Network Access Control (NAC)
describes technologies such as 802.1x, Web Authentication (WebAuth), MAC Authentication Bypass (MAB), TrustSec and MACsec.
Describes multiple NAC:
- 802.1x
- MAB
- WebAuth
- TrustSec
- MACsec.
802.1x
- IEEE 802.1x (Dot1x): a standard for port-based network access control that provides an authentication mechanism for LANs/WLANs.
- Comprises the following:
- Extensible Authentication Protocol (EAP) – This message format and framework provides an encapsulated transport for authentication parameters.
- EAP method (EAP type) – Different authentication methods can be used with EAP.
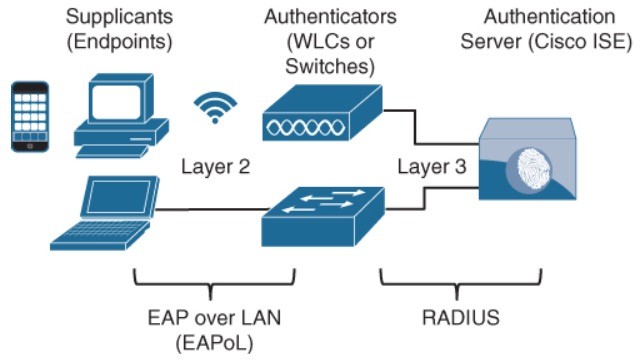
- EAP over LAN (EAPoL) – This L2 encapsulation protocol for the transport of EAP messages over IEEE 802 wired/wireless networks.
- RADIUS protocol – used by EAP.
802.1x Roles
- Supplicant – Software on the endpoint communicates and provides identity credentials through EAPoL with the authenticator.

- Authenticator – A network access device (switch/WLC) controls access to the network based on the authentication status of the user/endpoint.
- Authentication server
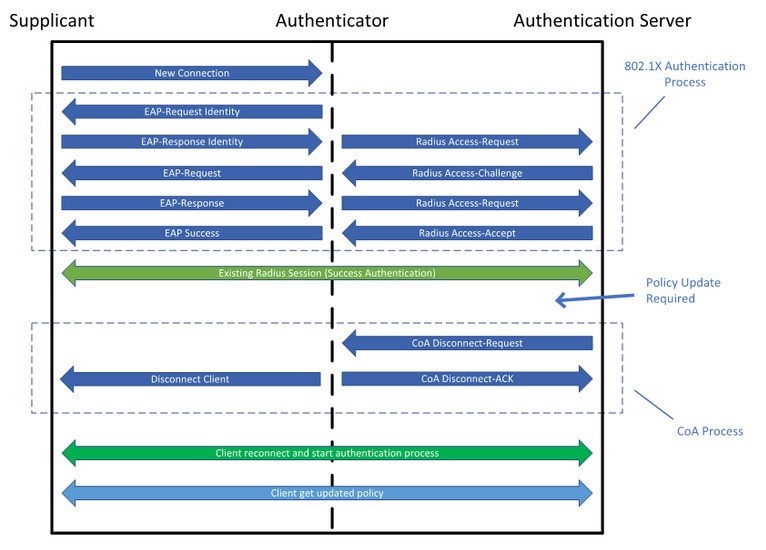
802.1x Authentication
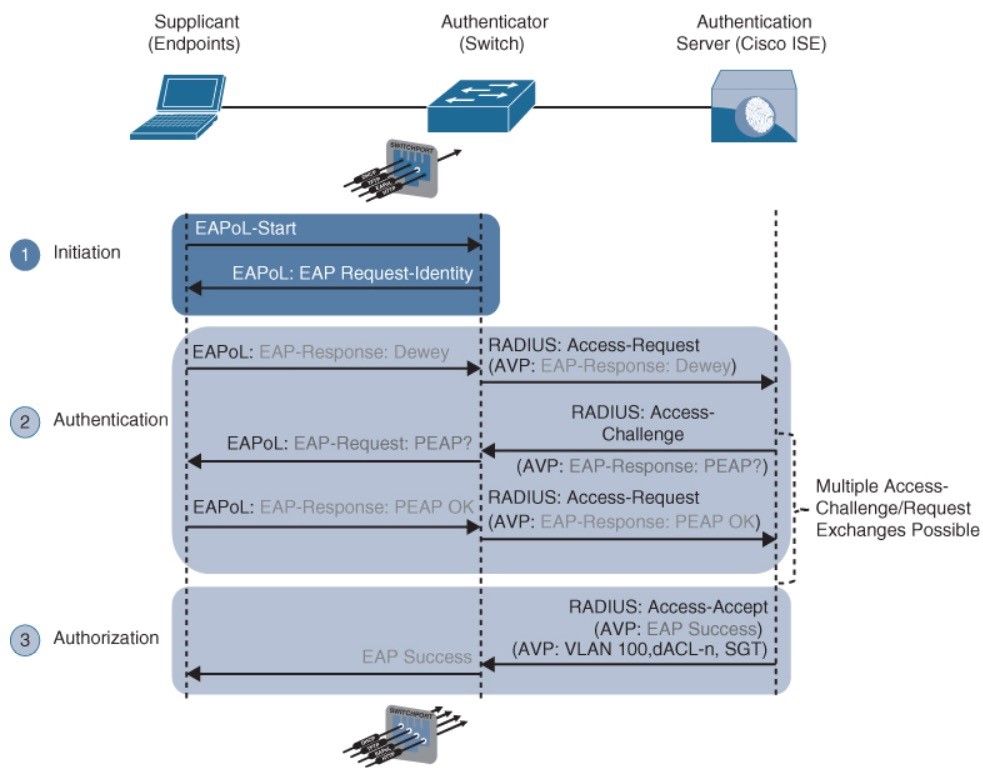
- Step 1. When the authenticator notices a port coming up, it starts the authentication process by sending periodic EAP-request/identify frames.
- Step 2. The authenticator relays EAP messages between the supplicant and the authentication server.
- Step 3. If authentication is successful, the authentication server returns a RADIUS access-accept message.
EAP Methods
EAP Methods
- EAP challenge-based authentication method
- Extensible Authentication Protocol-Message Digest 5 (EAP-MD5)
- EAP TLS authentication method
- Extensible Authentication Protocol-Transport Layer Security (EAP-TLS)
- EAP tunneled TLS authentication methods
- Extensible Authentication Protocol Flexible Authentication via Secure Tunneling (EAP-FAST)
- Extensible Authentication Protocol Tunneled Transport Layer Security (EAP-TTLS)
- Protected Extensible Authentication Protocol (PEAP)
- EAP inner authentication methods
- EAP Generic Token Card (EAP-GTC)
- EAP Microsoft Challenge Handshake Authentication Protocol Version 2 (EAP-MSCHAPv2)
- EAP TLS.
EAP Methods
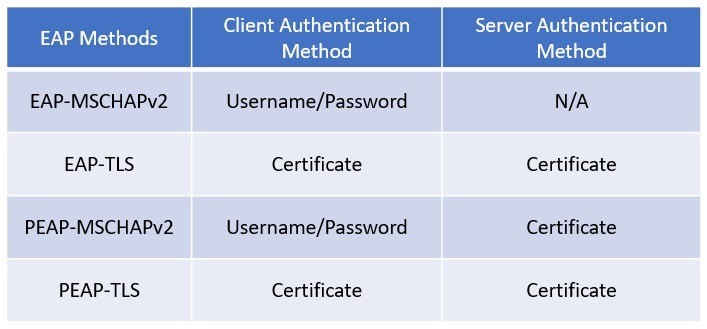
- EAP-MD5 – uses the MD5 message-digest algorithm to hide the credentials in a hash.
- EAP-TLS – uses the TLS PKI certificate authentication mechanism to provide mutual authentication of supplicant to authentication server and authentication server to supplicant.
- PEAP – Only the authentication server requires a certificate. PEAP forms an encrypted TLS tunnel between the supplicant and the authentication server
After the tunnel has been established, PEAP uses one of the following EAP authentication inner methods to authenticate the supplicant through the outer PEAP TLS tunnel:
| PEAP Authentication | ||
| EAP-MSCHAPv2 (PEAPv0) | EAP-TLS | EAP-TTLS |
| EAP-GTC (PEAPv1) | EAP-FAST | |
EAP Chaining
- EAP-FAST includes the option of EAP chaining:
- Supports machine and user authentication inside a single outer TLS tunnel
- Enables machine and user authentication to be combined into a single overall authentication result
- Allows the assignment of greater privileges or posture assessments to users who connect to the network using corporate managed devices
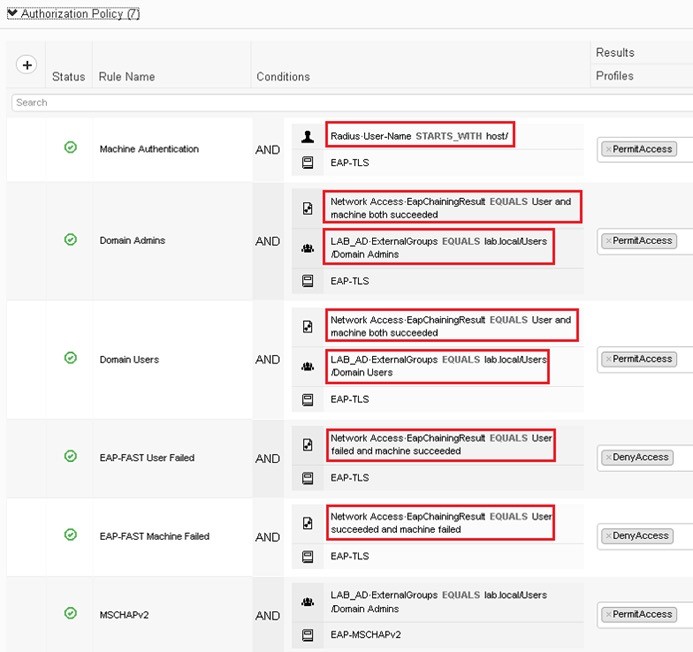
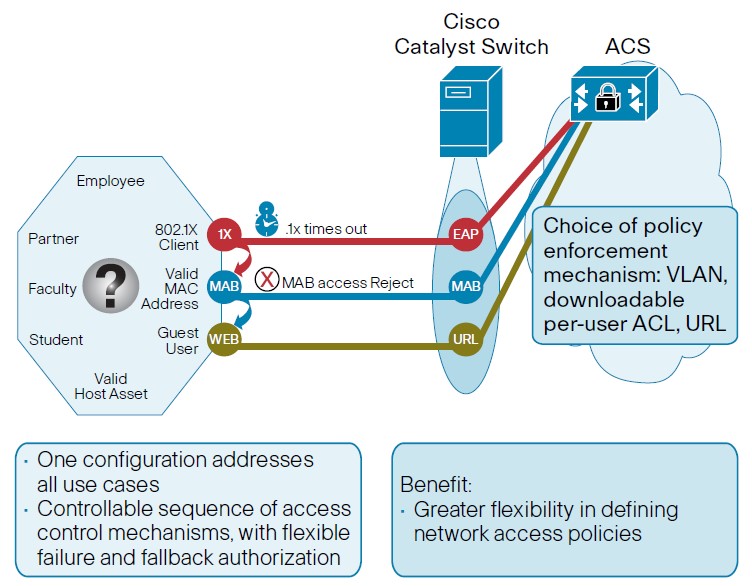
MAB
An access control technique that enables port-based access control using the endpoint MAC.
- Step 1. Switch initiates authentication by sending an EAPoL identity request message to the endpoint every 30s (default).
- Step 2. Switch begins MAB by opening the port to accept a single packet from which it will learn the source MAC.
- Step 3. RADIUS server determines whether the device granted access to the network
MAB
- MAC are easily spoofed. MAB authenticated endpoints should be given very restricted access.
- Should only be allowed to communicate to the networks and services that the endpoints are required to speak to.
- If the authenticator is a Cisco switch, then many authorization options :
- dACLs
- dVLAN
- SGT tags
WebAuth
- Used for endpoints that try to connect to the network, might not have 802.1x supplicants and might not know the MAC to perform MAB.
-
- WebAuth, like MAB, can be used as a fallback authentication mechanism for 802.1x.
- If both MAB and WebAuth are configured as fallbacks for 802.1x, when 802.1x times out a switch first attempts to authenticate through MAB, and if it fails, the switch attempts to authenticate with WebAuth.
- Unlike MAB, WebAuth is only for users and not devices since it requires a web browser and manual username and password entry.
- Two types:
-
- Local WebAuth
- Centralized Web Authentication with ISE
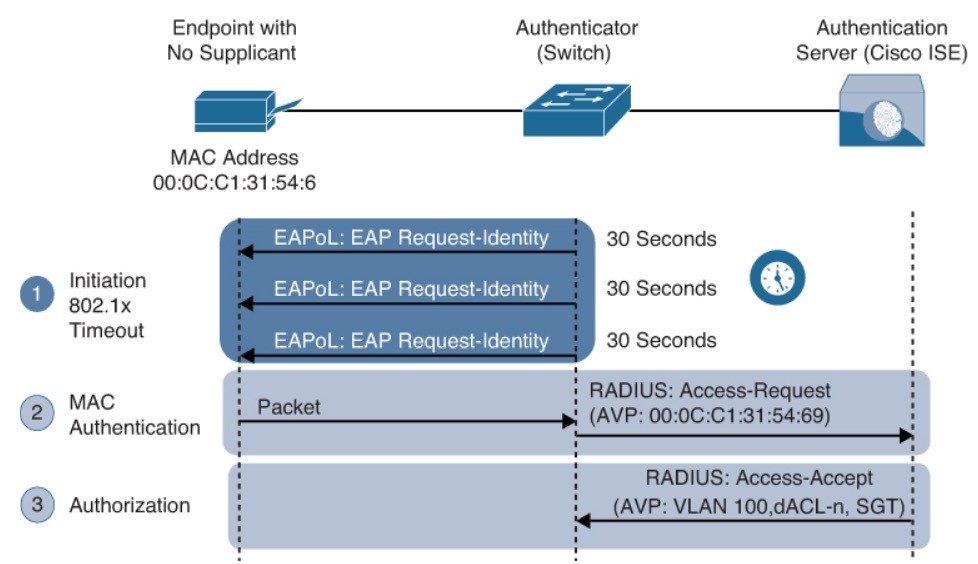
Local WebAut LWA
- The switch (or WLC) redirects web traffic (HTTP and/or HTTPS) to a locally hosted web portal running in the switch. End user can enter a username and a password.
- When the switch sends the login credentials on behalf of the user, it is considered to be LWA.
- The LWA web portals are not customizable.
Local WebAuth
- With Cisco switches, there is no native support for advanced services such as acceptable use policy (AUP), acceptance pages, password changing capabilities, device registration, and self-registration. For those capabilities, a centralized web portal is required.
- LWA does not support VLAN assignment; it supports only ACL assignment.
- LWA doesn’t support CoA feature to apply new policies.
- Access policies cannot be changed based on posture/profiling state, and even administrative changes cannot be made as a result of malware to quarantine the endpoint.
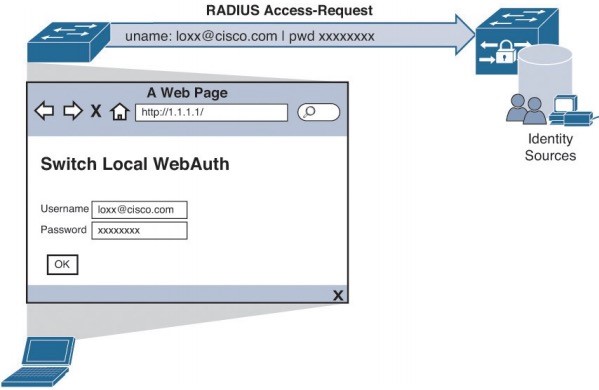
Central Web Auth CWA with ISE
- Cisco create CWA to overcome LWA’s deficiencies.
- CWA supports:
- CoA for posture profiling, dACL and VLAN authorization options.
- All the advanced services: client provisioning, posture assessments, acceptable use policies, password changing, self-registration, device registration.
- CWA is only for endpoints that have a web browser, user manually enter a username and a password.
- With CWA, WebAuth and guest VLAN functions remain mutually exclusive.
CWA with ISE
Authentication for CWA is different from authentication for LWA.
- Step 1. The endpoint entering the network does not have a configured supplicant or the supplicant is misconfigured.
- Step 2. The switch performs MAB, sending the RADIUS access-request to the authentication server.
- Step 3. ISE sends the RADIUS result, including a URL redirection, to the centralized portal on the ISE server itself.
- Step 4. The endpoint assigned an IP address, DNS server, default gateway using DHCP.
- Step 5. The end user opens a browser and enters credentials into the centralized web portal.
- Step 6. ISE sends a re-authentication CoA-reauth to the switch.
- Step 7. The switch sends a new MAB request with the same session ID to ISE. ISE sends the final authorization result to the switch for the end user.
CWA with ISE
Enhanced Flexible Authentication (FlexAuth)
- By default, a switch configured with 802.1x, MAB, and WebAuth attempts 802.1x authentication first, followed by MAB, finally WebAuth.
- If an endpoint does not support 802.1x tries to connect to the network, it needs to wait for a considerable amount of time before WebAuth offered as option. • Enhanced FlexAuth (Access Session Manager) allow multiple authentication methods concurrently (802.1x & MAB) so that endpoints can be authenticated and brought online more quickly.
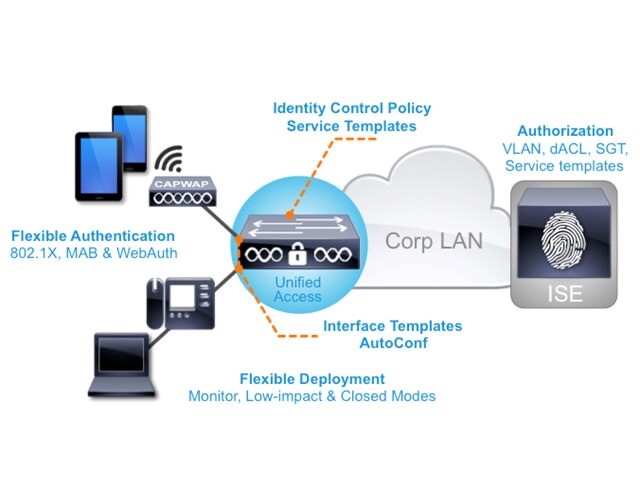
Identity-Based Networking Services (IBNS) 2.0
- An integrated solution that offers authentication, access control, and user policy enforcement with a common end-to-end access policy that applies to both wired and wireless. It is a combination of the following:
-
- Enhanced FlexAuth (Access Session Manager)
-
- Common Classification Policy Language (C3PL)
-
- ISE
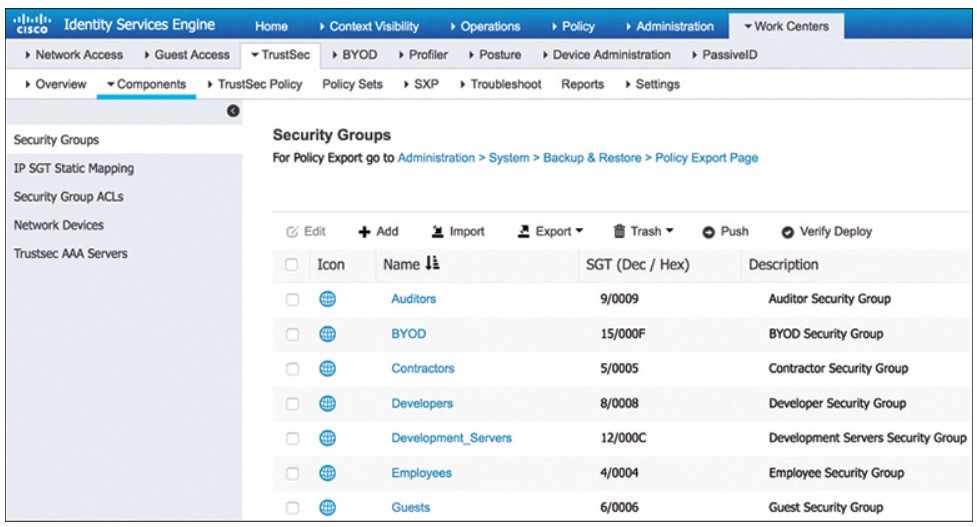
TrustSec
A next-generation access control enforcement solution to address the growing operational challenges related to maintaining firewall rules and ACLs.
- TrustSec uses SGT tags to perform ingress tagging and egress filtering to enforce access control policy.
- ISE assigns the SGT tags to users/devices that are successfully authenticated and authorized through 802.1x, MAB, WebAuth.
- The SGT tag assignment is delivered to the authenticator as an authorization option (same way as a dACL).
- After the SGT tag assigned, an access enforcement policy (allow or drop) based on the SGT tag can be applied at any egress point of the TrustSec network.
- SGT tags represent the context of the user, device, use case, or function. This means SGT tags are often named after particular roles or business use cases.
- SGT referred to as scalable group tags in SD-Access.
TrustSec
- Configuration occurs in three phases:
-
- Ingress classification
- Propagation
- Egress enforcement
- The SGT name available on ISE and network devices to create policies; what is actually inserted into a L2 frame SGT tag is a numeric value.
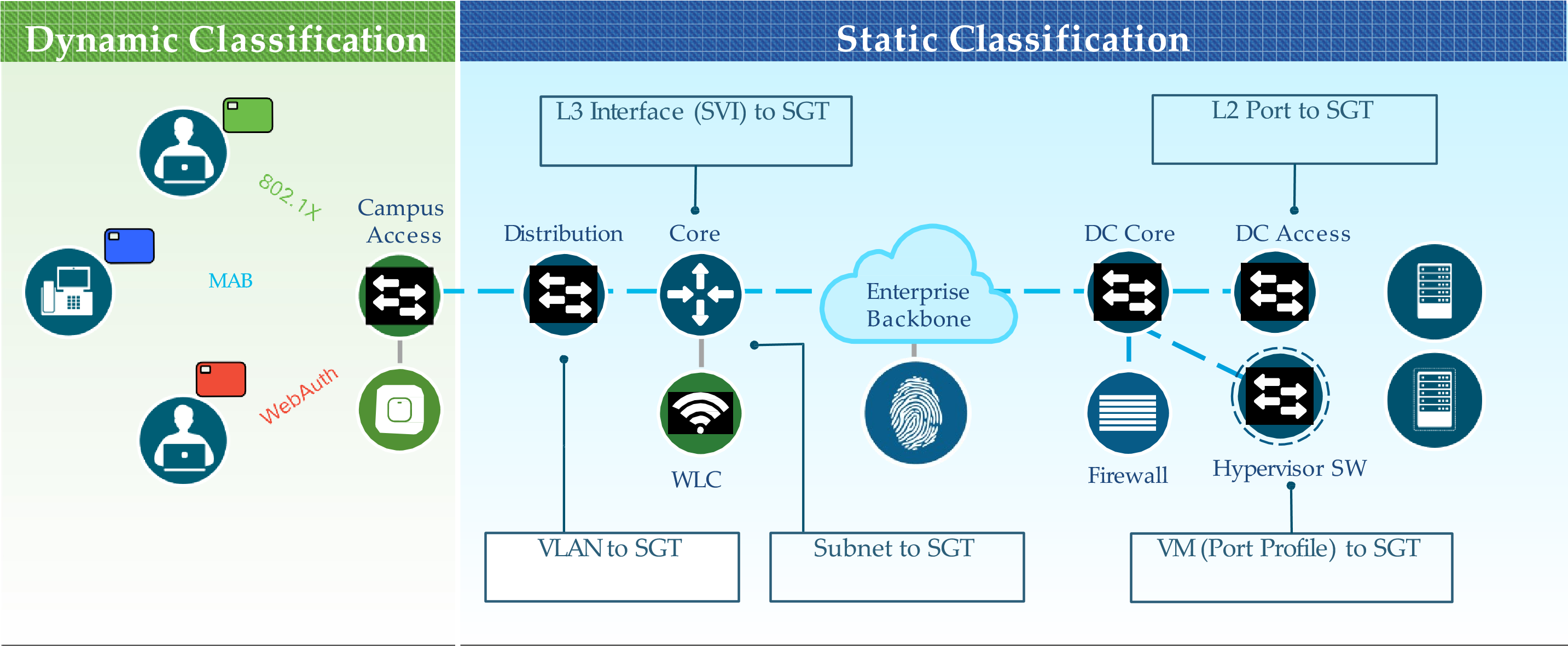
Ingress Classification
The process of assigning SGT tags to users, endpoints, or other resources as they ingress the TrustSec network:
- Dynamic assignment – The SGT assigned dynamically and can be downloaded as an authorization option from ISE.
- Static assignment – In environments such as a data center that do not require 802.1x, MAB, or WebAuth, dynamic SGT assignment is not possible. Static assignment on a device can be one of the following:
- IP to SGT tag
- Layer 3 logical interface to SGT tag
- Subnet to SGT tag
- Port to SGT tag
- VLAN to SGT tag
- Port profile to SGT tag
- Layer 2 interface to SGT tag
- As an alternative to assigning an SGT tag to a port, ISE added the ability to centrally configure a database of IP addresses and their corresponding SGT tags.
- Network devices (SGT capable) can download the list from ISE.
Two ways to assign SGT

Propagation
- The process of communicating the mappings to the TrustSec network devices that will enforce policy based on SGT tags.
- Two methods available for propagating an SGT tag—inline tagging (native tagging) and the Cisco-created SGT Exchange Protocol (SXP):
• Inline tagging – With inline tagging, a switch inserts the SGT tag inside a frame to allow upstream devices to read and apply policy. 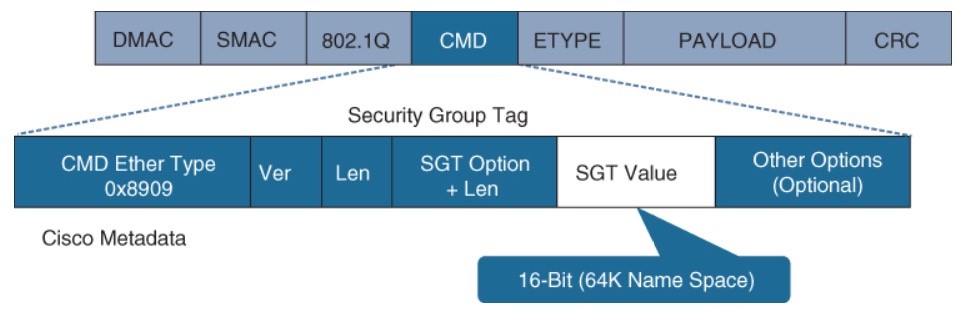
Propagation
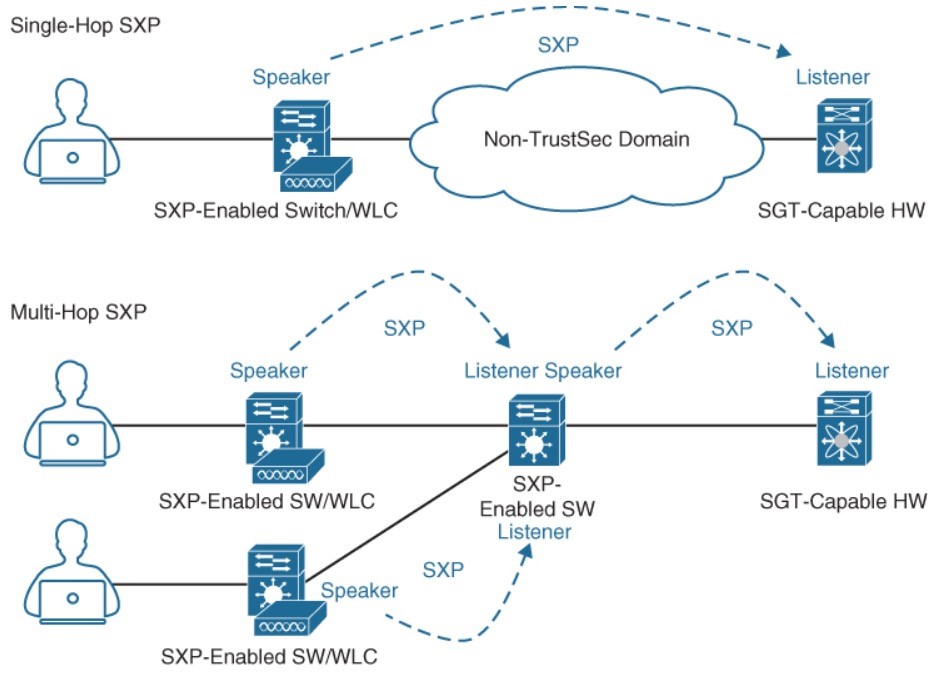
- SXP propagation – a TCPbased peer-to-peer protocol used for network devices that do not support SGT inline tagging in hardware.
- Non-inline tagging switches also have an SGT mapping database to check packets against and enforce policy.
- Speaker: The SXP peer that sends IP-to-SGT binding.
- Listener: The IP-to-SGT binding receiver.
- SXP connections can be single-hop or multi-hop.
Propagation: SXP Example
- It also shows a switch that is not capable of inline tagging and that uses SXP to update the upstream switch.
- In both cases, the upstream switch continues to tag the traffic throughout the infrastructure.
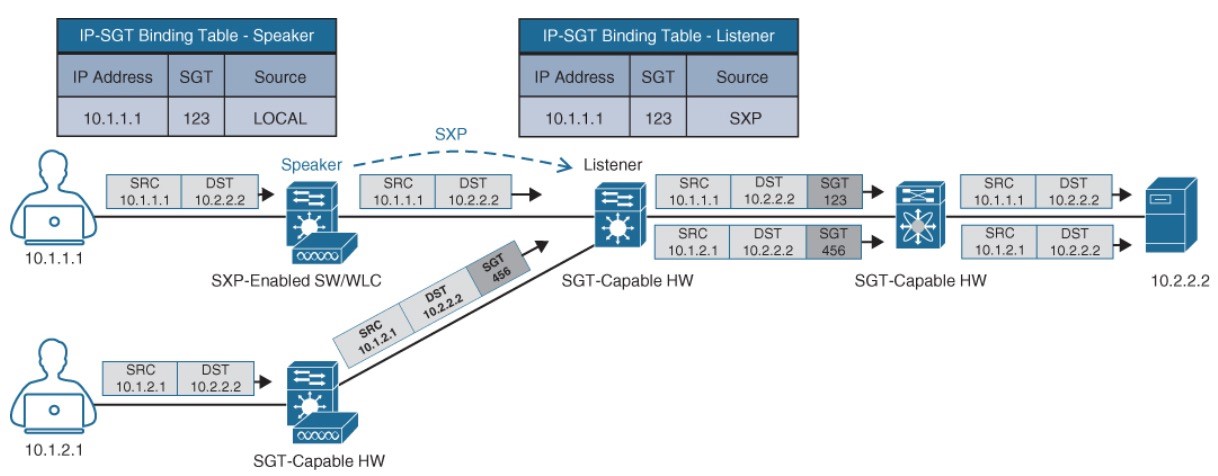
access switch that supports native tagging. The packets get tagged on the uplink port and through the infrastructure.
Propagation: SXP Peering
- User is connected to a switch that does not support inline tagging or SXP. This means an SGTto-IP binding cannot be assigned to the user on the switch.
- The solution is for ISE to assign an SGT to the user by sending a mapping through SXP to an upstream device that supports TrustSec.
- ISE also supports assigning the SGT mapping information to an upstream device through pxGrid.
SXP Peering Between ISE and TrustSec-Capable Devices 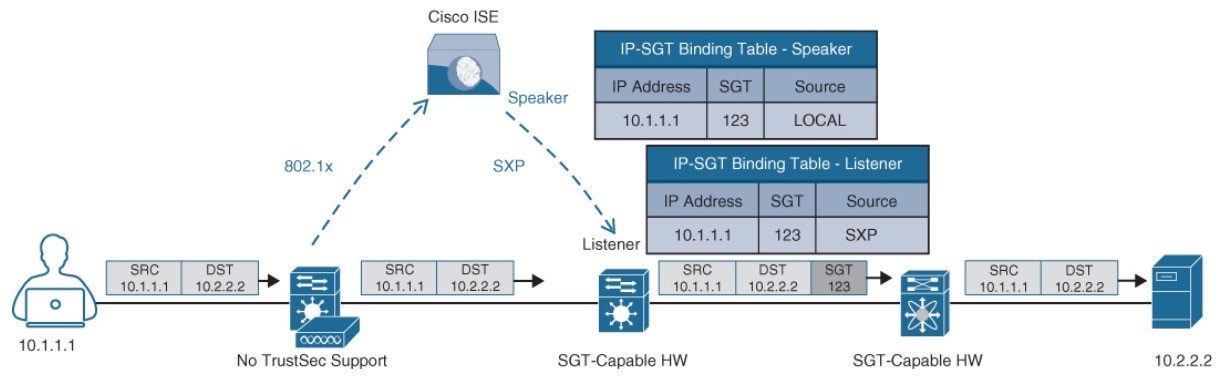
Egress Enforcement
After the SGT tags assigned (classification) and being transmitted across the network, policies can be enforced at the egress point of the TrustSec network.
- Security Group ACL (SGACL) – Provides enforcement on routers and switches. Access lists provide filtering based on source and destination SGT tags.
- Security Group Firewall (SGFW) – Provides enforcement on firewalls (ASA/NGFW). Requires tag-based rules to be defined locally on the firewall.
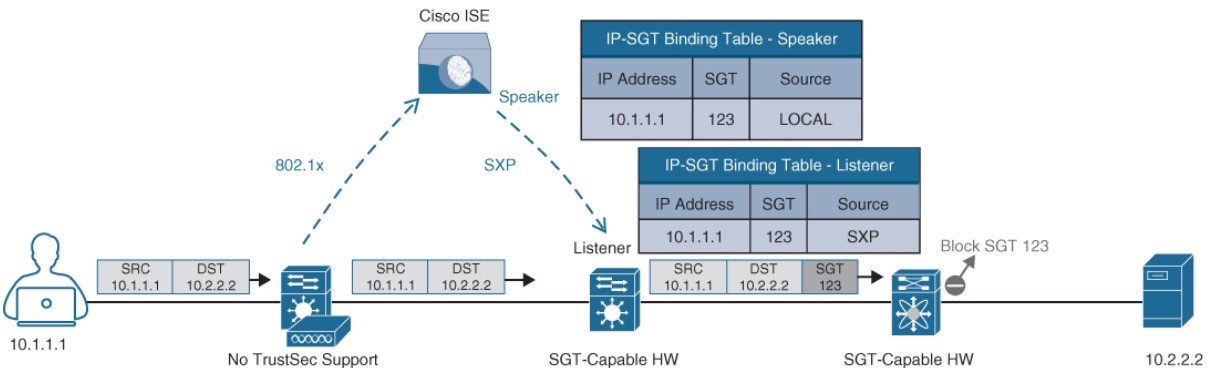
Egress Enforcement: SGACL
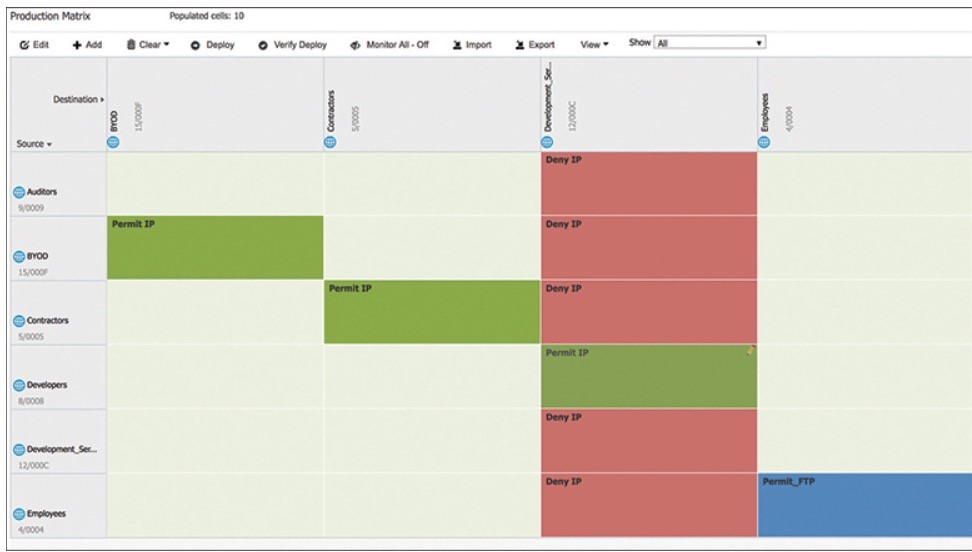
- Figure illustrates an SGACL egress policy production matrix from ISE that allows the defined SGACL enforcements to be visualized.
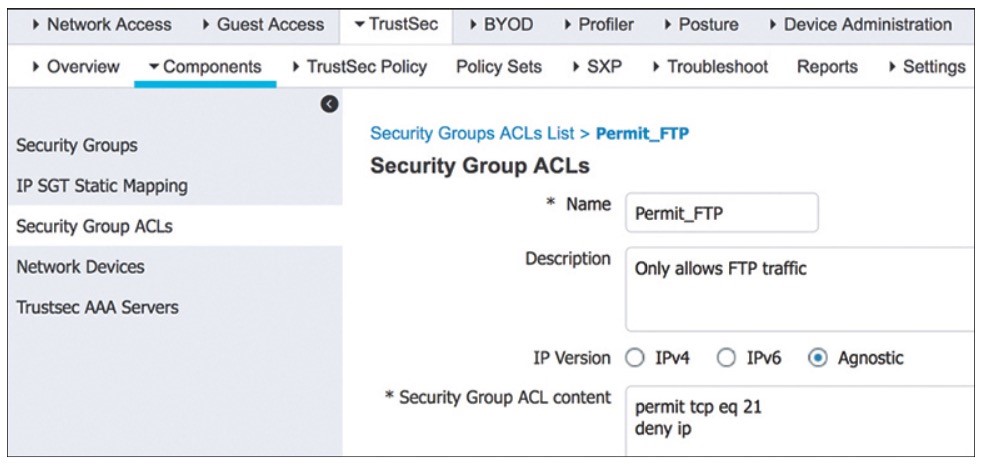
- Figure shows the SGACL Permit_FTP configuration on ISE, which is only allowing FTP traffic (TCP p21) and denying all other traffic.
Egress Enforcement Example
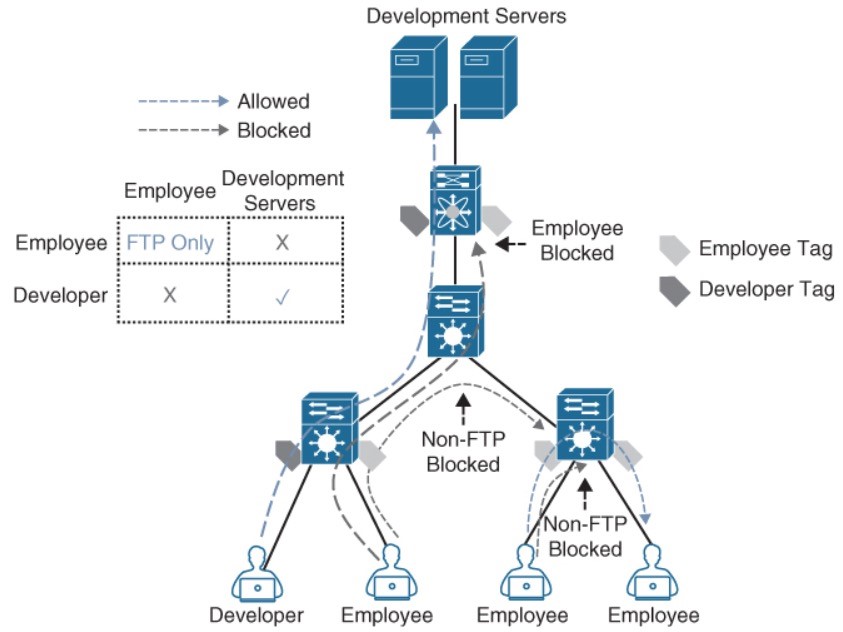
- Traffic blocked on egress and not on ingress.
- FTP is the only protocol allowed between employees, while any other type of traffic is blocked.
- For the employees connected to the same switch, the switch is acting as the ingress and egress point.
- Only developers have access to the development servers, and any employee trying to access them is blocked.
MACsec
- An IEEE 802.1AE standards-based L2 hop-by-hop encryption method.
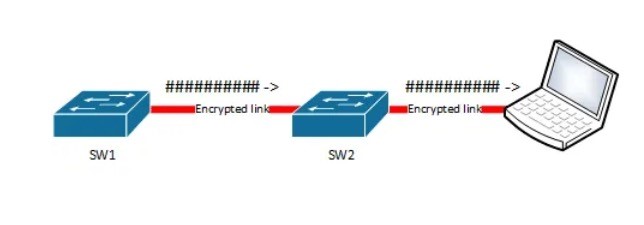
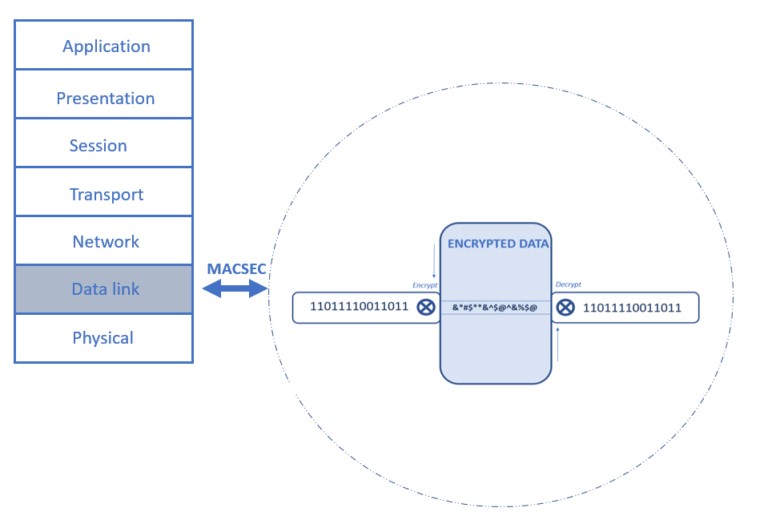
- The traffic encrypted only on the wire between two MACsec peers and is unencrypted as it is processed internally within the switch.
- Allows the switch to look into the inner packets for things like SGT tags to perform packet enforcement or QoS prioritization.
- Leverages onboard ASICs to perform the encryption/decryption rather than offload to a crypto engine, as with IPsec.
- Based on the Ethernet frame format; however, an additional 16-byte MACsec Security Tag field (802.1AE header) and a 16-byte Integrity Check Value (ICV) field added.
- MACsec provides authentication using Galois Method Authentication Code (GMAC) or authenticated encryption using Galois/Counter Mode Advanced Encryption Standard (AES-GCM).
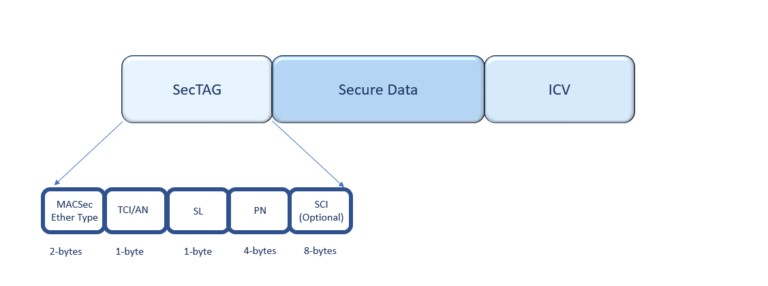
MACsec Illustrated
MACsec frame format and how it encrypts the TrustSec SGT tag. 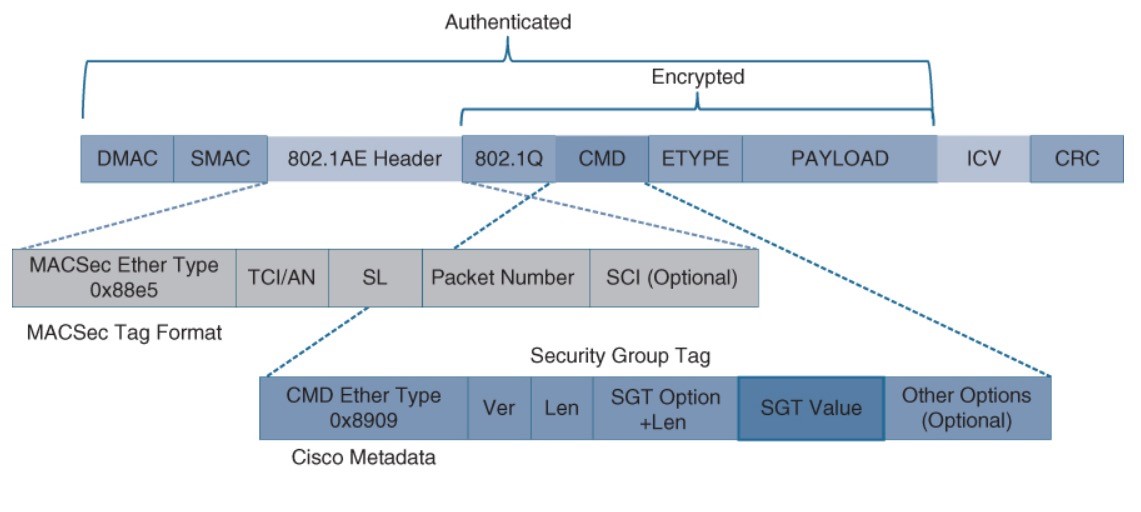
MACsec Tags
- MACsec EtherType (first two octets) – Set to 0x88e5, designating the frame as a MACsec frame
- TCI/AN (third octet) – Tag Control Information/Association Number field, designating the version number if confidentiality or integrity is used on its own
- SL (fourth octet) – Short Length field, the length of the encrypted data
- Packet Number (octets 5–8) – The packet number for replay protection and building of the initialization vector
- SCI (octets 9–16) – Secure Channel Identifier, for classifying the connection to the virtual port
Two MACsec keying mechanisms:
- Security Association Protocol (SAP) – A proprietary Cisco keying protocol used between Cisco switches.
- MACsec Key Agreement (MKA) protocol – provides the required session keys and manages the required encryption keys.
Downlink MACsec
The encrypted link between an endpoint and a switch.
- The encryption between the endpoint and the switch is handled by the MKA keying protocol.
- Requires a MACsec-capable switch and a MACsec-capable supplicant on the endpoint (AnyConnect).
- The encryption on the endpoint may be handled in hardware/software, using the main CPU for encryption and decryption.
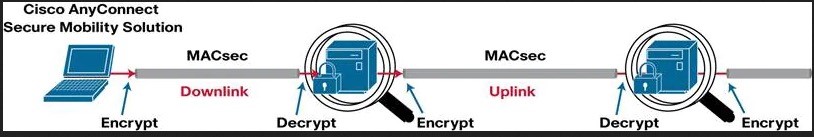
Downlink MACsec
- The switch has the ability to force encryption, make encryption optional, or force nonencryption.
- This setting may be configured manually per port (not common) or dynamically as an authorization option from ISE.
- If ISE returns an encryption policy with the authorization result, the policy issued by ISE overrides anything set using the switch CLI.
Uplink MACsec
Uplink MACsec is the term for encrypting a link between switches with 802.1AE.
- By default, uplink MACsec uses Cisco proprietary SAP encryption. The encryption is the same AES-GCM-128 encryption used with both uplink and downlink MACsec.
- Uplink MACsec may be achieved manually or dynamically.
- Dynamic MACsec requires 802.1x authentication between the switches.
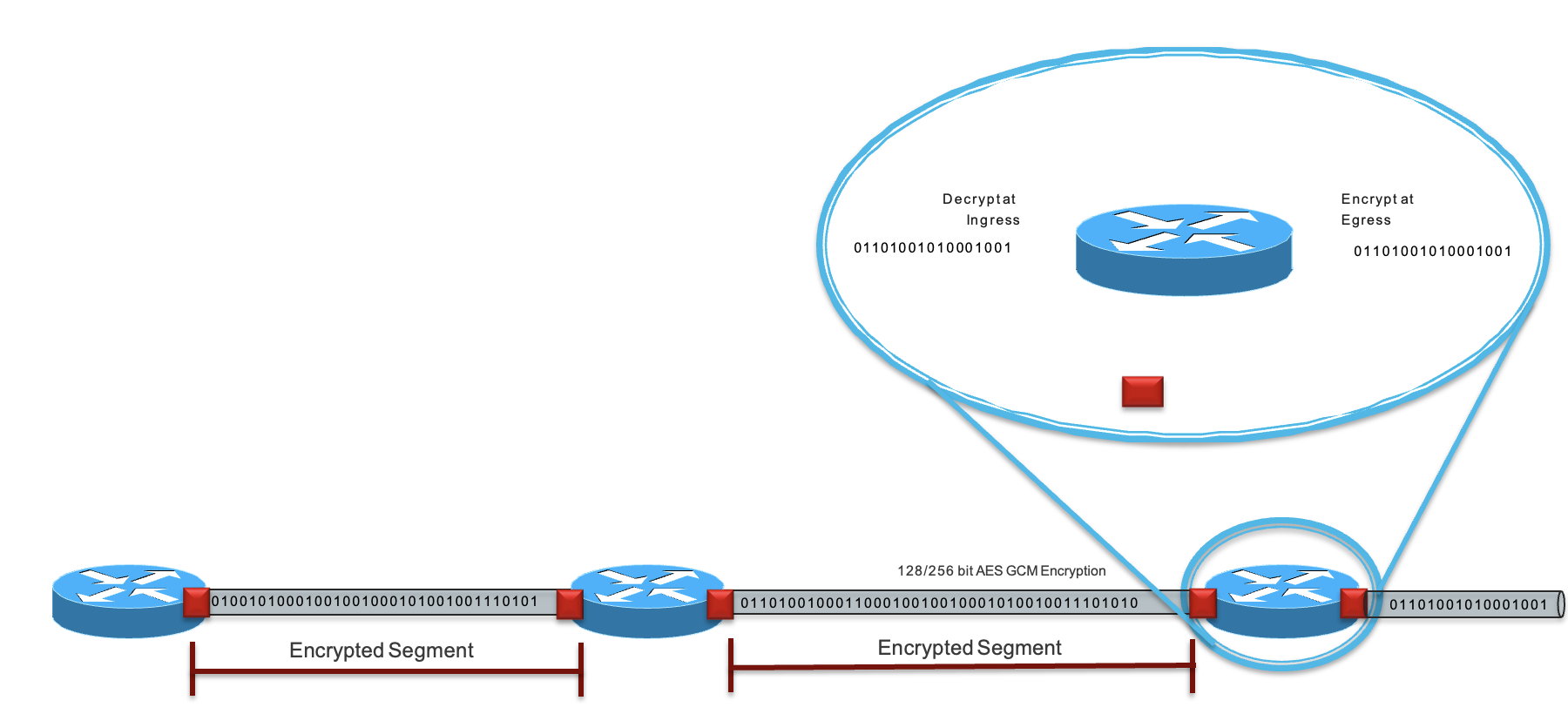
What is MAC Security (MACsec)?
Hop-by-Hop Encryption via IEEE 802.1AE
- Hop-by-Hop Encryption model -Packets are decrypted on ingress port -Packets are in the clear in the device -Packets are encrypted on egress port
- Supports 1/10G, 40G, 100G encryption speeds
- Data plane (IEEE 802.1AE) and control plane (IEEE 802.1x-Rev)
- Transparent to IPv4/v6, MPLS, multicast, routing
- Encryption aligns with Link PHY speed (Ethernet) 128/256 bit AES GCM Encryption
What is “WAN MACsec?
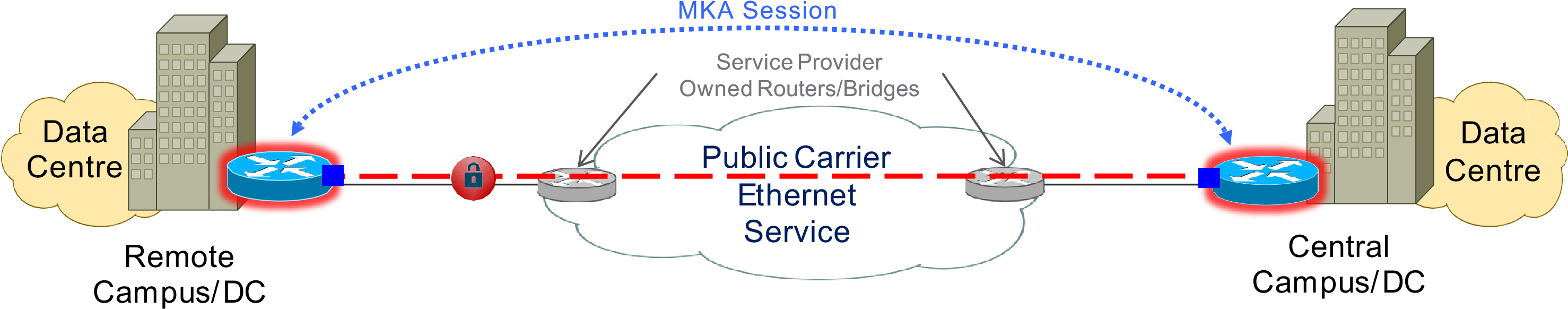
- Leverage MACsec over “public” standard Ethernet transport
- Optimize MACsec + WAN features to accommodate running over public
- Target “line-rate” encryption for high-speed applications MACsec Capable Router
- Inter DC, MPLS WAN links, massive data projects MACsec Capable PHY
- Targets 100G, but support 1/10/40G as wellSP TransportOwned DeviceEthernet
New Enhancements to 802.1AE for WAN/Metro-E Transport
- AES-256 (AES/GCM) support – 1/10/40 and 100G rates
- Target Next Generation Encryption (NGE) profile that currently leverages public NSA Suite B
- Standards Based MKA key framework
- (defined in 802.1X-2010) within Cisco security development (Cisco “NGE”)
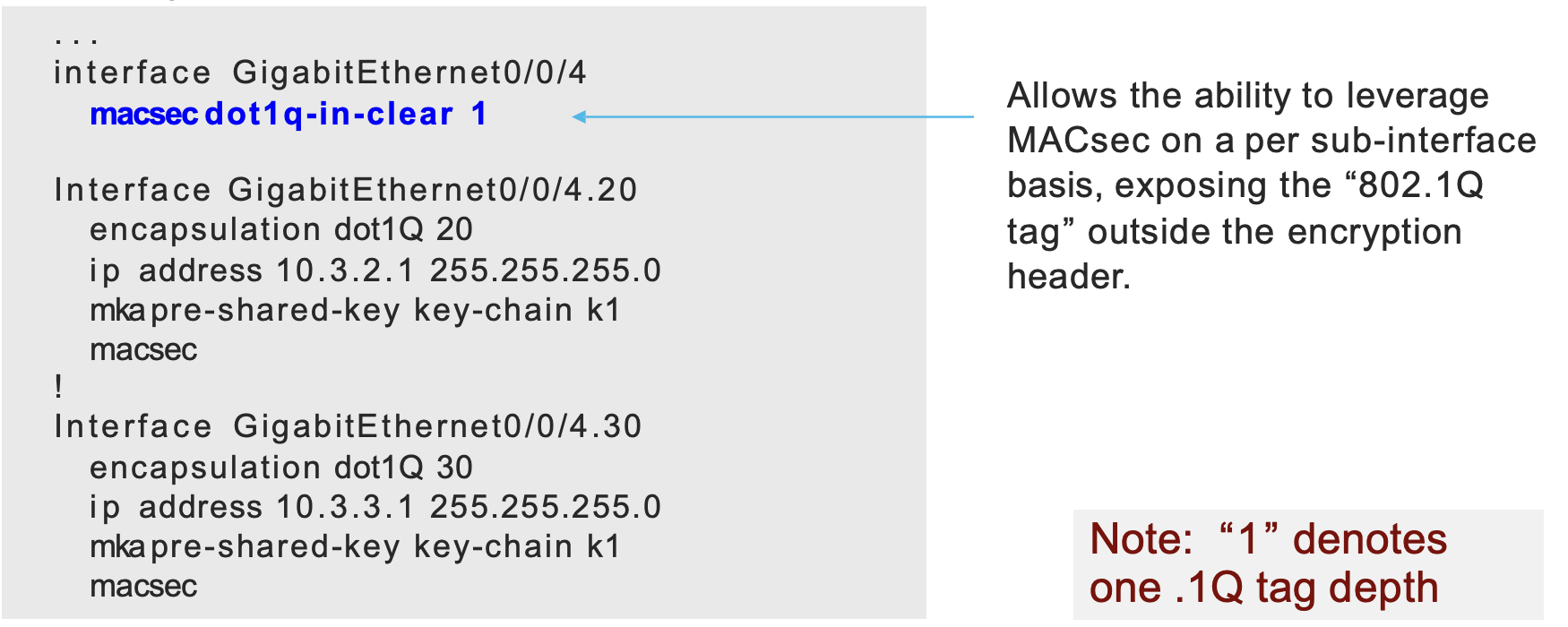
- Ability to support 802.1Q tags in clear
- Offset 802.1Q tags in clear before encryption (2 tags is optional)
- Vital Network Features to Interoperate over Public Carrier Ethernet Providers
- 802.1Q tag in the clear
- Ability to change MKA EAPoL Destination Address type
- Ability to change MKA Ether-type value
- Ability to configure Anti-replay window sizes
- System Interoperability
- Create a common MACsec integration among all MACsec platforms in Cisco and Open Standards
WAN MACsec Use Case – 802.1Q Tag in the Clear
- Leverage 802.1Q for logical connectivity to each site
- This is analogous to “channelization” in SONET MACsec
- Router leverages IP sub-interface tag per location (80PHY 2.1Q)
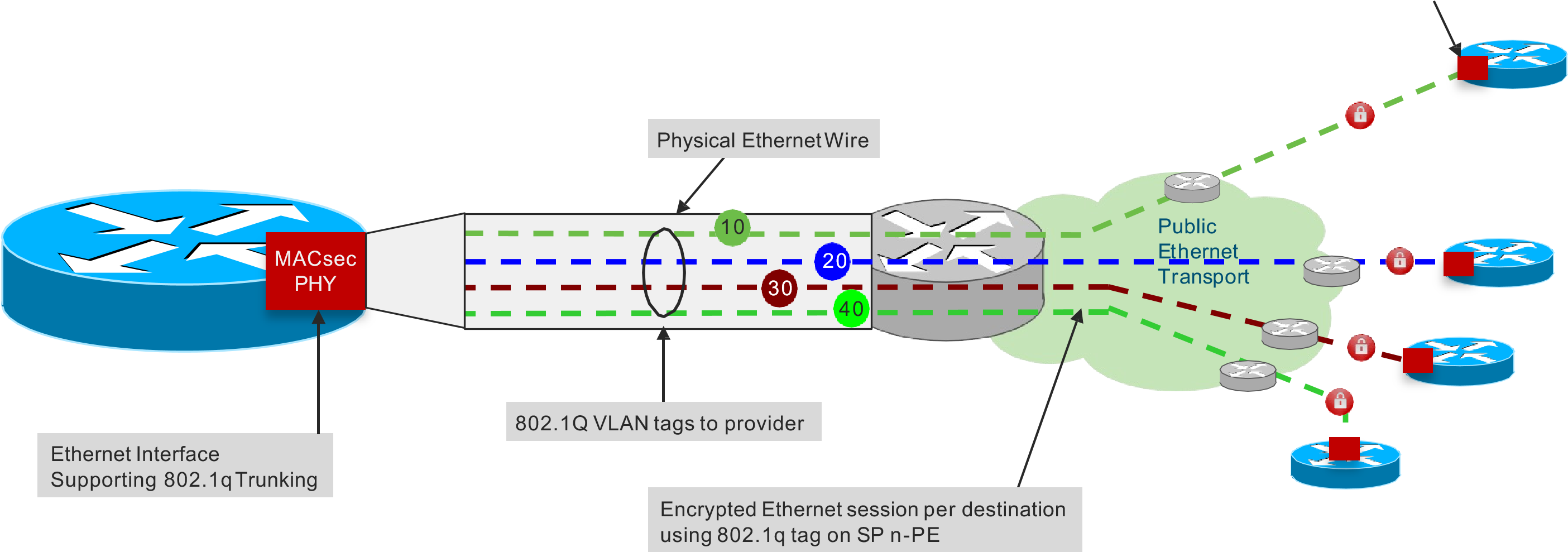
WAN MACsec – 802.1Q Tag in the Clear
Expose the 802.1Q tag “outside” the encrypted payload