About Lesson
Authenticating with WebAuth
use of a web page where credentials are entered.
- WebAuth is different because it presents the end user with content to read and interact with before granting access to the network.
- Can be used as an additional layer in concert with Open Authentication, PSK, and EAP-based authentication.
Local WebAuth (LWA)
WebAuth can be handled locally on the WLC for smaller environments:
- LWA with an internal database on the WLC
- LWA with an external database on a RADIUS/LDAP server
- LWA with an external redirect after authentication
- LWA with an external splash page redirect, using an internal database on the WLC
- LWA with passthrough, requiring user acknowledgment
When there are many controllers providing WebAuth, it makes sense to use LWA with an external database on a RADIUS server (ISE), keep the user database centralized. The next logical progression is to move the WebAuth page onto the central server, Central Web Authentication (CWA).
Configure WebAuth on WLAN
- Go to the General tab and enter the SSID string, apply the appropriate controller interface, and change the status to Enabled.
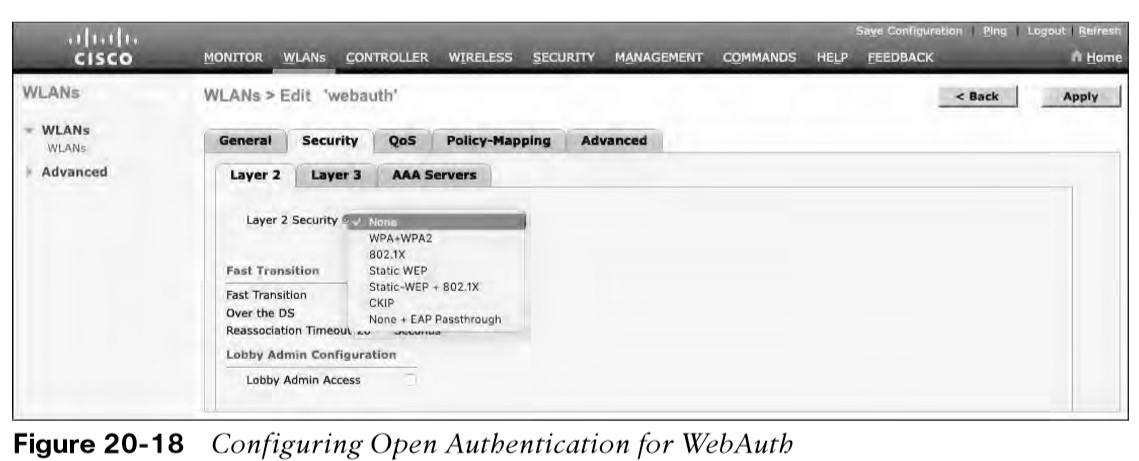
- On the Security tab, select the Layer 2 tab to choose a wireless security scheme to be used on the WLAN.
the WLAN is named webauth, the SSID is Guest_webauth, and Open Authentication used because the None method selected. 
- Next, select the Security > Layer 3 tab and choose Web Policy.
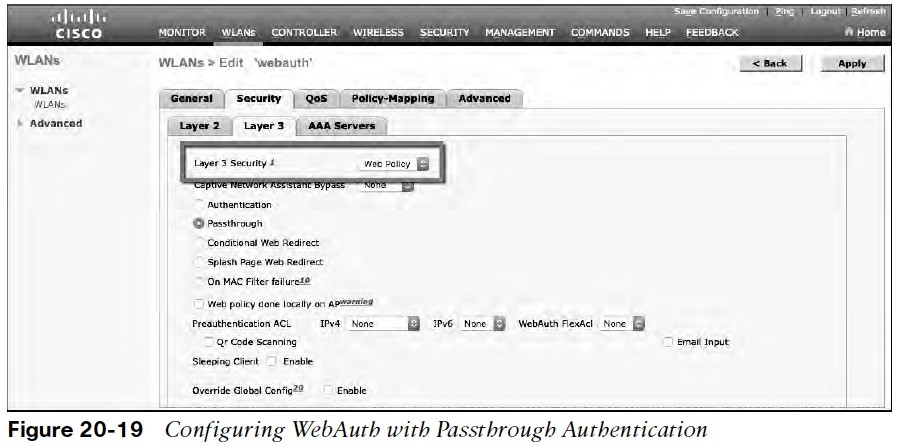
- When the Authentication radio button selected (the default), WebAuth performed locally on the WLC by prompting the user for credentials that will be checked against RADIUS, LDAP, local EAP servers.
- In the figure, Passthrough has been selected, which will display web content such as an acceptable use policy to the user and prompt for acceptance.
- Through the other radio buttons, WebAuth can redirect the user to an external web server for content and interaction. Click Apply.
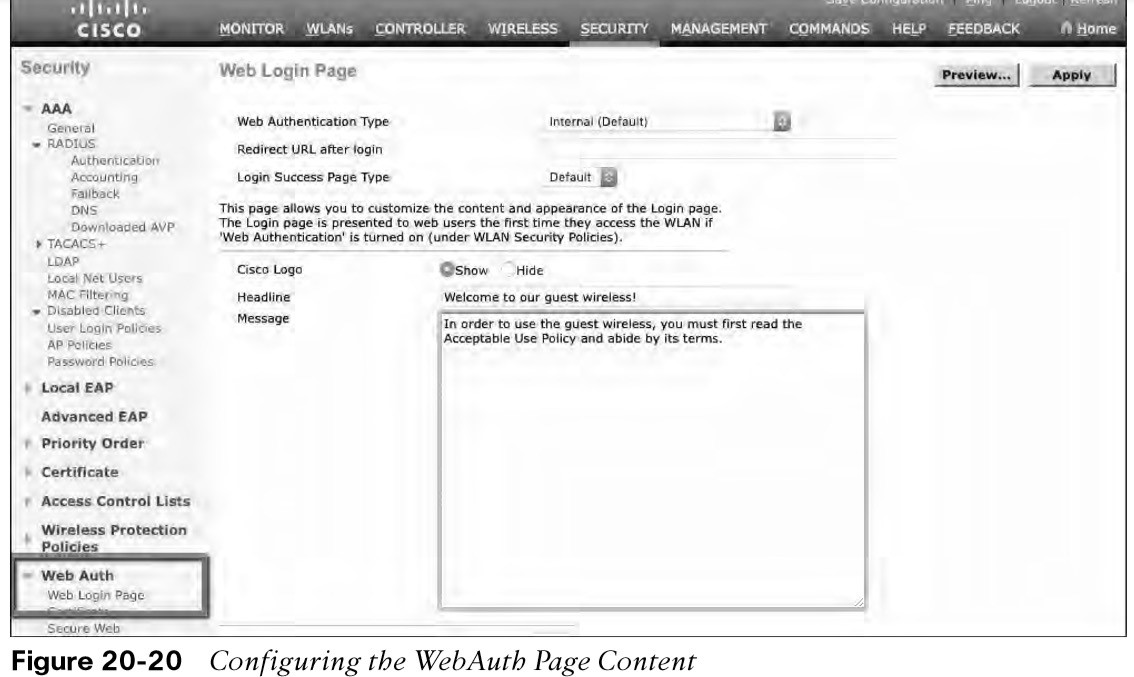
- You will need to configure the WLC’s local web server with content to display during a WebAuth session.
- Security > Web Auth > Web Login Page. By default, internal WebAuth used.
- You can enter the web content that will be displayed to the user.
Verifying WebAuth on a WLAN
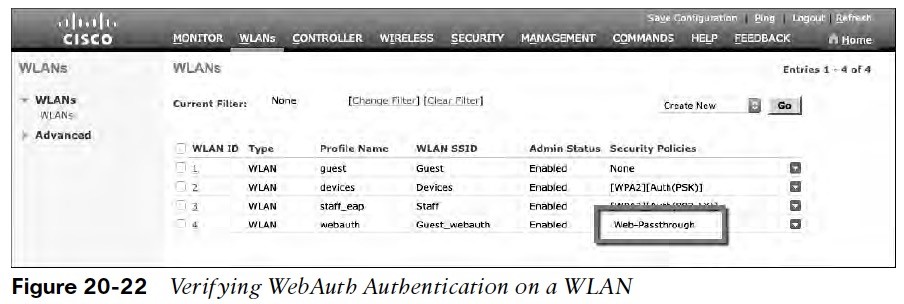
- You can verify the WebAuth settings by selecting WLANs > WLAN
- WLAN 4 with SSID Guest_webauth shown to use the Web-Passthrough security policy.
- The WLAN status is enabled and active.
Other useful information:
Join the conversation