102-500 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your 102-500 certification? Our 102-500 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an 102-500 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our 102-500 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
Which of the following commands can be used to limit the amount of memory a user may use?
A. umask
B. usermod
C. passwd
D. ulimit
E. chage
FILL BLANK - Which parameter of the ssh command speci es the location of the private key used for login attempts? (Specify only the option name without any values or parameters.)
Which command is used to set restrictions on the size of a core file that is created for a user when a program crashes?
A. core
B. edquota
C. quota
D. ulimit
E. ktrace
FILL BLANK - What option to useradd creates a new user's home directory and provisions it with a set of standard files? (Specify only the option name without any values or parameters.)
Which of the following commands lists all defines variables and functions within Bash?
A. env
B. export
C. env -a
D. set
E. echo $ENV
What information is provided by the echo $$ command?
A. The process ID of the current shell.
B. The process ID for the following command.
C. The process ID of the last command executed.
D. The process ID of the last command which has been placed in the background.
E. The process ID of the echo command.
FILL BLANK - What is the top-level directory which contains the configuration files for CUPS? (Specify the full path to the directory.)
Which of the following commands will delete the default gateway from the system's IP routing table? (Choose two.)
A. ifconfig unset default
B. route del default
C. ip route del default
D. netstat -r default
E. sysctl ipv4.default_gw=0
Which file contains the data of the last change of a user's password?
A. /etc/gshadow
B. /etc/passwd
C. /etc/pwdlog
D. /var/log/shadow
E. /etc/shadow
What output does the command seq 10 produce?
A. A continuous stream of numbers increasing in increments of 10 until the command is stopped.
B. It creates no output because a second parameter is missing.
C. The number 0 through 9 with one number per line.
D. The number 10 to standard output.
E. The numbers 1 through 10 with one number per line.
Which of the following commands shows all active systemd timers?
A. systemctl-timer show
B. timectl list
C. systemctl “t
D. systemctl list-timers
E. timeq
Which of the following changes may occur as a consequence of using the command ip? (Choose three.)
A. Network interfaces may become active or inactive.
B. New name servers may be added to the resolver configuration.
C. The system’s host name may change.
D. IP addresses may change.
E. The routing table may change.
What output does the command seq 1 5 20 produce?
A. 1
B. 1
C. 1
D. 2
E. 5
Why is the correct configuration of a system's time zone important?
A. Because the timezone is included in checksum calculations and timezone changes invalidate existing checksums.
B. Because the time zone is saved as part of the modification times of files and cannot be changed after a file is created.
C. Because the environment variables LANG and LC_MESSAGES are, by default, set according to the time zone.
D. Because NTP chooses servers nearby based on the configured time zone.
E. Because the conversion of Unix timestamps to local time relies on the time zone configuration.
FILL BLANK - Which parameter is missing in the command ip link set ____ dev eth0 to activate the previously inactive network interface eth0? (Specify the parameter only without any command, path or additional options.)
Which of the following are valid host addresses for the subnet 203.0.113.64/28? (Choose two.)
A. 203.0.113.64
B. 203.0.113.78
C. 203.0.113.65
D. 203.0.113.80
E. 203.0.113.81
Which of the following steps prevents a user from obtaining an interactive login session?
A. Setting the UID for the user to 0.
B. Running the command chsh “s /bin/false with the user name.
C. Removing the user from the group staff.
D. Adding the user to /etc/noaccess.
E. Creating a .nologin file in the user’s home directory.
Which of the following getent invocations lists all existing users?
A. getent homes
B. getent uids
C. getent passwd
D. getent users
E. getent logins
Which of the following protocols is related to the term open relay?
A. SMTP
B. POP3
C. NTP
D. IMAP
E. LDAP
Which of the following commands displays all environment and shell variables?
A. getargs
B. lsenv
C. ls
D. env
E. lsshell
FILL BLANK - What command, depending on its options, can display the open TCP connections, the routing tables, as well as network interface statistics? (Specify only the command without any path or parameters.)
What is true regarding the statement beginning with #! that is found in the first line of script? (Choose two.)
A. It prevents the scripts from being executed until the ! is removed.
B. it triggers the installation of the script’s interpreter.
C. It speci es the path and the arguments of the interpreter used to run the script.
D. It defines the character encoding of the script.
E. It is a comment that is ignored by the script interpreter.
Which of the following commands sets the system's time zone to the Canadian Eastern Time?
A. localegen -t -f /usr/share/zoneinfo/Canada/Eastern > /etc/locate.tz
B. tzconf /etc/localtime
C. sysctl -w clock.tz=’Canada/Eastern’
D. modprobe tz_ca_est
E. ln -sf /usr/share/zoneinfo/Canada/Eastern /etc/localtime
Which of the following statements is true regarding systemd timer units?
A. Timer units can only be defined within a service unit’s file.
B. The command executed by the timer is speci ed in the timer unit’s [Cmd] section.
C. A dedicated system service, systemd-cron, handles the execution of timer units.
D. Timer units only exist in the system scope and are not available for users.
E. Each systemd timer unit controls a specific systemd service unit.
Which of the following is true regarding the command sendmail?
A. With any MTA, the sendmail command must be run periodically by the cron daemon.
B. When using systemd, sendmail is an alias to relayctl.
C. The sendmail command prints the MTA’s queue history of which mails have been sent successfully.
D. It is only available when the sendmail MTA is installed.
E. All common MTAs, including Post x and Exim, provide a sendmail command.
Which of the following parameters are used for journalctl to limit the time frame of the output? (Choose two.)
A. –since=
B. –from=
C. –until=
D. –upto=
E. –date=
FILL BLANK - Which file, if present, must contain all users that are allowed to use the cron scheduling system? (Specify the full name of the file, including path.)
Depending on a system's configuration, which of the following files can be used to enable and disable network services running on this host?
A. /etc/profile
B. /etc/xinetd.conf
C. /etc/ports
D. /etc/services
E. /etc/host.conf
FILL BLANK - Which command included in systemd supports selecting messages from the systemd journal by criteria such as time or unit name? (Specify only the command without any path or parameters.)
What is the purpose of a screen reader?
A. It manages virtual keyboards on touch screen displays.
B. It reads the parameters of the attached monitors and creates an appropriate X11 configuration.
C. It displays lines and markers to help people use speed reading techniques.
D. It manages and displays files that contain e-books.
E. It reads displayed text to accommodate the needs of blind or visually impaired people.
Which of the following commands is used to rotate, compress, and mail system logs?
A. logrotate
B. striplog
C. syslogd “-rotate
D. rotatelog
E. logger
Which of the following information is stored in /etc/shadow for each user?
A. The timestamp of the user’s last login
B. The user’s private SSH keys
C. The hashed password of the user
D. The numerical user ID (UID)
E. The path to the user’s home directory
Which of the following configuration files should be modified to globally set shell variables for all users?
A. /etc/profile
B. /etc/bashrc
C. ~/.bash_profile
D. /etc/.bashrc
E. /etc/shellenv
Which of the following options in the chrony configuration file define remote time sources? (Choose two.)
A. source
B. clock
C. remote
D. pool
E. server
What is true regarding the file ~/.forward?
A. When configured correctly ~/.forward can be used to forward each incoming mail to one or more other recipients.
B. After editing ~/.forward the user must run newaliases to make the mail server aware of the changes.
C. Using ~/.forward, root may configure any email address whereas all other users may configure only their own addresses.
D. As ~/.forward is owned by the MTA and not writable by the user, it must be edited using the editaliases command.
E. By default, only ~/.forward files of users in the group mailq are processed while all other user’s ~/.forward files are ignored.
Which of the following comparison operators for test work on elements in the file system? (Choose two.)
A. “z
B. “eq
C. “d
D. “f
E. “lt
Which file inside the CUPS configuration directory contains the settings of the printers?
A. cups-devices.conf
B. snmp.conf
C. printers.conf
D. printcap.conf
E. cupsd.conf
If an alias ls exists, which of the following commands updates the alias to point to the command ls -l instead of the alias's current target?
A. set ls=’ls -l’
B. alias ls=’ls -l’
C. alias –force ls=’ls -l’
D. alias –update ls ls=’ls -l’
E. realias ls=’ls -l’
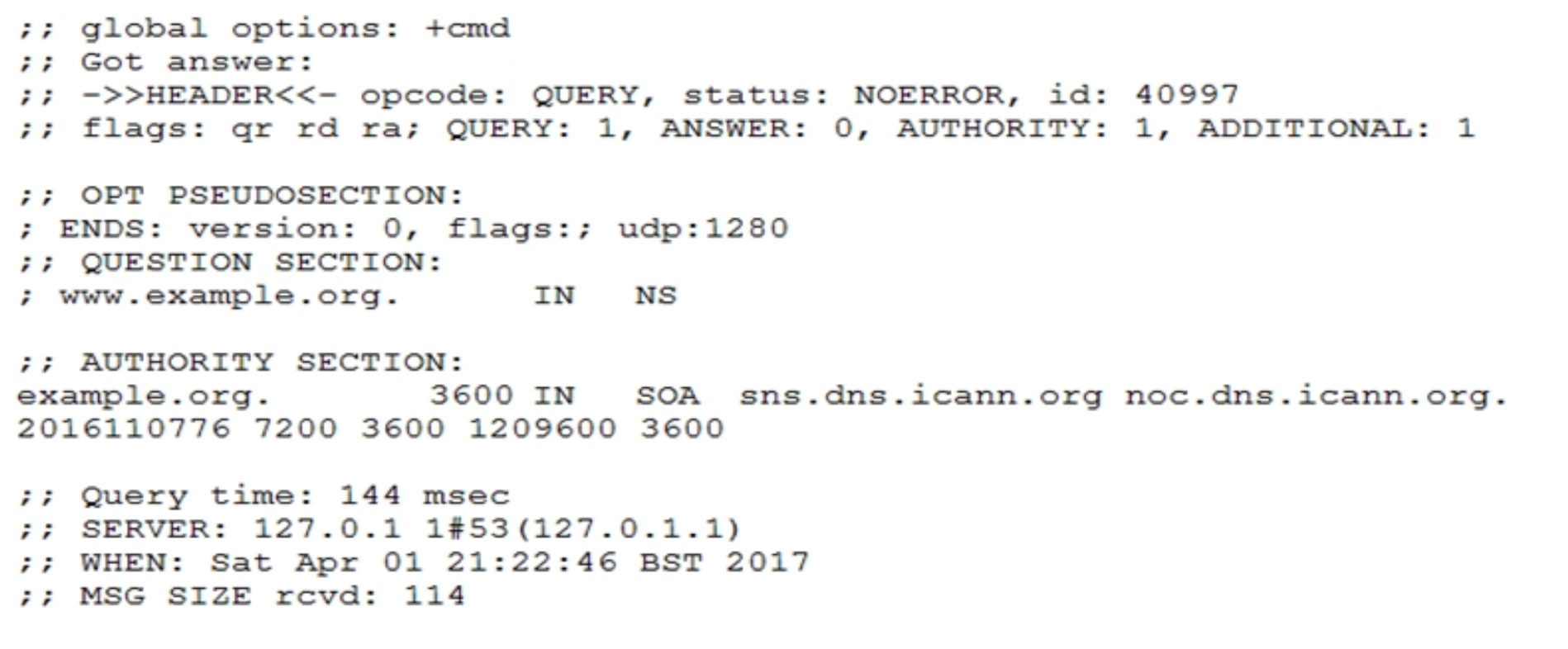
Which of the commands below might have produced the following output?
A. dig -t mx www.example.org
B. dig www.example.org
C. dig -t ns www.example.org
D. dig -t a www.example.org
E. dig -t soa www.example.org
Which command makes the shell variable named VARIABLE visible to subshells?
A. export $VARIABLE
B. env VARIABLE
C. set $VARIABLE
D. set VARIABLE
E. export VARIABLE
After editing the TCP wrapper configuration to grant specific hosts access to a service, when do these changes become effective?
A. The new configuration becomes effective after restarting the respective service.
B. The new configuration becomes effective at the next system reboot.
C. The new configuration becomes effective when the last established connection to the service is closed.
D. The new configuration becomes effective after restarting the tcpd service.
E. The new configuration becomes effective immediately for all new connections.
FILL BLANK - Which command is used to set the hostname of the local system? (Specify only the command without any path or parameters.) hostname
FILL BLANK - What command enables a network interface according to distribution-specific configuration, such as /etc/network/interfaces or /etc/sysconfig/ network-scripts/ifcfg-eth0? (Specify only the command without any path or parameters.)
Which of the following protocols is designed to access the video card output of a virtual machine?
A. KDE
B. X11
C. Xfce
D. SPICE
E. XDMCP
FILL BLANK - Which command is used to sync the hardware clock to the system clock? (Specify only the command without any path or parameters.) hwclock
Which of the following elds can be found in the /etc/group file? (Choose two.)
A. The home directory of the group.
B. The list of users that belong to the group.
C. The name of the group.
D. The default group ACL.
E. The description of the group.
If neither cron.allow nor cron.deny exist in /etc/, which of the following is true?
A. Without additional configuration, all users may create user specific crontabs.
B. Without additional configuration, only root may create user specific crontabs.
C. The cron daemon will refuse to start and report missing files in the system’s log file.
D. When a user creates a user specific crontab the system administrator must approve it explicitly.
E. The default settings of /etc/crond.conf define whether or not user specific crontabs are generally allowed or not.
On a system using systemd-journald, which of the following commands add the message Howdy to the system log? (Choose two.)
A. append Howdy
B. logger Howdy
C. systemd-cat echo Howdy
D. echo Howdy > /dev/journal
E. journalctl add Howdy
Which of the following commands display the number of bytes transmitted and received via the eth0 network interface? (Choose two.)
A. route -v via eth0
B. ip stats show dev eth0
C. netstat -s -i eth0
D. ifconfig eth0
E. ip -s link show eth0
What is true about the file /etc/localtime?
A. It is a plain text file containing a string such as Europe/Berlin
B. It is created and maintained by the NTP service based on the location of the system’s IP address.
C. It is a symlink to /sys/device/clock/ltime and always contains the current local time.
D. After changing this file, newtzconfig has to be run to make the changes effective.
E. It is either a symlink to or a copy of a timezone information file such as /usr/share/zoneinfo/Europe/Berlin.
Access Full 102-500 Dump Free
Looking for even more practice questions? Click here to access the complete 102-500 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our 102-500 dump free questions — and get one step closer to exam success!