About Lesson
Locating Devices in a Wireless Network
how the components of a wireless network used to compute the physical location of wireless devices.
• Locating a user or device is important in several use cases, and a wireless network can be leveraged to provide that information.
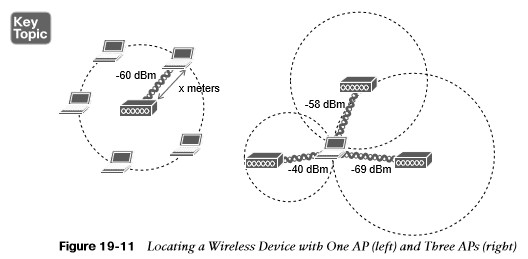
Locating a Wireless Device with One AP or Three
APs
- A client’s distance from an AP computed from its RSS.
- Obtain the same measurement from three or more APs, correlate the results and determine where they intersect.
- WLC <-> MSE/CMX

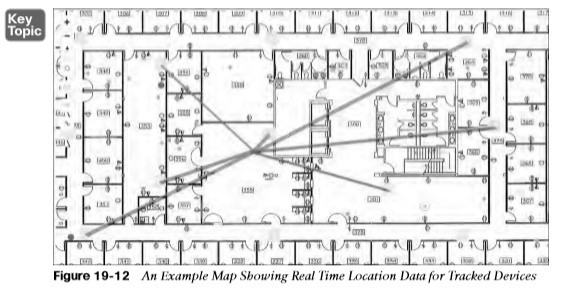
Real Time Location Data for Tracked Devices
- The most intuitive way to interpret location data is to view devices on a map that represents the building and floor.
- The square icons represent AP locations, which were manually entered on the map. One device has been selected in the figure causing lines to be drawn to some of the APs that overheard the device.
Real Time Location for Other Tracked Devices
- The same real-time location service also supports wireless devices that might never actually associate with an AP.
- RFID tags are another type of device that can be attached to objects so that they can be tracked and located.
- Some RFID tags can actively join a wireless network to exchange data, while others are meant to simply “wake up” periodically to send 802.11 Probe Requests or multicast frames to announce their presence.
- Another interesting use case is locating rogue devices and sources of Wi-Fi interference.
- Rogue devices will likely probe the network and can be discovered and located. Interference sources, such as cordless phones, wireless video cameras, and other transmitters, might not be compatible with the 802.11 standard at all.
Other useful information:
Join the conversation