN provides a copy of network traffic from switch to destination.
An analyst discovers that a legitimate security alert has been dismissed. Which signature caused this impact on network traffic?
A. true negative
B. false negative
C. false positive
D. true positive
How does an SSL certificate impact security between the client and the server?
A. by enabling an authenticated channel between the client and the server
B. by creating an integrated channel between the client and the server
C. by enabling an authorized channel between the client and the server
D. by creating an encrypted channel between the client and the server
Which action should be taken if the system is overwhelmed with alerts when false positives and false negatives are compared?
A. Modify the settings of the intrusion detection system.
B. Design criteria for reviewing alerts.
C. Redefine signature rules.
D. Adjust the alerts schedule.
A company's cyber security team performed a phishing simulation campaign for employees and performed security awareness trainings to affected personal. According to NIST.SP800-61, at which phase of incident response is this action?
A. post-incident activity phase
B. detection and analyze phase
C. preparation phase
D. eradication and recovery phase
Refer to the exhibit. A company's user HTTP connection to a malicious site was blocked according to configured policy. What is the source technology used for this measure?
A. network application control
B. firewall
C. IPS
D. web proxy
One of the objectives of information security is to protect the CIA of information and systems. What does CIA mean in this context?
A. confidentiality, identity, and authorization
B. confidentiality, integrity, and authorization
C. confidentiality, identity, and availability
D. confidentiality, integrity, and availability
DRAG DROP - Drag and drop the data source from the left onto the data type on the right. Select and Place:
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
A. syslog messages
B. full packet capture
C. NetFlow
D. firewall event logs
What is the difference between indicator of attack (IoA) and indicators of compromise (IoC)?
A. IoA refers to the individual responsible for the security breach, and IoC refers to the resulting loss.
B. IoA is the evidence that a security breach has occurred, and IoC allows organizations to act before the vulnerability can be exploited.
C. IoC refers to the individual responsible for the security breach, and IoA refers to the resulting loss.
D. IoC is the evidence that a security breach has occurred, and IoA allows organizations to act before the vulnerability can be exploited.
A user received an email attachment named `Hr402-report3662-empl621.exe` but did not run it. Which category of the cyber kill chain should be assigned to this type of event?
A. delivery
B. reconnaissance
C. weaponization
D. installation
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group. What is the initial event called in the NIST SP800-61?
A. online assault
B. precursor
C. trigger
D. instigator
What are two denial-of-service (DoS) attacks? (Choose two.)
A. port scan
B. phishing
C. man-in-the-middle
D. teardrop
E. SYN flood
Refer to the exhibit. Which two elements in the table are parts of the 5-tuple? (Choose two.)
A. First Packet
B. Initiator User
C. Ingress Security Zone
D. Source Port
E. Initiator IP
DRAG DROP - Drag and drop the security concept on the left onto the example of that concept on the right. Select and Place:
Which system monitors local system operation and local network access for violations of a security policy?
A. host-based intrusion detection
B. systems-based sandboxing
C. host-based firewall
D. antivirus
What are two differences between tampered disk images and untampered disk images? (Choose two.)
A. The image is tampered if the stored hash and the computed hash are identical.
B. Tampered images are used as an element for the root cause analysis report.
C. Untampered images can be used as law enforcement evidence.
D. Tampered images are used in a security Investigation process.
E. The image is untampered if the existing stored hash matches the computed one.
Access Full 200-201 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 200-201 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 200-201 mock test free today—and take a major step toward exam success!