About Lesson
Device Security
Configure network devices with device hardening features to mitigate security threats.
Cisco AutoSecure
- The security settings are set to the default values when a new operating system is installed on a device. In most cases, this level of security is inadequate.
- For Cisco routers, the Cisco AutoSecure feature can be used to assist securing the system.
- In addition, there are some simple steps that should be taken that apply to most operating systems:
-
- Default usernames and passwords should be changed immediately.
- Access to system resources should be restricted to only the individuals that are authorized to use those resources.
- Any unnecessary services and applications should be turned off and uninstalled when possible.
- Often, devices shipped from the manufacturer have been sitting in a warehouse for a period of time and do not have the most up-to-date patches installed. It is important to update any software and install any security patches prior to implementation.
Passwords
- To protect network devices, it is important to use strong passwords.
- Here are standard guidelines to follow:
-
- Use a password length of at least eight characters, preferably 10 or more characters.
- Make passwords complex. Include a mix of uppercase and lowercase letters, numbers, symbols, and spaces, if allowed.
- Avoid passwords based on repetition, common dictionary words, letter or number sequences, usernames, relative or pet names, biographical information, such as birthdates, ID numbers, ancestor names, or other easily identifiable pieces of information.
- Deliberately misspell a password. For example, Smith = Smyth = 5mYth or Security = 5ecur1ty.
- Change passwords often. If a password is unknowingly compromised, the window of opportunity for the threat actor to use the password is limited.
- Do not write passwords down and leave them in obvious places such as on the desk or monitor.
- On Cisco routers, leading spaces are ignored for passwords, but spaces after the first character are not. Therefore, one method to create a strong password is to use the space bar and create a phrase made of many words. This is called a passphrase.
- A passphrase is often easier to remember than a simple password. It is also longer and harder to guess.
Additional Password Security
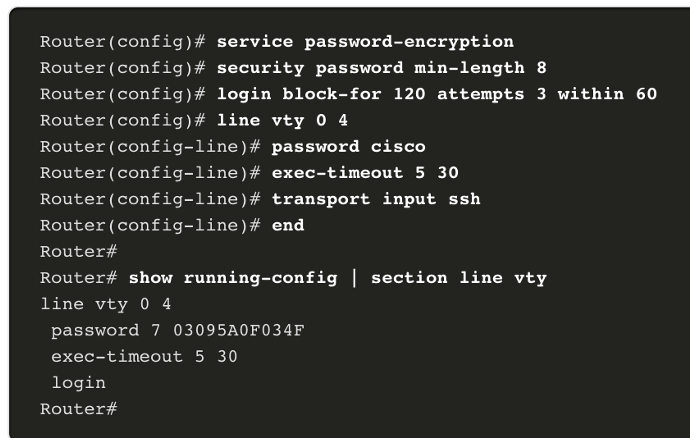
There are several steps that can be taken to help ensure that passwords remain secret on a Cisco router and switch including these:
- Encrypt all plaintext passwords with the service password-encryption command.
- Set a minimum acceptable password length with the security passwords min-length command.
- Deter brute-force password guessing attacks with the login block-for # attempts # within # command.
- Disable an inactive privileged EXEC mode access after a specified amount of time with the exec-timeout command.

Enable SSH
It is possible to configure a Cisco device to support SSH using the following steps:
- Configure a unique device hostname. A device must have a unique hostname other than the default.
- Configure the IP domain name. Configure the IP domain name of the network by using the global configuration mode command ip-domain name.
- Generate a key to encrypt SSH traffic. SSH encrypts traffic between source and destination. However, to do so, a unique authentication key must be generated by using the global configuration command crypto key generate rsa general-keys modulus bits. The modulus bits determines the size of the key and can be configured from 360 bits to 2048 bits. The larger the bit value, the more secure the key. However, larger bit values also take longer to encrypt and decrypt information. The minimum recommended modulus length is 1024 bits.
- Verify or create a local database entry. Create a local database username entry using the username global configuration command.
- Authenticate against the local database. Use the login local line configuration command to authenticate the vty line against the local database.
- Enable vty inbound SSH sessions. By default, no input session is allowed on vty lines. You can specify multiple input protocols including Telnet and SSH using the transport input [ssh | telnet] command.
Disable Unused Services
Cisco routers and switches start with a list of active services that may or may not be required in your network. Disable any unused services to preserve system resources, such as CPU cycles and RAM, and prevent threat actors from exploiting these services.
- The type of services that are on by default will vary depending on the IOS version. For example, IOS-XE typically will have only HTTPS and DHCP ports open. You can verify this with the show ip ports all command.
- IOS versions prior to IOS-XE use the show control-plane host open-ports command.
Other related topics
| Topic Title | Topic Objective |
|---|---|
| Security Threats and Vulnerabilities | Explain why basic security measures are necessary on network devices. |
| Network Attacks | Identify security vulnerabilities. |
| Network Attack Mitigation | Identify general mitigation techniques. |
| Device Security | Configure network devices with device hardening features to mitigate security threats. |
Other useful information
Join the conversation