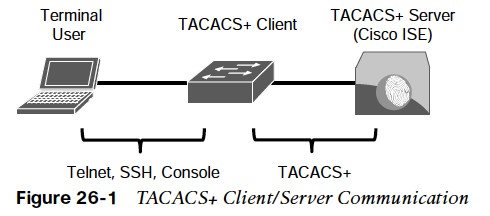
Authentication, Authorization, and Accounting (AAA)
how to configure and verify network device access control on IOS through an AAA TACACS+ server.
AAA is an architectural framework for enabling a set of three independent security functions:
- Authentication
- Authorization
- Accounting
AAA is commonly used in the networking industry for the following two use cases:
- Network device access control
- Secure network access control
AAA Framework
AAA is an architectural framework for enabling a set of three independent security functions:
- Authentication – Enables a user to be identified and verified prior to being granted access to a network device and/or network services.
- Authorization – Defines the access privileges and restrictions to be enforced for an authenticated user.
- Accounting – Provides the ability to track and log user access, including user identities, start and stop times, executed commands (that is, CLI commands), and so on. In other words, it maintains a security log of events.
There are many AAA protocols available, but the two most popular ones are Remote Authentication Dial-In User Service (RADIUS) and Terminal Access Controller Access-Control System Plus (TACACS+).
AAA Use Cases
AAA is commonly used in the networking industry for the following two use cases:
- Network device access control – As described earlier in this chapter, IOS provides local features for simple device access control, such as local username-based authentication and line password authentication. However, these features do not provide the same degree of access control and scalability that is possible with AAA. For this reason, AAA is the recommended method for access control. TACACS+ is the protocol of choice for network device access control.
- Secure network access control – AAA can be used to obtain the identity of a device or user before that device or user is allowed to access to the network. RADIUS is the preferred protocol for secure network access.
TACACS+
- Cisco developed TACACS+ and released it as an open standard in the early 1990s. Although TACACS+ is mainly used for AAA device access control, it is possible to use it for some types of AAA network access. The TACACS+ protocol uses Transmission Control Protocol (TCP) port 49 for communication between the TACACS+ clients and the TACACS+ server.

RADIUS
- One of the key differentiators of TACACS+ is its capability to separate authentication, authorization, and accounting into independent functions. This is why TACACS+ is so commonly used for device administration instead of RADIUS, even though RADIUS is capable of providing network device access control.
- RADIUS is an IETF standard AAA protocol. RADIUS is the AAA protocol of choice for secure network access. The reason for this is that RADIUS is the AAA transport protocol for Extensible Authentication Protocol (EAP), while TACACS+ does not support this functionality.
- Another major difference between TACACS+ and RADIUS is that RADIUS needs to return all authorization parameters in a single reply, while TACACS+ can request authorization parameters separately and multiple times throughout a session.
RADIUS & TACACS+ Comparison
Table 26-4 provides a summary comparison of RADIUS and TACACS+.
| Component | RADIUS | TACACS+ |
| Protocol and port(s) used | Cisco’s implementation:
|
TCP: port 49 |
| Encryption |
|
|
| Authentication and authorization |
|
|
| Accounting | Does not support network device CLI command accounting | Supports network device CLI command accounting |
| Primary Use | Secure network access | Network device access control |
Configuring AAA for Network Device Access Control
There are two parts to configuring TACACS+:
- The configuration of the device itself
- The configuration of the TACACS+ AAA server (for example, Cisco ISE)
The following steps are for configuring an IOS device with TACACS+ for device access control. Configuration for the TACACS+ server is not included here because it is beyond the scope of this book:
- Step 1. Create a local user with full privilege for fallback or to avoid being locked out after enabling AAA by using the command username {username} privilege 15 algorithm-type {md5 | sha256 | scrypt} secret {password}
- Step 2. Enable AAA functions on by using with the command aaa new-model.
- Step 3. Add a TACACS+ server using one of these methods, depending on the IOS version:
- To add a TACACS+ server on IOS versions prior to 15.x, use the command tacacs-server host { hostname | host-ip-address } key key-string
- To add a TACACS+ server on IOS versions 15.x and later, use the following commands: tacacs server name address ipv4 { hostname | host-ip-address } key key-string
- Step 4. Create an AAA group by using the following commands:
- aaa group server tacacs+ group-name
- server name server-name.
- This creates an AAA group that includes the TACACS+ servers that are added to the group with the server name command.
- Step 5. Enable AAA login authentication by using the command aaa authentication login { default | custom-list-name } method1 [ method2 . . . ] Method lists enable login authentication. The default keyword applies the method lists that follow (method1 [ method2 . . .) to all lines (cty, tty, aux, and so on). The custom list-name CLI assigns a custom name for the method lists that follow it. To apply a custom list to a line, use the command login authentication custom-listname under the line configuration mode. Method lists are applied sequentially from left to right.
- Step 6. Enable AAA authorization for EXEC by using the command aaa authorization exec { default | custom-list-name } method1 [ method2 . . . ] This command enables EXEC shell authorization for all lines except the console line.
- Step 7. Enable AAA authorization for the console by using the command aaa authorization console. Authorization for the console is disabled by default to prevent inexperienced users from locking themselves out.
- Step 8. Enable AAA command authorization by using the command aaa authorization commands {privilege level} { default | custom-list-name } method1 [ method2 . . . ]
- Step 9. Enable command authorization in global configuration mode (and all global configuration submodes) by using the command aaa authorization config-commands
- Step 10. Enable login accounting by using the command aaa accounting exec { default | custom-list-name } method1 [ method2 . . . ]
- Step 11. Enable command accounting by using the command aaa accounting commands {privilege level} { default | custom-list-name } method1 [ method2 . . . ]
AAA Configuration For Device Control Example
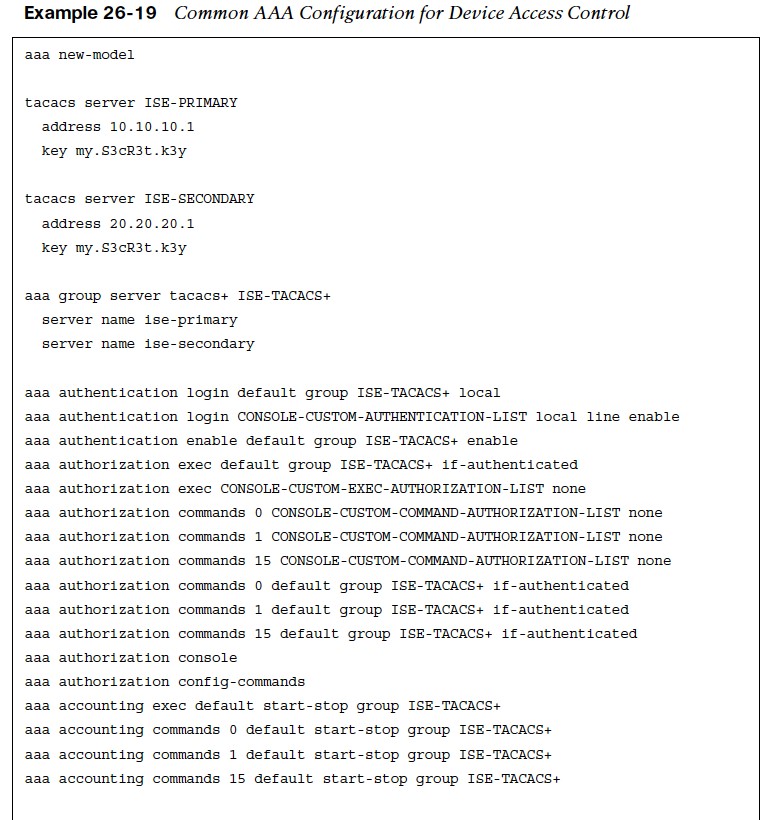
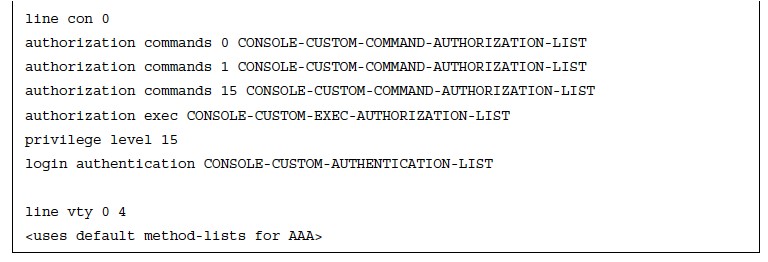
- Apart from the IOS configuration, the AAA server also needs to be configured with the AAA client information (hostname, IP address, and key), the login credentials for the users, and the commands the users are authorized to execute on the device.
Verifying AAA Configuration
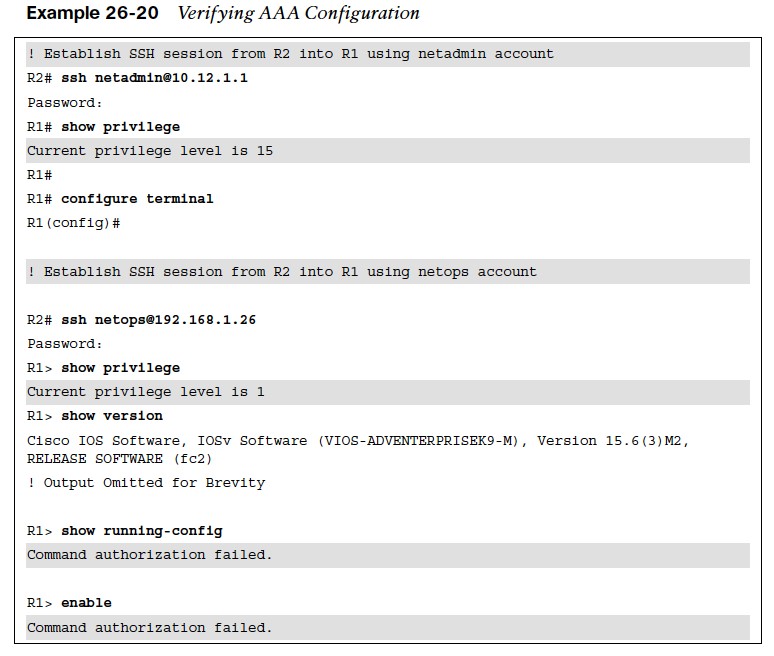
- Example 26-20 demonstrates SSH sessions being initiated from R2 into R1, using the netadmin and netops accounts.
- The netadmin account was configured in the AAA server with privilege 15, and netops was configured with privilege 1. The netadmin account has access to the full set of commands, while netops is very limited.