Policing and Shaping
Used to enforce rate limiting, where excess IP traffic is either dropped, marked, or delayed.
- Traffic policers and shapers are traffic-conditioning QoS mechanisms used to classify traffic and enforce other QoS mechanisms such as rate limiting.
- Traffic policers and shapers classify traffic in an identical manner but differ in their implementation.
- Policers: Drop or re-mark incoming or outgoing traffic that goes beyond a desired traffic rate.
- Shapers: Buffer and delay egress traffic rates that momentarily peak above the desired rate until the egress traffic rate drops below the defined traffic rate. If the egress traffic rate is below the desired rate, the traffic is sent immediately.
Placing Policers and Shapers in the Network
Policers for incoming traffic are most optimally deployed at the edge of the network to keep traffic from wasting valuable bandwidth in the core of the network.
- Policers for outbound traffic are most optimally deployed at the edge of the network or core-facing interfaces on network edge devices.
- A downside of policing is that it causes TCP retransmissions when it drops traffic.
Shapers are used for egress traffic and typically deployed by enterprise networks on service provider (SP)–facing interfaces.
- Shaping is useful in cases where SPs are policing incoming traffic or when SPs are not policing traffic but do have a maximum traffic rate SLA, which, if violated, could incur monetary penalties.
- Shaping buffers and delays traffic rather than dropping it, and this causes fewer TCP retransmissions compared to policing.
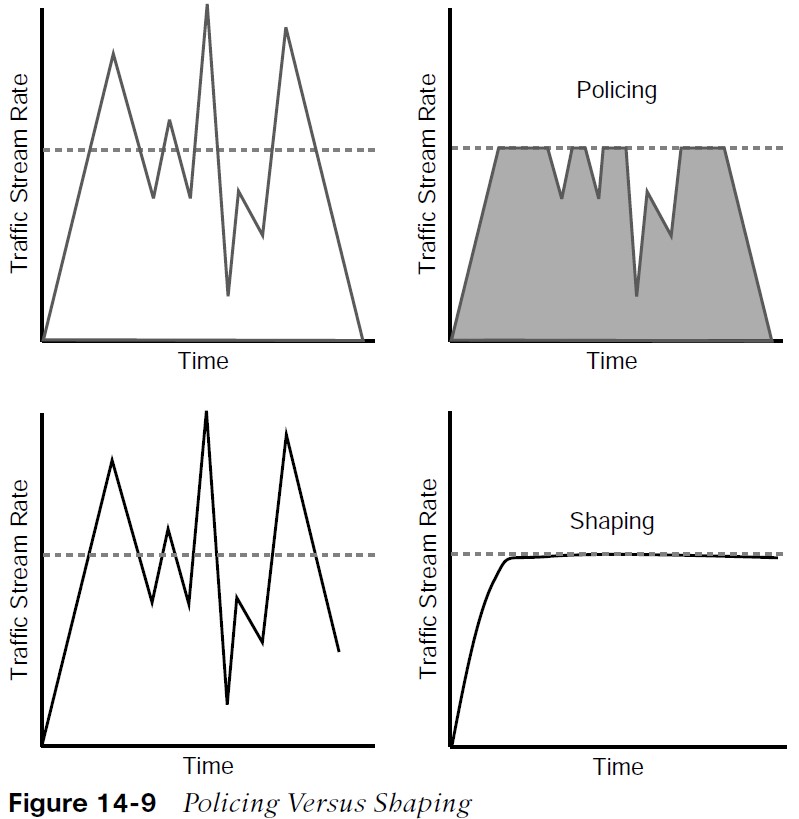
 Figure 14-9 illustrates the difference between traffic policing and shaping. Policers drop or remark excess traffic, while shapers buffer and delay excess traffic.
Figure 14-9 illustrates the difference between traffic policing and shaping. Policers drop or remark excess traffic, while shapers buffer and delay excess traffic.
Markdown
When a desired traffic rate is exceeded, a policer can take one of the following actions:
- Drop the traffic.
- Mark down the excess traffic with a lower priority.
Marking down excess traffic involves re-marking the packets with a lower-priority class value:
- For example, excess traffic marked with AFx1 should be marked down to AFx2 (or AFx3 if using two-rate policing).
- After marking down the traffic, congestion avoidance mechanisms, such as DSCP-based weighted random early detection (WRED), should be configured throughout the network to drop AFx3 more aggressively than AFx2 and drop AFx2 more aggressively than AFx1.
Token Bucket Algorithms
Cisco IOS policers and shapers are based on token bucket algorithms. The following list includes definitions that are used to explain how token bucket algorithms operate:
- Committed Information Rate (CIR) – The policed traffic rate, in bits per second (bps), defined in the traffic contract.
- Committed Time Interval (Tc) – The time interval, in milliseconds (ms), over which the committed burst (Bc) is sent. Tc can be calculated with the formula Tc = (Bc [bits] / CIR [bps]) × 1000.
- Committed Burst Size (Bc) – The maximum size of the CIR token bucket, measured in bytes, and the maximum amount of traffic that can be sent within a Tc. Bc can be calculated with the formula Bc = CIR × (Tc / 1000).
- Token – A single token represents 1 byte or 8 bits.
Token Bucket Algorithms
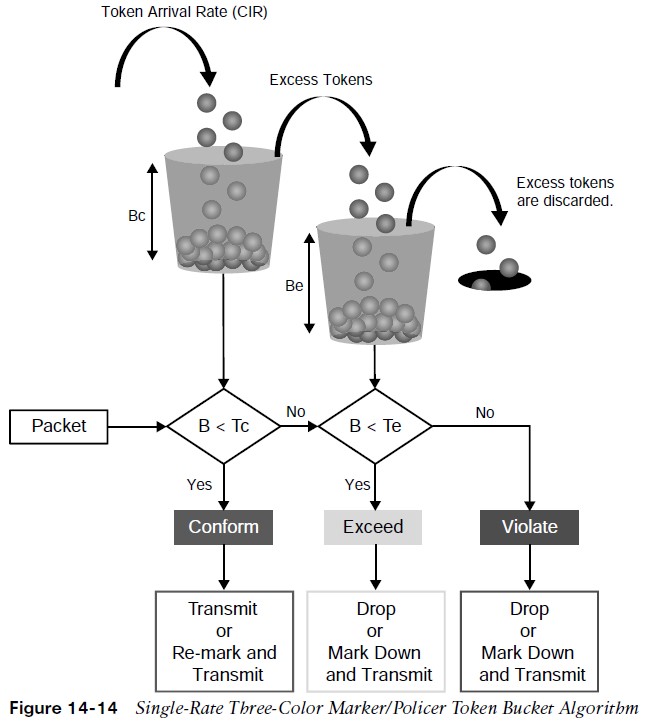
Token bucket: A bucket that accumulates tokens until a maximum predefined number of tokens is reached (such as the Bc when using a single token bucket). These tokens are added into the bucket at a fixed rate (the CIR). Each packet is checked for conformance to the defined rate and takes tokens from the bucket equal to its packet size. For example, if the packet size is 1500 bytes, it takes 12,000 bits (1500 × 8) from the bucket. If there are not enough tokens in the token bucket to send the packet, the traffic conditioning mechanism can take one of the following actions:
- Buffer the packets while waiting for enough tokens to accumulate in the token bucket (traffic shaping)
- Drop the packets (traffic policing)
- Mark down the packets (traffic policing)
Single Token Bucket Algorithm
It is recommended for the Bc value to be larger than or equal to the size of the largest possible IP packet in a traffic stream. Otherwise, there will never be enough tokens in the token bucket for larger packets, and they will always exceed the defined rate. 
- If the bucket fills up to the maximum capacity, newly added tokens are discarded. Discarded tokens are not available for use in future packets.
- Token bucket algorithms may use one or multiple token buckets.
- For single token bucket algorithms, the measured traffic rate can conform to or exceed the defined traffic rate. The measured traffic rate is conforming if there are enough tokens in the token bucket to transmit the traffic. The measured traffic rate is exceeding if there are not enough tokens in the token bucket to transmit the traffic.
Single Token Bucket Operation
To understand how the single token bucket algorithms operate in more detail, assume that a 1 Gbps interface is configured with a policer defined with a CIR of 120 Mbps and a Bc of 12 Mb. 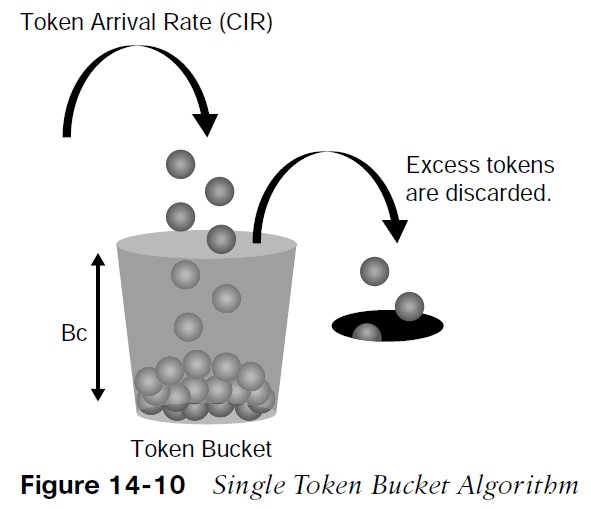 The Tc value cannot be explicitly defined in IOS, but it can be calculated as follows:
The Tc value cannot be explicitly defined in IOS, but it can be calculated as follows:
- Tc = (Bc [bits] / CIR [bps]) × 1000
- Tc = (12 Mb / 120 Mbps) × 1000
- Tc = (12,000,000 bits / 120,000,000 bps) × 1000 = 100 ms
Once the Tc value is known, the number of Tcs within a second can be calculated as follows:
- Tcs per second = 1000 / Tc
- Tcs per second = 1000 ms / 100 ms = 10 Tcs
Single Token Bucket Operation (Cont.)
If a continuous stream of 1500-byte (12,000-bit) packets is processed by the token algorithm, only a Bc of 12 Mb can be taken by the packets within each Tc (100 ms). The number of packets that conform to the traffic rate and are allowed to be transmitted can be calculated as follows: • Number of packets that conform within each Tc = Bc / packet size in bits (rounded down) • Number of packets that conform within each Tc = 12,000,000 bits / 12,000 bits = 1000 packets Any additional packets beyond 1000 will either be dropped or marked down. To figure out how many packets would be sent in one second, the following formula can be used:
- Packets per second = Number of packets that conform within each Tc × Tcs per second
- Packets per second = 1000 packets × 10 intervals = 10,000 packets
CIR Calculation
To calculate the CIR for the 10,000, the following formula can be used:
- CIR = Packets per second × Packet size in bits
- CIR = 10,000 packets per second × 12,000 bits = 120,000,000 bps = 120 Mbps
To calculate the time interval it would take for the 1000 packets to be sent at interface line rate, the following formula can be used:
- Time interval at line rate = (Bc [bits] / Interface speed [bps]) × 1000
- Time interval at line rate = (12 Mb / 1 Gbps) × 1000
- Time interval at line rate = (12,000,000 bits / 1000,000,000 bps) × 1000 = 12 ms
CIR Calculation
Figure 14-11 illustrates how the Bc (1000 packets at 1500 bytes each, or 12Mb) is sent every Tc interval. After the Bc is sent, there is an interpacket delay of 113 ms (125 ms minus 12 ms) within the Tc where there is no data transmitted. 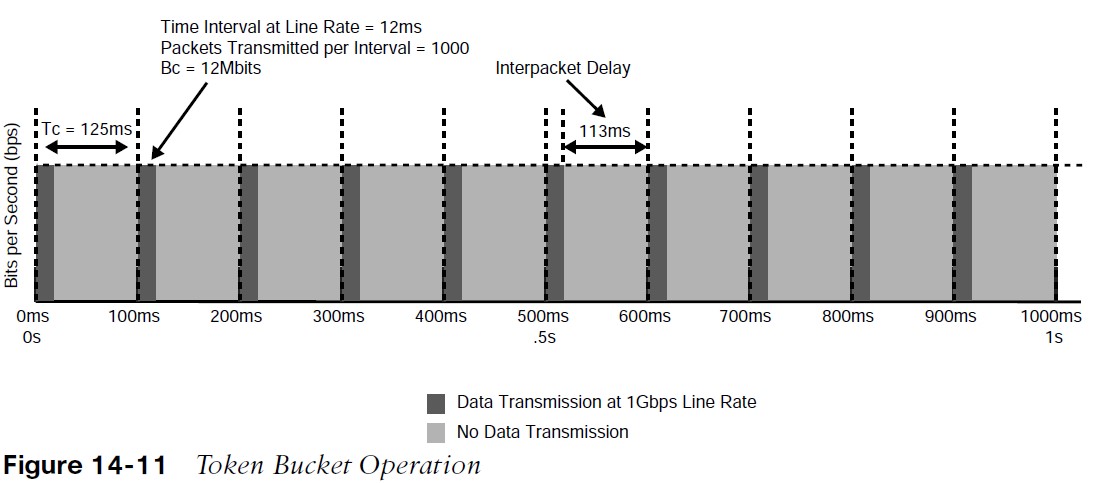 The recommended values for Tc range from 8 ms to 125 ms. Shorter Tcs, such as 8 ms to 10 ms, are necessary to reduce interpacket delay for real-time traffic such as voice. Tcs longer than 125 ms are not recommended for most networks because the interpacket delay becomes too large.
The recommended values for Tc range from 8 ms to 125 ms. Shorter Tcs, such as 8 ms to 10 ms, are necessary to reduce interpacket delay for real-time traffic such as voice. Tcs longer than 125 ms are not recommended for most networks because the interpacket delay becomes too large.
Policing and Shaping
Single Rate Two-Color Markers/Policers
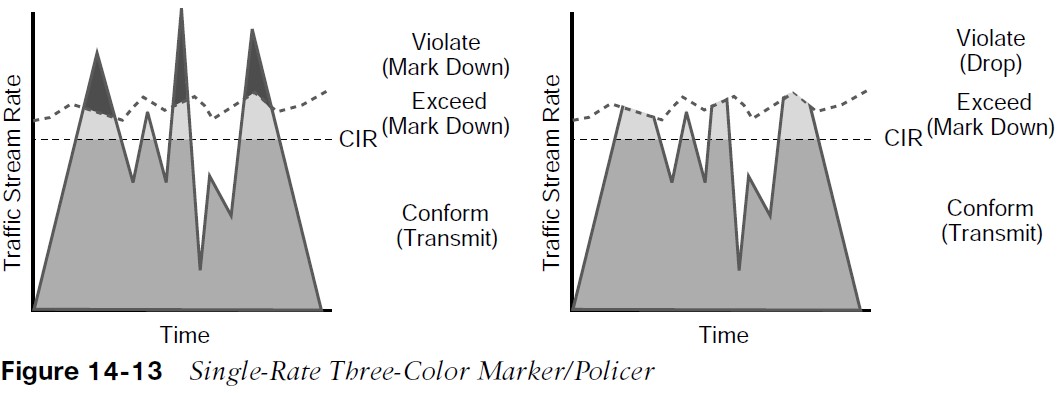
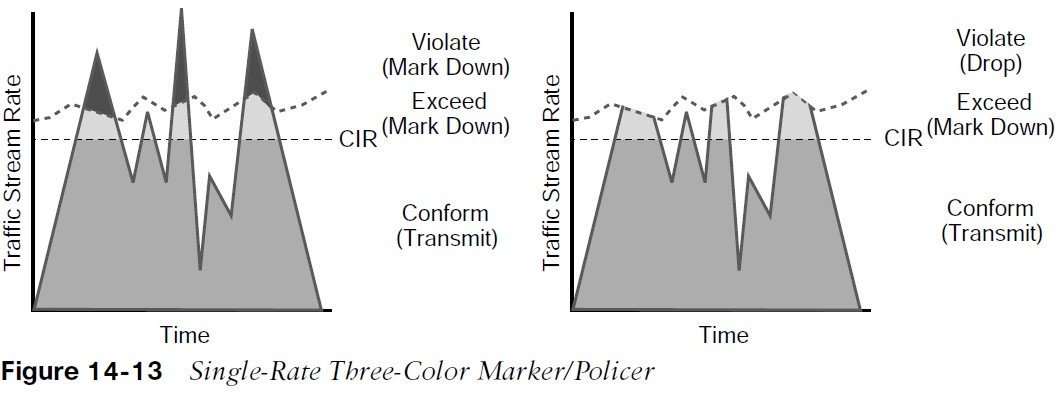
There are different policing algorithms, including single-rate two-color marker/policer, single-rate three-color marker/policer (srTCM), two-rate three-color marker/policer (trTCM). Single-rate, two-color model is based on the single token bucket algorithm. For this type of policer, traffic can be either conforming to or exceeding the CIR. Marking down or dropping actions can be performed for each of the two states. 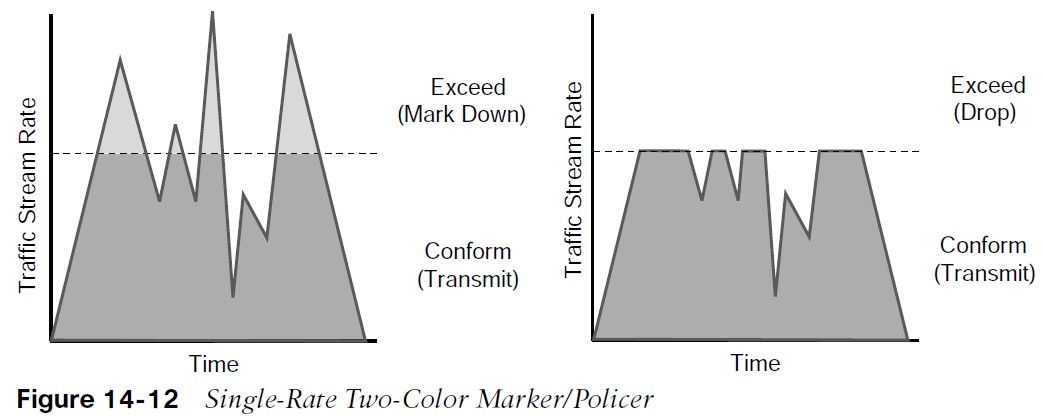 Figure 14-12 illustrates different actions that the single-rate two-color policer can take.
Figure 14-12 illustrates different actions that the single-rate two-color policer can take.
- The section above the dotted line on the left side of the figure represents traffic that exceeded the CIR and was marked down.
- The section above the dotted line on the right side of the figure represents traffic that exceeded the CIR and was dropped.
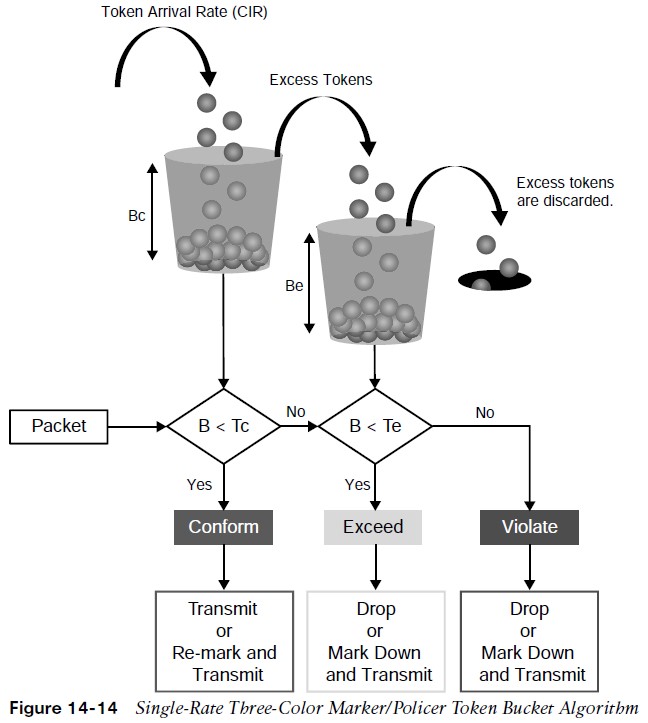
Single Rate Three – Color Markers/Policers
Single-rate three-color policer algorithms are based on RFC 2697. This type of policer uses two token buckets, and the traffic can be classified as either conforming to, exceeding, or violating the CIR. Marking down or dropping actions are performed for each of the three states of traffic. The first token bucket operates very similarly to the single-rate two-color system; with a few differences:
- If there are any tokens left over in the bucket after each time period due to low or no activity, instead of discarding the excess tokens (overflow), the algorithm places them in a second bucket to be used later for temporary bursts that might exceed the CIR.
- Tokens placed in this second bucket are referred to as the excess burst (Be), and Be is the maximum number of bits that can exceed the Bc burst size.
Single Rate Three- Color Markers/Policers (Cont.)
Traffic can be classified in three colors or states, as follows:
- Conform – Traffic under Bc is classified as conforming and green. Conforming traffic is usually transmitted and can be optionally re-marked.
- Exceed – Traffic over Bc but under Be is classified as exceeding and yellow. Exceeding traffic can be dropped or marked down and transmitted.
- Violate – Traffic over Be is classified as violating and red. This type of traffic is usually dropped but can be optionally marked down and transmitted.
Single Rate Three – Color Markers/Policers (Cont.)
- The section below the straight dotted line on the left side of the figure represents the traffic that conformed to the CIR, the section right above the straight dotted line represents the exceeding traffic that was marked down, and the top section represents the violating traffic that was also marked down.
- The exceeding and violating traffic rates vary because they rely on random tokens spilling over from the Bc bucket into the Be.
- The section right above the straight dotted line on the right side of the figure represents traffic that exceeded the CIR and was marked down and the top section represents traffic that violated the CIR and was dropped.
Single Rate Three- Color Markers/Policers Parameters
The single-rate three-color marker/policer uses the following parameters to meter the traffic stream:
- Committed Information Rate (CIR) – The policed rate.
- Committed Burst Size (Bc) – The maximum size of the CIR token bucket, measured in bytes. Referred to as Committed Burst Size (CBS) in RFC 2697.
- Excess Burst Size (Be) – The maximum size of the excess token bucket, measured in bytes. Referred to as Excess Burst Size (EBS) in RFC 2697.
- Bc Bucket Token Count (Tc) – The number of tokens in the Bc bucket. Not to be confused with the committed time interval Tc.
- Be Bucket Token Count (Te) – The number of tokens in the Be bucket.
- Incoming Packet Length (B) – The packet length of the incoming packet, in bits.
Single Rate Three- Color Marker Uses
- The single-rate three-color policer’s two bucket algorithm causes fewer TCP retransmissions and is more efficient for bandwidth utilization.
- It is the perfect policer to be used with AF classes (AFx1, AFx2, and AFx3).
- Using a three-color policer makes sense only if the actions taken for each color differ.
- If the actions for two or more colors are the same, for example, conform and exceed both transmit without re-marking, the single-rate two-color policer is recommended to keep things simpler.
Two Rate Three-Color Markers/Policers
- The two-rate three-color marker/policer is based on RFC 2698 and is similar to the single-rate three-color policer.
- The difference is that single-rate three-color policers rely on excess tokens from the Bc bucket, which introduces a certain level of variability and unpredictability in traffic flows.
- The two-rate three-color marker/policers address this issue by using two distinct rates:
- the CIR
- the Peak Information Rate (PIR)
- The two-rate three-color marker/policer allows for a sustained excess rate based on the PIR that allows for different actions for the traffic exceeding the different burst values. For example, violating traffic can be dropped at a defined rate, and this is something that is not possible with the single-rate three-color policer.
Two Rate Three-Color Markers/Policers (Cont.)
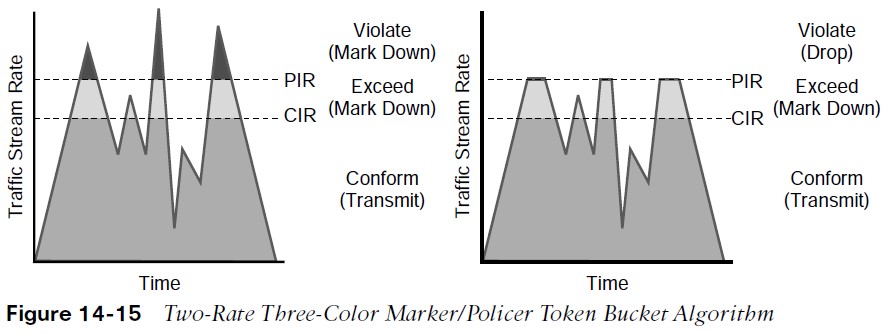
- Figure 14-15 illustrates how violating traffic that exceeds the PIR can either be marked down (on the left side of the figure) or dropped (on the right side of the figure).
- Compare Figure 14-15 to Figure 14-13 to see the difference between the two-rate three-color policer and the single-rate three-color policer.
Two Rate Three-Color Markers/Policers Parameters
The two-rate three-color marker/policer uses the following parameters to meter the traffic stream:
- Committed Information Rate (CIR) – The policed rate.
- Peak Information Rate (PIR) – The maximum rate of traffic allowed. PIR should be equal to or greater than the CIR.
- Committed Burst Size (Bc) – The maximum size of the second token bucket, measured in bytes. Referred to as Committed Burst Size (CBS) in RFC 2698.
- Peak Burst Size (Be) – The maximum size of the PIR token bucket, measured in bytes. Referred to as Peak Burst Size (PBS) in RFC 2698. Be should be equal to or greater than Bc.
- Bc Bucket Token Count (Tc) – The number of tokens in the Bc bucket. Not to be confused with the committed time interval Tc.
- Bp Bucket Token Count (Tp) – The number of tokens in the Bp bucket.
- Incoming Packet Length (B) – The packet length of the incoming packet, in bits.
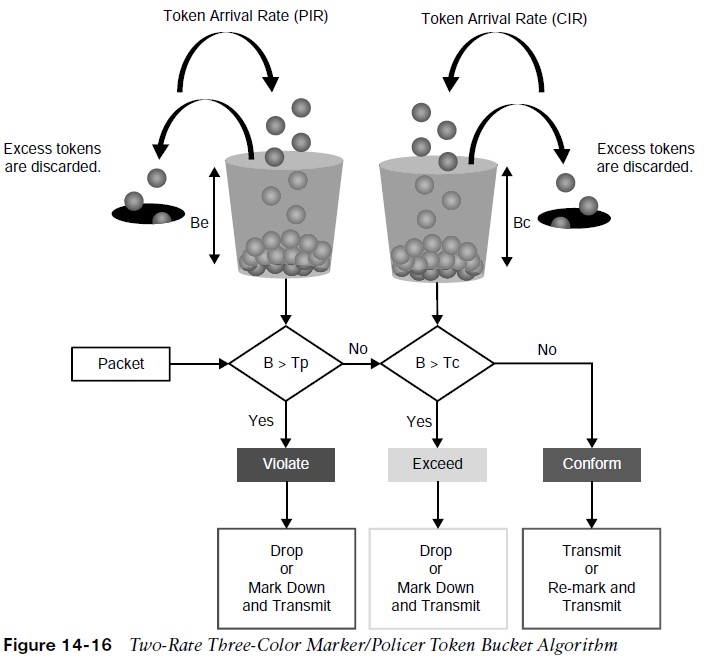
Two Rate Three-Color Markers/Policers
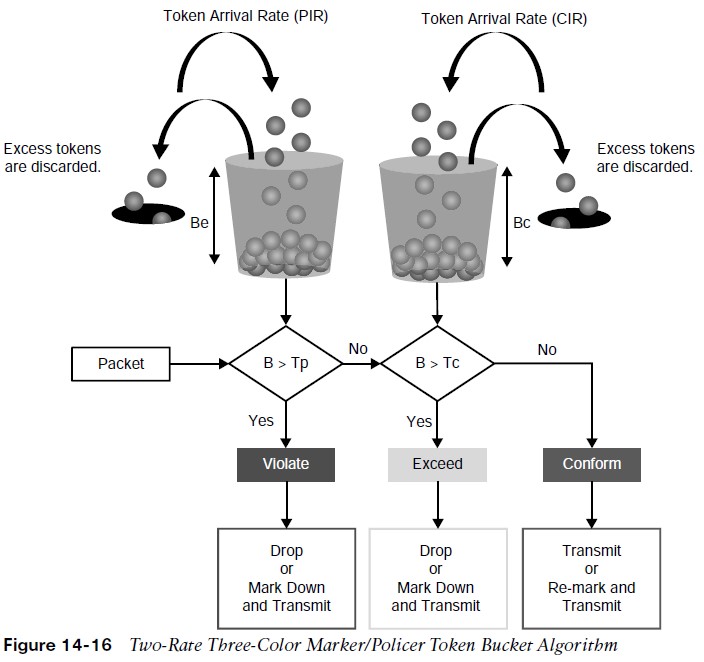
- The two-rate three-color policer also uses two token buckets.
- Instead of transferring unused tokens from the Bc bucket to the Be bucket, this policer has two separate buckets that are filled with two separate token rates.
- The Be bucket is filled with the PIR tokens, and the Bc bucket is filled with the CIR tokens. In this model, the Be represents the peak limit of traffic that can be sent during a subsecond interval.
- The logic varies further in that the initial check is to see whether the traffic is within the PIR. Only then is the traffic compared against the CIR. In other words, a violate condition is checked first, then an exceed condition, and finally a conform condition, which is the reverse of the logic of the single-rate three-color policer.
Two Rate Three-Color Markers/Policers
- Figure 14-16 illustrates the token bucket algorithm for the two-rate three-color marker/policer.
- Compare it to the token bucket algorithm of the single-rate three-color marker/policer in Figure 14-14 to see the differences between the two.
Other useful information: