Access Control Lists (ACLs)
how to configure and verify ACLs to secure the network infrastructure.
- ACLs are sequential lists of access control entries (ACEs) that perform permit or deny packet classification, based on predefined conditional matching statements.
- Packet classification starts at the top (lowest sequence) and proceeds down (higher sequence) until a matching pattern is identified.
- When a match is found, the appropriate action (permit or deny) is taken, and processing stops.
- At the end of every ACL is an implicit deny ACE, which denies all packets that did not match earlier in the ACL.
ACLs
- Numbered standard ACLs – These ACLs define packets based solely on the source network, and they use the numbered entries 1–99 and 1300–1999.
- Numbered extended ACLs – These ACLs define packets based on source, destination, protocol, port, or a combination of other packet attributes, and they use the numbered entries 100–199 and 2000–2699.
- Named ACLs –These ACLs allow standard and extended ACLs to be given names instead of numbers.
- Port ACLs (PACLs) – These ACLs can use standard, extended, named, and named extended MAC ACLs to filter traffic on Layer 2 switchports.
- VLAN ACLs (VACLs) – These ACLs can use standard, extended, named, and named extended MAC ACLs to filter traffic on VLANs.
Wildcard Masks
- ACLs use wildcard masks instead of subnet masks to classify packets that are being evaluated.
- All that is required to convert a subnet mask into a wildcard mask is to subtract the subnet mask from 255.255.255.255.

Applying ACLs
- ACLs have no effect until they are applied to an interface. The next step after creating an ACL is to apply it to an interface.
- In addition to the interface, the direction (in or out) in which the ACL needs to be applied must be specified. Cisco routers allow only one inbound ACL and one outbound ACL per interface.
- ACLs can also be used for various other services in addition to applying to interfaces, such as route maps, class maps, NAT, SNMP, virtual terminal (vty) lines, or trafficclassification techniques.
Numbered ACLs
- Step 1. Define the ACL by using the command access-list-number { deny | permit } source [source-wildcard] [log]. The ACL number can be 1–99 or 1300–1999.
- Step 2. Apply the ACL to an interface by using the command ip access-group {acl-number} {in|out} under interface configuration mode.
The keywords any and host can be used as abbreviations for source [source-wildcard]. Using the keyword any is the equivalent to specifying 0.0.0.0 255.255.255.255, which matches all packets. The keyword host is used to match a specific host. It is the equivalent to having specified a host IP address followed by a wildcard mask of 0.0.0.0. The source and source-wildcard reflect a matching pattern for the network prefix that is being matched.
Numbered ACLs
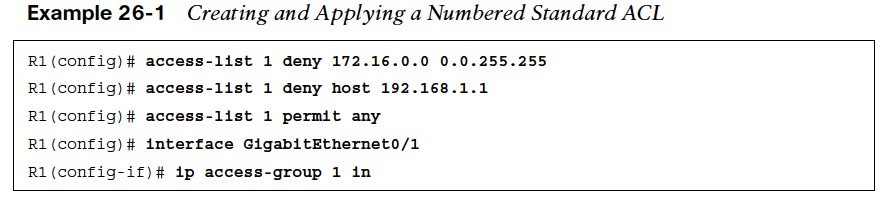
- Example 26-1 demonstrates how a numbered standard ACL is created and applied to an interface to deny traffic from the 172.16.0.0/24 subnet and from host 192.168.1.1/32 while allowing all other traffic coming into interface Gi0/1.
- Notice that the last ACE in the ACL explicitly permits all traffic (permit any). If this ACE is not included, all traffic will be dropped because of the implicit deny (deny any) at the end of every ACL.
| ACE Entry | Networks |
| Permit any | Permits all networks |
| permit 172.16.0.0 0.0.255.255 | Permits all networks in the 172.16.0.0/16 range |
| permit host 192.168.1.1 | Permits only the 192.168.1.1/32 network |
Numbered Extended ACLs
The process for defining a numbered extended ACL is as follows:
- Step 1. Define the ACL by using the command access-list acl-number {deny|permit} protocol source source-wildcard destination destination-wildcard [protocol-options] [log | log-input]. The ACL number can be 100–199 or 2000–2699.
- Step 2. Apply the ACL to an interface by using the command ip access-group {aclnumber} {in|out} under interface configuration mode.
As with standard ACLs, source source-wildcard and destination destination-wildcard can be defined to match a single host with the host keyword or match any subnet with the any keyword. The protocol-options keyword differs based on the protocol specified in the ACE.
Numbered Extended ACLs (Cont.)
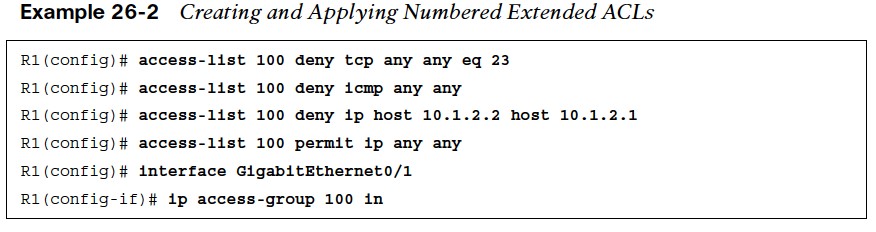
- numbered extended ACL is created and applied to an interface to block all Telnet and ICMP traffic as well as deny all IP traffic from host 10.1.2.2 to host 10.1.2.1. Notice how Telnet’s TCP port 23 is being matched with the eq keyword.
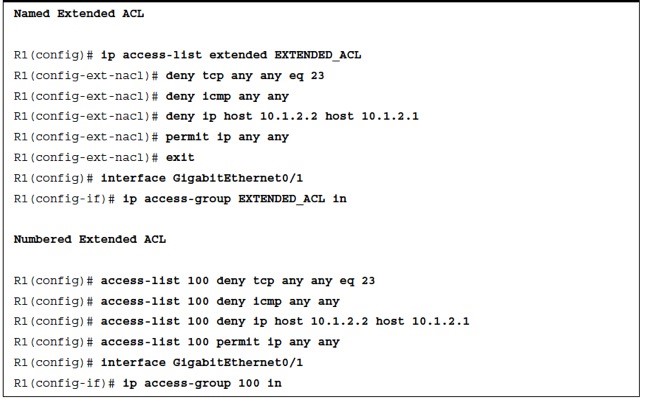
Named ACLs
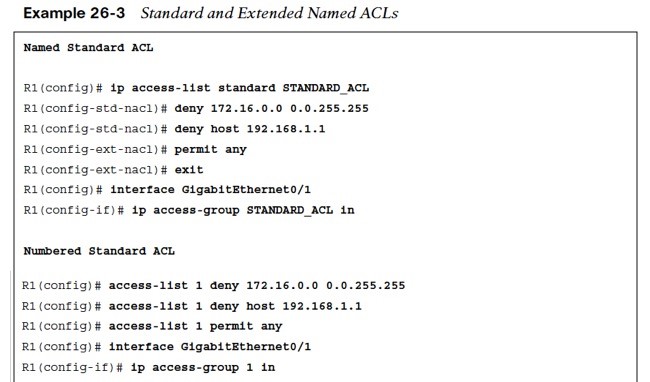
Named ACLs allow for ACLs to be named, which makes administering ACLs much easier as long as proper ACL naming conventions are followed. To create and apply a named ACL, follow these steps:
- Step 1. Define the ACL by using the command ip access-list standard|extended {acl-number | acl-name}. Entering this command places the CLI in ACL configuration mode.
- Step 2. Configure the specific ACE in ACL configuration mode by using the command [sequence] {permit | deny} source source-wildcard.
- Step 3. Apply the ACL to an interface by using the command ip access-group { acl-number | acl-name } {in|out} under interface configuration mode.
Standard and Extended Names ACLs
Port ACLs (PACLs)
Access lists applied on Layer 2 ports are called port access control lists (PACLs). PACLs can be standard, extended, or named IPv4 ACLs for Layer 3, and they can be named MAC address ACLs for Layer 2. PACLs have a few restrictions that vary from platform to platform. The following are some of the most common restrictions:
- PACLs only support filtering incoming traffic on an interface (no outbound filtering support).
- PACLs cannot filter Layer 2 control packets, such as CDP, VTP, DTP, PAgP, UDLD, and STP.
- PACLs are supported only in hardware.
- PACLs do not support ACLs to filter IPv6, ARP, or Multiprotocol Label Switching (MPLS) traffic.
Applying a PACL
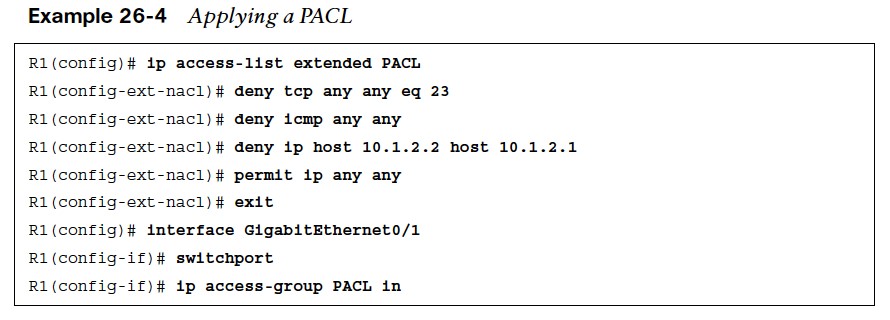
- An IPv4 PACL is applied to an interface with the ip access-group access-list in command.
- Example 26-4 shows a PACL applied to a Layer 2 interface Gi0/1 to block ICMP, Telnet traffic, and host 10.1.2.2 access to host 10.1.2.1.
VLAN ACLs (VACLs)
Access lists applied to VLANs are called VLAN access control lists (VACLs). VACLs can filter traffic that is bridged within a VLAN or that is routed into or out of a VLAN. To create and apply a VACL, follow these steps:
- Step 1. Define a VLAN access map by using the command vlan access-map name sequence.
- Step 2. Configure the match statement by using the command match { ip address { acl-number | acl-name } | mac address acl-name }.
- Step 3. Configure the action statement by using the command action forward|drop [log]. The action statement specifies the action to be taken when a match occurs.
- Step 4. Apply the VACL by using the command vlan filter vlan-access-map-name vlan-list. vlanlist can be a single VLAN, a range of VLANs (such as 5–30), or a comma-separated list of multiple VLANs (such as 1,2–4,6)
Creating and Applying a VACL
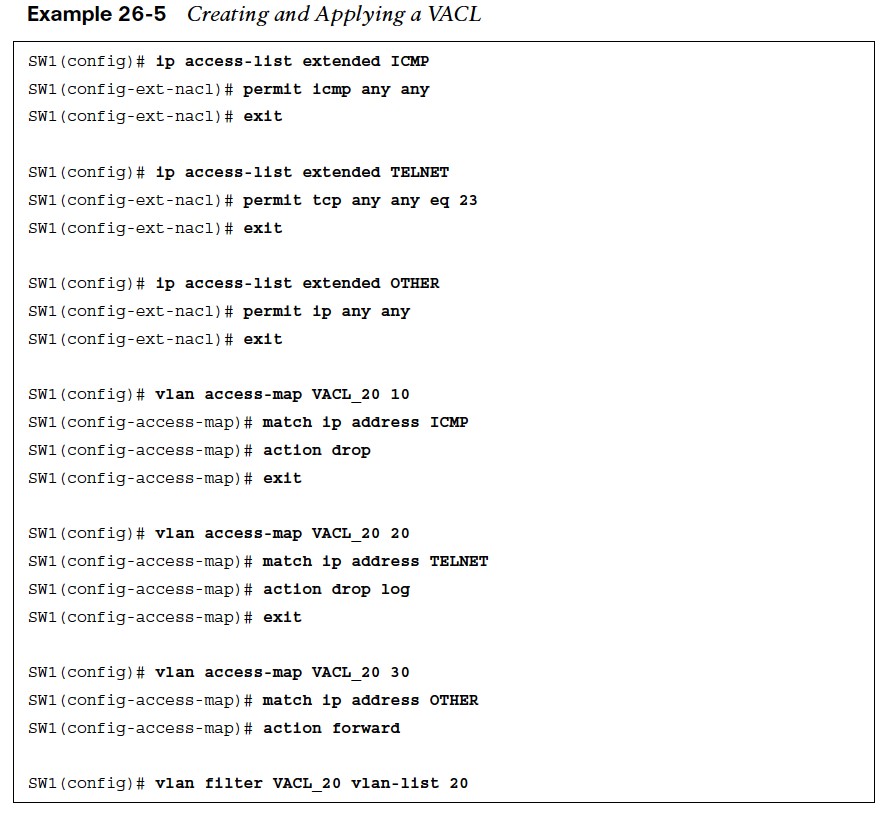
- Example 26-5 shows a VLAN access map applied to VLAN 20 to drop ICMP and Telnet traffic and allow other traffic.
- Notice that the named ACLs, ICMP and TELNET, only include ACEs with a permit statement.
- This is because the ACLs are only used as matching criteria by the VLAN access maps, while the VLAN access maps are configured with the action to drop the matched traffic.
PACL, VACL, PACL Interaction
When a PACL, a VACL, and a RACL are all configured in the same VLAN, the ACLs are applied in a specific order, depending on whether the incoming traffic needs to be bridged or routed. Bridged traffic processing order (within the same VLAN):
- Inbound PACL on the switchport (for example, VLAN 10)
- Inbound VACL on the VLAN (for example, VLAN 10)
- Outbound VACL on the VLAN (for example, VLAN 10)
Routed traffic processing order (across VLANs):
- Inbound PACL on the switchport (for example, VLAN 10)
- Inbound VACL on the VLAN (for example, VLAN 10)
- Inbound ACL on the SVI (for example, SVI 10)
- Outbound ACL on the SVI (for example, SVI 20)
- Outbound VACL on the VLAN (for example, VLAN 20)