BGP Route Filtering and Manipulation
expands on how conditional matching and route maps work by applying real-world use cases to demonstrate the filtering or manipulation of BGP routes.
- Route filtering is a method of selectively identifying routes that are advertised or received from neighbor routers.
- Route filtering may be used to manipulate traffic flows, reduce memory utilization, or improve security.
BGP Route Filtering Concepts
Route filtering selectively identifies routes that are advertised or received from neighbor routers. Route filtering may be used to manipulate traffic flows, reduce memory utilization, or improve security. ISPs commonly deploy route filters on BGP peerings to customers. Ensuring that only the customer routes are allowed over the peering link prevents the customer from accidentally becoming a transit AS on the internet. IOS XE has four methods of filtering routes inbound or outbound for a specific BGP peer:
- Distribute list – This filters network prefixes based on a standard or extended ACL. An implicit deny implied for any prefix not permitted.
- Prefix list – The prefix-matching specifications permit or deny network prefixes in a top-down fashion. An implicit deny for any prefix not permitted.
- AS path ACL/filtering – A list of regex commands allow for the permit or deny of a network prefix based on the current AS path values. An implicit deny for any prefix not permitted.
- Route maps – These provide a method of conditional matching on a variety of prefix attributes and taking a variety of actions. Actions could be a simple permit or deny; or could include the modification of BGP path attributes. An implicit deny for any prefix that is not permitted.
BGP Route Filtering Concepts (begin routing table reference)
The following slides explain each of the route filtering techniques in more detail. Imagine a simple scenario with R1 (AS 65100) that has a single eBGP peering with R2 (AS 65200), which then may peer with other autonomous systems (such as AS 65300). The relevant portion of the topology is that R1 peers with R2 and focuses on R1’s BGP table, as shown in Example 12-8, with an emphasis on the network prefix and the AS path. 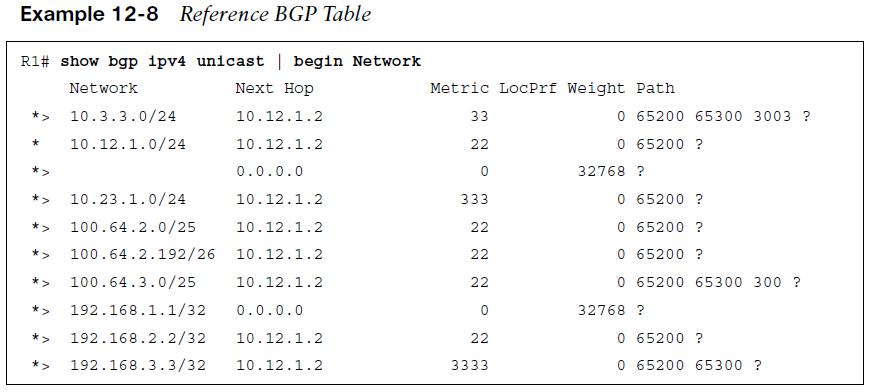
BGP Distribute List Filtering
Distribute lists allow the filtering of network prefixes on a neighbor-by-neighbor basis, using standard or extended ACLs. Configuring a distribute list requires using the BGP address family configuration command neighbor ip-address distribute-list {acl-number | acl-name} {in|out}. Remember that extended ACLs for BGP use the source fields to match the network portion and the destination fields to match against the network mask. 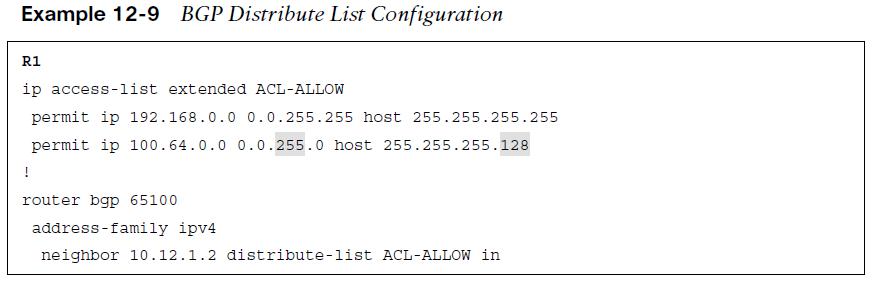
BGP Distribute List Filtering (routing table result)
Two local routes are injected into the BGP table by R1 (10.12.1.0/24 and 192.168.1.1/32). The two loopback networks from R2 (AS 65200) and R3 (AS 65300) are allowed because they are within the first ACL-ALLOW entry, and two of the networks in the 100.64.x.0 pattern (100.64.2.0/25 and 100.64.3.0/25) are accepted. The 100.64.2.192/26 network is rejected because the prefix length does not match the second ACL-ALLOW entry. Example 12-10 displays the routing table of R1 after BGP distribute list filtering. 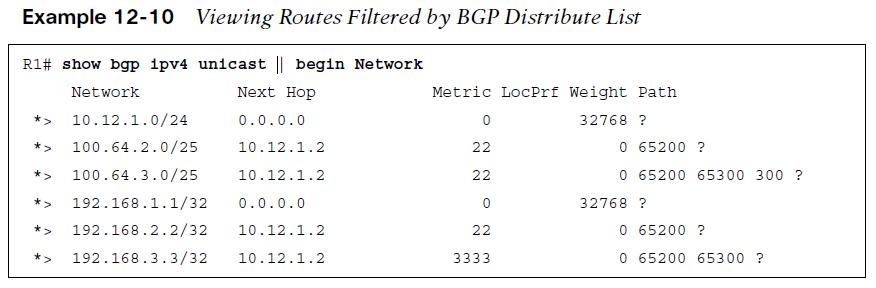
BGP Prefix List Filtering and Routing Table Result
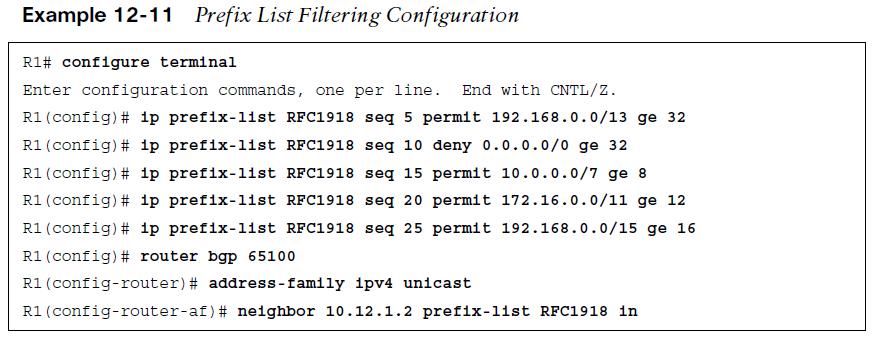
Prefix lists allow the filtering of network prefixes on a neighbor-by-neighbor basis, using a prefix list. Configuring a prefix list involves using the BGP address family configuration command neighbor ip-address prefix-list prefix-list-name {in | out}. Example 12-11 demonstrates the use of a prefix list filter to allow only routes within the RFC 1918 space. The prefix-list is applied on R1’s peering to R2 (AS 65200).  The BGP table can be examined on R1, as shown in Example 12-12. Notice that the 100.64.2.0/25, 100.64.2.192/26, and 100.64.3.0/25 networks were filtered as they did not fall within the prefix list matching criteria.
The BGP table can be examined on R1, as shown in Example 12-12. Notice that the 100.64.2.0/25, 100.64.2.192/26, and 100.64.3.0/25 networks were filtered as they did not fall within the prefix list matching criteria. 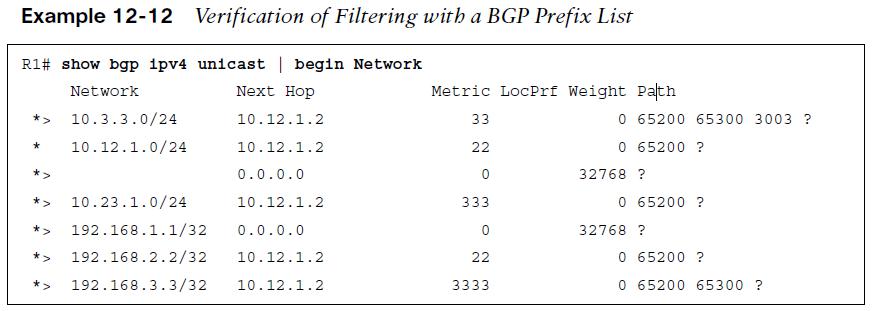
BGP AS Path ACL Filtering
Selecting routes from a BGP neighbor by using the AS path requires the definition of an AS path access control list (AS path ACL). Regular expressions, introduced earlier in this chapter, are a component of AS_Path filtering. Example 12-13 shows the routes that R2 (AS 65200) is advertising toward R1 (AS 65100). 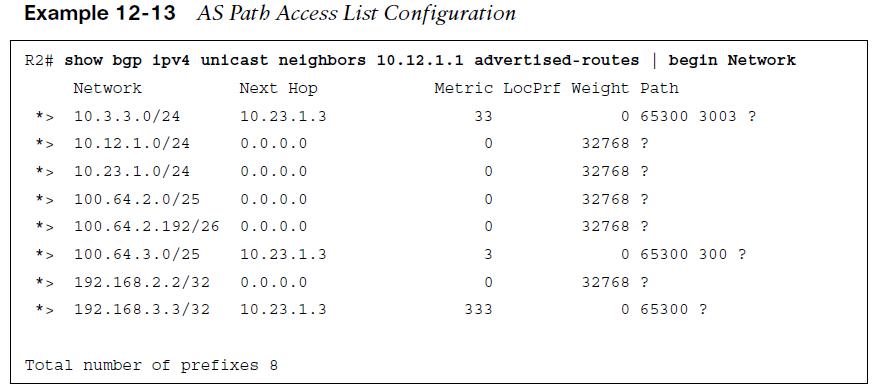 R2 is advertising the routes learned from R3 (AS 65300) to R1. In essence, R2 provides transit connectivity between the autonomous systems. If this were an Internet connection and R2 were an enterprise, it would not want to advertise routes learned from other ASs. Using an AS path access list to restrict the advertisement of only AS 65200 routes is recommended.
R2 is advertising the routes learned from R3 (AS 65300) to R1. In essence, R2 provides transit connectivity between the autonomous systems. If this were an Internet connection and R2 were an enterprise, it would not want to advertise routes learned from other ASs. Using an AS path access list to restrict the advertisement of only AS 65200 routes is recommended.
BGP AS Path ACL Filtering (Cont.)
IOS supports up to 500 AS path ACLs and uses the command ip as-path access- list acl-number {deny | permit} regex-query for creating an AS path ACL. The ACL is then applied with the command neighbor ip-address filter-list acl-number {in|out}. Example 12-14 shows the configuration on R2 using an AS path ACL to restrict traffic to only locally originated traffic, using the regex pattern ^$ to ensure completeness, the AS path ACL is applied on all eBGP neighborships. 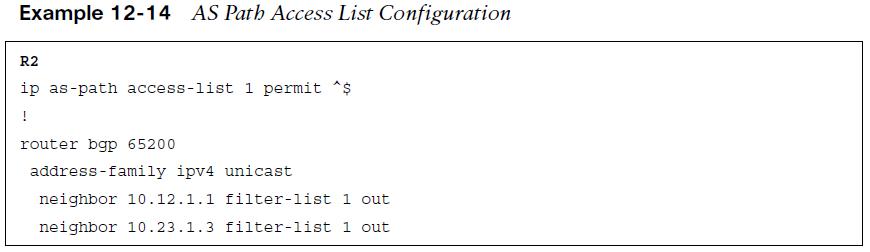 Example 12-15 displays the routes being advertised to R1. Notice that all the routes do not have an AS path, confirming that only locally originating routes are being advertised externally.
Example 12-15 displays the routes being advertised to R1. Notice that all the routes do not have an AS path, confirming that only locally originating routes are being advertised externally. 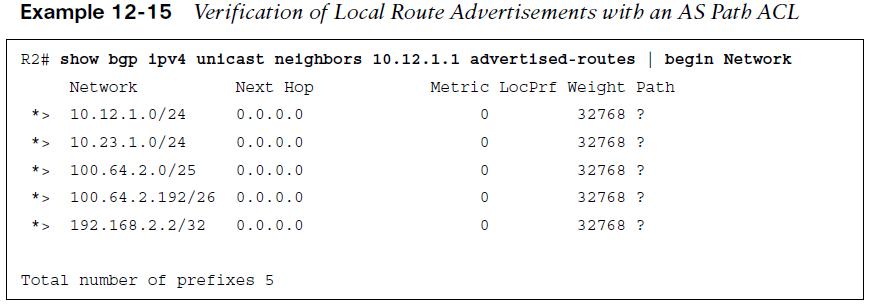
BGP Route Map Filtering
Route maps provide additional functionality over pure filtering. Route maps can manipulate BGP path attributes as well. Route maps are applied on a BGP neighbor for routes that are advertised or received. A different route map can be used for each direction. The route map is associated with the BGP neighbor under the specific address family, with the command neighbor ip-address route-map route-map-name {in|out}. 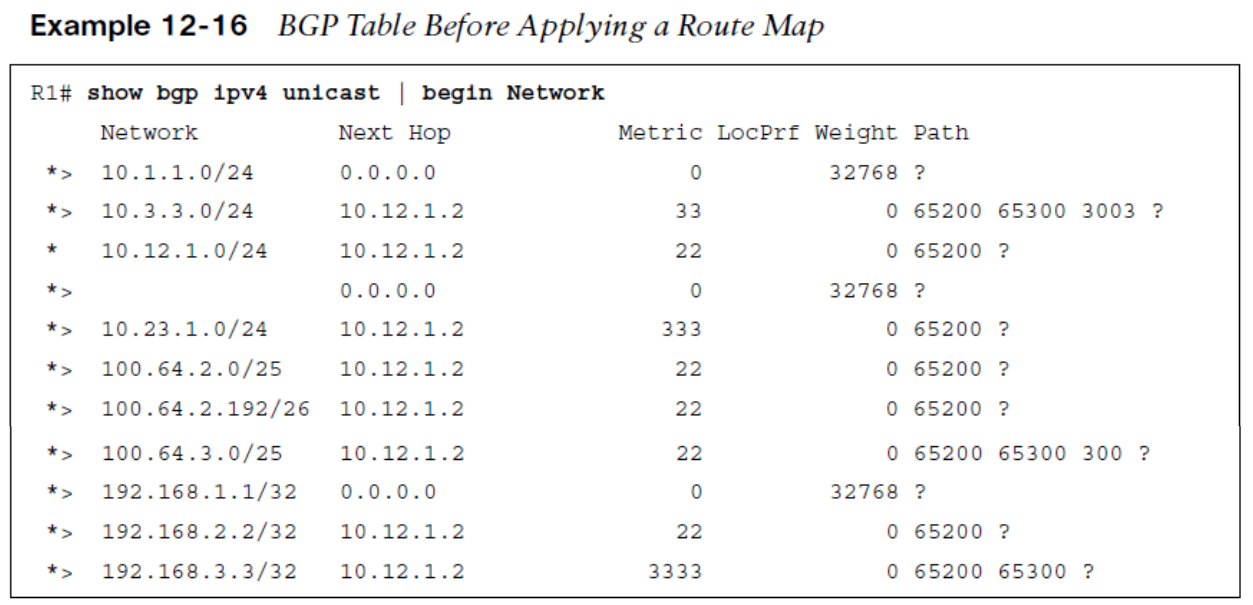
BGP Route Map Filtering
This route map consists of four steps:
- Deny any routes that are in the 192.168.0.0/16 network by using a prefix list.
- Match any routes originating from AS 65200 that are within the 100.64.0.0/10 network range and set the BGP local preference to 222.
- Match any routes originating from AS 65200 that did not match step 2 and set the BGP weight to 65200.
- Permit all other routes to process.
Example 12-17 demonstrates R1’s configuration, where multiple prefix lists are referenced along with an AS path ACL. 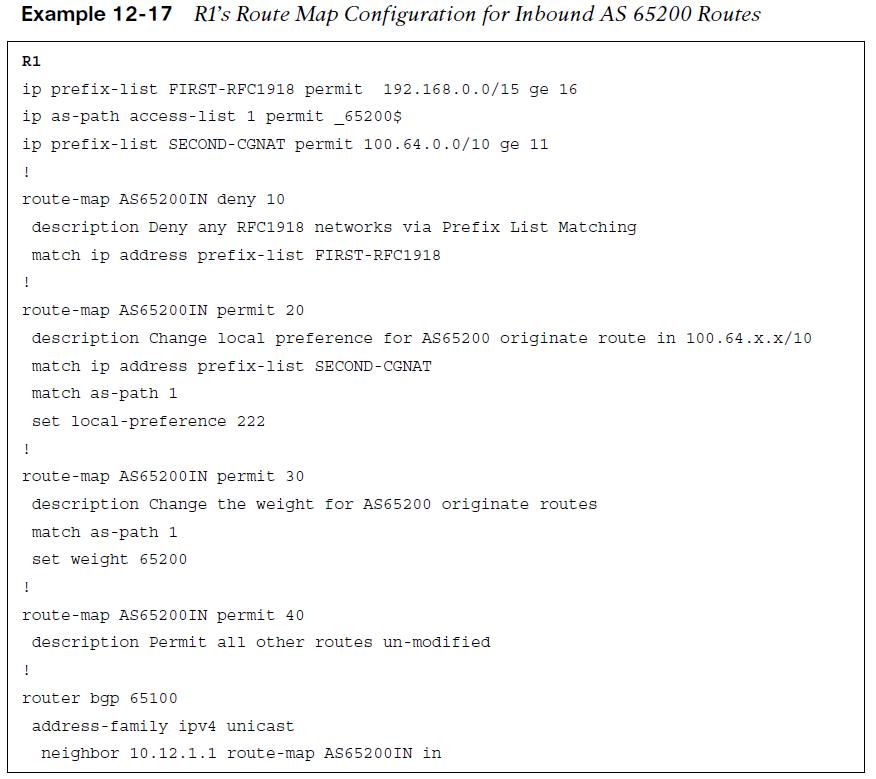
BGP Route Map Filtering (routing table result)
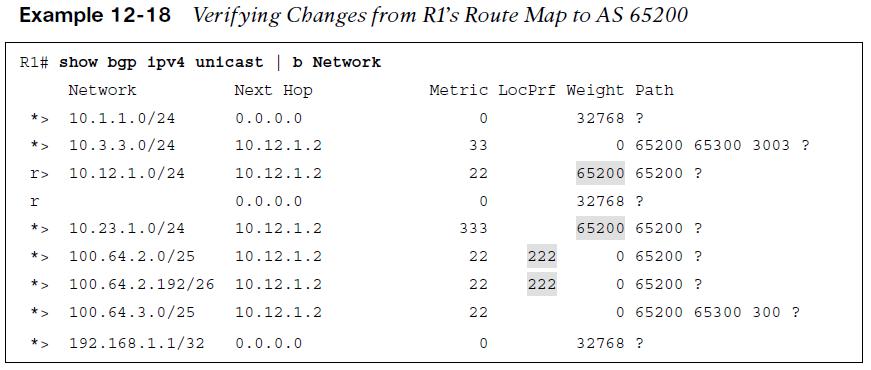 Example 12-18 displays R1’s BGP routing table. The following actions have occurred:
Example 12-18 displays R1’s BGP routing table. The following actions have occurred:
- The 192.168.2.2/32 and 192.168.3.3/32 routes were discarded. The 192.168.1.1/32 route is a locally generated route.
- The 100.64.2.0/25 and 100.64.2.192/26 networks had the local preference modified to 222 because they originated from AS 65200 and are within the 100.64.0.0/10 network range.
- The 10.12.1.0/24 and 10.23.1.0/24 routes from R2 were assigned the locally significant BGP attribute weight 65200.
- All other routes were received and not modified.
It is considered a best practice to use a different route policy for inbound and outbound prefixes for each BGP neighbor.
Clearing BGP Connections
Depending on the change to the BGP route manipulation technique, a BGP session may need to be refreshed in order to take effect. BGP supports two methods of clearing a BGP session:
- Hard reset tears down the BGP session, removes BGP routes from the peer, and is the most disruptive.
- Soft reset invalidates the BGP cache and requests a full advertisement from its BGP peer.
Routers initiate a hard reset with the command: clear ip bgp ip-address [soft] and a soft reset by using the optional soft keyword. All of a router’s BGP sessions can be cleared by using an asterisk * in lieu of the peer’s IP address. Soft resets can be performed for a specific address family with the command clear bgp afi safi {ip-address|*} soft [in | out] Soft resets reduce the number of routes that must be exchanged if multiple address families are configured with a single BGP peer. Other useful information: