About Lesson
Authenticating with EAP
authenticating clients with Extensible Authentication Protocol (EAP).
- Rather than build additional authentication methods into the 802.11 standard, EAP offers a more flexible and scalable authentication framework.
- EAP is extensible and does not consist of any one authentication method. Instead, EAP defines a set of common functions that actual authentication methods can use to authenticate users.
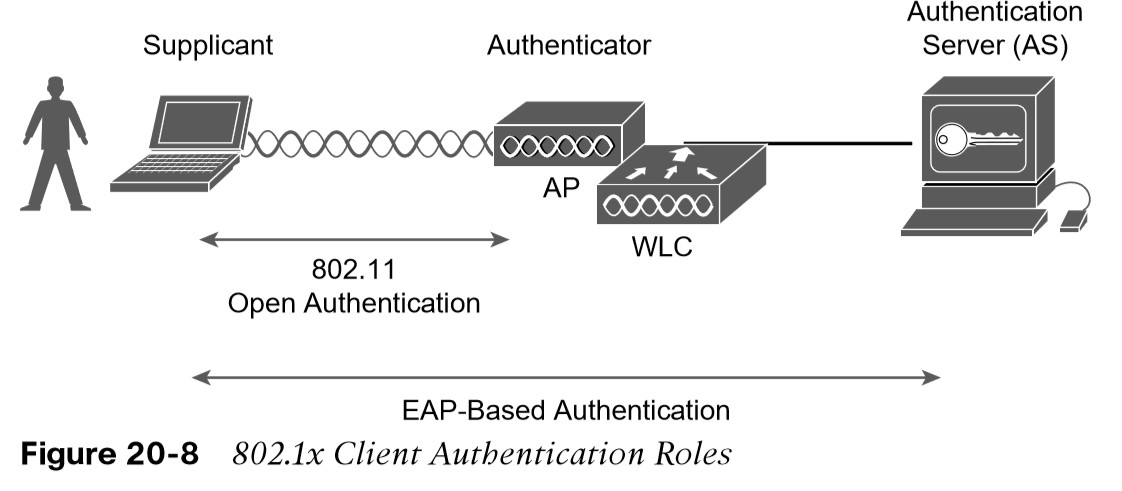
- It can integrate with the IEEE 802.1x port-based access control standard. When 802.1x enabled, it limits access to a network medium until a client authenticates. This means that a wireless client might be able to associate with an AP but will not be able to pass data to any other part of the network until it successfully authenticates.
802.1x Client Authentication Roles

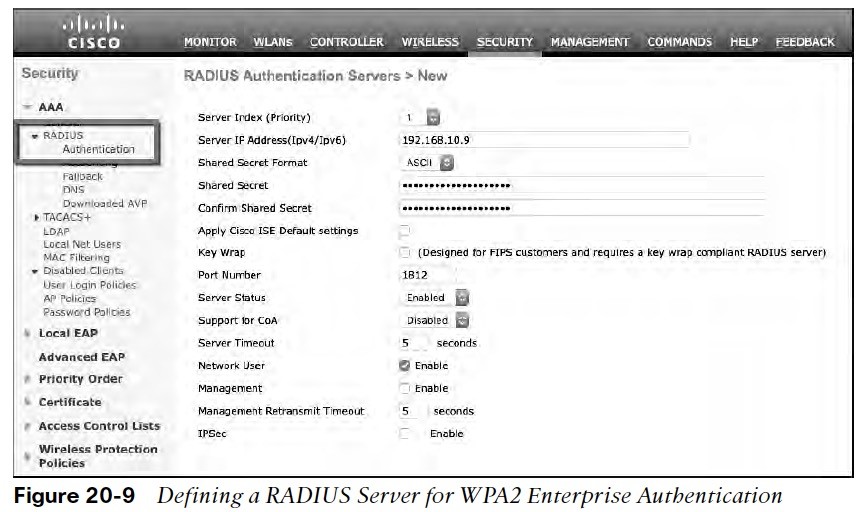
Configuring EAP-Based Authentication with External RADIUS Servers
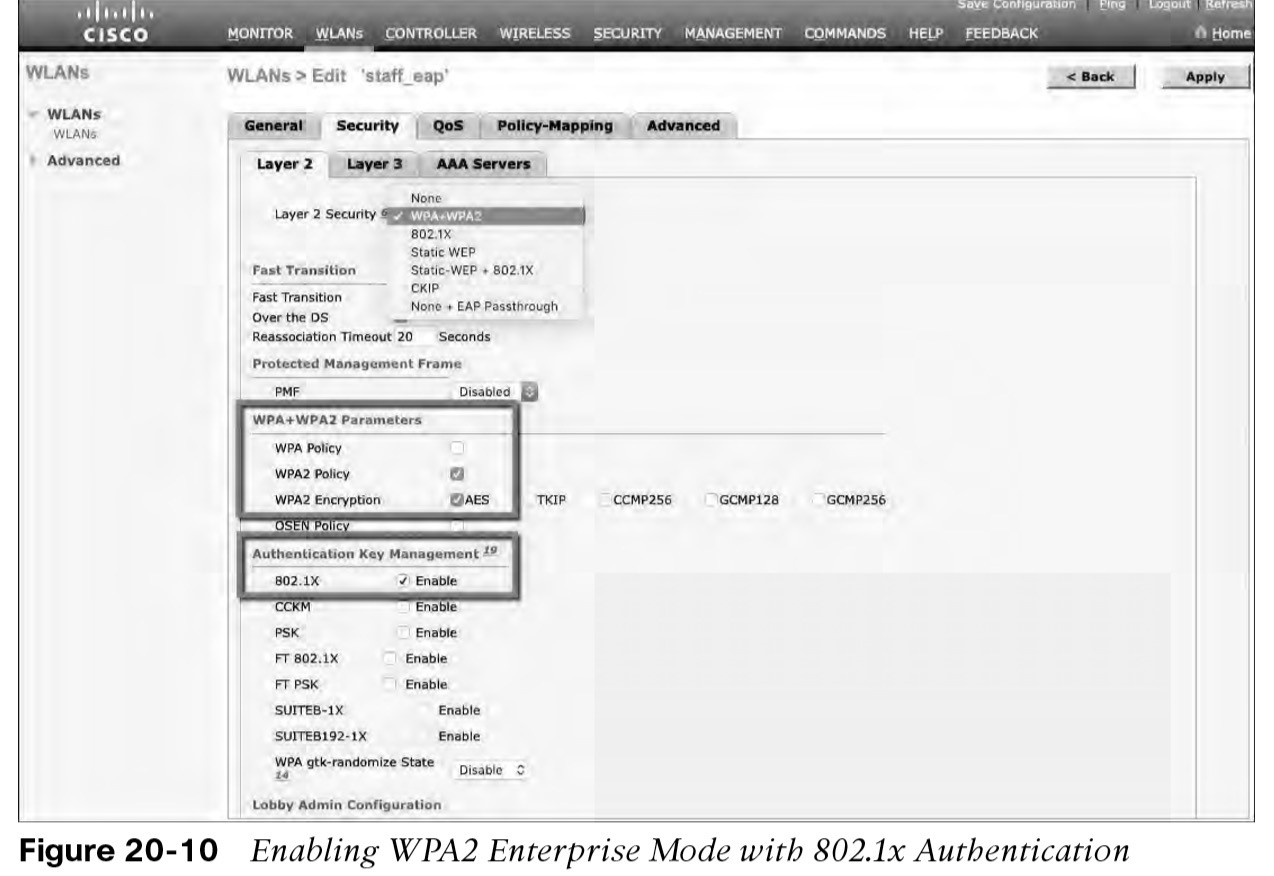
- Next, enable 802.1x authentication on the WLAN.
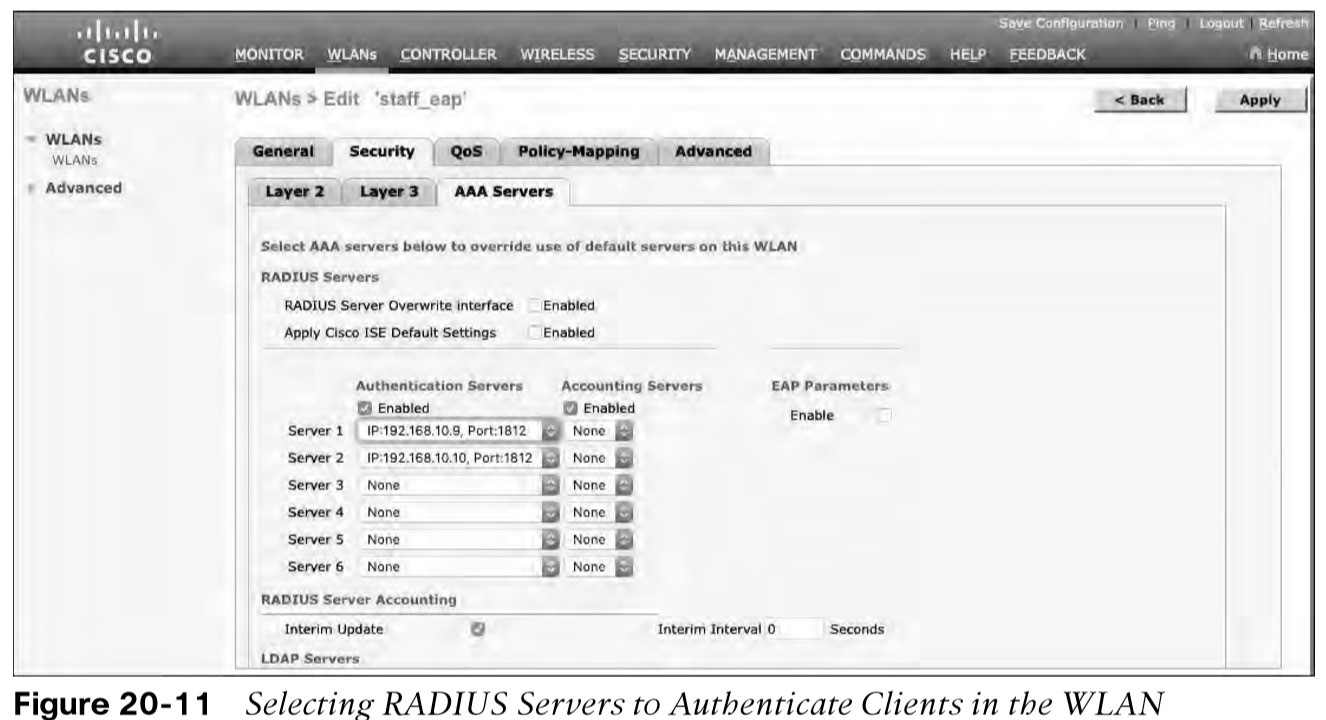
Configuring EAP-Based Authentication with Local EAP
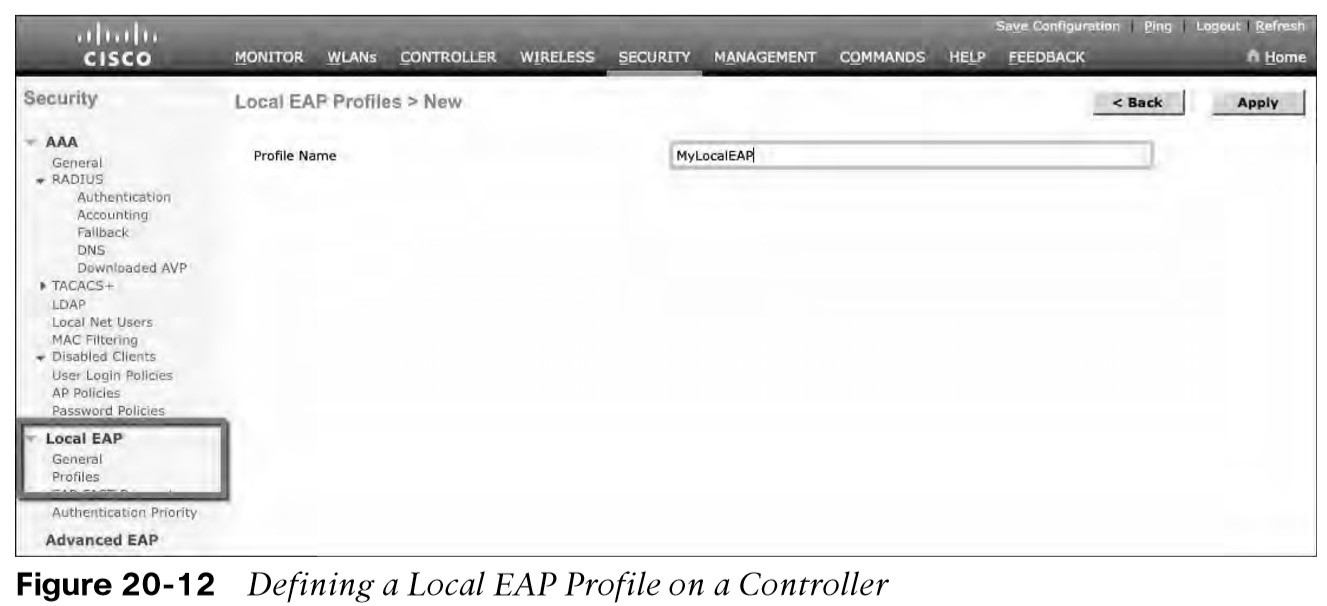
- If your environment is small or you do not have a RADIUS server, you can use Local EAP.
- It supports LEAP, EAP-FAST, PEAP, EAP-TLS.
- Define and enable the local EAP service on the controller. Navigate to Security > Local EAP > Profiles and click the New button. Enter a name for the Local EAP profile, which will be used to define the authentication server methods.
Other useful information:
Join the conversation