101 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 101 certification exam? Start your preparation the smart way with our 101 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 101 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 101 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
When initially configuring the BIG-IP system using the config utility, which two parameters can be set. (Choose two.)
A. the netmask of the SCCP
B. the IP address of the SCCP
C. the port lockdown settings for the SCCP
D. the netmask of the host via the management port
E. the IP address of the host via the management port
F. the port lockdown settings for the host via the management port
The BIG-IP ASM System sets two types of cookies to enforce elements in the security policy. The two types are main and frame cookies. What is the purpose of the frame cookie? (Choose two.)
A. Validates domain cookies
B. Detects session expiration
C. Stores dynamic parameters and values
D. Handles dynamic parameter names and flow extractions
Which action CANNOT be performed by an iRule?
A. Direct a connection request to a specific pool.
B. Substitute a server’s response with alternate data.
C. Chang the virtual server’s default pool.
D. Direct a client’s request to a pool based on the client’s browser’s language.
E. Limit a given client to a set amount of bandwidth.
F. Discard a client before connecting to a server.
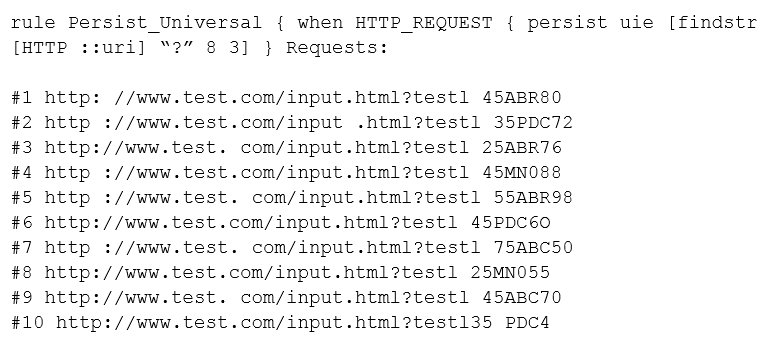
The following iRule is being used within a persistence profile on a virtual server. Assuming the following HTTP requests are made within the same timeout window, what is the maximum number of persistence records that will be created iRule:
A. 4
B. 3
C. 10
D. It cannot be determined from the given data.
E. 5
F. 1
G. 0
One reason APM beats the competition is its ability to perform both user authentication and authorization on a single device.
A. True
B. False
What are two advantages of the Quality of Service (QoS) load balancing method? (Choose two.)
A. It resolves requests to the site with the highest QoS value in the IP header.
B. It combines multiple load balancing metric values in a single load balancing method.
C. It allows the GTM administrator to place relative values on each metric used to determine the optimum site.
D. It allows the GTM System to select the optimum virtual server based on all available path and server metrics.
You need to terminate client SSL traffic at the BIG-IP and also to persist client traffic to the same pool member based on a BIG-IP supplied cookie. Which four are profiles that would normally be included in the virtual server's definition? (Choose four.)
A. TCP
B. HTTP
C. HTTPS
D. ClientSSL
E. ServerSSL
F. CookieBased Persistence
A monitor has been defined using the HTTP monitor template. The send and receive strings were customized, but all other settings were left at their defaults. Which resources can the monitor be assigned to?
A. only specific pool members
B. most virtual severs
C. most nodes
D. most pools
An administrator is planning on solving latency issues by placing the backup data center in a neighboring city to the primary data center. Why isn't this effective solution?
A. It does not provide an acceptable disaster recovery solution.
B. It won’t improve latency between the data centers.
C. It won’t improve the backup time from the primary data center to the backup data center.
D. Users near the data centers will find their connections going back and forth between the two site
E. It costs more to have the data centers close together than further apart.
Which two of the following statements are accurate descriptions of the ARX index? (Choose two.)
A. The ARX index stores the bulk of its data as bit arrays and answers most questions by performing bitwise logical operations on these bitmaps.
B. The ARX index contains the index keys in sorted order, with the leaf level of the index containing the pointer to the page and the row number in the data page.
C. The ARX index is the key enabler of transparent data mobility because the ARX tracks where files reside at all times, from creation through migration and deletion.
D. The ARX index is 100% disposable and can be rebuilt at any point in time without disrupting client or application access to data.
What is the purpose of the GTM Systems Address Exclusion List concerning local DNS servers?
A. to prevent probing of specific local DNSs
B. to prevent name resolution to specific Virtual Servers
C. to prevent name resolution for requests from specific local DNSs
D. to prevent probing of any local DNS servers by specific F5 devices
Which of the following is a language used for content provided by a web server to a web client?
A. FTP
B. TCP
C. HTTP
D. HTML
The following request is sent to the BIG-IP ASM System: GET http://www.example.local/financials/week1.xls?display=yes&user=john&logon=true Which of the following components in this requests line represent the query string?
A. .xls
B. /week1.xls
C. /financials/week1.xls
D. display=yes&user=john&logon=true
FastCache will NOT work with compressed objects.
A. True
B. False
When configuring a Virtual Server to use an iRule with an HTTP_REQUEST event, which lists required steps in a proper order to create all necessary objects?
A. create profiles, create the iRule, create required pools, create the Virtual Server
B. create the Virtual Server, create required pools, create the iRule, edit the Virtual Server
C. create a custom HTTP profile, create required pools, create the Virtual Server, create the iRule
D. create required pools, create a custom HTTP profile, create the iRule, create the Virtual Server
Which three of these scenarios should you identify as being an APM opportunity? (Choose three.)
A. An organization using Novell Netware for authentication.
B. An organization that has been recently fined for failing security compliance.
C. An organization with a traveling sales force.
D. An organization with a single location and no remote employees.
E. An organization that needs to ensure users are using Symantec antivirus software.
F. An organization sharing a public Web site for all Internet users.
Which statement accurately describes the difference between two load balancing modes specified as "member" and "node"?
A. There is no difference; the two terms are referenced for backward compatibility purposes.
B. When the load balancing choice references “node”, priority group activation is unavailable.
C. Load balancing options referencing “nodes” are available only when the pool members are defined for the “any” port.
D. When the load balancing choice references “node”, the addresses’ parameters are used to make the load balancing choice rather than the member’s parameters.
Over the years, F5 has led the industry in which of the four following areas? (Choose three.)
A. Security
B. Acceleration
C. Application availability
D. Application scalability
E. Application design
F. Remote access
Which three of the following must be done in order for GTM to properly communicate LTM? (Choose three.)
A. Connect the GTM and LTM with a network crossover cable.
B. Synchronize the big3d versions between GTM and LTM.
C. Add the LTM object to the GTM configuration.
D. Configure the GTM and LTM to we MAC masquerading.
E. Ensure that GTM and LTM use the same floating IP address.
F. Exchange SSL certificates between the two devices.
Which HTTP response code ranges indicate an error condition? (Choose two.)
A. 1xx
B. 2xx
C. 3xx
D. 4xx
E. 5xx
TMOS is an F5 software module that runs on the BIG-IP platform.
A. True
B. False
A site has six members in a pool. All of the servers have been designed, built, and configured with the same applications. It is known that each client's interactions vary significantly and can affect the performance of the servers. If traffic should be sent to all members on a regular basis, which load balancing mode is most effective if the goal is to maintain a relatively even load across all servers.
A. Ratio
B. Priority
C. Observed
D. Round Robin
The APM Dashboard enables administrators to monitor which two of these metrics? (Choose two.)
A. Number of active sessions
B. Number of new sessions
C. Number of denied users
D. Number of users from each country
With standard DNS, assuming no DNS request failures, which process describes the normal resolution process on a "first time" DNS request?
A. Client requests address from root server, root server returns IP address to Authoritative DNS, Authoritative DNS returns requested IP address, LDNS returns requested IP address to client.
B. Client requests address from LDNS, LDNS requests from GTM, GTM requests from Authoritative DNS, Authoritative DNS returns requested IP address, LDNS returns requested IP address to client.
C. Client requests address from LDNS, Authoritative DNS receives request from root server, root server returns LDNS address, LDNS returns client address, Authoritative DNS returns requested IP address, LDNS returns requested IP address to client.
D. Client requests address from LDNS, LDNS requests from root server, root server returns Authoritative DNS address, LDNS requests from Authoritative DNS, Authoritative DNS returns requested IP address, LDNS returns requested IP address to client.
Which of the following is NOT a profile type on the BIG-IP?
A. Protocol
B. Application
C. Persistence
D. Authentication
E. SSL
What will likely happen if you were to define a LTM System in the wrong Data Center?
A. There would be no effect if the LTM System is defined in the wrong Data Center.
B. The GTM System would not be able to communicate with that LTM System.
C. Data from probes from that LTM System might result in inaccurate path metrics and load balancing decisions.
D. The GTM System would not be able to resolve Wide-IPs to the addresses associated with that LTM System’s Virtual Servers.
A site has six members in a pool. Three of the servers are new and have more memory and a faster processor than the others. Assuming all other factors are equal and traffic should be sent to all members, which two load balancing methods are most appropriate? (Choose two.)
A. Ratio
B. Priority
C. Observed
D. Round Robin
When configuring monitors for individual pool members, which three options can be selected? (Choose three.)
A. inherit the pool’s monitor
B. choose a default monitor
C. inherit the Wide-IP’s monitor
D. assign a monitor to the specific pool member
E. do not assign any monitor to the specific pool member
The PCI compliance report is proof that a company is secure.
A. True
B. False
Which of these statements about a stream profile is false?
A. It is applied to an HTTP class profile.
B. It is not recommended for telnet traffic.
C. It can replace one data string for another for all traffic going through a virtual server.
D. It applies to both inbound and outbound traffic.
E. It will not inspect HTTP headers when an HTTP profile is present.
Which of the following is NOT a logging option within an APM access control entry?
A. Packet
B. Verbose
C. Nominal
D. Summary
E. None
Which of the following is a client-side action in the Visual Policy Editor that prevents external access and deletes any files created during a secure access session?
A. Windows Group Policy
B. Resource Assign
C. Protected Workspace
D. Virtual Keyboard
E. Browser Cache and Session Control
In the next few years, 75% of new storage capacity will shift to unstructured data (also known as file data). Which two of the following are examples of unstructured data? (Choose two.)
A. CAD drawings
B. Location data in a GIS (geographic information system)
C. Customer records and product records in a CRM (customer relationship management) database
D. Microsoft Office and PDF documents
Which three parameters could be used to determine whether a connection request will have the source address translated as the request is processed? (Choose three.)
A. the client’s router’s IP address
B. the client’s browser’s preferred language
C. the client’s IP netmask
D. the client’s TCP port
E. the client’s IP address
F. the client IP fragment offset
The least connections load balancing method functions best when all pool members share similar characteristics.
A. True
B. False
Using file virtualization, what can the ARX do for customers?
A. Match data to the most appropriate tier of storage (e.g. critical data on tier 1 storage; older data on secondary storage tier).
B. All of the above.
C. Move individual files or entire file systems in real-time without disruption of down-time.
D. Automate many storage management tasks such as storage tiering, dynamic capacity balancing, and no disruptive data migration.
A security audit has determined that your web application is vulnerable to a cross site scripting attack. Which of the following measures are appropriate when building a security policy? (Choose two.)
A. Cookie length must be restricted to 1024 bytes.
B. Attack signature sets must be applied to any user input parameters.
C. Parameter data entered for explicit objects must be checked for minimum and maximum values.
D. Parameter data entered for flow level parameters must allow some metacharacters but not others.
A standard virtual server is defined with a pool and a SNAT using automap. All other settings for the virtual server are at defaults. When client traffic is processed by the BIG-IP, what will occur to the IP addresses?
A. Traffic initiated by the pool members will have the source address translated to a self-IP address but the destination address will not be changed.
B. Traffic initiated to the virtual server will have the destination address translated to a pool member address and the source address. Traffic initiated to the virtual server will have the destination address translated to a pool member. address and the source address translated to a self-IP address.
C. Traffic initiated by selected clients, based on their IP address, will have the source address translated to a self-IP address but the destination will only be translated if the traffic is destined to the virtual server.
D. Traffic initiated to the virtual server will have the destination address translated to a pool member address and the source address. Traffic initiated to the virtual server will have the destination address translated to a pool member. address and the source address translated to a self-IP address. Traffic arriving destined to other destinations will have the source translated to a self-IP address only.
Which of the following methods of protection operates on server responses?
A. Dynamic parameter protection
B. Response code validation and response scrubbing
C. Response code validation and HTTP method validation
D. HTTP RFC compliancy check and metacharacter enforcement
Which four of the following statements about LDNS probes are true? (Choose four.)
A. Only GTM devices can act as a prober.
B. They check each requesting LDNS that has made a request of the GTM.
C. They can determine available cache size on the client.
D. They are used to develop path metrics.
E. They verify the link between a data center and an LDNS.
F. Probing only takes place if GTM is configured to use dynamic load balancing.
Listeners that correspond to nonfloating self IP addresses are stored in which configuration file?
A. /config/BIG-IP.conf
B. /config/BIG-IP_base.conf
C. /config/gtm/wideip.conf
D. /config/BIG-IP_local.conf
Which two processes are involved when BIG-IP systems issue traps? (Choose two.)
A. bigd
B. alertd
C. smtpd
D. syslogng
A virtual server is listening at 10.10.1.100:any and has the following iRule associated with it:If a user connects to 10.10.1.100 and port 22, which pool will receive the request?
A. ftp pool
B. telnet pool
C. None. The request will be dropped.
D. Unknown. The pool cannot be determined from the information provided.
Which statement is true regarding OneConnect processing?
A. The virtual server must have UDP profile.
B. Server-side request can utilize existing client-side connections.
C. The number of client connection is reduced.
D. Client-side request can utilize existing server-side connections.
Using IP Geolocation, an organization can always direct a client request from France to a datacenter in Dublin.
A. True
B. False
Application templates save the time it typically takes to create nodes, pools, pool members, virtual servers, and monitors.
A. True
B. False
Which four are GTM server static load balancing modes? (Choose four.)
A. Return to DNS
B. CPU
C. Packet Rate
D. Drop Packet
E. Round Robin
F. Static Persist
Which two of the following LTM load balancing methods require the least amount of resources? (Choose two.)
A. Round robin
B. Ratio
C. Observed
D. Fastest
E. Predictive
F. Least connections
Which of the following business benefits does storage tiering offer to customers?
A. Reduces time for backups because data on the secondary tier can have a less time intensive backup policed applied to it.
B. All of the above.
C. Enables customers to apply a more aggressive RTO/RPO for business critical Tier-1 unstructured data.
D. Reduces money spent on storage since the majority of data can be moved to less expensive secondary tier storage.
Which of the following are the three main business drivers for placing LTM into a network? (Choose three.)
A. Secure the connection between WAN sites.
B. Improve application availability and scalability.
C. Authenticate and authorize users.
D. Boost application performance.
E. Include application security.
F. Act as a Web application firewall
Access Full 101 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 101 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 101 mock test free today—and take a major step toward exam success!