101 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the 101 exam? Start with our 101 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a 101 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free 101 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
The Rapid Deployment Policy is used to:A. Improve website performance
B. Quickly protect web sites for most common attacks
C. Improve ASM performance
D. Provide wizard functionality for quick policy creation
A site needs to terminate client HTTPS traffic at the BIG-IP and forward that traffic unencrypted. Which two are profile types that must be associated with such a virtual server? (Choose two.)A. TCP
B. HTTP
C. HTTPS
D. ClientSSL
E. ServerSSL
To share device information with F5 technical support, a customer must either verbally share the information over the phone or copy and send the information in an Email.A. True
B. False
All members of a pool must share the same service port?A. True
B. False
A GTM System would like to ensure that a given LTM System is reachable and iQuery communication is allowed prior to sending it client request. What would be the simplest monitor template to use?A. TCP
B. ICMP
C. HTTP
D. BIG-IP
E. SNMP
You have created a custom profile named TEST2. The parent profile of TEST2 is named TEST1. If additional changes are made to TEST1, what is the effect on
TEST2?A. All changes to TEST1 are propagated to TEST2.
B. Some of the changes to TEST1 may propagate to TEST2.
C. Changes to TEST1 cannot affect TEST2 once TEST2 is saved.
D. When TEST1 is changed, the administrator is prompted and can choose whether to propagate changes to TEST2.
Monitors can be assigned to which three resources? (Choose three.)A. Pools
B. Servers
C. Wide-IPs
D. Data Centers
E. Pool Members
Assume a virtual server is configured with a ClientSSL profile. What would the result be if the virtual server's destination port was not 443?A. SSL termination could not be performed if the virtual server's port was not port 443.
B. Virtual servers with a ClientSSL profile are always configured with a destination port of 443.
C. As long as client traffic was directed to the alternate port, the virtual server would work as intended.
D. Since the virtual server is associated with a ClientSSL profile, it will always process traffic sent to port 443.
Listeners that correspond to nonfloating self IP addresses are stored in which configuration file?A. /config/BIG-IP.conf
B. /config/BIG-IP_base.conf
C. /config/gtm/wideip.conf
D. /config/BIG-IP_local.conf
What occurs when a load command is issued?A. rootBIG-IPsystem[Active][tmos.Itm.pool]#create pooh members add {170.16.20.1:80}
B. rootBIG-IPsystem[Active][tmos.Itm.pool]#create pooh members add {172.16.20.1:80}
C. rootBIG-IPsystem[Active][tmos.Itm.pool]#create pooh members add {172.16.20.1:80{} }
D. rootBIG-IPsystem[Active][tmos.Itm.pool]#create pooh members add {172.16.20.1:80{priority group 2}}
The default staging-tightening period for attack signatures and wildcard entities is?A. 5 days
B. 7 days
C. 10 days
D. 30 days
A BIG-IP has two SNATs, a pool of DNS servers and a virtual server configured to load balance UDP traffic to the DNS servers. One SNAT's address is
64.100.130.10; this SNAT is defined for all addresses. The second SNAT's address is 64.100.130.20; this SNAT is defined for three specific addresses,
172.16.3.54, 172.16.3.55, and 172.16.3.56. The virtual server's destination is 64.100.130.30:53. The SNATs and virtual server have default VLAN associations. If a client with IP address 172.16.3.55 initiates a request to the virtual server, what is the source IP address of the packet as it reaches the chosen DNS server?A. 64.100.130.30
B. 172.16.3.55
C. 64.100.130.20
D. 64.100.130.10
Which of the following statements are correct regarding Attack signatures? (Choose two.)A. Attack signatures can apply to requests, responses, and parameters.
B. Attack signatures are the basis for positive security logic with the BIG-IP ASM System.
C. Any new Attack signature downloaded manually or automatically will be active and assigned directly to the security policy.
D. Individual Attack signatures can be assigned to the security policy. Only Attack signature sets can apply to the security policy.
Which three files/data items are included in a BIG-IP UCS backup file? (Choose three.)A. the BIG-IP administrative addresses
B. the BIG-IP license
C. the BIG-IP log files
D. the BIG-IP default traps
E. the BIG-IP host name
An F5 customer must install WebAccelerator on top of LTM:A. True
B. False
When configuring a Virtual Server to use an iRule with an HTTP_REQUEST event, which lists required steps in a proper order to create all necessary objects?A. create profiles, create the iRule, create required pools, create the Virtual Server
B. create the Virtual Server, create required pools, create the iRule, edit the Virtual Server
C. create a custom HTTP profile, create required pools, create the Virtual Server, create the iRule
D. create required pools, create a custom HTTP profile, create the iRule, create the Virtual Server
A site is load balancing to a pool of web servers. Which statement is true concerning BIG-IP's ability to verify whether the web servers are functioning properly or not?A. Web server monitors can test the content of any page on the server.
B. Web server monitors always verify the contents of the index.html page.
C. Web server monitors can test whether the server's address is reachable, but cannot test a page's content.
D. Web server monitors can test the content of static web pages, but cannot test pages that would require the web server to dynamically build content.
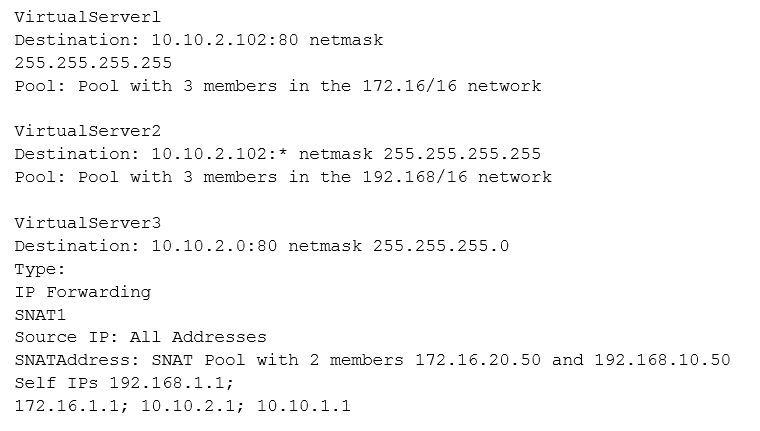
A virtual server is defined per the charts. The last five client connections were to members C, D, A, B, B. Given the conditions shown in the above graphic, if a client with IP address 205.12.45.52 opens a connection to the virtual server, which member will be used for the connection?
A. 172.16.20.1:80
B. 172.16.20.2:80
C. 172.16.20.3:80
D. 172.16.20.4:80
E. 172.16.20.5:80
GTM solves which three of these standard DNS limitations? (Choose three.)A. It can verify that a host is available before resolving a host name for a client.
B. It can use HTTPS for the connection between itself and the client.
C. It can ensure that clients remain at the same data center for stateful applications.
D. It can verify that a client does not have any viruses before sending the IP address.
E. It has more complex load balancing methods.
Which HTTP response code ranges indicate an error condition? (Choose two.)A. 1xx
B. 2xx
C. 3xx
D. 4xx
E. 5xx
A top-level DNS zone uses a CNAME record to point to a sub-zone. Which of the following is an example of a sub-zone?A. www.F5.com/sub
B. www.F5.com
C. www.gslb.F5.com
D. .com
E. f5.com
Which process or system can be monitored by the BIG-IP system and used as a failover trigger in a redundant pair configuration.A. bandwidth utilization
B. duplicate IP address
C. CPU utilization percentage
D. VLAN communication ability
Administrators can configure which three of the following load balancing options in GTM? (Choose three.)A. Alternate
B. Fallback
C. Required
D. Preferred
E. Backup
F. Optional
How do you support non intelligent DNS resolution in an environment with GTM Systems and standard DNS servers? (Choose two.)A. The GTM System must be a secondary server in all of your zones.
B. Your GTM System must delegate some DNS names to the DNS Servers.
C. Your DNS servers may delegate some DNS names to the GTM Systems.
D. The GTM System may have a Listener set for your DNS server's address.
E. The GTM System may have a Listener set for the GTM's loopback address.
What are the two most common methods of placing a BIG-IP device into a network environment? (Choose two.)A. Channeled configuration
B. VLAN configuration
C. NAT configuration
D. SNAT configuration
E. Asymmetric configuration
F. Routed configuration
Which two of the following options can LTM use when all of the pool members are not available or if the pool is overloaded?A. Floating IPs
B. Fallback host
C. Auto last hop
D. SNAT automap
E. Pool offload
F. Priority group activation
WebAccelerator uses three tiers to improve performance. What are the three tiers? (Choose three.)A. Bandwidth offload
B. Client offload
C. Application offload
D. Protocol offload
E. Web server offload
F. Network offload
Which parameters are set to the same value when a pair of BIG-IP devices are synchronized?A. host names
B. system clocks
C. profile definitions
D. VLAN failsafe settings
E. MAC masquerade addresses
Mobile device browsers typically display Web pages more slowly than PC browsers.A. True
B. False
Which three of these software modules can you layer on top of LTM on a BIG-IP device? (Choose three.)A. Web Accelerator
B. APM
C. ARX
D. GTM
E. Firepass
F. Enterprise Manager
What is the expected difference between two source address persistence profiles if profile A has a mask of 255.255.255.0 and profile B has a mask of
255.255.0.0?A. Profile A will have more clients matching existing persistence records.
B. There are no detectable differences.
C. Profile B has a greater potential number of persistence records.
D. Profile B will have fewer persistence records for the sane client base.
A web client accesses a web application using what protocol?A. TCP
B. XML
C. HTML
D. HTTP
Learning suggestions can be the result of:A. A false positive
B. A malicious attack
C. A change in the web site content
D. All the above
APM provides access control lists at which two 051 layersA. Layer 6
B. Layer 5
C. Layer 7
D. Layer 4
E. Layer 3
F. Layer 2
Select the best word or phrase to complete the following sentence.
Using the _______ feature in GTM, F5's Application Delivery Firewall solution can handle a significantly higher number of queries than traditional DNS servers.A. DNS Express
B. BIND
C. Site availability request
D. Location-based routing
Which four of the following statements about LDNS probes are true? (Choose four.)A. Only GTM devices can act as a prober.
B. They check each requesting LDNS that has made a request of the GTM.
C. They can determine available cache size on the client.
D. They are used to develop path metrics.
E. They verify the link between a data center and an LDNS.
F. Probing only takes place if GTM is configured to use dynamic load balancing.
Which three iRule events are likely to be seen in iRules designed to select a pool for load balancing. (Choose 3)A. CLIENT_DATA
B. SERVER_DATA
C. HTTP_REQUEST
D. HTTP_RESPONSE
E. CLIENT_ACCEPTED
F. SERVER_SELECTED
G. SERVER_CONNECTED
The BIG-IP ASM System sets two types of cookies to enforce elements in the security policy. The two types are main and frame cookies. What is the purpose of the frame cookie? (Choose two.)A. Validates domain cookies
B. Detects session expiration
C. Stores dynamic parameters and values
D. Handles dynamic parameter names and flow extractions
Which three of the following must be done in order for GTM to properly communicate LTM? (Choose three.)A. Connect the GTM and LTM with a network crossover cable.
B. Synchronize the big3d versions between GTM and LTM.
C. Add the LTM object to the GTM configuration.
D. Configure the GTM and LTM to we MAC masquerading.
E. Ensure that GTM and LTM use the same floating IP address.
F. Exchange SSL certificates between the two devices.
The following request is sent to the BIG-IP ASM System:
GET http://www.example.local/financials/week1.xls?display=yes&user=john&logon=true
Which of the following components in this requests line represent the query string?A. .xls
B. /week1.xls
C. /financials/week1.xls
D. display=yes&user=john&logon=true
Which three can be a part of a pool's definition? (Choose three.)A. Link
B. Monitors
C. Wide IPs
D. Persistence
E. Data Centers
F. Virtual Servers
What feature of the F5 Exchange solution helps administrators to streamline implementation for added security and granular control?A. iControl
B. Enterprise Manager
C. iApps
D. WebAccelerator
An LTM has the 3 virtual servers, a SNAT, four self IP addresses defined and the networks shown in the exhibit. Selected options for each object are shown below. Settings not shown are at their defaults.
A connection attempt is made with a source IP and port of 10.20.100.50:2222 and a destination IP and port of 10.10.2.102:80.
When the request is processed, what will be the destination IP address?
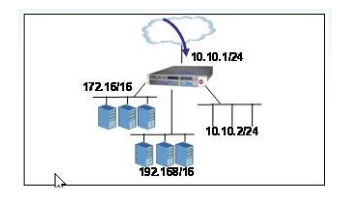
A. Destination IP: 10.10.2.10
B. Destination IP: pool member in the 192.168/16 network.
C. Destination IP: pool member in the 172.16/16 network
D. The request will be dropped.
Using IP Geolocation, an organization can always direct a client request from France to a data enter in Dublin.A. True
B. False
You have a pool of servers that need to be tested. All of the servers but one should be tested every 10 seconds, but one is slower and should only be tested every
20 seconds. How do you proceed?A. It cannot be done. All monitors test every five seconds.
B. It can be done, but will require assigning monitors to each pool member.
C. It cannot be done. All of the members of a pool must be tested at the same frequency.
D. It can be done by assigning one monitor to the pool and a different monitor to the slower pool member.
Could an iRule perform persistence based on a cookie?A. Yes an iRule could be designed to persist based on the contents of a cookie.
B. No. iRules cannot affect persistence.
C. Yes. An iRule could be designed to persist based on the contents of a cookie.
D. No. Cookie persistence is only is based on a cookie persistence profile.
Which of the following are default settings when using the Policy Builder to build a security policy based on the QA lab deployment scenario? (Choose two.)A. All learned entities are placed in staging.
B. Attack signatures are not placed in staging
C. The security policy is placed in blocking mode
D. Tightening is enabled only on file types and parameters.
The SNMP monitor can collect data based on which three metrics? (Choose three.)A. packet rate
B. memory utilization
C. content verification
D. current connections
E. hops along the network path
The ARX is like a mini network manager. It is able to check the health of the environment and can raise alerts when thresholds are reached.A. True
B. False
Why does the F5 Application Delivery Firewall solution mitigate SSL attacks more effectively than any other firewalls?A. Because F5 has unlimited capacity to handle SSL traffic.
B. Because F5 has full visibility and control of SSL traffic.
C. Because F5 has a separate iApp to handle SSL traffic.
D. Because F5 supports large SSL key sizes.
Free Access Full 101 Practice Test Free Questions
If you're looking for more 101 practice test free questions, click here to access the full 101 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 101 certification journey!