200-201 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the 200-201 certification? Our 200-201 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective 200-201 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic 200-201 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
What are the two differences between stateful and deep packet inspection? (Choose two.)
A. Deep packet inspection is capable of TCP state monitoring only, and stateful inspection can inspect TCP and UDP.
B. Stateful inspection is capable of packet data inspections, and deep packet inspection is not.
C. Deep packet inspection is capable of malware blocking, and stateful inspection is not.
D. Stateful inspection is capable of TCP state tracking, and deep packet filtering checks only TCP source and destination ports.
E. Deep packet inspection operates on Layer 3 and 4, and stateful inspection operates on Layer 3 of the OSI model.
What is an incident response plan?
A. an organizational approach to events that could lead to asset loss or disruption of operations
B. an organizational approach to security management to ensure a service lifecycle and continuous improvements
C. an organizational approach to disaster recovery and timely restoration of operational services
D. an organizational approach to system backup and data archiving aligned to regulations
An analyst received a ticket regarding a degraded processing capability for one of the HR department's servers. On the same day an engineer noticed a disabled antivirus software and was not able to determine when or why it occurred. According to the NIST Incident Handling Guide, what is the next phase of this investigation?
A. Analysis
B. Eradication
C. Detection
D. Recovery
Refer to the exhibit. What does this Cuckoo sandbox report indicate?
A. The file is ransomware.
B. The file is spyware.
C. The file will open unsecure ports when executed.
D. The file will open a command interpreter when executed.
An organization is cooperating with several third-party companies. Data exchange is on an unsecured channel using port 80. Internal employees use the FTP service to upload and download sensitive data. An engineer must ensure confidentiality while preserving the integrity of the communication. Which technology must the engineer implement in this scenario?
A. RADIUS server
B. web application firewall
C. X.509 certificates
D. CA server
What describes a buffer overflow attack?
A. suppressing the buffers in a process
B. injecting new commands into existing buffers
C. overloading a predefined amount of memory
D. fetching data from memory buffer registers
Refer to the exhibit. An engineer received an event log file to review. Which technology generated the log?
A. IDS/IPS
B. firewall
C. proxy
D. NetFlow
Refer to the exhibit. What does the message indicate?
A. an access attempt was made from the Mosaic web browser
B. a successful access attempt was made to retrieve the password file
C. a successful access attempt was made to retrieve the root of the website
D. a denied access attempt was made to retrieve the password file
One of the objectives of information security is to protect the CIA of information and systems. What does CIA mean in this context?
A. confidentiality, identity, and authorization
B. confidentiality, integrity, and authorization
C. confidentiality, identity, and availability
D. confidentiality, integrity, and availability
An engineer is analyzing a recent breach where confidential documents were altered and stolen by the receptionist. Further analysis shows that the threat actor connected an external USB device to bypass security restrictions and steal data. The engineer could not find an external USB device. Which piece of information must an engineer use for attribution in an investigation?
A. receptionist and the actions performed
B. stolen data and its criticality assessment
C. external USB device
D. list of security restrictions and privileges boundaries bypassed
A developer is working on a project using a Linux tool that enables writing processes to obtain these required results: ✑ If the process is unsuccessful, a negative value is returned. ✑ If the process is successful, 0 value is returned to the child process, and the process ID is sent to the parent process. Which component results from this operation?
A. parent directory name of a file pathname
B. process spawn scheduled
C. macros for managing CPU sets
D. new process created by parent process
Which system monitors local system operation and local network access for violations of a security policy?
A. host-based data loss prevention
B. host-based intrusion detection
C. antivirus
D. sandbox
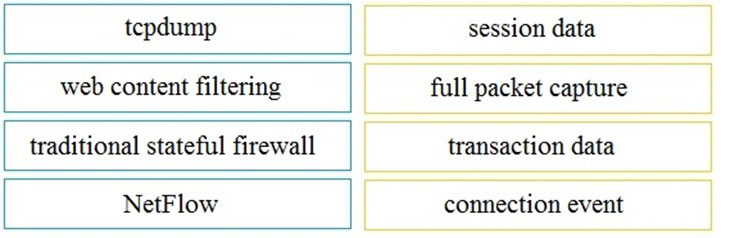
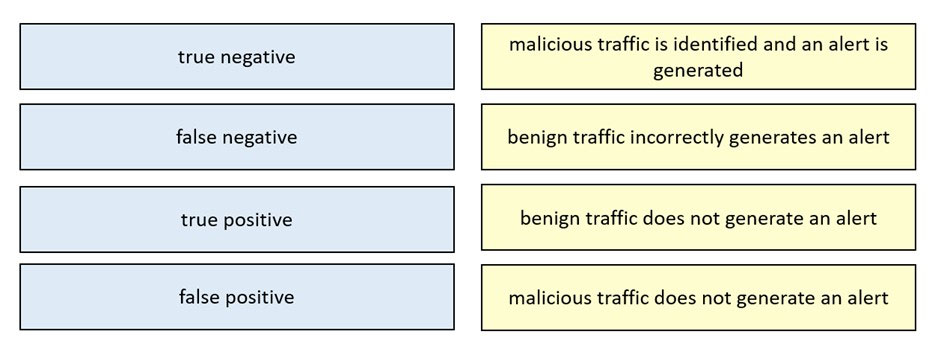
DRAG DROP - Drag and drop the technology on the left onto the data type the technology provides on the right. Select and Place:
What is a difference between signature-based and behavior-based detection?
A. Signature-based identifies behaviors that may be linked to attacks, while behavior-based has a predefined set of rules to match before an alert.
B. Behavior-based identifies behaviors that may be linked to attacks, while signature-based has a predefined set of rules to match before an alert.
C. Behavior-based uses a known vulnerability database, while signature-based intelligently summarizes existing data.
D. Signature-based uses a known vulnerability database, while behavior-based intelligently summarizes existing data.
What is the difference between an attack vector and an attack surface?
A. An attack surface identifies vulnerabilities that require user input or validation; and an attack vector identifies vulnerabilities that are independent of user actions.
B. An attack vector identifies components that can be exploited; and an attack surface identifies the potential path an attack can take to penetrate the network.
C. An attack surface recognizes which network parts are vulnerable to an attack; and an attack vector identifies which attacks are possible with these vulnerabilities.
D. An attack vector identifies the potential outcomes of an attack; and an attack surface launches an attack using several methods against the identified vulnerabilities.
Refer to the exhibit. An analyst was given a PCAP file, which is associated with a recent intrusion event in the company FTP server. Which display filters should the analyst use to filter the FTP traffic?
A. dst.port = 21
B. tcp.port == 21
C. dstport == FTP
D. tcpport = FTP
Which event is a vishing attack?
A. obtaining disposed documents from an organization
B. using a vulnerability scanner on a corporate network
C. impersonating a tech support agent during a phone call
D. setting up a rogue access point near a public hotspot
A company's cyber security team performed a phishing simulation campaign for employees and performed security awareness trainings to affected personal. According to NIST.SP800-61, at which phase of incident response is this action?
A. post-incident activity phase
B. detection and analyze phase
C. preparation phase
D. eradication and recovery phase
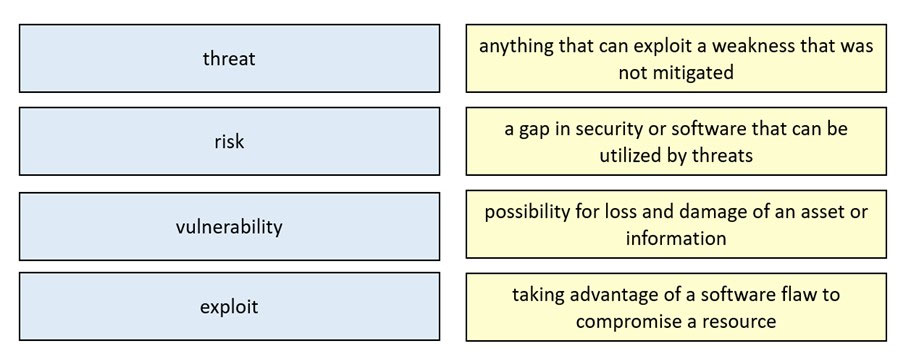
What is the relationship between a vulnerability and a threat?
A. A threat exploits a vulnerability
B. A vulnerability is a calculation of the potential loss caused by a threat
C. A vulnerability exploits a threat
D. A threat is a calculation of the potential loss caused by a vulnerability
Which type of evidence supports a theory or an assumption that results from initial evidence?
A. probabilistic
B. indirect
C. best
D. corroborative
The SOC team has confirmed a potential indicator of compromise on an endpoint. The team has narrowed the executable file's type to a new trojan family. According to the NIST Computer Security Incident Handling Guide, what is the next step in handling this event?
A. Perform forensics analysis on the infected endpoint
B. Isolate the infected endpoint from the network
C. Prioritize incident handling based on the impact
D. Collect public information on the malware behavior
An offline audit log contains the source IP address of a session suspected to have exploited a vulnerability resulting in system compromise. Which kind of evidence is this IP address?
A. best evidence
B. corroborative evidence
C. indirect evidence
D. forensic evidence
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs. Which technology should be used to accomplish this task?
A. application whitelisting/blacklisting
B. network NGFW
C. host-based IDS
D. antivirus/antispyware software
An engineer needs to discover alive hosts within the 192.168.1.0/24 range without triggering intrusive portscan alerts on the IDS device using Nmap. Which command will accomplish this goal?
A. nmap –top-ports 192.168.1.0/24
B. nmap ג€”sP 192.168.1.0/24
C. nmap -sL 192.168.1.0/24
D. nmap -sV 192.168.1.0/24
What are two differences between tampered disk images and untampered disk images? (Choose two.)
A. The image is tampered if the stored hash and the computed hash are identical.
B. Tampered images are used as an element for the root cause analysis report.
C. Untampered images can be used as law enforcement evidence.
D. Tampered images are used in a security Investigation process.
E. The image is untampered if the existing stored hash matches the computed one.
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
A. Tampered images are used in the security investigation process.
B. Tampered images are used in the incident recovery process.
C. The image is tampered if the stored hash and the computed hash match.
D. Untampered images are used in the security investigation process.
E. The image is untampered if the stored hash and the computed hash match.
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
A. application identification number
B. active process identification number
C. runtime identification number
D. process identification number
Which system monitors local system operation and local network access for violations of a security policy?
A. host-based intrusion detection
B. systems-based sandboxing
C. host-based firewall
D. antivirus
An engineer runs a suspicious file in a sandbox analysis tool to see the outcome. The analysis report shows that outbound callouts were made post infection. Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
A. signatures
B. host IP addresses
C. file size
D. dropped files
E. domain names
Refer to the exhibit. In which Linux log file is this output found?
A. /var/log/authorization.log
B. /var/log/dmesg
C. var/log/var.log
D. /var/log/auth.log
Which incidence response step includes identifying all hosts affected by an attack?
A. detection and analysis
B. post-incident activity
C. preparation
D. containment, eradication, and recovery
DRAG DROP - Drag and drop the security concept from the left onto the example of that concept on the right. Select and Place:
How does statistical detection differ from rule-based detection?
A. Statistical detection involves the evaluation of events, and rule-based detection requires an evaluated set of events to function.
B. Rule-based detection involves the evaluation of events, and statistical detection requires an evaluated set of events to function.
C. Statistical detection defines legitimate data over time, and rule-based detection works on a predefined set of rules.
D. Rule-based detection defines legitimate data over a period of time, and statistical detection works on a predefined set of rules.
A threat actor penetrated an organization's network. Using the 5-tuple approach, which data points should the analyst use to isolate the compromised host in a grouped set of logs?
A. event name, log source, time, source IP, and username
B. event name, log source, time, source IP, and host name
C. protocol, log source, source IP, destination IP, and host name
D. protocol, source IP, source port destination IP, and destination port
A SOC analyst observed Ursnif malware at the SIEM dashboard. The analyst opened the PCAP file to search the certificate issue data. Where must the analyst navigate?
A. under the rdnSequence line
B. under the validity line
C. under the subject
D. under the signed certificate
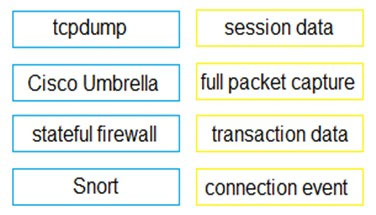
DRAG DROP - Drag and drop the technology on the left onto the data type the technology provides on the right. Select and Place:
A user received a suspicious email and reported it to the SOC team. After analysis, the team concluded that it was a spear phishing attack. According to the Diamond Model, how is the phishing email categorized?
A. capability
B. infrastructure
C. adversary
D. victim
Which regex matches only on all lowercase letters?
A. [aגˆ’z]+
B. [^aגˆ’z]+
C. aגˆ’z+
D. a*z+
Refer to the exhibit. What must be interpreted from this packet capture?
A. IP address 192.168.88.12 is communicating with 192.168.88.149 with a source port 49098 to destination port 80 using TCP protocol.
B. IP address 192.168.88.149 is communicating with 192.168.88.12 with a source port 49098 to destination port 80 using TCP protocol.
C. IP address 192.168.88.149 is communicating with 192.168.88.12 with a source port 80 to destination port 49098 using TCP protocol.
D. IP address 192.168.88.12 is communicating with 192.168.88.149 with a source port 74 to destination port 49098 using TCP protocol.
An engineer is working with the compliance teams to identify the data passing through the network. During analysis, the engineer informs the compliance team that external perimeter data flows contain records, writings, and artwork. Internal segregated network flows contain the customer choices by gender, addresses, and product preferences by age? The engineer must identify protected data. Which two types of data must be identified? (Choose two.)
A. SOX
B. PII
C. PCI
D. PHI
E. copyright
What is a difference between SIEM and SOAR?
A. SIEM predicts and prevents security alerts, while SOAR checks attack patterns and applies the mitigation.
B. SIEM’s primary function is to collect and detect anomalies, while SOAR is more focused on security operations automation and response.
C. SOAR’s primary function is to collect and detect anomalies, while SIEM is more focused on security operations automation and response.
D. SOAR predicts and prevents security alerts, while SIEM checks attack patterns and applies the mitigation.
What is email greylisting by the mail transfer agent?
A. denying any email from a sender it does not recognize
B. returning emails that are potential phishing attempts
C. allowing emails from unknown senders temporarily
D. quarantining emails sent from outside of the organization
A system administrator is ensuring that specific registry information is accurate. Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
A. file extension associations
B. hardware, software, and security settings for the system
C. currently logged in users, including folders and control panel settings
D. all users on the system, including visual settings
What are two denial of service attacks? (Choose two.)
A. MITM
B. TCP connections
C. ping of death
D. UDP flooding
E. code red
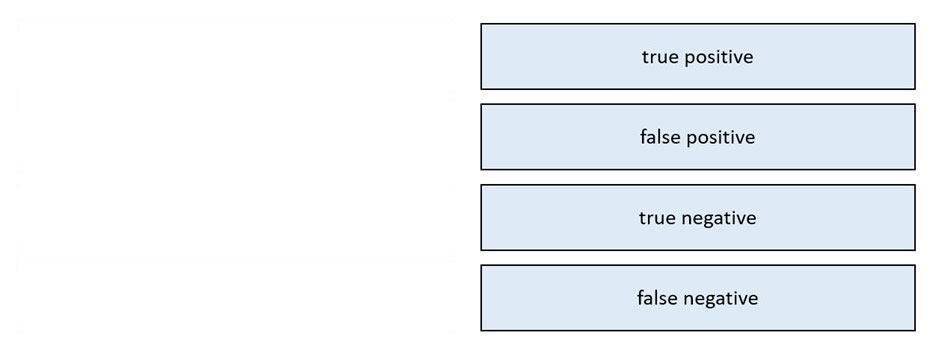
DRAG DROP - Drag and drop the event term from the left onto the description on the right. Select and Place:
DRAG DROP - Cisco’s Zero Trust Architecture simplifies the Zero Trust journey into three critical areas. Drag the definitions onto the graphic to describe Zero Trust from the Cisco perspective
What makes HTTPS traffic difficult to monitor?
A. SSL interception
B. packet header size
C. signature detection time
D. encryption
What is the function of a command and control server?
A. It enumerates open ports on a network device
B. It drops secondary payload into malware
C. It is used to regain control of the network after a compromise
D. It sends instruction to a compromised system
What is the impact of encryption?
A. Data is unaltered and its integrity is preserved.
B. Data is accessible and available to permitted individuals.
C. Confidentiality of the data is kept secure and permissions are validated.
D. Data is secure and unreadable without decrypting it.
Refer to the exhibit. Which component is identifiable in this exhibit?
A. Windows Registry hive
B. Trusted Root Certificate store on the local machine
C. Windows PowerShell verb
D. local service in the Windows Services Manager
Access Full 200-201 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of 200-201 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your 200-201 certification journey!