101 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the 101 certification? Our 101 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective 101 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic 101 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
How is persistence configured?
A. Persistence is an option within each pool’s definition.
B. Persistence is a profile type; an appropriate profile is created and associated with virtual server.
C. Persistence is a global setting; once enabled, load balancing choices are superseded by the persistence method that is specified.
D. Persistence is an option for each pool member. When a pool is defined, each member’s definition includes the option for persistence.
What is the purpose of floating self-IP addresses?
A. to define an address that grants administrative access to either system at any time
B. to define an address that allows either system to initiate communication at any time
C. to define an address that allows network devices to route traffic via a single IP address
D. to define an address that gives network devices greater flexibility in choosing a path to forward traffic
How is traffic flow through transparent virtual servers different from typical virtual servers? (Choose two.)
A. any text string within a cookie
B. any bytes within the initial client request packet
C. an IP address
D. the value in the tcp acknowledgement field
IP Enforcer blocks IP addresses that have repeatedly and regularly attacked the site.
A. True
B. False
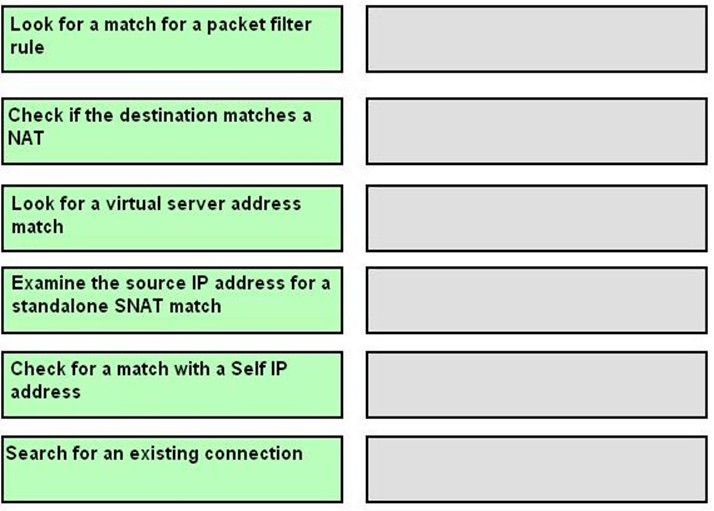
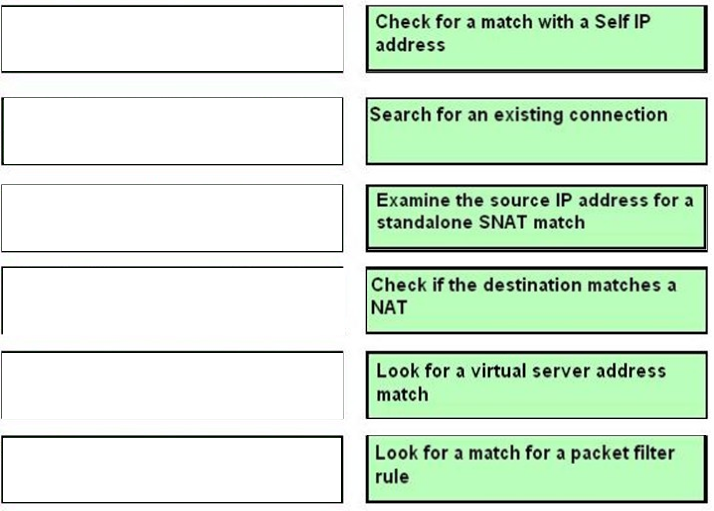
DRAG DROP - Place the following items in the order that the BIG-IP device uses when processing a packet. Select and Place:
Listeners that correspond to nonfloating self IP addresses are stored in which configuration file?
A. /config/BIG-IP.conf
B. /config/BIG-IP_base.conf
C. /config/gtm/wideip.conf
D. /config/BIG-IP_local.conf
Assuming there are open connections through an active system's virtual servers and a failover occurs, by default, what happens to the connections?
A. All open connections are lost.
B. All open connections are maintained.
C. When persistence mirroring is enabled, open connections are maintained even if a failover occurs.
D. Long-lived connections such as Telnet and FTP are maintained, but short-lived connections such as HTTP are lost.
E. All open connections are lost, but new connections are initiated by the newly active BIG-IP, resulting in minimal client downtime.
Which three of these file types work well with HTTP compression? (Choose three.)
A. MP4 videos
B. Digital photos
C. Text files
D. Static HTML Web pages
E. CD quality songs
F. Microsoft Word documents
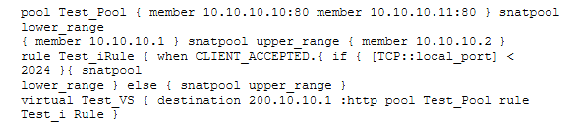
The partial configuration below includes an iRule, a virtual server, and pools. When traffic from the client at 160.10.10.10:2056 connects to the virtual server Test_VS and sends an HTTP request, what will the client's source address be translated to as the traffic is sent to the chosen pool member?
A. 160.10.10.IOC.160.10.10.10
B. It could be either 10.10.10.10 or 10.10.10.11.
C. 10.10.10.2
D. 200.10.10.1
E. 10.10.10.1
True or False, WOM speeds up large file data transfer across the WAN between a Windows client and a Windows file Server.
A. True
B. False
Which statement is correct if a TOP-based monitor is assigned to an LTM System and an HTTP-based monitor is assigned to one of that LTM System's Virtual Servers?
A. The Virtual Server status is based on the TCP monitor only.
B. The Virtual Server status is based on the HTTP monitor only.
C. GTM Systems do not allow monitors on both an LTM System and one of its Virtual Servers.
D. The Virtual Server status is based on both the TOP and HTTP monitor; if either fails, the Virtual Server is unavailable.
E. The Virtual Server status is based on both the TOP and HTTP monitor; if either succeeds, the Virtual Server is available.
Which aspect of F5's Intelligent Services Platform helps you extend your security conversation to include F5professionals and customers?
A. Modular Functionality
B. iApps
C. TMOS
D. DevCentral
The Policy Builder benefits include:
A. Doesn’t require in depth web application knowledge
B. Only requires limited ASM knowledge
C. All of the above
D. Very low administrative impact
An HTTP class is available -
A. on any BIG-IP LTM system
B. only when ASM is licensed.
C. only when ASM or WA are licensed.
D. only when a specific license key is required.
Which of the following is NOT a benefit of using SSL offload?
A. It increases the bandwidth between the client and LTM.
B. It enables LTM to decrypt traffic, examine the payload, and then re-encrypt before sending it to a pool member.
C. The organization requires far less SSL certificates.
D. The CPU processing load on backend servers is reduced.
E. It enables iRules to be used on traffic arriving to LTM that is encrypted.
The ARX saves customers time, money and frustration through a stub-based system that makes a slight modification to each file in order to more efficiently sort and store end user data.
A. True
B. False
In the following configuration, a virtual server has the following HTTP class configuration:A request arriving for WWW.F5.COM will be matched by which class(es)?
A. Class 1
B. Class 2
C. Both Class 1 and Class 2
D. The request will be dropped
Which two can be a part of a pool's definition? (Choose two.)
A. rule(s)
B. profile(s)
C. monitor(s)
D. persistence type
E. load balancing mode
Which three can be a part of a pool's definition? (Choose three.)
A. Link
B. Monitors
C. Wide IPs
D. Persistence
E. Data Centers
F. Virtual Servers
What occurs when a load command is issued?
A. rootBIG-IPsystem[Active][tmos.Itm.pool]#create pooh members add {170.16.20.1:80}
B. rootBIG-IPsystem[Active][tmos.Itm.pool]#create pooh members add {172.16.20.1:80}
C. rootBIG-IPsystem[Active][tmos.Itm.pool]#create pooh members add {172.16.20.1:80{} }
D. rootBIG-IPsystem[Active][tmos.Itm.pool]#create pooh members add {172.16.20.1:80{priority group 2}}
Which of the following can be accomplished using iRules?
A. Track inbound and outbound traffic
B. Perform deep packet inspection
C. Inspect traffic and drop it
D. All of the above
E. Intercept traffic and redirect it
Replicating a large database between sites could take several hours without WOM, and only several minutes with WOM.
A. True
B. False
When using the setup utility to configure a redundant pair, you are asked to provide a "Failover Peer IP". Which address is this?
A. an address of the other system in its management network
B. an address of the other system in a redundant pair configuration
C. an address on the current system used to listen for failover messages from the partner BIG-IP
D. an address on the current system used to initiate mirroring and network failover heartbeat messages
Which is NOT a function of ASM?
A. Attack signature enforcement
B. HTTP protocol enforcement
C. Network security
D. Parameter value enforcement
Which of the following methods of protection are used by the BIG-IP ASM System to mitigate buffer overflow attacks?
A. HTTP RFC compliancy checks
B. Length restrictions and attack signatures
C. Length restrictions and site cookie compliancy checks
D. Metacharacter enforcement and HTTP RFC compliancy check
FILL BLANK - GTM uses the F5 ___________ protocol to synchronize performance metrics between GTM devices. (Fill in)
A site needs to terminate client HTTPS traffic at the BIG-IP and forward that traffic unencrypted. Which two are profile types that must be associated with such a virtual server? (Choose two.)
A. TCP
B. HTTP
C. HTTPS
D. ClientSSL
E. ServerSSL
ASM provides antivirus protection by:
A. Extracting files being uploaded and sending them to an AV system via ICAP
B. Running a local antivirus program on the BIG-IP
C. None of the above
D. Using IP Penalty enforcement to block requests from hackers IPs
When configuring a Virtual Server to use an iRule with an HTTP_REQUEST event, which lists required steps in a proper order to create all necessary objects?
A. create profiles, create the iRule, create required pools, create the Virtual Server
B. create the Virtual Server, create required pools, create the iRule, edit the Virtual Server
C. create a custom HTTP profile, create required pools, create the Virtual Server, create the iRule
D. create required pools, create a custom HTTP profile, create the iRule, create the Virtual Server
Which three of the following are unique differentiators for F5 in the marketplace? (Choose three.)
A. VLANs
B. Load-balancing pools
C. Secure remote access
D. TMOS
E. OneConnect
F. iRules
In the current version of BIG-IP, what happens if the GTM does not find a wide IP that matches the DNS request?
A. It sends a broadcast request to all GTM devices.
B. It uses iQuery to request the information from LTM.
C. It sends a request to its configured backup GTM device.
D. It sends an un-resolvable error to the client.
E. It sends the request to an external DNS.
Which three of the following must be done in order for GTM to properly communicate LTM? (Choose three.)
A. Connect the GTM and LTM with a network crossover cable.
B. Synchronize the big3d versions between GTM and LTM.
C. Add the LTM object to the GTM configuration.
D. Configure the GTM and LTM to we MAC masquerading.
E. Ensure that GTM and LTM use the same floating IP address.
F. Exchange SSL certificates between the two devices.
To function properly, an Enterprise Manager device is required within each data center.
A. True
B. False
Administrators can specify an APM access profile when defining a virtual server in LTM.
A. True
B. False
Which of the following are default settings when using the Policy Builder to build a security policy based on the QA lab deployment scenario? (Choose two.)
A. All learned entities are placed in staging.
B. Attack signatures are not placed in staging
C. The security policy is placed in blocking mode
D. Tightening is enabled only on file types and parameters.
LTM can only load balance outbound traffic by using iRules
A. True
B. False
A standard virtual server is defined with a pool and a SNAT using automap. All other settings for the virtual server are at defaults. When client traffic is processed by the BIG-IP, what will occur to the IP addresses?
A. Traffic initiated by the pool members will have the source address translated to a self-IP address but the destination address will not be changed.
B. Traffic initiated to the virtual server will have the destination address translated to a pool member address and the source address. Traffic initiated to the virtual server will have the destination address translated to a pool member. address and the source address translated to a self-IP address.
C. Traffic initiated by selected clients, based on their IP address, will have the source address translated to a self-IP address but the destination will only be translated if the traffic is destined to the virtual server.
D. Traffic initiated to the virtual server will have the destination address translated to a pool member address and the source address. Traffic initiated to the virtual server will have the destination address translated to a pool member. address and the source address translated to a self-IP address. Traffic arriving destined to other destinations will have the source translated to a self-IP address only.
Which of the following is correct regarding User-defined Attack signatures?
A. User-defined signatures use an F5-supplied syntax
B. User-defined signatures may only use regular expressions
C. Attack signatures may be grouped within system-supplied signatures
D. User-defined signatures may not be applied globally within the entire policy
Which of the following are properties of an ASM logging profile? (Choose three.)
A. storage type
B. storage filter
C. storage policy
D. web application
Which process or system can be monitored by the BIG-IP system and used as a failover trigger in a redundant pair configuration.
A. bandwidth utilization
B. duplicate IP address
C. CPU utilization percentage
D. VLAN communication ability
With standard DNS, assuming no DNS request failures, which process describes the normal resolution process on a "first time" DNS request?
A. Client requests address from root server, root server returns IP address to Authoritative DNS, Authoritative DNS returns requested IP address, LDNS returns requested IP address to client.
B. Client requests address from LDNS, LDNS requests from GTM, GTM requests from Authoritative DNS, Authoritative DNS returns requested IP address, LDNS returns requested IP address to client.
C. Client requests address from LDNS, Authoritative DNS receives request from root server, root server returns LDNS address, LDNS returns client address, Authoritative DNS returns requested IP address, LDNS returns requested IP address to client.
D. Client requests address from LDNS, LDNS requests from root server, root server returns Authoritative DNS address, LDNS requests from Authoritative DNS, Authoritative DNS returns requested IP address, LDNS returns requested IP address to client.
A GTM System would like to ensure that a given LTM System is reachable and iQuery communication is allowed prior to sending it client request. What would be the simplest monitor template to use?
A. TCP
B. ICMP
C. HTTP
D. BIG-IP
E. SNMP
Which action will take place when a failover trigger is detected by the active system?
A. The active device will take the action specified for the failure.
B. The standby device also detects the failure and assumes the active role.
C. The active device will wait for all connections to terminate and then failover.
D. The standby device will begin processing virtual servers that have failed, but the active device will continue servicing the functional virtual servers.
If the BIG-IP device is NOT always located between the client and the server, it will NOT provide full optimization and security.
A. True
B. False
Which four of the following items are physical objects used by GTM?
A. Virtual servers
B. Links
C. Servers
D. Wide IPs
E. Data centers
F. Pools
Which of the following statements about cookie persistence is NOT true?
A. The cookie’s timeout value can be customized.
B. They are F5’spreferred persistence method.
C. No persistence information is placed on LTM.
D. Web servers must be configured to send cookies to clients.
E. They do not add a performance impact on LTM.
Which of the following statements about Web server offload is NOT true?
A. It performs rate shaping to reduce overflow.
B. It forces the client browser to use multiple connections streams.
C. It uses OneConnect to reduce multiple TCP connections.
D. It utilizes cached content to prevent unnecessary trips for the same content.
E. It uses specialized hardware for SSL offload.
On a BIG-IP ASM 3600, in standalone mode, which of the following pool configurations is valid?
A. Pool named vs_pool with 1 pool member, no persistence, and no load balancing method
B. Pool named vs_pool with 1 pool member, cookie persistence, and ratio load balancing method
C. Pool named vs_pool with 2 pool members, cookie persistence, and ratio load balancing method
D. Pool named vs_pool with 3 pool members, source IP persistence, and least connections load balancing method
GTM can load balance to LTM in addition to non-BIG-IP hosts.
A. True
B. False
The following request is sent to the BIG-IP ASM System: GET http://www.example.local/financials/week1.xls?display=yes&user=john&logon=true Which of the following components in this requests line represent the query string?
A. .xls
B. /week1.xls
C. /financials/week1.xls
D. display=yes&user=john&logon=true
Access Full 101 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of 101 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your 101 certification journey!