200-125 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 200-125 certification exam? Start your preparation the smart way with our 200-125 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 200-125 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 200-125 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
While troubleshooting a GRE tunnel interface issue, show interface command output displays tunnel status up, but line protocol is down. Which reason for this problem is the most likely?
A. The next hop server is misconfigured.
B. The route to the tunnel destination address is through the tunnel itself.
C. The tunnel was just reset.
D. The interface has been administratively shut down.
Which two options are benefits of DHCP snooping? (Choose two.)
A. It simplifies the process of adding DHCP servers to the network.
B. It prevents the deployment of rogue DHCP servers.
C. It prevents DHCP reservations.
D. It tracks the location of hosts in the network.
E. It prevents static reservations.
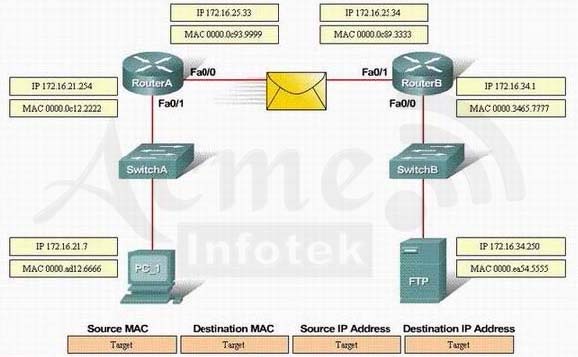
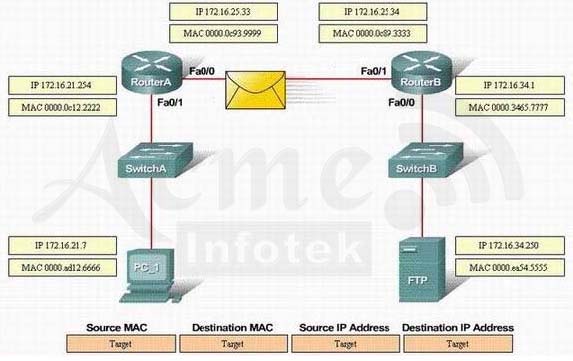
Refer to the exhibit. PC_1 is sending packets to the FTP server. Consider the packets as they leave RouterA interface Fa0/0 towards RouterB. Drag the correct frame and packet address to their place in the table.Select and Place:
Which type of frames is larger than 9000 bytes?
A. baby giant
B. jumbo
C. runt
D. giant
Which term describes a spanning-tree network that has all switch ports in either the blocking or forwarding state?
A. converged
B. redundant
C. provisioned
D. spanned
Which statement is correct regarding the operation of DHCP?
A. A DHCP client uses a ping to detect address conflicts.
B. A DHCP server uses a gratuitous ARP to detect DHCP clients.
C. A DHCP client uses a gratuitous ARP to detect a DHCP server.
D. If an address conflict is detected, the address is removed from the pool and an administrator must resolve the conflict.
E. If an address conflict is detected, the address removed from the pool for an amount of time configurable by the administrator.
F. If an address conflict is detected, the address is removed from the pool and will not be reused until server is rebooted.
Refer to the exhibit. If RTR01 is configured as shown, which three addresses will be received by other routers that are running EIGRP on the network?
A. 172.16.4.0
B. 192.168.2.0
C. 10.0.0.0
D. 192.168.0.0
E. 172.16.0.0
F. 10.4.3.0
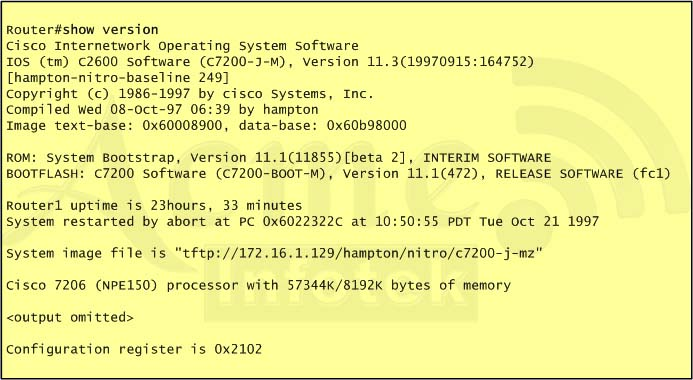
Refer to the exhibit. For what two reasons has the router loaded its IOS image from the location that is shown?(Choose two)
A. Router1 has specific boot system commands that instruct it to load IOS from TFTP server.
B. Router1 is acting as a TFTP server for other routers.
C. Router1 cannot locate a valid IOS image in flash memory.
D. Router1 defaulted to ROMMON mode and loaded the IOS image from a TFTP server.
E. Cisco routers will first attempt to load a image from TFTP for management purposes.
Which two passwords must be supplied in order to connect by Telnet to a properly secured Cisco switch and make changes to the device configuration? (Choose two.)
A. tty password
B. enable secret password
C. vty password
D. aux password
E. console password
F. username password
Which two statements about TACACS+ are true? (Choose two.)
A. It uses TCP port 49
B. It combines authentication and authorization to simplify configuration
C. It uses UDP port 49
D. It supports full command logging
E. It encrypts the password only
Which characteristics are representative of a link-state routing protocol? (Choose three.)
A. provides common view of entire topology
B. exchanges routing tables with neighbors
C. calculates shortest path
D. utilizes event-triggered updates
E. utilizes frequent periodic updates
Which command is used to enable CHAP authentication, with PAP as the fallback method, on a serial interface?
A. Router(config-if)# ppp authentication chap fallback ppp
B. Router(config-if)# authentication ppp chap fallback ppp
C. Router(config-if)# ppp authentication chap pap
D. Router(config-if)# authentication ppp chap pap
What can be done to secure the virtual terminal interfaces on a router? (Choose two.)
A. Administratively shut down the interface.
B. Physically secure the interface.
C. Create an access list and apply to the virtual terminal interfaces with the access-group command.
D. Configure a virtual terminal password and login process.
E. Enter an access list and apply it to the virtual terminal interfaces using the access-class command.
Which network topology allows all traffic to flow through a central hub?
A. bus
B. star
C. mesh
D. ring
Which two VLAN IDs indicate a default VLAN? (Choose two.)
A. 0
B. 1
C. 1005
D. 1006
E. 4096
Which two statements about wireless LAN controllers are true? (Choose two.)
A. They can simplify the management and deployment of wireless LANs.
B. They rely on external firewalls for WLAN security.
C. They are best suited to smaller wireless networks.
D. They must be configured through a GUI over HTTP or HTTPS.
E. They can manage mobility policies at a systemwide level.
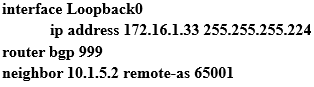
Refer to the exhibit. Which command do you enter so that R1 advertises the Loopback0 interface to the BGP peers?
A. network 172.16.1.32 mask 255.255.255.224
B. network 172.16.1.0 0.0.0.255
C. network 172.16.1.32 255.255.255.224
D. network 172.16.1.33 mask 255.255.255.224
E. network 172.16.1.32 mask 0.0.0.31
F. network 172.16.1.32 0.0.0.31
Which three statements accurately describe layer 2 Ethernet switches? (choose three)
A. Microsegmentation decreases the number of collisions on the network.
B. If a switch receives a frame for an unknown destination, it uses ARP to resolve the address.
C. Spanning Tree Protocol allows switches to automatically share vlan information.
D. In a properly functioning network with redundant switched paths, each switched segment will contain one root bridge with all its ports in the forwarding state. All other switches in that broadcast domain will have only one root port.
E. Establishing vlans increases the number of broadcast domains.
F. Switches that are configured with vlans make forwarding decisions based on both layer 2 and layer 3 address information.
Which configuration register value can you set on a Cisco device so that it ignores the NVRAM when it boots?
A. 0x2124
B. 0x2120
C. 0x2142
D. 0x2102
What occurs on a Frame Relay network when the CIR is exceeded?
A. All TCP traffic is marked discard eligible.
B. All UDP traffic is marked discard eligible and a BECN is sent.
C. All TCP traffic is marked discard eligible and a BECN is sent.
D. All traffic exceeding the CIR is marked discard eligible.
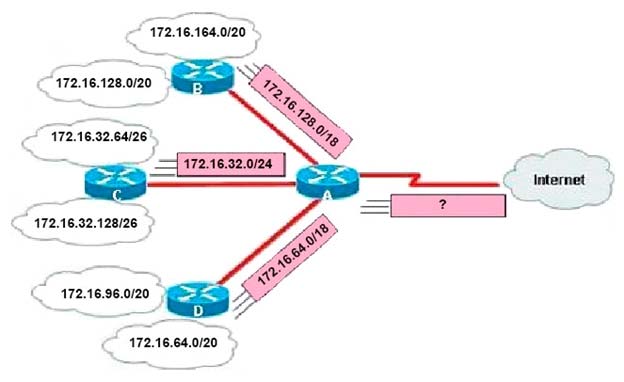
Refer to the exhibit.In the Frame Relay network, which IP addresses would be assigned to the interfaces with point-to- point PVCs?
A. DLCI 16: 192.168.10.1 /24 DLCI 17: 192.168.10.1 /24 DLCI 99: 192.168.10.2 /24 DLCI 28: 192.168.10.3 /24
B. DLCI 16: 192.168.10.1 /24 DLCI 17: 192.168.11.1 /24 DLCI 99: 192.168.12.1 /24 DLCI 28: 192.168.13.1 /24
C. DLCI 16: 192.168.10.1 /24 DLCI 17: 192.168.10.2 /24 DLCI 99: 192.168.10.3 /24 DLCI 28: 192.168.10.4 /24
D. DLCI 16: 192.168.10.1 /24 DLCI 17: 192.168.11.1 /24 DLCI 99: 192.168.10.2 /24
Which chassis-aggregation technology combines two physical switches into one virtual switch?
A. VSS
B. LACP
C. VRRP
D. StackWise
Which networking Technology is currently recognized as the standard for computer networking?
A. System network architecture
B. Transmission control protocol/Internet protocol
C. Open system Interconnect
D. Open network architecture
Which Type of ipv6 unicast ip address is reachable across the Internet?
A. Unique Local
B. Compatible
C. Link local
D. Globa
In which situation would the use of a static route be appropriate?
A. To configure a route to the first Layer 3 device on the network segment.
B. To configure a route from an ISP router into a corporate network.
C. To configure a route when the administrative distance of the current routing protocol is too low.
D. To reach a network is more than 15 hops away.
E. To provide access to the Internet for enterprise hosts.
Which statement about QoS default behavior is true?
A. Ports are untrusted by default.
B. VoIP traffic is passed without being tagged.
C. Video traffic is passed with a well-known DSCP value of 46.
D. Packets are classified internally with an environment.
E. Packets that arrive with a tag are untagged at the edge of an administrative domain.
You are implementing WAN access for an enterprise network while running applications that require a fully meshed network, which two design standards are appropriate for such an environment? (Choose two.)
A. a dedicated WAN distribution layer, to consolidate connectivity to remote sites
B. a centralized DMVPN solution, to simplify connectivity for the enterprise
C. multiple MPLS VPN connections with static routing
D. a collapsed core and distribution layer, to minimize costs
E. multiple MPLS VPN connections with dynamic routing
Which three statements about link-state routing are true? (Choose three.)
A. OSPF is a link-state protocol.
B. Updates are sent to a broadcast address.
C. It uses split horizon.
D. Routes are updated when a change in topology occurs.
E. RIP is a link-state protocol.
F. Updates are sent to a multicast address by default.
How should a router that is being used in a Frame Relay network be configured to avoid split horizon issues from preventing routing updates?
A. Configure a separate sub-interface for each PVC with a unique DLCI and subnet assigned to the sub-interface
B. Configure each Frame Relay circuit as a point-to-point line to support multicast and broadcast traffic
C. Configure many sub-interfaces on the same subnet
D. Configure a single sub-interface to establish multiple PVC connections to multiple remote router interfaces
What are two characteristics of Frame Relay point-to-point subinterfaces? (Choose two.)
A. They create split-horizon issues.
B. They require a unique subnet within a routing domain.
C. They emulate leased lines.
D. They are ideal for full-mesh topologies.
E. They require the use of NBMA options when using OSPF.
Which command can you use to manually assign a static IPv6 address to a router interface?
A. ipv6 autoconfig 2001:db8:2222:7272::72/64
B. ipv6 address 2001:db8:2222:7272::72/64
C. ipv6 address PREFIX_1 ::1/64
D. ipv6 autoconfig
What is one benefit of PVST+?
A. PVST+ supports Layer 3 load balancing without loops.
B. PVST+ reduces the CPU cycles for all the switches in the network.
C. PVST+ allows the root switch location to be optimized per VLAN.
D. PVST+ automatically selects the root bridge location, to provide optimized bandwidth usage.
What is the default lease time for a DHCP binding?
A. 24 hours
B. 12 hours
C. 48 hours
D. 36 hours
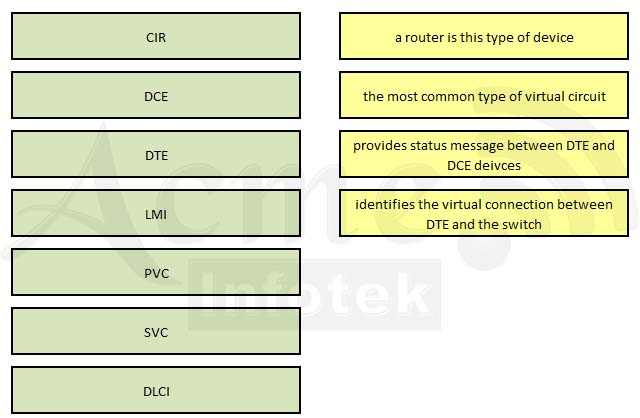
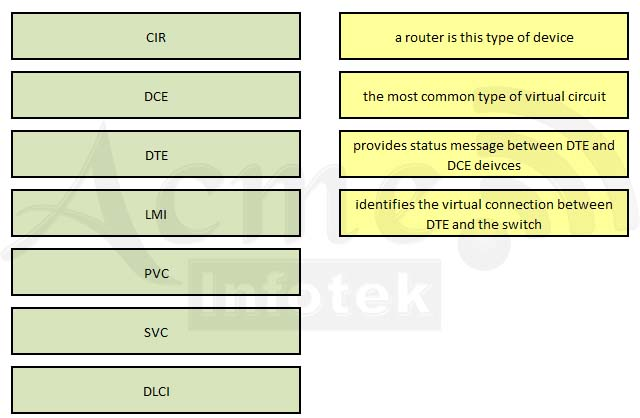
Drag the Frame Relay acronym on the left to match its definition on the right. (Not all acronyms are used.)Select and Place:
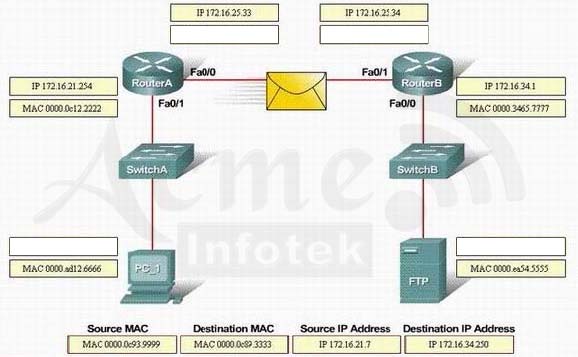
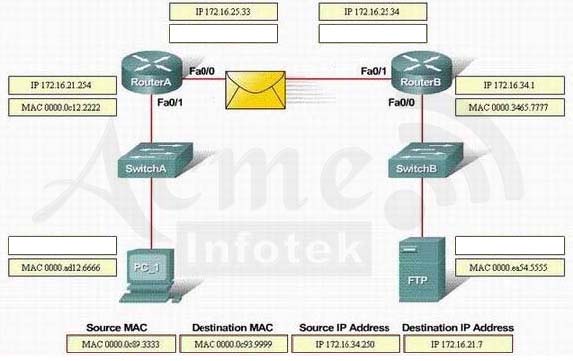
Refer to the exhibit. FTP Server is sending packets to the PC_1. Consider the packets as they leave RouterB interface Fa0/0 towards RouterA. Drag the correct frame and packet address to their place in the table.Select and Place:
Which NAT function can map multiple inside addresses to a single outside address?
A. PAT
B. SFTP
C. RARP
D. ARP
E. TFTP
What command is used to verify the DLCI destination address in a Frame Relay static configuration?
A. show frame-relay pvc
B. show frame-relay lmi
C. show frame-relay map
D. show frame relay end-to-end
Refer to the exhibit. In this VLSM addressing scheme, what summary address would be sent from router A?
A. 172.16.0.0 /16
B. 172.16.0.0 /20
C. 172.16.0.0 /24
D. 172.32.0.0 /16
E. 172.32.0.0 /17
F. 172.64.0.0 /16
Which type of EIGRP route entry describes a feasible successor?
A. a primary router, stored in the topology table
B. a backup router, stored in the routing table
C. a backup route, stored in the topology table
D. a primary router, stored in the routing table
When troubleshooting client DNS issues, which two task must you perform? (Choose two)
A. Ping a public website IP address.
B. Ping the DNS Server.
C. Determine whether a DHCP address has been assigned.
D. Determine whether the hardware address is correct.
E. Determine whether the name servers have been configured
Which address block identifies all link-local addresses?
A. FC00::/7
B. FC00::/8
C. FE80::/10
D. FF00::/8
What are two advantages of Layer 2 Ethernet switches over hubs? (Choose two.)
A. decreasing the number of collision domains
B. filtering frames based on MAC addresses
C. allowing simultaneous frame transmissions
D. increasing the size of broadcast domains
E. increasing the maximum length of UTP cabling between devices BC
How to verify SSH connections was secured?
A. ssh -v 1 -l admin IP
B. ssh -v 2 -l admin IP
C. ssh -l admin IP
D. ssh -v -l admin IP
Frame flooding can occur in which circumstances?
A. The destination IP address is missing from the route table.
B. The destination MAC address is missing from the CAM table.
C. The source IP address is missing from the route table.
D. The source MAC address is missing from the CAM table.
When a device learns multiple routes to a specific network, it installs the route with:
A. Longest bit Match (highest subnet Mask
B. lowest AD (Administrative distance)
C. lowest metric
D. equal load balancing
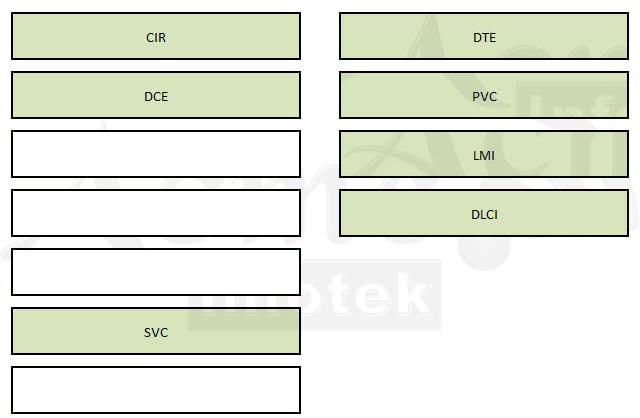
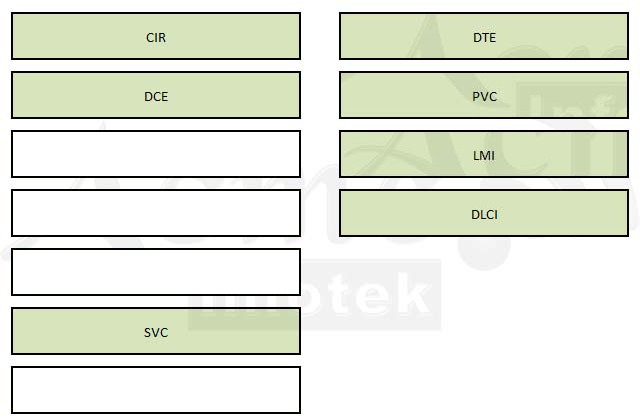
Drag the Frame Relay acronym on the left to match its definition on the right. (Not all acronyms are used.)Select and Place:
What is the purpose of Inverse ARP?
A. to map a known IP address to a MAC address
B. to map a known DLCI to a MAC address
C. to map a known MAC address to an IP address
D. to map a known DLCI to an IP address
E. to map a known IP address to a SPID
F. to map a known SPID to a MAC address
What are two characteristics of Frame Relay point-to-point subinterfaces? (Choose two.)
A. They create split-horizon issues.
B. They require a unique subnet within a routing domain.
C. They emulate leased lines.
D. They are ideal for full-mesh topologies.
E. They require the use of NBMA options when using OSPF.
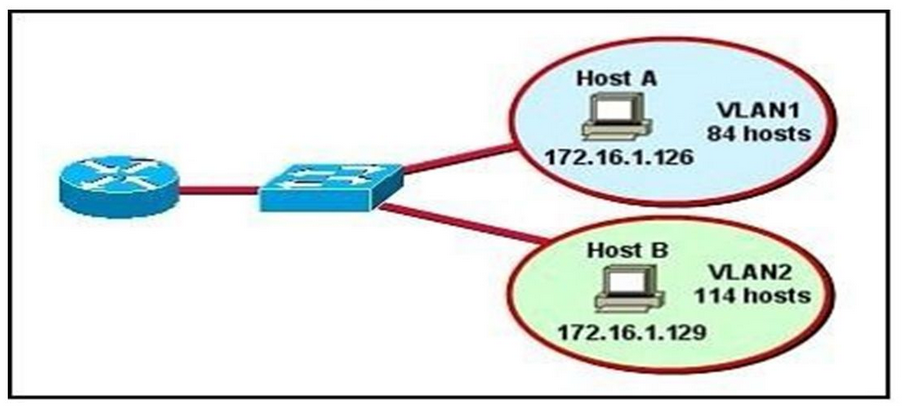
Refer to the diagram. All hosts have connectivity with one another. Which statements describe the addressing scheme that is in use in the network? (Choose three.)
A. The subnet mask in use is 255.255.255.192.
B. The subnet mask in use is 255.255.255.128.
C. The IP address 172.16.1.25 can be assigned to hosts in VLAN1
D. The IP address 172.16.1.205 can be assigned to hosts in VLAN1
E. The LAN interface of the router is configured with one IP address.
F. The LAN interface of the router is configured with multiple IP addresses.
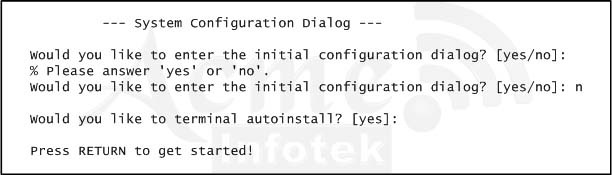
Refer to the exhibit. A network administrator configures a new router and enters the copy startup-config running-config command on the router. The network administrator powers down the router and sets it up at a remote location. When the router starts, it enters the system configuration dialog as shown. What is the cause of the problem?
A. The network administrator failed to save the configuration.
B. The configuration register is set to 0x2100.
C. The boot system flash command is missing from the configuration.
D. The configuration register is set to 0x2102.
E. The router is configured with the boot system startup command.
Access Full 200-125 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 200-125 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 200-125 mock test free today—and take a major step toward exam success!