102-500 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the 102-500 certification? Our 102-500 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective 102-500 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic 102-500 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
Which configuration file contains the default options for SSH clients?
A. /etc/ssh/sshd_config
B. /etc/ssh/ssh
C. /etc/ssh/ssh_config
D. /etc/ssh/client
E. /etc/ssh/ssh_client
Which of the following files is not read directly by a Bash login shell?
A. ~/.bashrc
B. ~/.bash_profile
C. ~/.bash_login
D. ~/.profile
E. /etc/profile
Which command makes the shell variable named VARIABLE visible to subshells?
A. export $VARIABLE
B. env VARIABLE
C. set $VARIABLE
D. set VARIABLE
E. export VARIABLE
Which mechanism does ssh use to interact with the SSH agent?
A. Connecting to port 2222 which is used by the system-wide SSH agent.
B. Using the fixed socket .ssh-agent/ipc.
C. Creating an alias replacing ssh with calls to ssh-agent.
D. Starting ssh-agent as a child process for each ssh invocation.
E. Evaluating environment variables such as SSH_AUTH_SOCK.
What is the purpose of the iconv command?
A. It converts bitmap images from one format to another such as PNG to JPE
B. It verifies that the root directory tree compiles to all conventions from the Filesystem Hierarchy Standard (FHS).
C. It converts files from one character set to an other.
D. It changes the mode of an inode in the ext4 filesystem.
E. It displays additional meta information from icon files ending in .ico.
What output is produced by the following command sequence? echo '1 2 3 4 5 6' | while read a b c; do echo result $c $b $a; done
A. result: 6 5 4
B. result: 1 2 3 4 5 6
C. result: 3 4 5 6 2 1
D. result: 6 5 4 3 2 1
E. result: 3 2 1
What information is provided by the echo $$ command?
A. The process ID of the current shell.
B. The process ID for the following command.
C. The process ID of the last command executed.
D. The process ID of the last command which has been placed in the background.
E. The process ID of the echo command.
Which of the following features are provided by SPICE? (Choose two.)
A. Connecting local USB devices to remote applications.
B. Accessing graphical applications on a remote host.
C. Replacing Xorg as local X11 server.
D. Downloading and locally installing applications from a remote machine.
E. Uploading and running a binary program on a remote machine.
Why is the correct configuration of a system's time zone important?
A. Because the timezone is included in checksum calculations and timezone changes invalidate existing checksums.
B. Because the time zone is saved as part of the modification times of files and cannot be changed after a file is created.
C. Because the environment variables LANG and LC_MESSAGES are, by default, set according to the time zone.
D. Because NTP chooses servers nearby based on the configured time zone.
E. Because the conversion of Unix timestamps to local time relies on the time zone configuration.
Which of the following commands display the number of bytes transmitted and received via the eth0 network interface? (Choose two.)
A. route -v via eth0
B. ip stats show dev eth0
C. netstat -s -i eth0
D. ifconfig eth0
E. ip -s link show eth0
How many IP addresses can be used for unique hosts inside the IPv4 subnet 192.168.2.128/26?
A. 6
B. 14
C. 30
D. 62
E. 126
FILL BLANK - Which command is used to set the hostname of the local system? (Specify only the command without any path or parameters.) hostname
Which of the following configuration files should be modified to globally set shell variables for all users?
A. /etc/profile
B. /etc/bashrc
C. ~/.bash_profile
D. /etc/.bashrc
E. /etc/shellenv
If neither cron.allow nor cron.deny exist in /etc/, which of the following is true?
A. Without additional configuration, all users may create user specific crontabs.
B. Without additional configuration, only root may create user specific crontabs.
C. The cron daemon will refuse to start and report missing files in the system’s log file.
D. When a user creates a user specific crontab the system administrator must approve it explicitly.
E. The default settings of /etc/crond.conf define whether or not user specific crontabs are generally allowed or not.
Which of the following files assigns a user to its primary group?
A. /etc/pgroup
B. /etc/shadow
C. /etc/passwd
D. /etc/group
E. /etc/gshadow
On a system using systemd-journald, which of the following commands add the message Howdy to the system log? (Choose two.)
A. append Howdy
B. logger Howdy
C. systemd-cat echo Howdy
D. echo Howdy > /dev/journal
E. journalctl add Howdy
Which of the following commands shows all active systemd timers?
A. systemctl-timer show
B. timectl list
C. systemctl “t
D. systemctl list-timers
E. timeq
FILL BLANK - Which command is used to sync the hardware clock to the system clock? (Specify only the command without any path or parameters.) hwclock
What is a purpose of an SSH host key?
A. It must be sent by any SSH client in addition to a user key in order to identify the client’s host.
B. It is root key by which all user SSH keys must be signed.
C. It provides the server’s identity information to connecting SSH clients.
D. It authenticates any user that logs into a remote machine from the key’s host.
E. It is used by system services like cron, syslog or a backup job to automatically connect to remote hosts.
Which of the following are syslog facilities? (Choose two.)
A. local5
B. accounting
C. mail
D. postmaster
E. remote
Which of the following IPv4 networks are reserved by IANA for private address assignment and private routing? (Choose three.)
A. 10.0.0.0/8
B. 127.0.0.0/8
C. 169.255.0.0/16
D. 172.16.0.0/12
E. 192.168.0.0/16
FILL BLANK - Which file is processed by newaliases? (Specify the full name of the file, including path.)
Which of the following sections exists in a systemd timer unit?
A. [Events]
B. [Timer]
C. [cron]
D. [Schedule]
E. [Trigger]
What is true about NetworkManager on a Linux system that uses its distribution's mechanisms to configure network interfaces? (Choose two.)
A. NetworkManager reconfigures all network interfaces to use DHCP unless they are specifically managed by NetworkManager.
B. NetworkManager must be explicitly enabled for each interface it should manage.
C. NetworkManager by default does not change interfaces which are already configured.
D. NetworkManager disables all interfaces which were not configured by NetworkManager.
E. NetworkManager can be configured to use the distribution’s network interface configuration.
Which of the following statements is true if the UID of a regular user is identical to the GID of a group?
A. UID have precedence over GIDs, therefore the user is available while the group doesn’t.
B. The user as well as the group are not available to avoid ambiguity due to the ID conflict.
C. UIDs and GIDs are independent of each other, therefore the user as well as the group are still available.
D. The user is the only member of the group, even if the group configuration contains other members.
E. GIDs have precedence over UIDs, therefore the group is available while the user isn’t.
Given the following routing table:
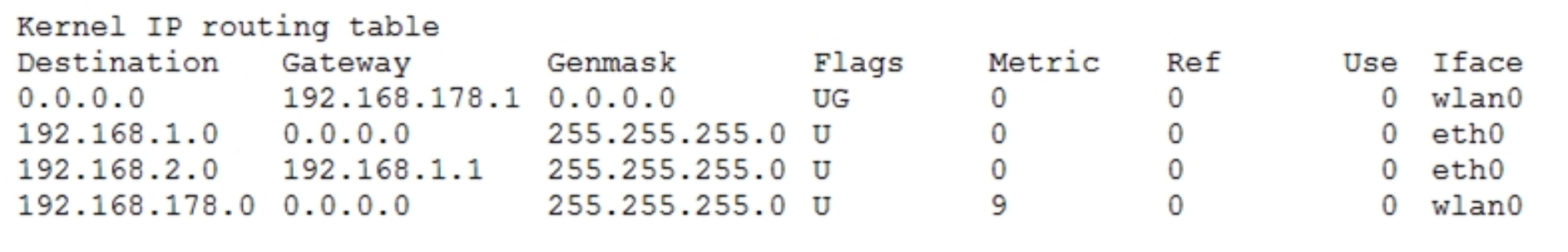
How would an outgoing packet to the destination 192.168.2.150 be handled?
A. It would be passed to the default router 192.168.178.1 on wlan0.
B. It would be directly transmitted on the device eth0.
C. It would be passed to the default router 255.255.255.0 on eth0.
D. It would be passed to the router 192.168.1.1 on eth0.
E. It would be directly transmitted on the device wlan0.
Which of the following connection types, as seen in nmcli connection show, may exist in NetworkManager? (Choose three.)
A. tcp
B. ethernet
C. wi
D. ipv6
E. bridge
Which file inside the CUPS configuration directory contains the settings of the printers?
A. cups-devices.conf
B. snmp.conf
C. printers.conf
D. printcap.conf
E. cupsd.conf
Which of the following parameters are used for journalctl to limit the time frame of the output? (Choose two.)
A. –since=
B. –from=
C. –until=
D. –upto=
E. –date=
What information related to a user account is modified using the chage command?
A. Default ownership for new files
B. Group membership
C. Set of commands available to the user
D. Password expiry information
E. Default permissions for new files
FILL BLANK - Which option in the /etc/ntp.conf file speci es an external NTP source to be queried for time information? (Specify only the option without any values or parameters.) server
Which file contains the data of the last change of a user's password?
A. /etc/gshadow
B. /etc/passwd
C. /etc/pwdlog
D. /var/log/shadow
E. /etc/shadow
FILL BLANK - Which command included in systemd supports selecting messages from the systemd journal by criteria such as time or unit name? (Specify only the command without any path or parameters.)
On a machine running several X servers, how do programs identify the different instances of the X11 server?
A. By a fixed UUID that is defined in the X11 configuration file.
B. By a display name like: 1.
C. By the name of the user that runs the X server like x11:bob.
D. By a device name like /dev/X11/xservers/1.
E. By a unique IPv6 address from the fe80::/64 subnet.
Depending on a system's configuration, which of the following files can be used to enable and disable network services running on this host?
A. /etc/profile
B. /etc/xinetd.conf
C. /etc/ports
D. /etc/services
E. /etc/host.conf
Which of the following is true about IPv6?
A. IPv6 no longer supports broadcast addresses.
B. With IPv6, the TCP port numbers of most services have changed.
C. IPv4 addresses can be used without any change with IPv6.
D. IPv6 no longer supports multicast addresses.
E. For IPv6, UDP and TCP have been replaced by the Rapid Transmission Protocol RTP.
FILL BLANK - Which parameter of the ssh command speci es the location of the private key used for login attempts? (Specify only the option name without any values or parameters.)
Which of the following statements is true regarding systemd timer units?
A. Timer units can only be defined within a service unit’s file.
B. The command executed by the timer is speci ed in the timer unit’s [Cmd] section.
C. A dedicated system service, systemd-cron, handles the execution of timer units.
D. Timer units only exist in the system scope and are not available for users.
E. Each systemd timer unit controls a specific systemd service unit.
FILL BLANK - What command, depending on its options, can display the open TCP connections, the routing tables, as well as network interface statistics? (Specify only the command without any path or parameters.)
How can a specific user be prevented from scheduling tasks with at?
A. By adding the specific user to the /etc/at.allow file.
B. By adding the specific user to the [deny] section in the /etc/atd.conf file.
C. By adding the specific user to the nojobs group.
D. By adding the specific user to the /etc/at.deny file.
E. By executing the atd –deny [user] command.
What can be speci ed with useradd? (Choose two.)
A. Commands the user can run using sudo.
B. The absolute path to the user’s home directory.
C. Which printers are available for the new user.
D. The SSH keys used to login to the new account.
E. The numeric user ID (UID) of the user.
FILL BLANK - What command enables a network interface according to distribution-specific configuration, such as /etc/network/interfaces or /etc/sysconfig/ network-scripts/ifcfg-eth0? (Specify only the command without any path or parameters.)
Which of the following commands can identify the PID od a process which opened a TCP port?
A. ptrace
B. strace
C. debug
D. lsof
E. nessus
What does the term Braille Display refer to?
A. A standardized high contract graphical theme for desktop applications?
B. A Linux desktop environment similar to KDE and GNOM
C. A legacy display technology superseded by LC
D. A physical representation of characters using small dots.
E. A standard file format for data exchange, similar to fixML.
Which of the following steps prevents a user from obtaining an interactive login session?
A. Setting the UID for the user to 0.
B. Running the command chsh “s /bin/false with the user name.
C. Removing the user from the group staff.
D. Adding the user to /etc/noaccess.
E. Creating a .nologin file in the user’s home directory.
Which of the following commands puts the output of the command date into the shell variable mydate?
A. mydate= date
B. mydate= exec date
C. mydate= $((date))
D. mydate= $(date)
E. mydate= ${date}
Which of the following information is stored in /etc/shadow for each user?
A. The timestamp of the user’s last login
B. The user’s private SSH keys
C. The hashed password of the user
D. The numerical user ID (UID)
E. The path to the user’s home directory
How do shadow passwords improve the password security in comparison to standard no-shadow password?
A. Regular users do not have access to the password hashes of shadow passwords.
B. Every shadow password is valid for 45 days and must be changed afterwards.
C. The system’s host key is used to encrypt all shadow passwords.
D. Shadow passwords are always combined with a public key that has to match the user’s private key.
E. Shadow passwords are stored in plain text and can be checked for weak passwords.
FILL BLANK - Which command, available with all sendmail-compatible MTAs, is used to list the contents of the MTA's mail queue? (Specify only the command without any path or parameters.) mailq
Which of the following statements about systemd-journald are true? (Choose three.)
A. It is incompatible with syslog and cannot be installed on a system using regular syslog.
B. It only processes messages of systemd and not messages of any other tools.
C. It can pass log messages to syslog for further processing.
D. It maintains metadata such as _UID or _PID for each message.
E. It supports syslog facilities such as kern, user, and auth.
Access Full 102-500 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of 102-500 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your 102-500 certification journey!

