Next-Generation Endpoint Security
security components such as NGFW, Web Security Appliance (WSA), and Email Security Appliance (ESA) to protect endpoints from threats and attacks.
- The most critical components needed to implement the SAFE framework for a campus environment.
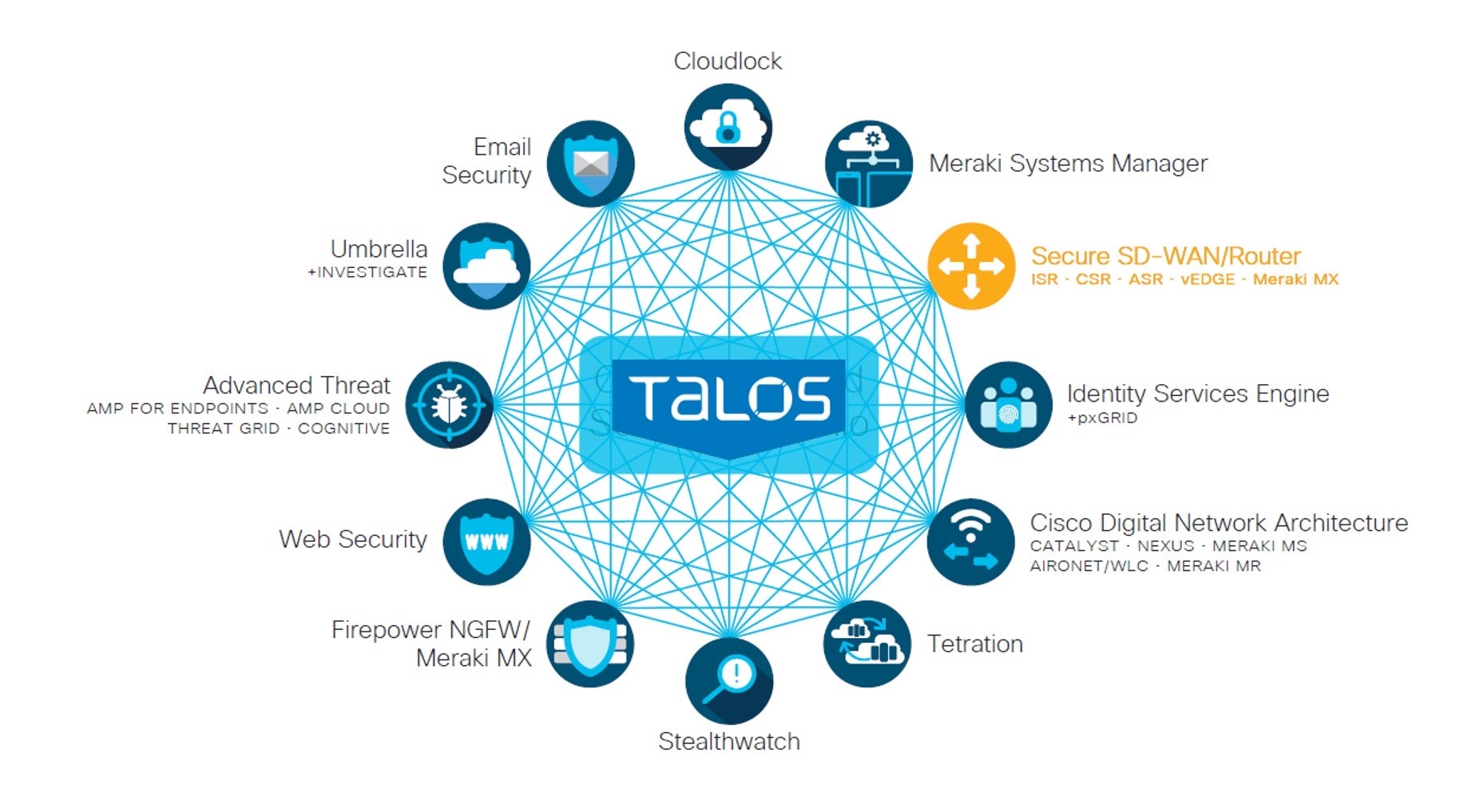
Talos

- The Cisco threat intelligence organization,
- An elite team of security experts to create threat intelligence that detects, analyzes, protects against both known and emerging threats for Cisco products.
- Created from the combination of three security research teams:
- IronPort Security Applications (SecApps)
- Sourcefire Vulnerability Research Team (VRT)
- Cisco Threat Research, Analysis, and Communications (TRAC) team
 Receives valuable intelligence through the following intelligence feeds:
Receives valuable intelligence through the following intelligence feeds:
- Advanced Microsoft, AMP community
- ClamAV, Snort, Immunet, SpamCop, SenderBase, Threat Grid, Talos user communities
- Honeypots
- The Sourcefire Awareness, Education, Guidance, Intelligence Sharing (AEGIS) program
- Private and public threat feeds
- Dynamic analysis
Threat Grid
A solution that can perform static file analysis, dynamic file analysis (behavioral analysis), by running the files in a controlled and monitored sandbox. 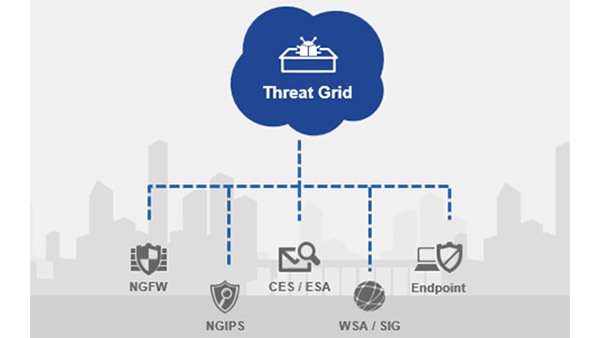
- Behavioral analysis is combined with threat intelligence feeds from Talos, and with existing security technologies.
- Possible to upload suspicious files into a sandbox called Glovebox to safely interact with them and observe malware behavior directly.
- Available as an appliance and in the cloud.
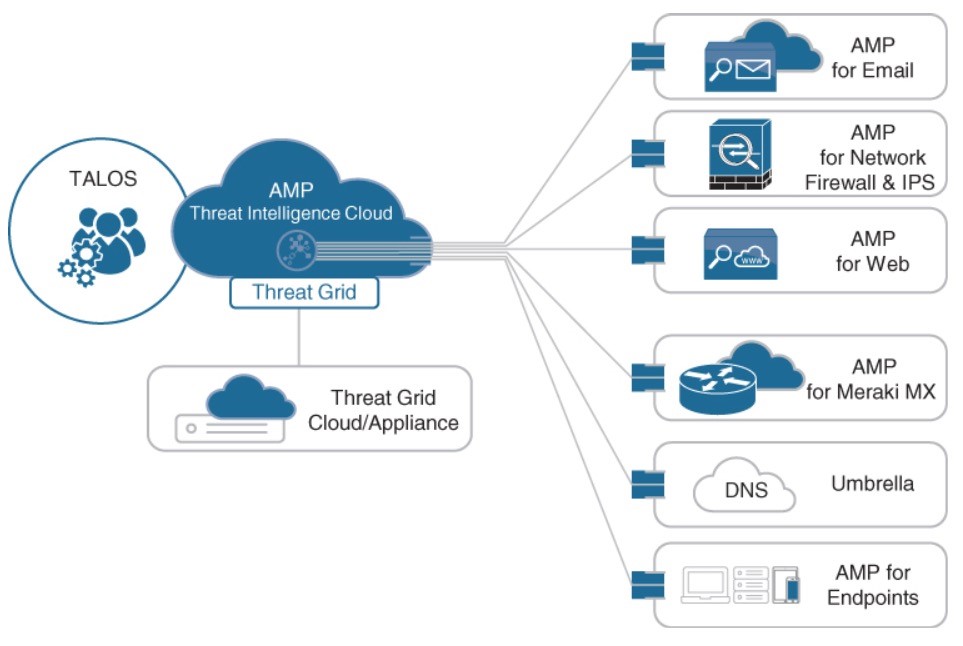
AMP
A malware analysis and protection solution that goes beyond point-in-time detection.
| Attack Time | AMP Processes |
| Before | Global threat intelligence from Talos and Threat Grid feeds into AMP to protect against known and new emerging threats. |
| During | File reputation to determine whether a file is clean or malicious as well as sandboxing used to identify threats during an attack. |
| After | AMP provides retrospection, IoCs, breach detection, tracking, analysis, and surgical remediation after an attack, when advanced malware has slipped past other defenses. |
AMP Components
- AMP Cloud (private/public).
- AMP connectors
- AMP for Endpoints (Win, macOS X, Android, Apple iOS, Linux)
- AMP for Networks (NGFW, NGIPS, ISRs)
- AMP for ESA
- AMP for Web (WSA)
- AMP for Meraki MX
- Threat intelligence from Talos and Threat Grid.
AnyConnect
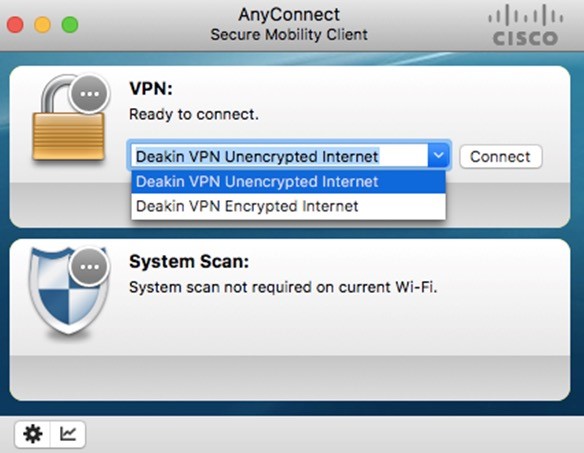
- AnyConnect Secure Mobility Client is a modular endpoint software: VPN client (TLS/SSL and IPsec IKEv2), VPN Posture (HostScan) and an ISE Posture module.
- Also includes web security (Cloud Web Security), network visibility (Stealthwatch), roaming protection (Umbrella).
- Supported Win, macOS, iOS, Linux, Android, Windows Phone/Mobile, BlackBerry, ChromeOS.
Umbrella
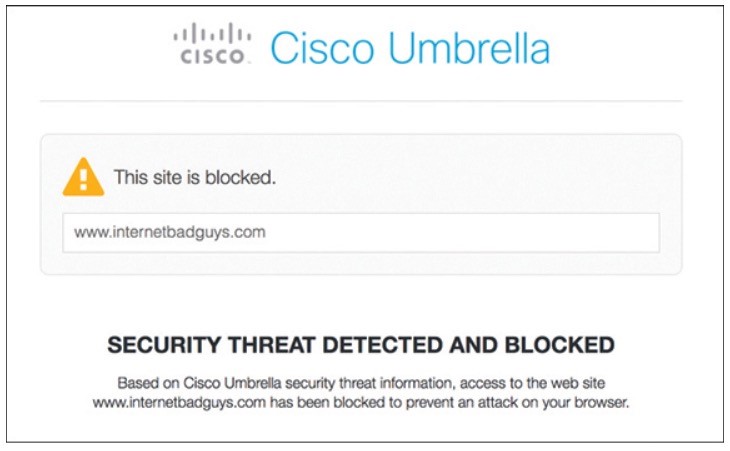
- Provides the first line of defense against threats on the internet.
- Blocking requests to malicious destinations (domains, IPs, URLs) using DNS before an IP connection is established or a file is downloaded.
- It is 100% cloud delivered, with no hardware/software to install.
- The Umbrella global network includes 30 DCs around the world using Anycast DNS, which allows it to guarantee 100% uptime.
Web Security Appliance

- Web Proxy incl. Caching (http,https, ftp, ftp over http)
and
- Rich security functionalities
- Reputation filtering
- Malware scanning
- URL Filtering
- Application visibility & control
- HTTPS inspection Authentication
- Reporting and tracking L4TM
- …
WSA
An all-in-one web gateway that includes a wide variety of protections that can block hidden malware from both suspicious and legitimate websites. 
| Before | During | After | |||
| Web reputation filters Web filtering Application Visibility and Control (AVC) | Cloud access security Parallel antivirus (AV) scanning Layer 4 traffic monitoring File reputation and analysis with AMP Data loss prevention (DLP) | Continuously inspects for instances of undetected malware and breaches. Global Threat Analytics (GTA) |
Before an Attack content
| Terms | Description |
| Web reputation filters | WSA detects and correlates threats in real time using Talos. Web reputation filtering prevents client devices from accessing dangerous websites containing malware or phishing links. |
| Web filtering | Traditional URL filtering is combined with real-time dynamic content analysis. This is used to shut down access to websites known to host malware. |
| Application Visibility and Control (AVC) | AVC identifies and classifies the most relevant and widely used web and mobile applications and more than 150,000 microapplications. |
During an Attack
| Terms | Description |
| Cloud access security | WSA protect against hidden threats in cloud apps |
| Parallel antivirus (AV) scanning | WSA enhances malware defense coverage with multiple antimalware scanning engines |
| Layer 4 traffic monitoring | WSA scans all traffic, ports, and protocols to detect and block spyware “phone-home” communications |
| File reputation and analysis with Cisco AMP | WSA assesses files using the latest threat information from Talos |
| Data loss prevention (DLP) | WSA uses Internet Control Adaptation Protocol (ICAP) to integrate with DLP solutions from leading third-party DLP vendors |
After an Attack
- After an initial detection, using AMP retrospection capabilities, WSA continues to scan files over an extended period of time, using the latest threat intelligence from Talos and AMP Thread Grid.
- Alerts are sent when a file disposition changes to provide awareness and visibility into malware that evades initial defenses.
Global Threat Analytics (GTA) analyzes web traffic, endpoint data from AMP for Endpoints, and network data from Stealthwatch. It then identifies malicious activity before it can exfiltrate sensitive data. WSA can be deployed in the cloud, as a virtual appliance, on-premises, or in a hybrid arrangement. All features are available across any deployment option.
ESA

- Deployed as a physical appliance, virtual appliance, a cloud service.
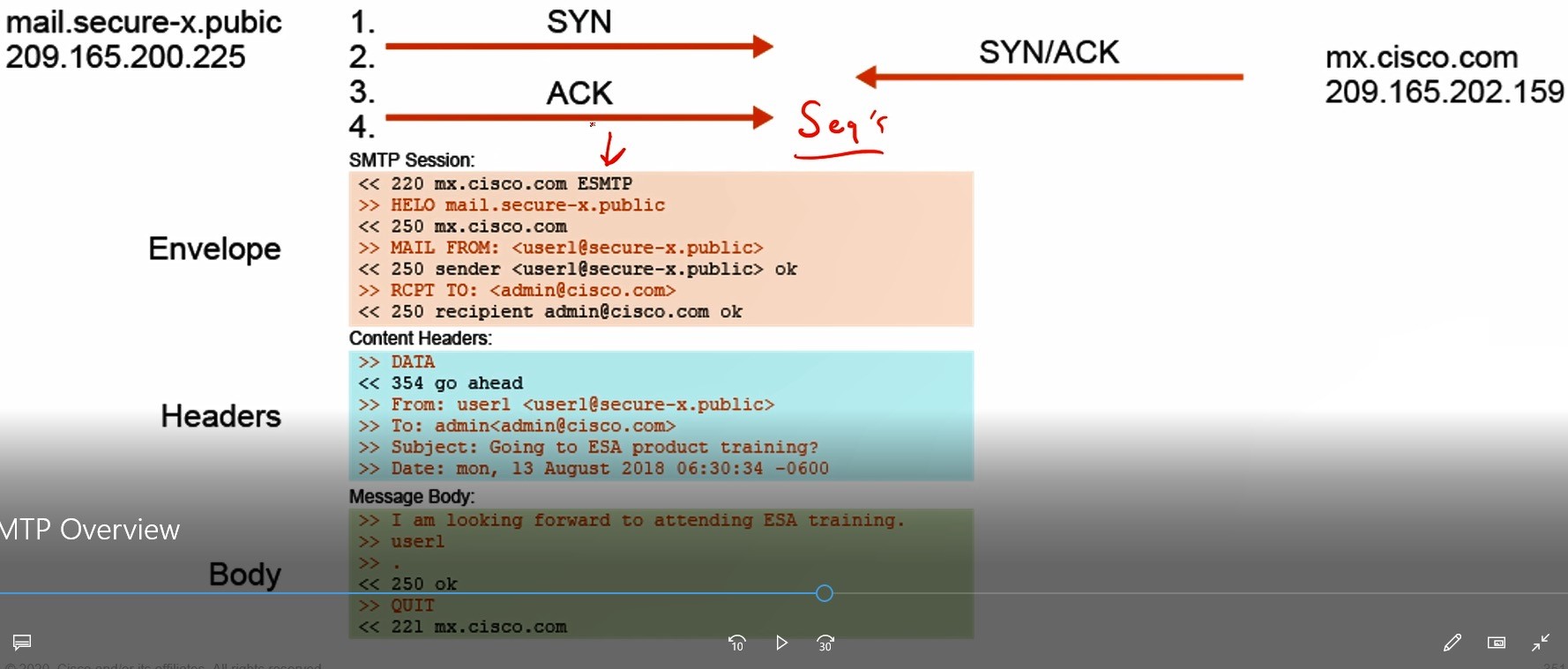
- Act as the email gateway to an organization, controlling the transfer of all email connections, accepting messages, relaying messages to the appropriate email servers.
- Handle all SMTP connections for an organization, acting as the SMTP gateway.
- ESA is the destination of the public MX records, the MX records of the underlying domain should point to ESA’s public IP address. The first hop the organization’s email infrastructure.
- ESA needs to be accessible through the public Internet.
- Enables users to communicate securely via email and helps organizations combat email security threats with a multilayered approach.
- Includes the following advanced threat protection capabilities that allow it to detect, block, and remediate threats across the attack continuum:
- Global threat intelligence – leverages real-time threat intelligence from Talos/AMP.
- Reputation filtering – blocks unwanted email with reputation filtering.
- Spam protection – uses the Cisco Context Adaptive Scanning Engine (CASE) to block spam emails.
- Forged email detection – Forged email detection protects high-value targets such as executives against business email compromise (BEC) attacks.
MIME – What is it?
- MIME refers to an official Internet standard that specifies how messages must be formatted so that they can be exchanged between different email systems.
- MIME permits the inclusion of virtually any type of file or document in an email message.
- Specifically, MIME messages can contain text images audio video application-specific data. spreadsheets word processing documents
Mapping Features to Protection
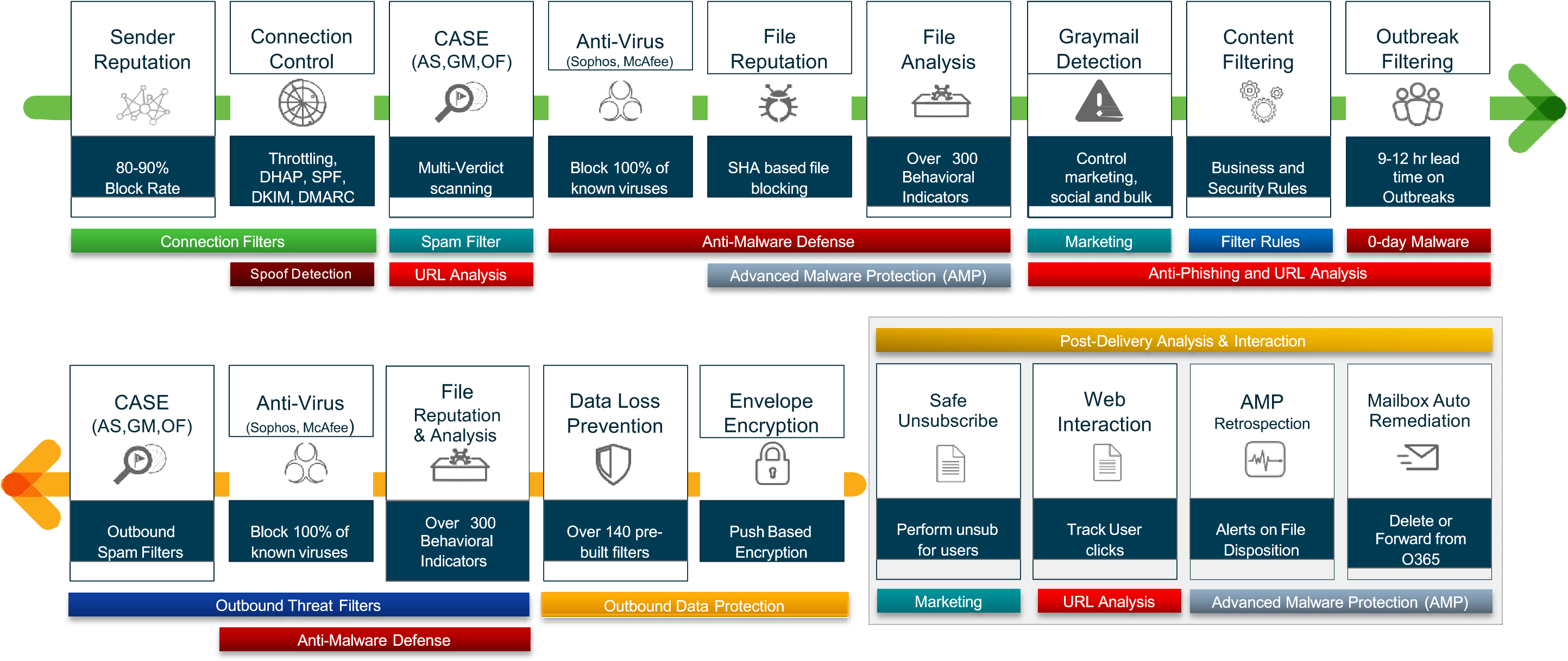
ESA (Cont.)
- Cisco Advanced Phishing Protection (CAPP) – combines Talos with local email intelligence and advanced machine learning techniques to model trusted email behaviors.
- Cisco Domain Protection (CDP) – CDP for external email helps prevent phishing emails from being sent using a customer domains.
- Malware defense – ESA protects against malware with AMP for email.
- Graymail detection and Safe Unsubscribe – ESA detects and classifies graymail for an administrator to take action on it if necessary. Graymail consists of marketing, social networking, bulk messages (mailing list emails).
- URL-related protection and control – ESA protects against malicious URLs with URL filtering and scanning of URLs in attachments and shortened URLs.
- Outbreak filters – Outbreak filters defend against emerging threats and blended attacks by leveraging Talos.
- Web interaction tracking – generates reports that track the end users who click on URLs that have been rewritten by the outbreak filters.
- Top users who clicked on malicious URLs
- The top malicious URLs clicked by end users
- Date and time, rewrite reason, action taken on the URLs
- Data security for sensitive content in outgoing emails – Confidential outbound messages that match one of the more than 100 expert policies included with ESA are automatically protected.
NGIPS
- An IDS: A system that passively monitors and analyzes network traffic for potential network intrusion attacks and logs the intrusion attack data for security analysis.
- An IPS: A system that provides IDS functions and also automatically blocks intrusion attacks.
- NGIPS should include IPS functionality as well as the following capabilities:
- Real-time contextual awareness
- Advanced threat protection
- Intelligent security automation
- Unparalleled performance and scalability
- AVC and URL filtering
With the acquisition of Sourcefire in 2013, Cisco added the Firepower NGIPS to its portfolio.
| Features | Advanced Features |
| Real-time contextual awareness | Centralized management |
| Advanced threat protection and remediation | Global threat intelligence from Talos |
| Intelligent security automation | Snort IPS detection engine |
| Unparalleled performance and scalability | High availability and clustering |
| AVC | Third-party and open-source ecosystem |
| URL filtering | Integration with ISE: Quarantine, Unquarantine, Shutdown |
NGFW
- A firewall is a network security device that monitors incoming and outgoing network traffic and allows/blocks traffic by performing simple packet filtering and stateful inspection based on ports and protocols.
- Block threats such as advanced malware and application-layer attacks.
- A NGFW firewall must include:
- Standard firewall capabilities such as stateful inspection
- Integrated IPS
- Application-level inspection (to block malicious or risky apps)
- Leverage external security intelligence to address evolving security threats
NGFW: Management Options
- For FTD or Firepower Services software:
- Firepower Management Center (FMC) API
- Firepower Device Manager (FDM) for small appliances
- For ASA software:
- CLI
- Cisco Security Manager (CSM)
- ASDM
- Cisco Defense Orchestrator
FTD or Firepower Services software CLI configuration is not supported. CLI is only available for initial setup and troubleshooting purposes.
FMC
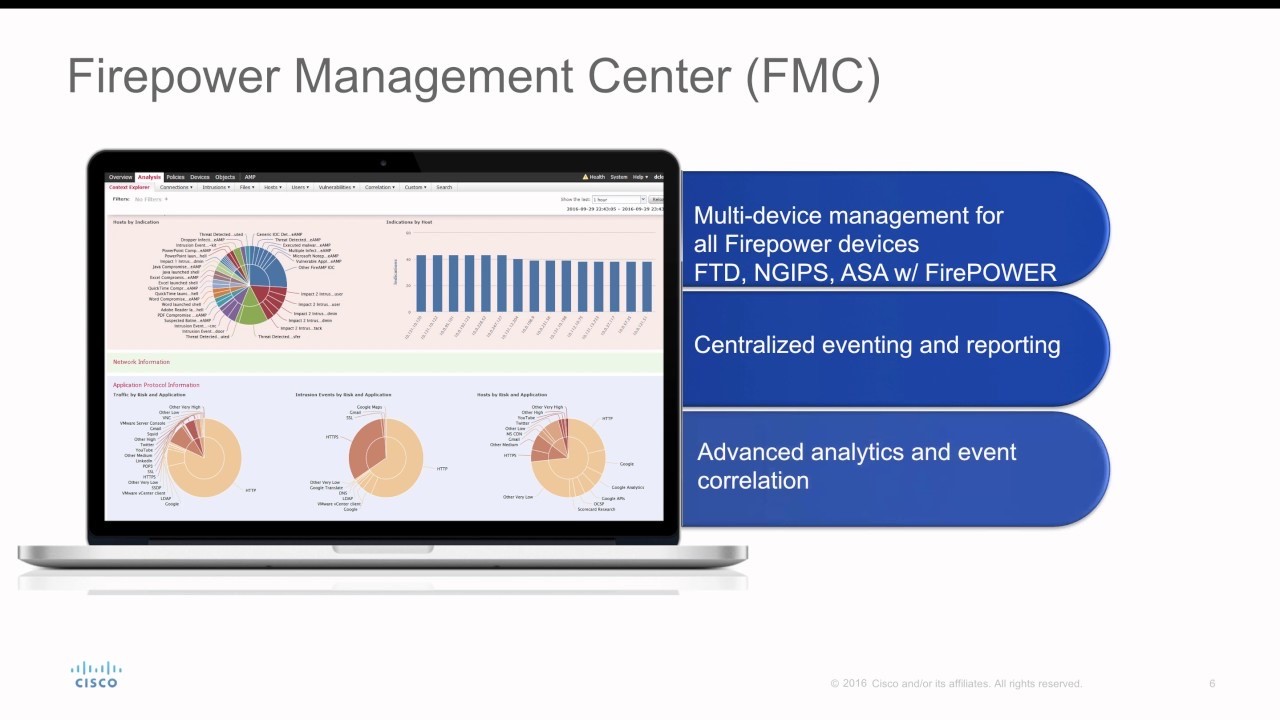
- A centralized management platform that aggregates and correlates threat events, contextual information, network device performance data.
- The FMC performs event and policy management:
- Firepower NGFW and NGFWv
- Firepower NGIPS and NGIPSv
- Firepower Threat Defense for ISR
- ASA with Firepower Services
- AMP
Stealthwatch – Visibility
- A collector and aggregator of network telemetry data that performs network security analysis and monitoring to automatically detect threats that manage to infiltrate a network as well as the ones that originate from within a network.
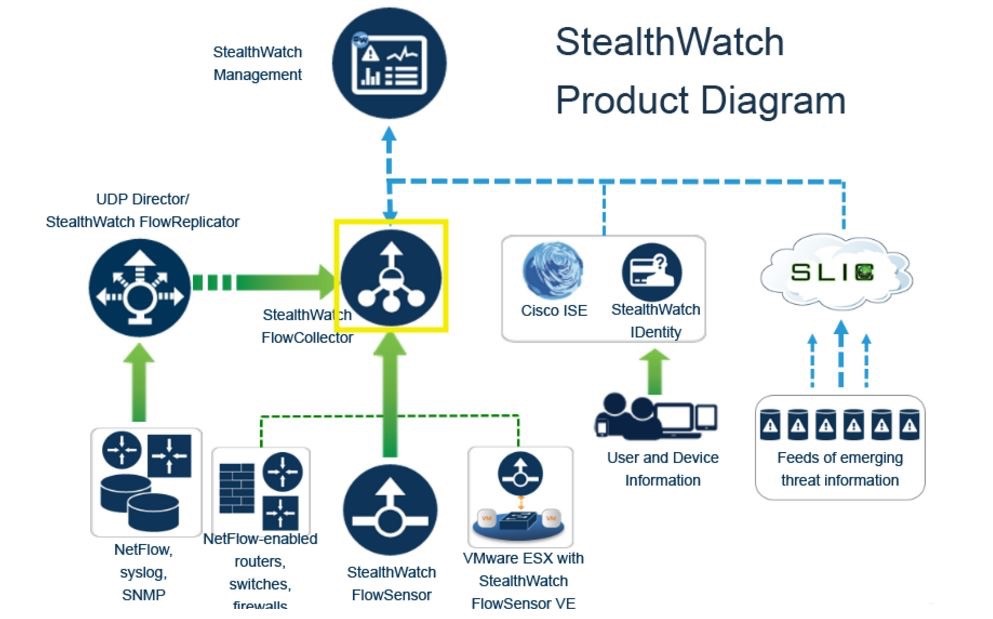
- Two offerings available for Stealthwatch:
- Stealthwatch Enterprise
- Stealthwatch Cloud
- LanCope Stealwatch
Stealthwatch Enterprise
Provides real-time visibility into activities occurring within the network.
- At the core are the Flow Rate License, the Flow Collector, Management Console, Flow Sensor. Optional but recommended components include the following:
- Stealthwatch Threat Intelligence
- Stealthwatch Endpoint
- Stealthwatch Cloud
- Offers the following benefits:
- Real-time threat detection
- Incident response and forensics
- Network segmentation
- Network performance and capacity planning
- Ability to satisfy regulatory requirements
Requires the following components:
- Flow Rate License – required for the collection, management, and analysis of flow telemetry data and aggregates flows at the Stealthwatch Management Console, as well as to define the volume of flows that can be collected
- Flow Collector – collects and analyzes enterprise telemetry data and other types of flow data.
- Stealthwatch Management Console (SMC) – the control center that aggregates, organizes, and presents analysis from up to 25 Flow Collectors, ISE, and other sources.
Optional Stealthwatch Enterprise components include the following:
- Flow Sensor
- UDP Director
Stealthwatch Cloud
Provides the visibility and continuous threat detection required to secure the onpremises, hybrid, and multicloud environments. q Consists of two primary offerings:
- Public Cloud Monitoring – provides visibility and threat detection in AWS, GCP, and MS Azure cloud infrastructures. It is a SaaS-based solution that can be deployed easily and quickly.
- Private Network Monitoring – provides visibility and threat detection for the onpremises network, delivered from a cloud-based SaaS solution.
Consumes metadata only. The actual packet payloads are never retained or transferred outside the network.
ISE vs MS NPS (Radius)
A security policy management platform that provides highly secure NAC to users and devices across wired, wireless, VPN connections.
| ISE Features | |
| Streamlined network visibility | Streamlined device onboarding |
| DNA Center integration | Internal certificate authority |
| Centralized secure network access control (authorization) | Device profiling |
| Centralized device access control (digital certificate) | Endpoint posture service |
| TrustSec | Active Directory support |
| Guest lifecycle management | Platform Exchange Grid (pxGrid) |
ISE Example
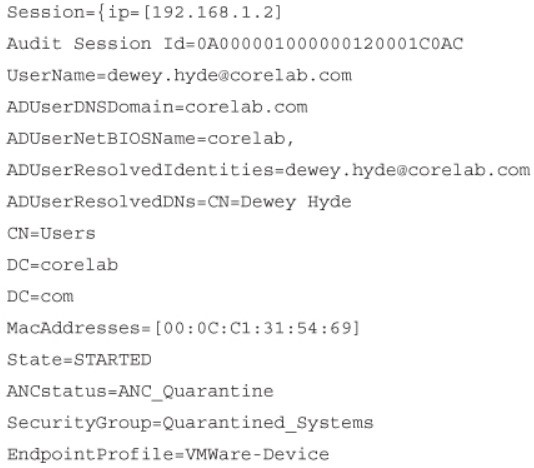
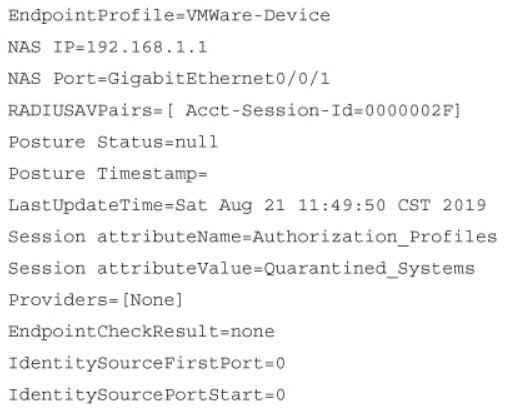
Example 25-1 Contextual Information from Cisco ISE Session Directory