101 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your 101 certification? Our 101 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an 101 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our 101 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
How is persistence configured?
A. Persistence is an option within each pool’s definition.
B. Persistence is a profile type; an appropriate profile is created and associated with virtual server.
C. Persistence is a global setting; once enabled, load balancing choices are superceded by the persistence method that is specified.
D. Persistence is an option for each pool member. When a pool is defined, each member’s definition includes the option for persistence.
Which statement is true regarding failover?
A. Hardware failover is disabled by default.
B. Hardware failover can be used in conjunction with network failover.
C. If the hardware failover cable is disconnected, both BIG-IP devices will always assume the active role.
D. By default, hardware failover detects voltage across the failover cable and monitors traffic across the internal VLAN.
Which three statements are true about SNATs? (Choose three.)
A. SNAT s provide bidirectional traffic initiation.
B. SNAT s support UDP, TCP, and ICMP traffic.
C. SNAT s provide a many-to-one mapping between IP addresses.
D. SNAT addresses can be identical to virtual server IP addresses.
Which two of the following are costs businesses may face in dealing with unstructured data? (Choose two.)
A. Lost productivity due to server downtime
B. Buying backup media
C. Buying additional storage capacity
D. Paying to convert unstructured data into structured data
Select the two best questions you would use to ask your customer about their current web access management solution. Select two.
A. What impact are slow remote access connections having on productivity?
B. Are you using Google multi-factor authentication?
C. Is user authentication data sitting on partner systems outside your control?
D. Have you standardized on Androids or iPhones?
E. How are you planning to extend Exchange to your mobile users?
F. How do you think a global remote access deployment with integrated acceleration and availability services might benefit your business?
Which three parameters can be specified within the Setup Utility? (Choose three.)
A. password of the “root” user
B. IP address of an NTP server
C. IP address of an initial Wide-IP
D. IP address restrictions for SSH access
E. all necessary administrative IP addresses (including floating addresses)
The current status of a given pool is offline (red). Which condition could explain that state? Assume the descriptions below include all monitors assigned for each scenario.
A. No monitors are currently assigned to any pool, member or node.
B. The pool has a monitor assigned to it, and none of the pool members passed the test. The pool has a monitor assigned to it, and none of the pool members passed the test.
C. The pool has a monitor assigned to it, and only some of the pool’s members passed the test.
D. A monitor is assigned to all nodes and all nodes have passed the test. The pool’s members have no specific monitor assigned to them.
When configuring a Virtual Server to use an iRule with an HTTP_REQUEST event, which lists required steps in a proper order to create all necessary objects?
A. create profiles, create the iRule, create required pools, create the Virtual Server
B. create the Virtual Server, create required pools, create the iRule, edit the Virtual Server
C. create a custom HTTP profile, create required pools, create the Virtual Server, create the iRule
D. create required pools, create a custom HTTP profile, create the iRule, create the Virtual Server
Which cookie persistence method requires the fewest configuration changes on the web servers to be implemented correctly?
A. insert
B. rewrite
C. passive
D. session
Which of the following does not pertain to protecting the Requested Resource (URI) element?
A. File type validation
B. URL name validation
C. Domain cookie validation
D. Attack signature validation
Which two daemons only run after the entire license process has been completed? (Choose two.)
A. zrd
B. tmm
C. ntpd
D. gtmd
Which of the following statements best describes the ARX architecture?
A. The ARX’s split path architecture has a data path that handles the most common operations, and a control path that handles other operations requiring deeper inspection and updating of the index.
B. The ARX’s architecture has redundancy built in, allowing a single ARX to be deployed in most use cases which provides a huge cost savings to customers.
C. All of the above.
D. It is a software agent that installs on the storage device.
TCP Express enables LTM to use different TCP settings for the connection between the client and LTM, and the connection between LTM and the pool member.
A. True
B. False
What is the difference between primary and secondary DNS servers?
A. Only primary servers can issue authoritative responses.
B. Primary servers host the original copy of the zone database file.
C. Primary servers resolve names more efficiently than secondary servers.
D. Secondary servers act as backups and will respond only if the primary fails.
A BIG-IP has two SNATs, a pool of DNS servers and a virtual server configured to load balance UDP traffic to the DNS servers. One SNAT's address is 64.100.130.10; this SNAT is defined for all addresses. The second SNAT's address is 64.100.130.20; this SNAT is defined for three specific addresses, 172.16.3.54, 172.16.3.55, and 172.16.3.56. The virtual server's destination is 64.100.130.30:53. The SNATs and virtual server have default VLAN associations. If a client with IP address 172.16.3.55 initiates a request to the virtual server, what is the source IP address of the packet as it reaches the chosen DNS server?
A. 64.100.130.30
B. 172.16.3.55
C. 64.100.130.20
D. 64.100.130.10
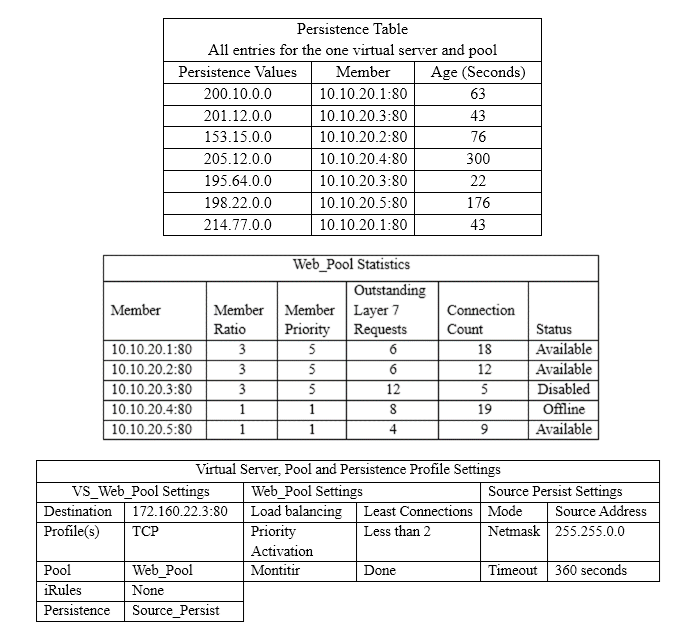
Given the configuration shown below, if a connection request arrived on the BIG-IP with a source address of 200.10.10.10:1050 and a destination of
150.10.10.75:80, what would the source IP address of the associated packet be when it arrived on the choosen member of the web_pool self 150.10.10.1
{ netmask 255.255.255.0 unit I floating enable vlan external allow tcp https } self 10.10.1.1 { netmask 255.255.255.0 unit I floating enable vlan internal allow default
} pool web_pool { member 10.10.1.11:80 member 10.10.1.12:80 member 10.10.1.13:80 }snatpool client_pool { member 10.10.1.100 member 150.10.10.15 }virtual
VS_web { destination 150.10.10.10:80 ip protocol tcp snat automap pool web_pool }virtual VS_network{ destination 150.10.1 0.0:any mask 255.255.255.0 snatpool client_pool ip protocol tcp pool web_pool } virtual VS_network { destination 150.10.1 0.0:any mask 255.255.255.0 snatpool client_pool ip protocol tcp pool web_pool } virtual VS_network { destination 150.10.10.0:any mask 255.255.255.0 snatpool client_pool ip protocol tcp pool web_pool }
A. 10.10.1.IA.10.10.1.1
B. 200.10.10.I0D.200.10.10.10
C. 10.10.1.I00B.10.10.1.100
D. 150.10.10.15C.150.10.10.15
Which of the following is not a configurable parameter data type?
A. Email
B. Array
C. Binary
D. Decimal
When can a single virtual server be associated with multiple profiles?
A. Never. Each virtual server has a maximum of one profile.
B. Often. Profiles work on different layers and combining profiles is common.
C. Rarely. One combination, using both the TCP and HTTP profile does occur, but it is the exception.
D. Unlimited. Profiles can work together in any combination to ensure that all traffic types are supported in a given virtual server.
When DNS_REV is used as the probe protocol by the GTM System, which information is expected in the response from the probe?
A. a reverse name lookup of the GTM System
B. the list of root servers known by the local DNS
C. the FQDN of the local DNS being probed for metric information
D. the revision number of BIND running on the requesting DNS server
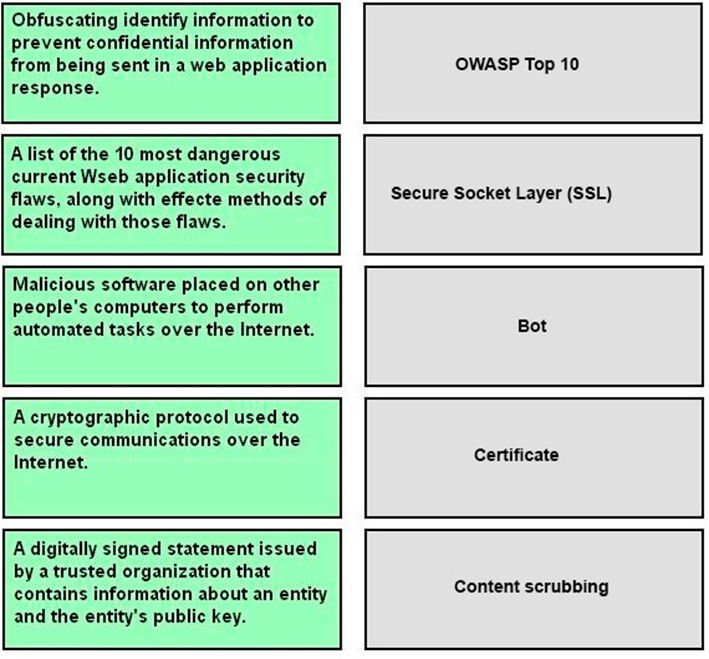
DRAG DROP - Match the security-related term with the correct definition. 1. OWASP Top 10 2. Secure Socket Layer (SSL) 3. Bot 4. Certificate 5. Content scrubbing Select and Place:
To make complex access policies easier to manage, an administrator can create a _______ containing several policy actions, and then add instances of it within the policy? (Fill in)
A. Visual Policy Editor
B. Policy Editor
C. Visual Editor
D. Policy creator
LTM runs on______F5's proprietary product platform. (Fill in the correct answer)
A. ARX
B. Firepass
C. Acopia
D. TMOS
IP Enforcer blocks IP addresses that have repeatedly and regularly attacked the site.
A. True
B. False
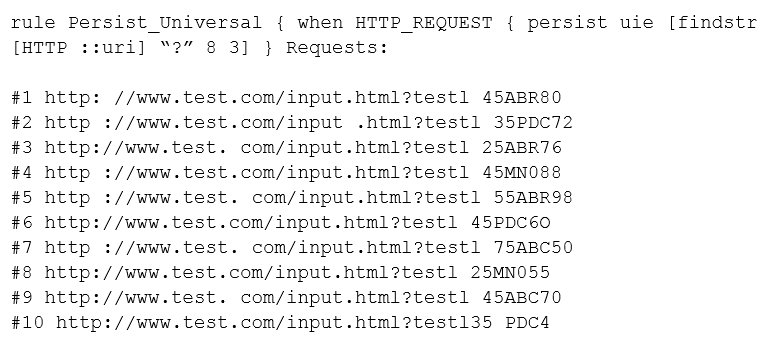
The following iRule is being used within a persistence profile on a virtual server. Assuming the following HTTP requests are made within the same timeout window, what is the maximum number of persistence records that will be created iRule:
A. 4
B. 3
C. 10
D. It cannot be determined from the given data.
E. 5
F. 1
G. 0
Which of the following are the three main business drivers for placing LTM into a network? (Choose three.)
A. Secure the connection between WAN sites.
B. Improve application availability and scalability.
C. Authenticate and authorize users.
D. Boost application performance.
E. Include application security.
F. Act as a Web application firewall
Which of the following does NOT describe network performance management?
A. Updating software on various devices
B. Seeing graphs in near real-time
C. Visibility into multiple network devices
D. Being alerted to an issue as it happens
E. Viewing virtual server statistics
In the current version of BIG-IP, what happens if the GTM does not find a wide IP that matches the DNS request?
A. It sends a broadcast request to all GTM devices.
B. It uses iQuery to request the information from LTM.
C. It sends a request to its configured backup GTM device.
D. It sends an un-resolvable error to the client.
E. It sends the request to an external DNS.
Which four of these scenarios will benefit from F5's WAN Optimization Module? (Choose four.)
A. An international organization with data centers in different countries.
B. An organization that does not want to rely on using tape backup.
C. An organization with one site but hundreds of Web servers.
D. An organization whose users create extremely large files.
E. An organization that expects their Web site usage to double in the next year.
F. An organization attempting to lower costs by reducing the number of data centers.
GTM solves which three of these standard DNS limitations? (Choose three.)
A. It can verify that a host is available before resolving a host name for a client.
B. It can use HTTPS for the connection between itself and the client.
C. It can ensure that clients remain at the same data center for stateful applications.
D. It can verify that a client does not have any viruses before sending the IP address.
E. It has more complex load balancing methods.
Using IP Geolocation, an organization can always direct a client request from France to a data enter in Dublin.
A. True
B. False
Which two statements are true concerning capabilities of current BIG-IP platforms? (Choose two.)
A. The 1600 hosts more ports than the 3900.
B. All current BIG-IP platform use both an ASIC. And CPU(s)to process traffic.
C. All current BIG-IP platform can perform hardware compression.
D. Only 2U BIG-IP Platform have an option of a second power supply.
E. All BIG-IP have capacity to perform bulk encryption I decryption of SSL traffic independent of the CPU.
As a part of the Setup Utility, the administrator sets the host name for the BIG-IP. What would be the result if the two systems in a redundant pair were set to the same host name?
A. Host names do not matter in redundant pair communication.
B. In a redundant pair, the two systems will always have the same host name. The parameter is synchronized between the systems.
C. The first time the systems are synchronized the receiving system will be assigned the same self-IP addresses as the source system.
D. When the administrator attempts to access the configuration utility using the host name, they will always connect to the active system.
Although not all modules run on all platforms, each F5 hardware platform can run LTM plus at least one additional software module.
A. True
B. False
The ARX saves customers time, money and frustration through a stub-based system that makes a slight modification to each file in order to more efficiently sort and store end user data.
A. True
B. False
Learning suggestions can be the result of:
A. A false positive
B. A malicious attack
C. A change in the web site content
D. All the above
Which item is NOT a function of ASM?
A. Provides authentication and authorization services
B. Logs and reports full HTTP messages
C. Provides comprehensive Web application security
D. Provides application level performance information
Which two statements are true about SNATs? (Choose two.)
A. SNATs are enabled on all VLANs, by default.
B. SNATs can be configured within a Profile definition.
C. SNATs can be configured within a Virtual Server definition.
D. SNAT’s are enabled only on the VLAN where origin traffic arrives, by default.
What is required for a virtual server to support clients whose traffic arrives on the internal VLAN and pool members whose traffic arrives on the external VLAN?
A. That support is never available.
B. The virtual server must be enabled for both VLANs.
C. The virtual server must be enabled on the internal VLAN.
D. The virtual server must be enabled on the external VLAN.
When probing LDNSs, which protocol is used by default?
A. TCP
B. ICMP
C. DNS_REV
D. DNS_DOT
Which of the following can be associated with an XML profile?
A. Flow
B. Method
C. Parameter
D. File type
Which of the following are properties of an ASM logging profile? (Choose three.)
A. storage type
B. storage filter
C. storage policy
D. web application
When implementing Data Guard, BIG-IP ASM scans for suspicious patterns in? (Choose two.)
A. All client requests
B. All server responses
C. Specific client requests
D. Specific server responses
An LTM object represents a downstream server that hosts a secure Web site and contains the IP address and port combination 192.168.9.250:443. What is this object?
A. Self IP
B. Virtual Server
C. Pool
D. Node
E. Pool Member
Since F5 built GTM on the TMOS platform it can exist on the same BIGIP device as LTM:
A. True
B. False
Could an iRule perform persistence based on a cookie?
A. Yes an iRule could be designed to persist based on the contents of a cookie.
B. No. iRules cannot affect persistence.
C. Yes. An iRule could be designed to persist based on the contents of a cookie.
D. No. Cookie persistence is only is based on a cookie persistence profile.
Which file contains the list of events for which the GTM System will send traps to an SNMP manager?
A. /etc/snmpd.conf
B. /etc/syslogng.conf
C. /etc/alertd/alert.conf
D. /etc/gtm_snmptrap.conf
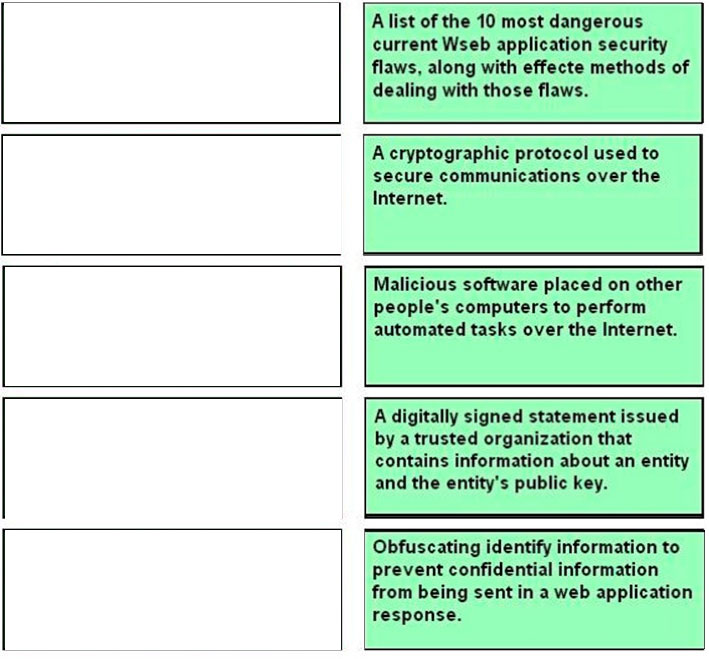
Match each persistence method with the correct statement describing it:
A. Cookie persistence
B. Source address persistence
C. SSL persistence
D. Universal persistence
Which item is NOT a function of a properly deployed and configured ASM?
A. Detects attacks
B. Stops hackers from attacking
C. Provides protection visibility
D. Provides security agility
TCP Express is licensed separately from LTM
A. True
B. False
Assuming that systems are synchronized, which action could take place if the failover cable is connected correctly and working properly, but the systems cannot communicate over the network due to extern al network problems.
A. If network failover is enabled, the standby system will assume the active mode.
B. Whether or not network failover is enabled, the standby system will stay in standby mode.
C. Whether or not network failover is enabled, the standby system will assume the active mode.
D. If network failover is enabled, the standby system will go into active mode but only until the network recovers.
Access Full 101 Dump Free
Looking for even more practice questions? Click here to access the complete 101 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our 101 dump free questions — and get one step closer to exam success!